November updates for powerful workflows, including detection for Log4Shell
Giving you the tools you need right now to speed up detection and reporting is always our top priority. Especially when your work is essential to effectively prioritize remediation. So, with every monthly update, we strive to do just that.
When you log into your Pentest-Tools.com account, you can find targets vulnerable to the Log4j vulnerability (CVE-2021-44228) with our Network Scanner and Website Scanner.
FIND VULNERABLE TARGETS DETECT LOG4SHELL
And integrating detection for this critical CVE is not all we did.
Here are 7 more updates we rolled out to make your work more powerful and efficient:
Exploit 4 new high-risk vulns with Sniper Automatic Exploiter
Schedule pentest robots to run automated testing sequences
Delete specific HTTP loggers you created and no longer need
Get detailed scan results with the new, slick Sniper interface
Include Password Auditor findings in your reports
Focus on finding critical CVEs with the Network Scanner
Find Python & Perl code injection issues with new Website Scanner modules
Let’s unpack them!
1. Sniper now automatically exploits these 4 new CVEs (CVSSv3 scores 9.8+)
Confirm, exploit, and do post-exploitation in under 2 minutes with Sniper Automatic Exploiter for:
the RCE vulnerability in Gitlab Community Edition (CE) and Enterprise Edition (EE) – CVE-2021-22205
another critical RCE in the Visual Tools DVR attackers can get using shell metacharacter on Linux- CVE-2021-42071
the Shellshock Bash RCE vulnerability found in Unix Bash shell – CVE-2014-6271
the RCE vulnerability in multiple Apache Struts web applications – CVE-2017-9791
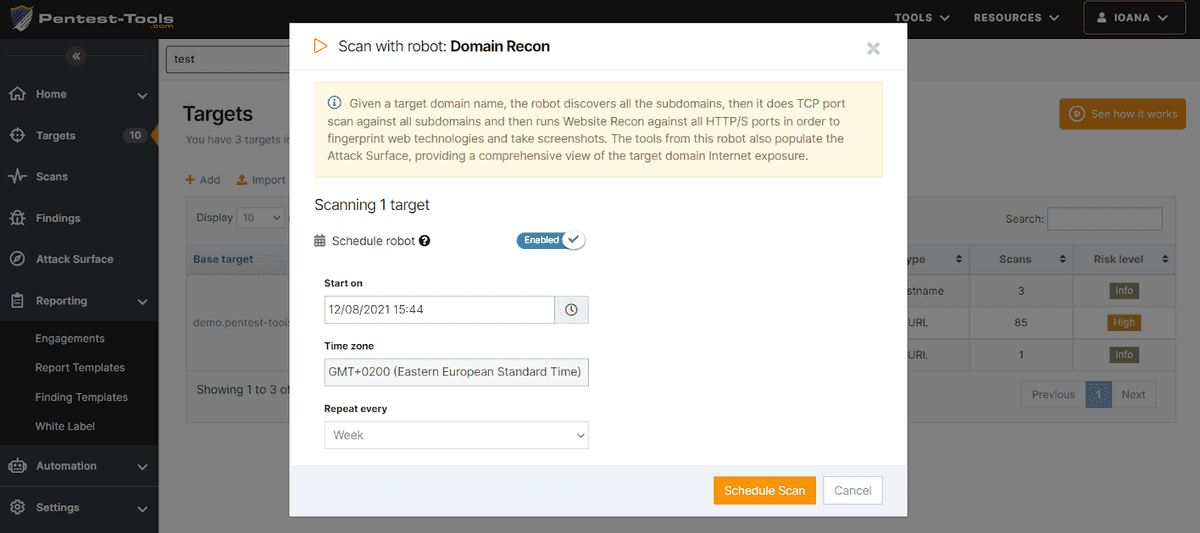
2. Automate periodic, custom testing sequences with scheduled pentest robots
You can now run scheduled scans with a predefined or custom-built pentest robot to automate recurring pentest tasks.
To keep your workflow productive, go to Targets, select a specific URL target, and choose Scan with Robot. Then, select the pentest robot you need, enable Schedule robot, and get scan notifications in your inbox.
