Cloud Vulnerability Scanner
Discover and report cloud security vulnerabilities, misconfigurations, bucket owners and users, weak access controls, and interesting files with our custom Cloud Vulnerability Scanner.
Assess targets across multi-cloud environments – AWS, GCP, Azure – both from the outside and from within. Monitor cloud-based systems, networks, and applications for security vulnerabilities with regular scans and notifications tuned to your severity criteria.
Paid plans give you access to its full capabilities, plus other 20+ security testing tools and features.
Unlock full capabilities
There's so much you can do with this tool!
Plus, access to it means full access to all 20+ tools on the platform.
Discover and report cloud security vulnerabilities, misconfigurations, bucket owners and users, weak access controls, and interesting files with our custom Cloud Vulnerability Scanner.
Assess targets across multi-cloud environments – AWS, GCP, Azure – both from the outside and from within. Monitor cloud-based systems, networks, and applications for security vulnerabilities with regular scans and notifications tuned to your severity criteria.
Paid plans give you access to its full capabilities, plus other 20+ security testing tools and features.
Reporting
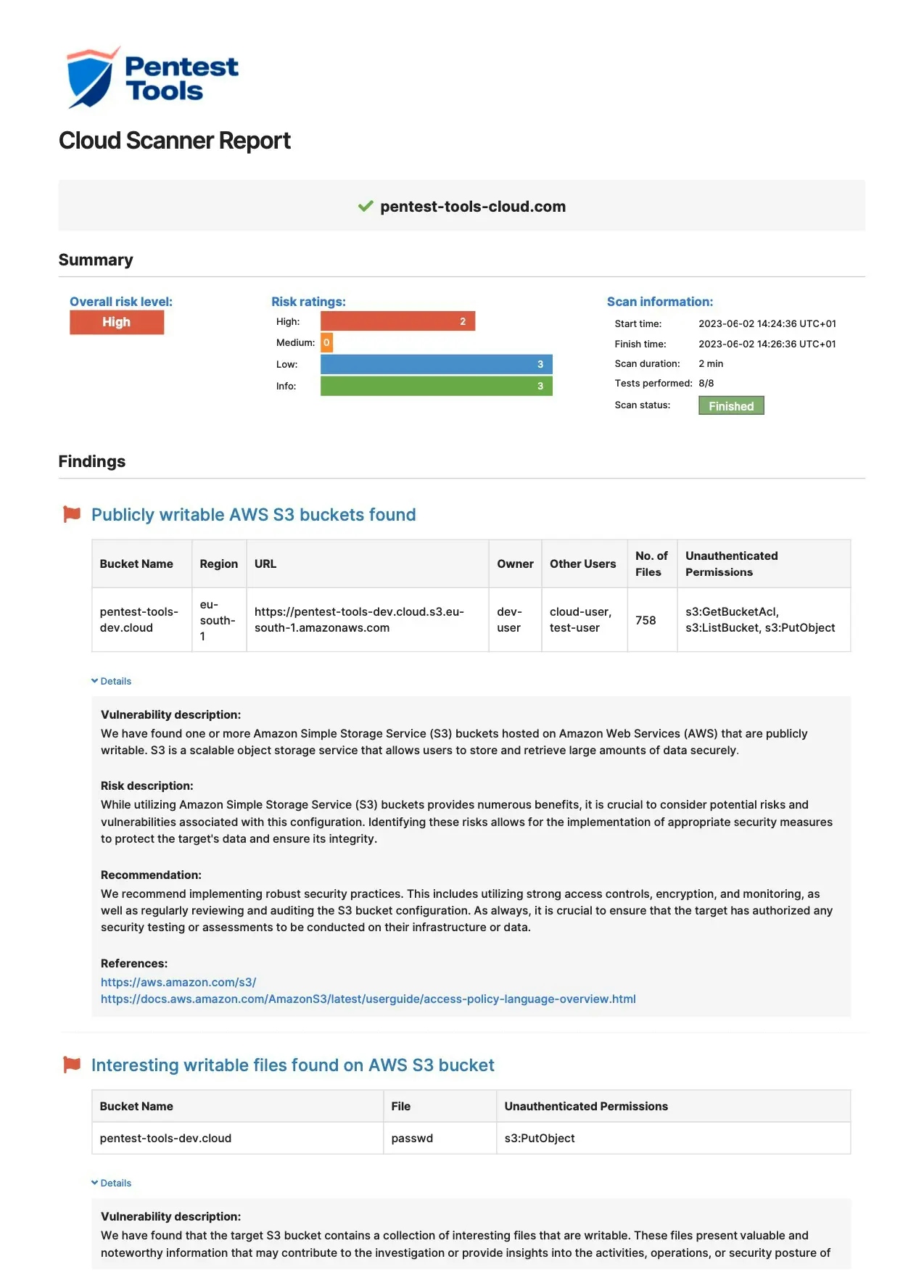
Sample Cloud Vulnerability Scanner report
Each cloud security scan generates detailed findings which are easy to export in PDF, HTML, CSV, XLSX, or editable DOCX reports, based on your subscription. Each report includes:
Vulnerability summary categorized by risk level
See your cloud asset’s overall risk level at a glance, complete with a classification of findings based on risk ratings, and scan details.
