How to do a full website vulnerability assessment with Pentest-Tools.com

- Article tags
As a pentester, I have a good day when my workflow is smooth and uninterrupted. Pushing routine tasks to the background (sweet automation!) helps me stay focused. It frees up my mind to work on interesting findings and attack sequences that not everyone can see. Plus, it feels good to be productive and get stuff done!
After running hundreds of pentests and learning from each of them, I created a fine-tuned web application pentesting flow that works every time. It integrates principles and tactics from industry staples such as the OWASP Web Security Testing Guide, the Penetration Testing Execution Standard, and the Open Source Security Testing Methodology Manual.
This step-by-step guide covers the essentials of how to use our tools and features to streamline and speed up your workflow when assessing websites.
We start by mapping the attack surface and continue by running specific tools to perform in-depth scans and find known vulnerabilities that affect web applications. I’ll show you how your findings get automatically stacked in the vulnerability management section of your Pentest-Tools.com dashboard, where you can filter them, validate them, adjust their risk level, or ignore what you don’t want to include in the final report.
Plus, I’ve included tons of time-saving tips you can use to shave hours from every pentest engagement.
Let’s dive into the details!
1. Find Subdomains [optional] to map your attack surface
If you already know your target hostname’s attack surface, you can skip this stage which identifies its subdomains.
Useful tip: What’s interesting about subdomains is they point to various, less-known applications and indicate different external network ranges. What’s more, subdomains sometimes host non-public applications (e.g. test, development, restricted) which are usually less secure than the public/official applications and often serve as primary attack targets.

As a discovery tool, Find Subdomains generates a list of… subdomains, but it doesn’t guarantee to discover all of them. Only if you have access to the DNS server of that domain and look at the zone file can you see ALL the subdomains.

2. Find Virtual Hosts [also optional]
For each web application, you can also run the virtual hosts tool. Here’s why.
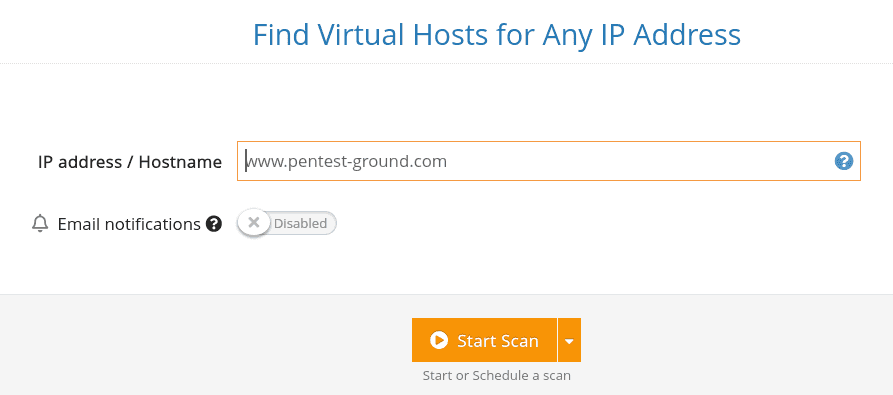
Finding all the virtual hosts that run on a web server (based on its IP address) is important because each website can include vulnerabilities that impact the same server.
If the attacker compromises one of the websites, there’s a high chance they can gain unauthorized access to others that run on the same server. That’s why testing all the vhosts is an essential step to run a penetration test with extensive coverage.