Tap into the huge potential of pentest robots:
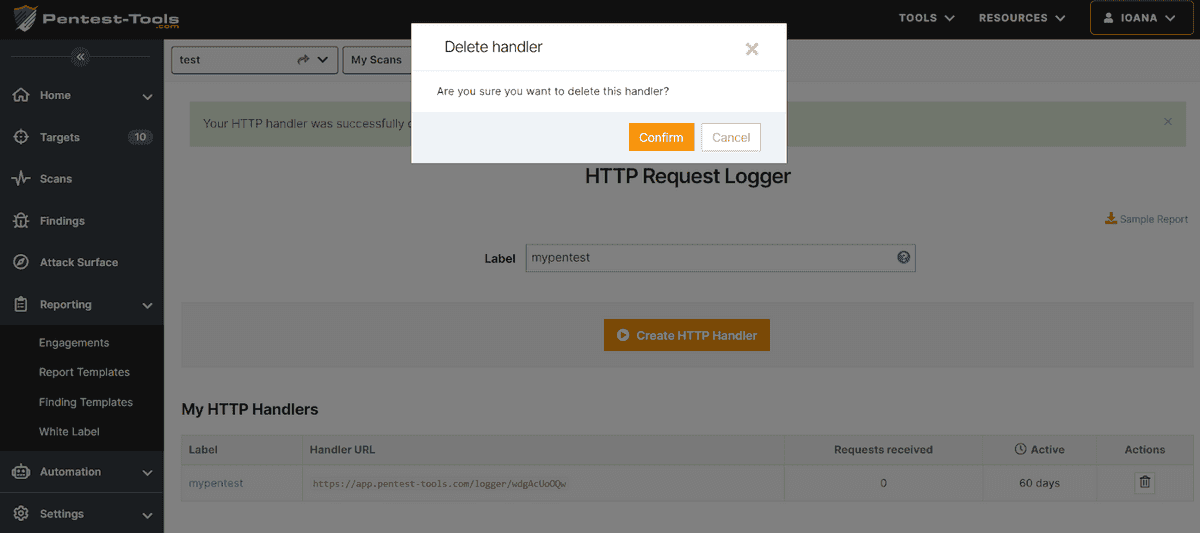
3. Delete HTTP handlers you no longer need
You can now easily delete HTTP handlers you don’t need, even if they are still valid or expired (after 60 days). It helps keep your workspace in top shape!
Go to the My handlers you created, select a specific one, and click on the Actions button.
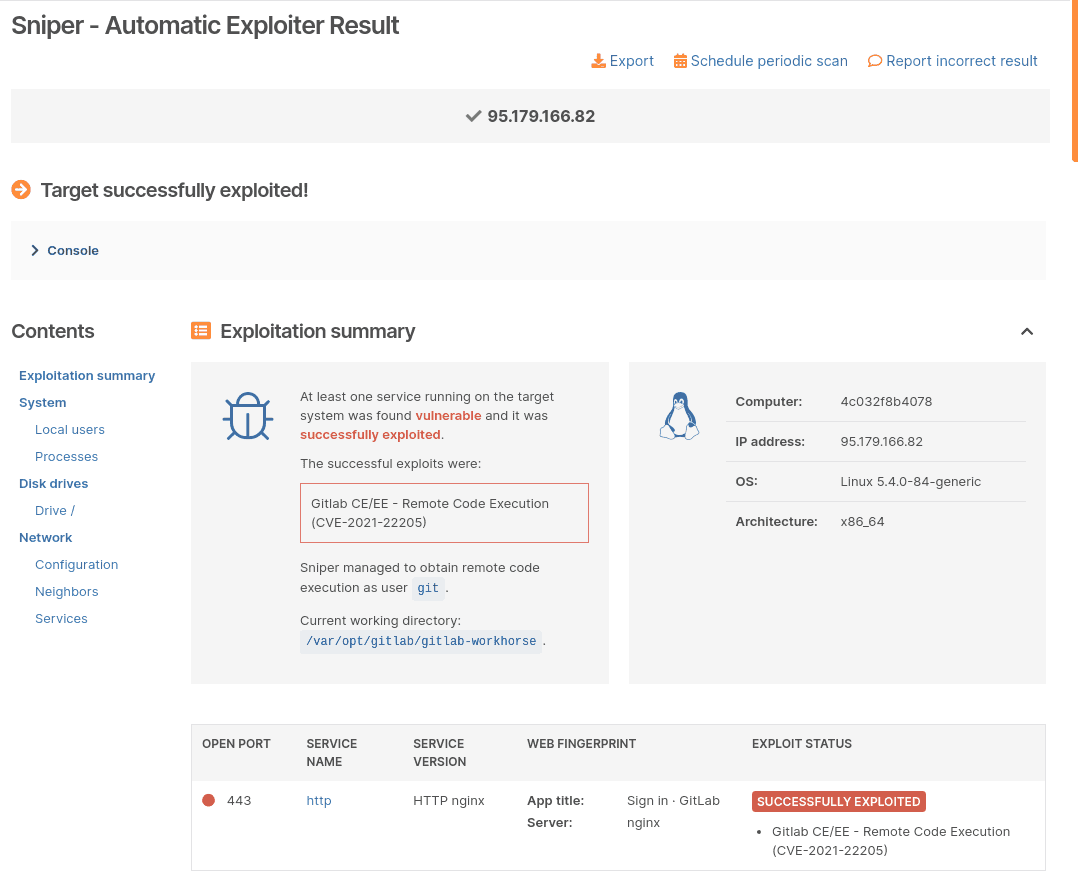
4. Successful automated exploits with Sniper – in a fresh, new interface
Having to wade through volumes of information each day is a tough task. We have your back, as promised!