Comprehensive vulnerability evidence
See the compromised bucket, its region and URL. Discover the username of the bucket's owner, other users who have access, and see permissions. Prefilled descriptions for each vulnerability and its associated risks make it easy to report this hard evidence.
Ready-to-use remediation advice
Reports about cloud security issues also provide professionally written mitigation recommendations, complete with references and links to documentation - where available.
Advanced pentest reporting options available
Choose a plan that gives you access to customizable .DOCX reports, available through our pentest report generator tool, and speed up this step with ready-to-use or custom templates.
Better vulnerability discovery.Faster pentest reporting.
Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.

Scanning capabilities
How our Cloud Vulnerability Scanner runs deep, accurate scans
- 1
Proprietary, up-to-date detectors developed in-house
The Cloud Vulnerability Scanner has a strong set of detectors to help you discover your target’s:
- Cloud provider (AWS, GCP, Azure)
- AWS S3 buckets
- AWS S3 ACLs
- Overly permissive configurations
- Interesting files inside AWS S3 buckets (wp-config, backup, keys, etc.)
- 2
Constantly updated cloud security testing capabilities
The engineering team behind our Cloud Vulnerability Scanner is constantly working to upgrade its capabilities. The next big improvement coming to this tool is authentication support for AWS targets so you can run internal scans.
- 3
Built-in mechanism for reducing scan errors
If your target has multiple redirects, enabling the Follow redirects option can help you automatically avoid scanning errors.
- 4
Scan S3 buckets by known URL
If you want to scan an AWS S3 bucket directly, just drop the URL (e.g
http(s)://{bucket_name}.s3.amazonaws.com) in the target field and get going! - 5
Functionality battle-tested by penetration testers
We also build and run Pentest-Tools.com in the cloud, so we use our own experience with maintaining strong cloud security to make this tool even more powerful for you.
Use cases
What you can do with the Cloud Vulnerability Scanner
Validate cloud asset security before deployment
Make sure all your cloud-based systems, networks, and applications are vulnerability-free and well configured before launch. All you have to do is sign up, sign in, and start scanning your targets from our online platform – no configuration or on-premise deployment required.
Demonstrate and maintain compliance
To achieve continuous monitoring of your cloud infrastructure, schedule the Cloud Vulnerability Scanner to run regular assessments and notify you when it finds security issues. Compiling findings into comprehensive reports is straightforward, which means security and IT managers can share critical information with the colleagues who can address issues before they become compliance problems.Balance scan depth and time limitations
Strapped for time? (Who isn’t?) Set a custom scan time to manage your cloud vulnerability scans efficiently while freeing up your time for other critical tasks. Let scans run in the background while you tackle other tasks on your to-do list.
Discover exploitable misconfigurations and risks
Adversaries often try to impersonate bucket owners and chain unauthorized access with vulnerabilities to achieve persistence. Thoroughly mapping your attack surface lets you focus on what you do best: act on findings and harden your cloud infrastructure.
Keep a documented trail of evidence for audits
The list of clear, detailed vulnerability scan results serves as up-to-date proof for audits. Exporting reports in various formats takes just minutes for both individual and multiple cloud targets. And you can also prove that you’ve addressed cloud security issues through rescan results.
Use clear risk evidence to get more resources for cloud security projects
Uncover sensitive data with the Cloud Vulnerability Scanner from Pentest-Tools.com, including legal, compliance, or intellectual property information, and highlight the potential damage a malicious hacker can do with it. Use the evidence to prove legal repercussions and reputational damage risks to executives who can approve more resources for cloud security projects.
Or check out 20+ more included tools
We built the Cloud Vulnerability Scanner for
Offensive security teams who need an up-to-date attack surface map, demonstrate the real risks of unauthorized access, automate vulnerability scans and other repetitive tasks, and produce customizable reports from a consolidated list of findings.
Defensive security teams who need to do ongoing cloud security testing, keep an up-to-date inventory of internal and publicly exposed assets (including shadow IT), and push relevant findings to other teams via email, Jira, Slack, or other communication channels.
System builders and admins who need to run regular essential security hygiene checks, put compliance scans on auto-pilot, evaluate their security posture ahead of audits, detect misconfigurations in cloud devices and apps, see which are missing patches, get alerts for new security issues, and automatically send them to colleagues for resolution.