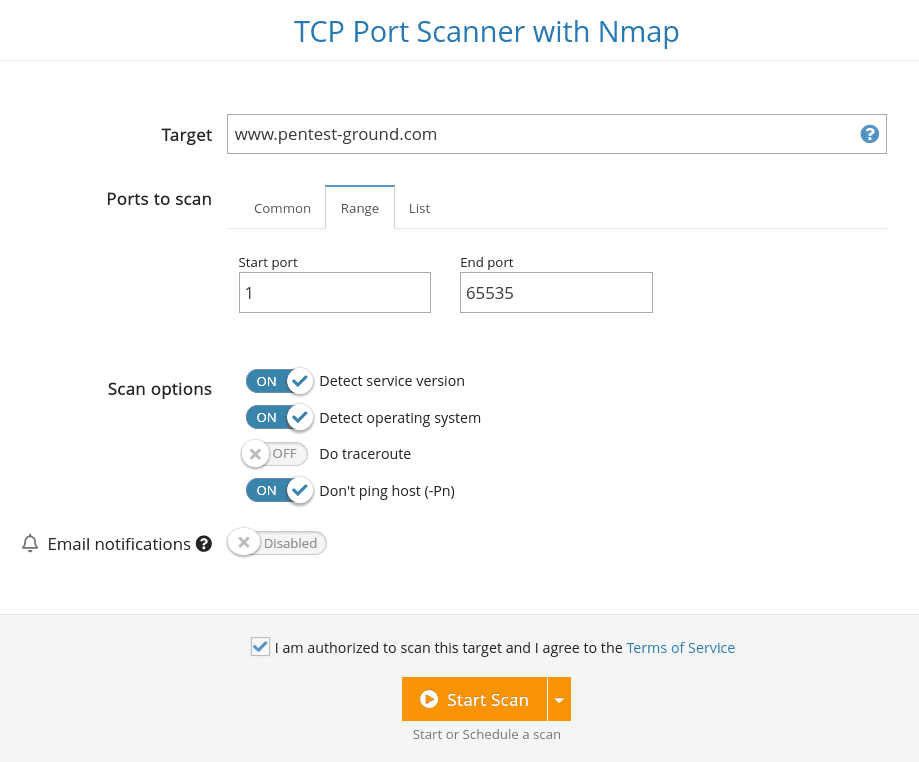
3. Run the TCP Port scanner
Knowing which network services are exposed to the Internet is essential for securing the web application. Run the TCP Port scanner for each hostname and check if there are any open ports that shouldn’t be publicly accessible.
For example, an SSH service that is not filtered based on a predefined list of whitelisted IPs.
After it finds a list of ports, the tool does an in-depth check to determine the exact type of service running on that port, including its version. This is necessary because common services can run on non-standard ports (e.g. a web server running on port 32566).
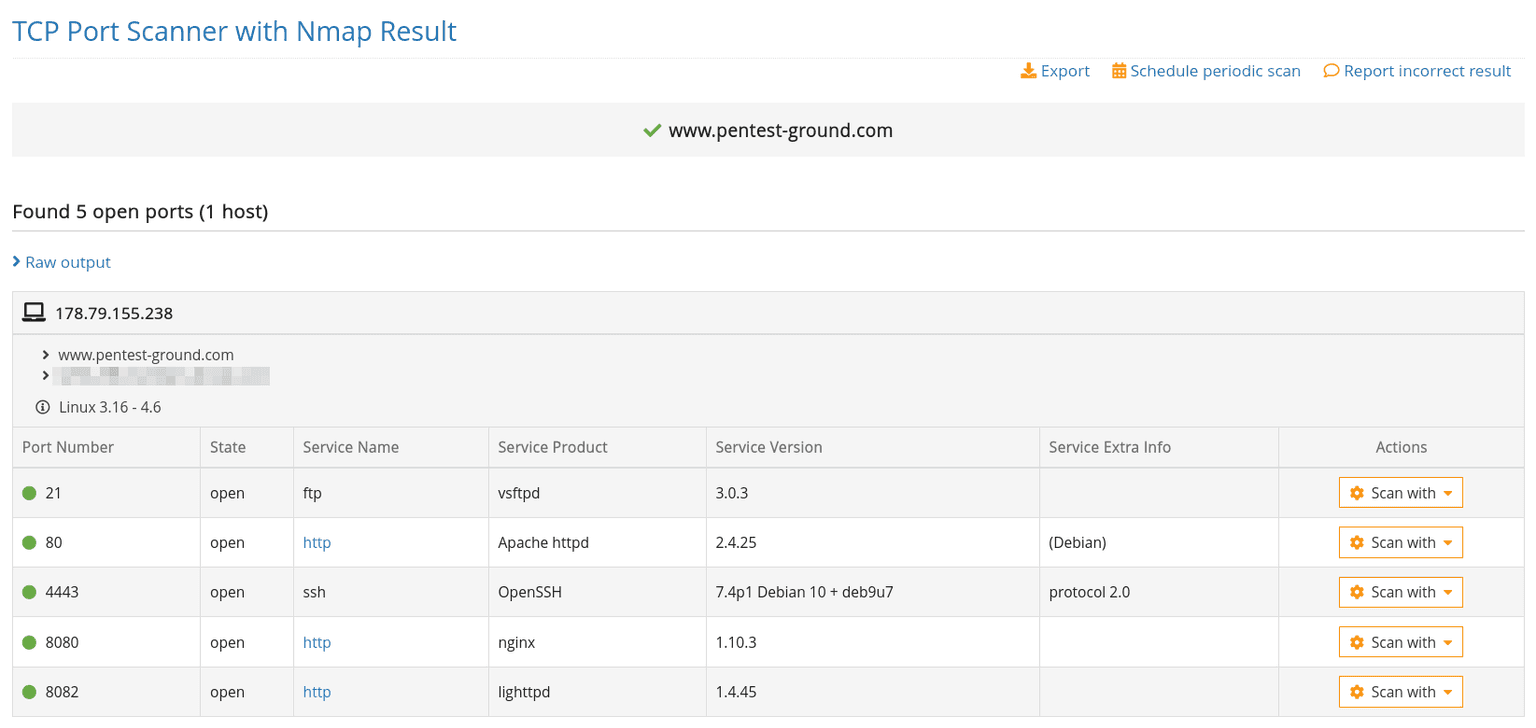
