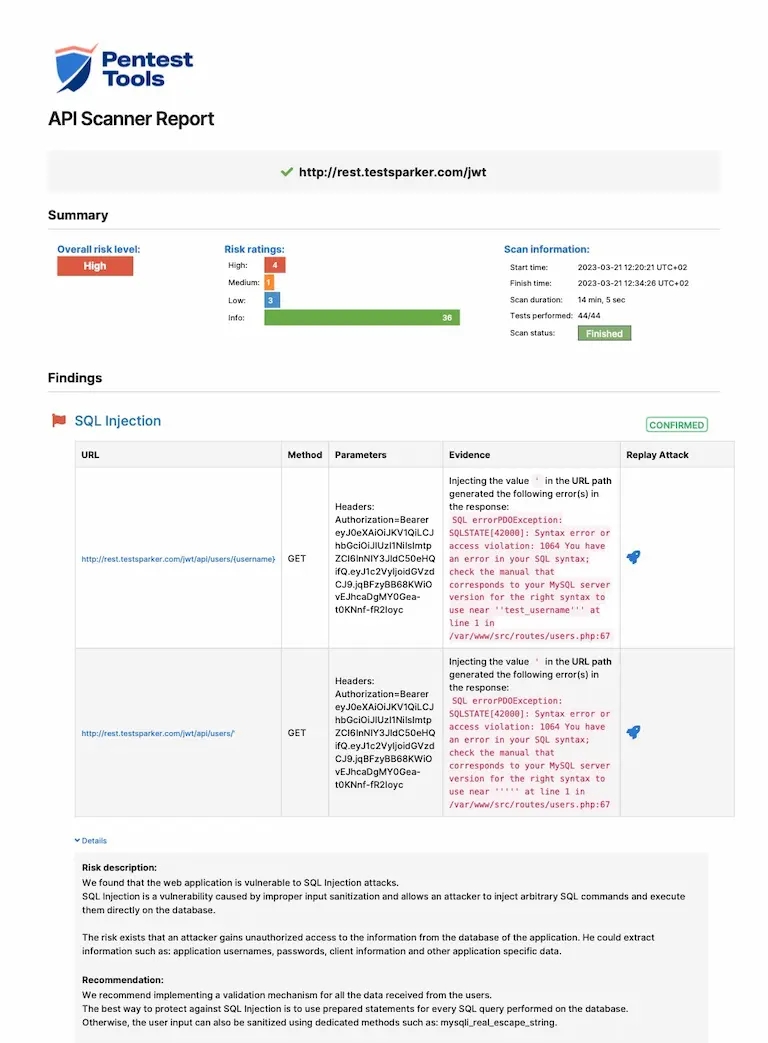
API Vulnerability Scanner
Technical details
Full list of API Vulnerability Scanner tests
| Included | Test |
|---|---|
| Included | Fingerprint web server software |
| Included | Analyze HTTP headers for security misconfiguration |
| Included | Check the security of HTTP cookies |
| Included | Check the SSL certificate of the server |
| Included | Check if the server software is affected by known vulnerabilities |
| Included | Analyze robots.txt for interesting URLs |
| Included | Check if HTTP TRACK/TRACE methods are enabled |
| Included | Check if security.txt is missing on the server |
| Included | Check if CORS is misconfigured |
| Included | Crawl website |
| Included | Check for SQL Injection |
| Included | Check for Local File Inclusion and Remote File Inclusion |
| Included | Check for OS Command Injection |
| Included | Check for Server Side Request Forgery |
| Included | Check for Open Redirect |
| Included | Check for PHP Code Injection |
| Included | Check for JavaScript Code Injection |
| Included | Check for Ruby Code Injection |
| Included | Check for Python Code Injection |
| Included | Check for Perl Code Injection |
| Included | Check for Log4j Remote Code Execution |
| Included | Check for Server-Side Template Injection |
| Included | Check for ViewState Remote Code Execution |
| Included | Check for Client-Side Prototype Pollution |
| Included | Check for Exposed Backup Files |
| Included | Check for Request URL Override |
| Included | Check for Client-Side Template Injection |
| Included | Check for HTTP/1.1 Request Smuggling |
| Included | Check for outdated JavaScript libraries |
| Included | Check for commented code/debug messages |
| Included | Find Login Interfaces |
| Included | Sensitive Data Crawl |