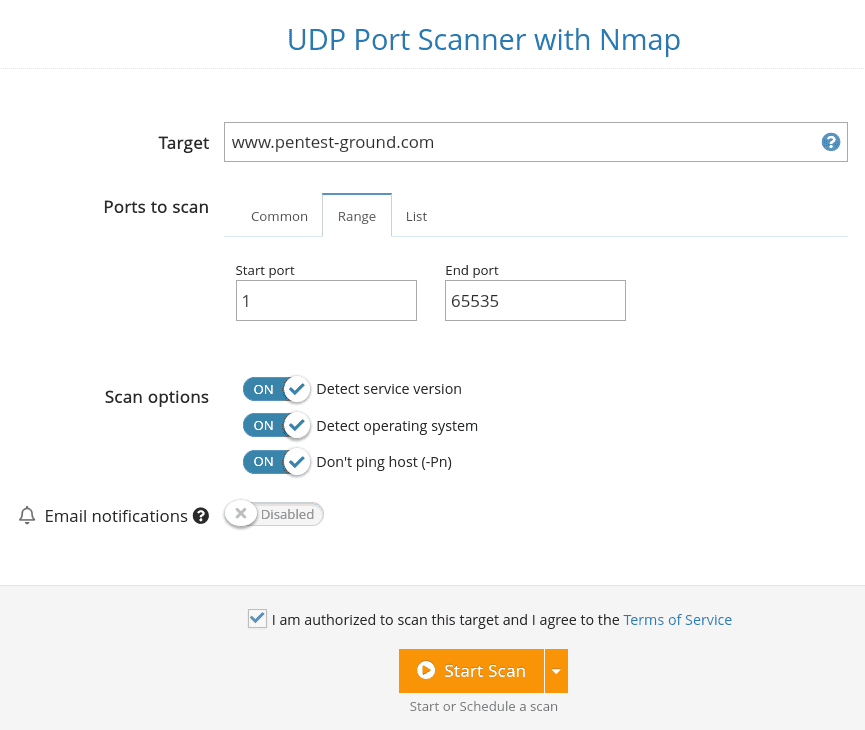
Discover more issues with the UDP Port Scanner
Even though UDP services are less popular than TCP ones, a vulnerable UDP service exposes the target system to the same risk as a vulnerable TCP service. That’s why running a UDP Port Scan to discover all open UDP ports is important in a penetration test so you can achieve full coverage during your security evaluation.
The results are either open or closed. To make sure a specific port marked as open|filtered is really open, you must enable the detection of the service version.
Because this process sometimes takes a while, you should do it in a subsequent scan and only for the ports reported as open|filtered in the first, simple scan.


4. Use the Website Scanner
The Website Scanner finds common vulnerabilities that affect web applications, such as SQL Injection, XSS, OS Command Injection, Directory Traversal, and others. The scanner also identifies specific web server configuration issues.
We recommend using the Light Scan if you don’t want to raise any alarms. It’s passive and performs only a few legitimate requests against the target system. However, as you can expect, the Light scan doesn’t go into much depth and it just scratches the surface in terms of security testing. Keep this in mind as you go through the process.
The Full scan goes into much more detail and attempts to map the entire attack surface of the target system through various tactics: crawling the application, discovering hidden files, using more attack vectors to check for server configuration issues and outdated services, etc.
Note: A Full Scan includes all the tests a Light Scan performs, so there’s no need to run both.

Try a free website vulnerability scan
Start understanding your website's security issues. (No strings attached. Get a PDF report.)
All the vulnerabilities the Website Vulnerability Scanner returns include detailed risk descriptions and a recommendations section which makes it easy to understand the vulnerability and learn how to fix it.
What’s more, the evidence for the vulnerability also contains the attack vector which you can use to trigger the vuln and validate it. We have a separate, dedicated guide that goes into more details about how to do a basic website vulnerability assessment with Pentest-Tools.com, so you should also check that out.

Run a specific CMS scanner [optional]
You can run a specific scanner – such as the ones for SharePoint or WordPress – to discover various security weaknesses or outdated versions of these particular CMSs.
Useful tip: 🤖 You can use our pre-built WordPress Scan Robot to automate the two previous steps. First, it runs the full Website Scanner on the target URL and searches for outdated technologies, SQLi, XSS, and other OWASP Top 10 vulnerabilities. If it finds a WordPress technology, it runs the WordPress Scanner to detect outdated plugins, themes, and more.

Perform an authenticated website scan [where applicable]
If your target application requires authentication and you don’t enable authenticated scans, the Website Scanner covers only a small set of application functionalities, specifically the ones exposed before the user has to log in. Since authenticated users have access to more functionalities than unauthenticated users, you may miss discovering vulnerabilities you can only identify after logging into the application. To get more in-depth results, we recommend performing authenticated scans.
We offer four authentication methods for our Website Scanner tool: recorded, automatic, cookies, or headers. If you don’t know which one is suitable for your target application, check out how each authentication method works in the dedicated guide we created for you.
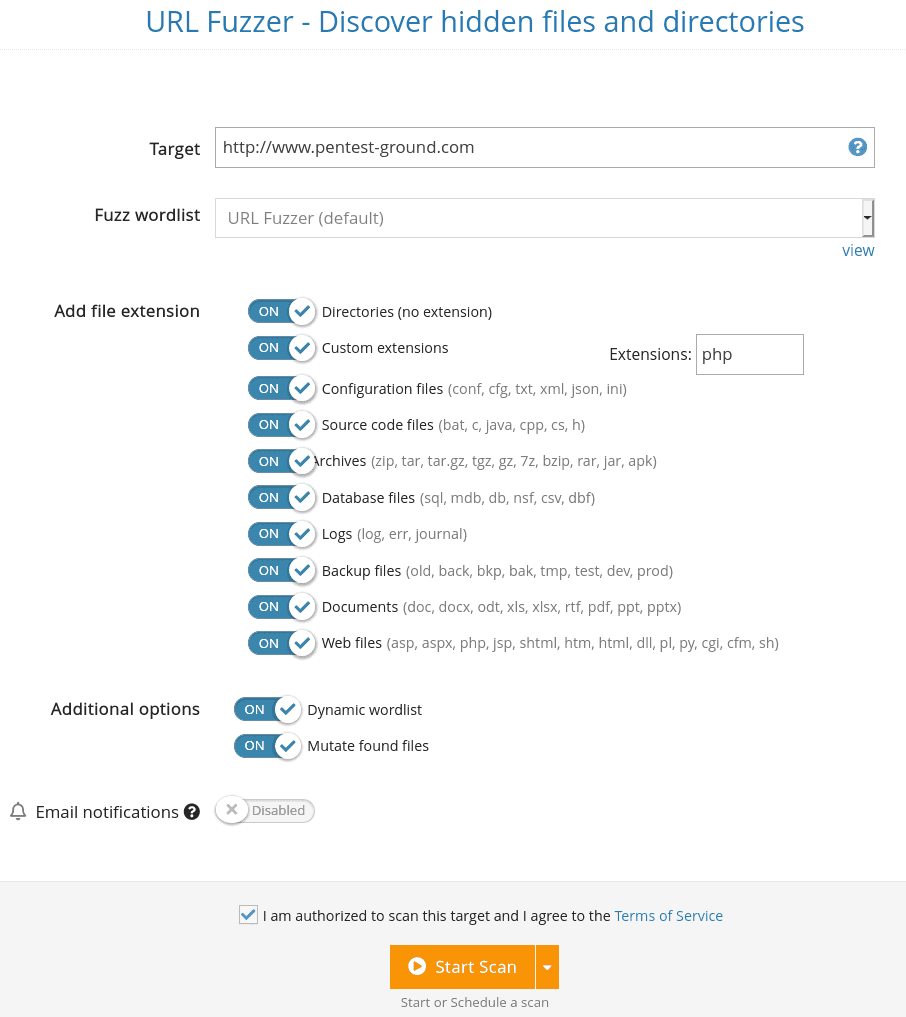
Run the URL Fuzzer
The URL Fuzzer finds hidden files and directories on a web server through the fuzzing method. This is a discovery technique that allows you to discover resources that are not meant to be publicly accessible (e.g. /backups, /index.php.old, /archive.tgz, /source_code.zip, etc).
Since “security by obscurity” is not a good practice to follow, you can often find sensitive information in the hidden locations the URL Fuzzer identifies.
The URL Fuzzer uses a wordlist (either the default one we provide or a custom one you can create) to discover hidden files and directories. For each word added to the list, the tool makes an HTTP request to BaseURL/WORD/ or to BaseURL/WORD.EXT if you chose to fuzz a specific EXTension.
The files and directories the tool discovers are returned together with their HTTP response code and the page size.

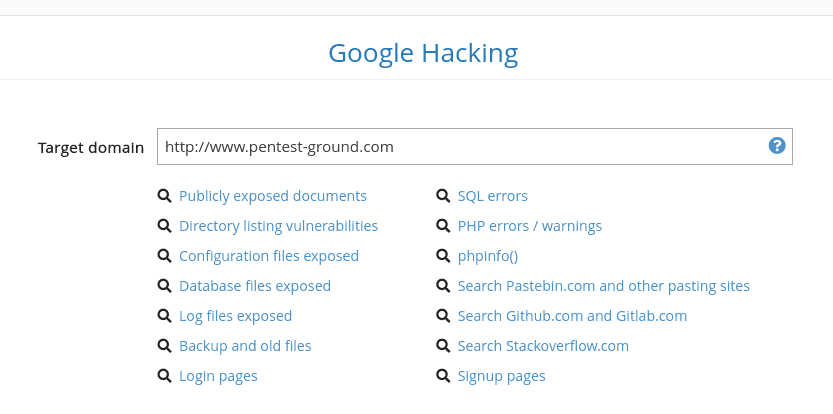
Discover sensitive data about your targets with Google Hacking
Another way to find sensitive information or data that’s not supposed to be public is to use public search engines. Since these engines have gathered huge amounts of information about almost every website from the Internet, it’s a good idea to make specific queries and get relevant data from them.
On Pentest-Tools.com, you can use the free Google Hacking tool to run queries fast and extend your ability to dig up interesting findings.
5. Perform a Password Audit
For the applications or web servers that require authentication, check for weak credentials that are being used by trying the username and password combinations from the input wordlists. The wordlists on Pentest-Tools.com provides you a list of frequently used credentials to start with, but you can also set up, update, and manage your own list of username/pass combinations to detect weak ones faster.
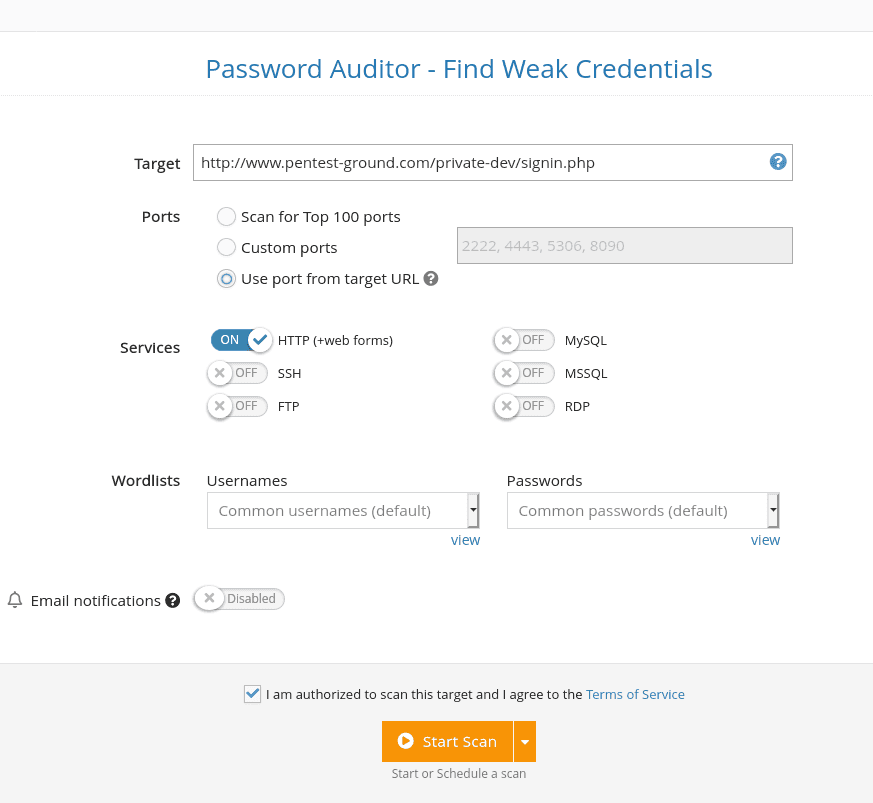
One of the unique advantages of the Password Auditor is that it detects web forms in web applications and it automatically attempts to log in with the given credentials. It has the ability to detect if a web form authentication is successful or not which streamlines your workflow and removes the need for manual checks.
As a result, you can easily find web interfaces with weak passwords (e.g. Jenkins, Tomcat, PhpMyAdmin, Cisco routers, etc.) along with network services such as SSH, FTP, MySQL, MSSQL, RDP, etc. which also have default credentials set.


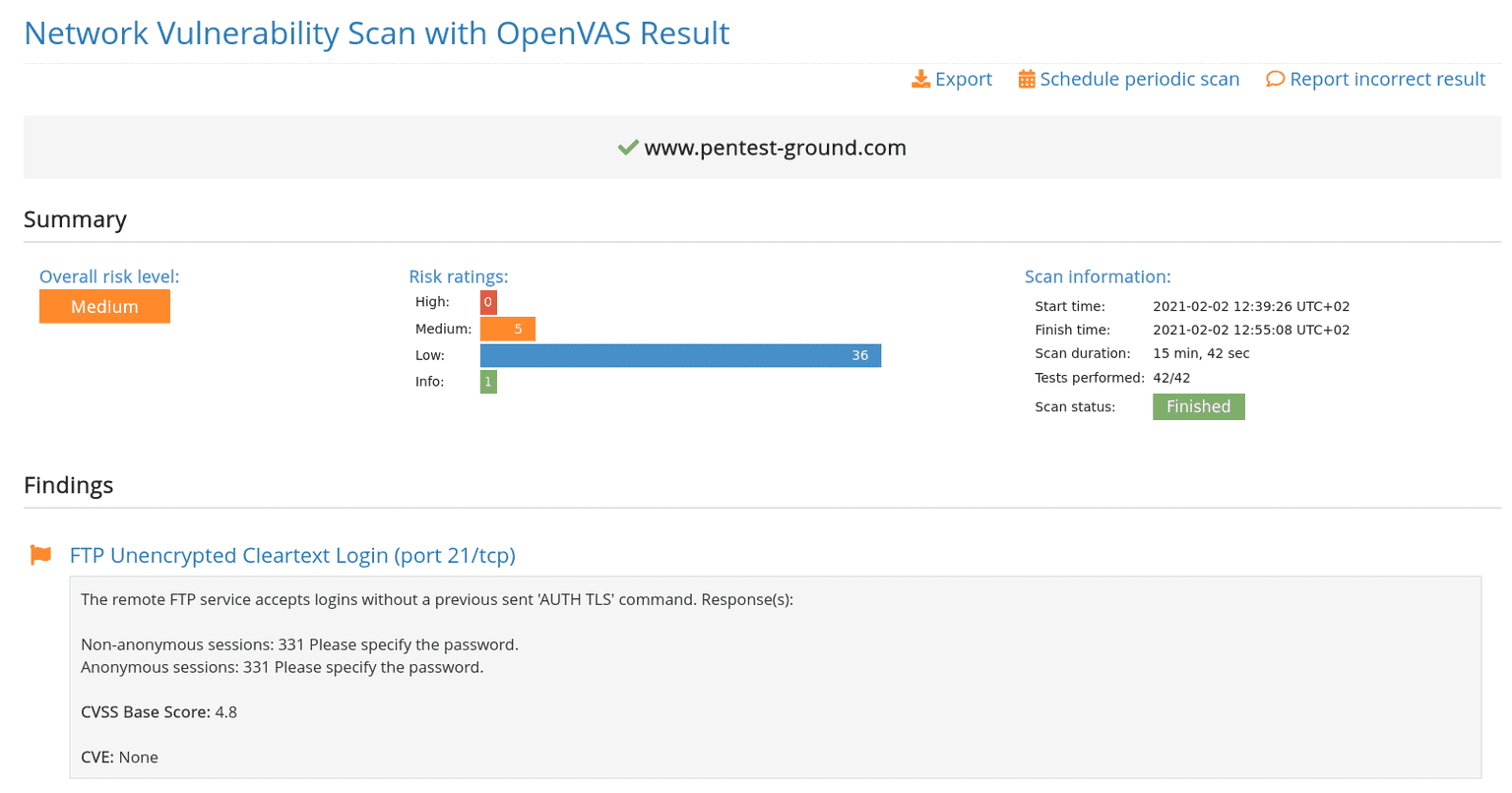
6. Run the Network Vulnerability Scanner with OpenVAS
Since the Network Vulnerability Scanner with OpenVAS helps you detect a wide range of vulnerabilities in network services, operating systems, and also in web servers, its use cases are very diverse. Make sure to test each of your servers to make the most of its capabilities.
If you also have any private servers in the internal network (e.g. for test environments), you can use our VPN agent to create a secure tunnel between our scanning tools and your target network. This way, you can bypass local network restrictions and use our tools to scan from an external IP address. When you get to this step, we show you how easy it is to configure the VPN Agent and create a new VPN profile on Pentest-Tools.com with a handy tutorial.

Quick tip: If the scanner doesn’t find any open ports even though you know there are some, we recommend re-running the scan with the option “Check if host is alive” disabled. This will skip the host discovery phase and just start the port scan.
7. Check the SSL/TLS [optional]
For applications that are not hosted on a major platform such as Azure or AWS, you can also check for SSL or TLS configuration issues using our dedicated SSL/TLS Vulnerability Scanner.
The tool performs a security assessment of the configuration of the target’s SSL/TLS service, providing a list of the security flaws and vulnerabilities it finds, providing you with detailed recommendations for remediation.

A major difference between scan templates and the 🤖 pentest robots is that the template will run all the scans even if some do not apply for the target, while the robots orchestrate multiple tools and run them sequentially, following the logic you implemented in the filters.
8. Validate findings and generate reports from your account
By using our vulnerability management feature (the Findings section of your Pentest-Tools.com dashboard), you can verify findings, change their risk level (if applicable), mark them as fixed or as ignored, and generate advanced reports by selecting findings from multiple scanners. You can manage findings individually, single out recent ones, and edit them in bulk to save massive amounts of time and manual work.
If you have a little over 3 minutes, check out the video walkthrough below.


IMPORTANT: To make sure the scanners run properly, whitelist the following FQDN: scanners.pentest-tools.com. This hostname resolves multiple IP addresses our scanning servers use. See the full list of IP addresses here.
Your workflow is ready. Time to hit the ground running
There’s no shortage of tools for penetration testing but, in my experience, it’s the pentester who makes all the difference. It’s not about how many tools you have, but how you use them to do things like:
downsize routine tasks to a minimum
use your unique experience and expertise to make connections
translate security risks to business risks
and make persuasive points that help decision-makers act on your recommendations.
With this step-by-step guide and your full toolbox on Pentest-Tools.com, you’re now ready to perform a full website vulnerability assessment like a pro!
Because dealing with vulnerabilities sometimes feels like treading water, I encourage you to preach the good word of continuously scanning systems. The team behind Pentest-Tools.com constantly works to add new features and improve the tools on the platform so you can focus on getting stuff done.