Our team has revamped the Sniper Auto-Exploiter report and added visual cues plus a handy navigation menu so you can find what you need and export a report in a flash.
Here’s a snapshot of the new report:
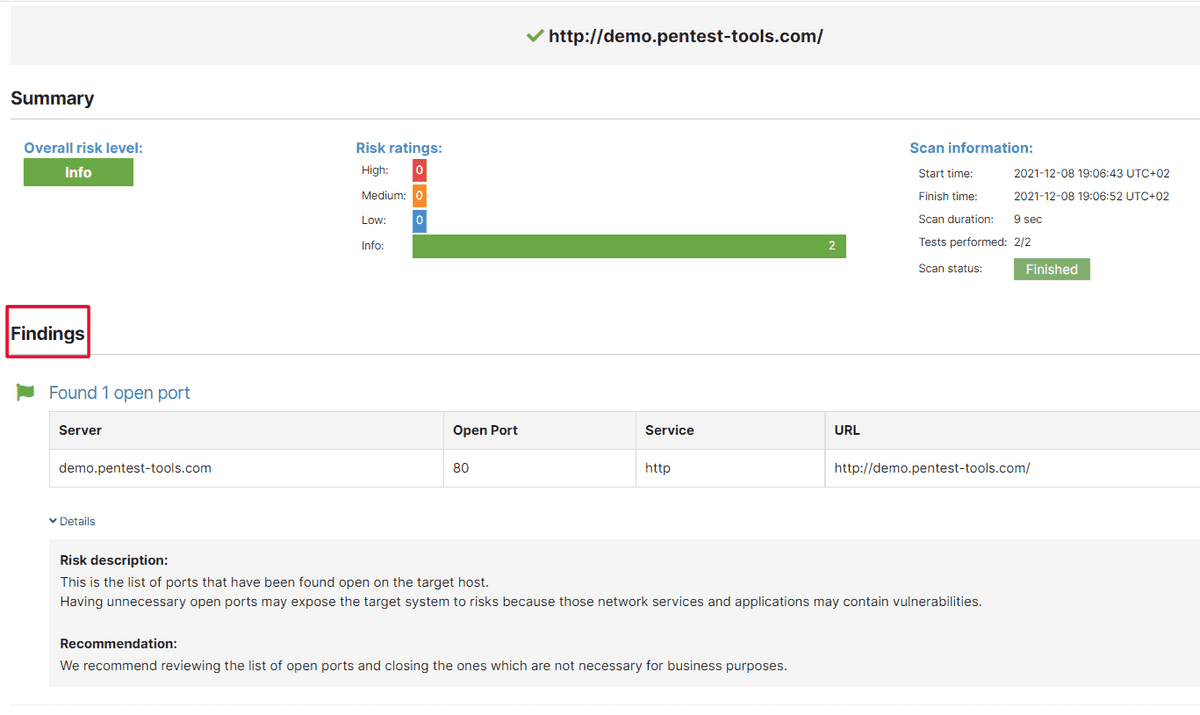
5. Automatically add Password Auditor findings in your reports
We’ve improved our Password Auditor scanner by including the option to generate findings.
Besides finding weak credentials in your web applications, it now adds detailed findings to your reports so you can ship them with even richer recommendations!.
Go to Password Auditor, insert your URL target, run a scan with it, and see results pouring in:
6. Run focused scans with the Network Scanner to find critical CVEs
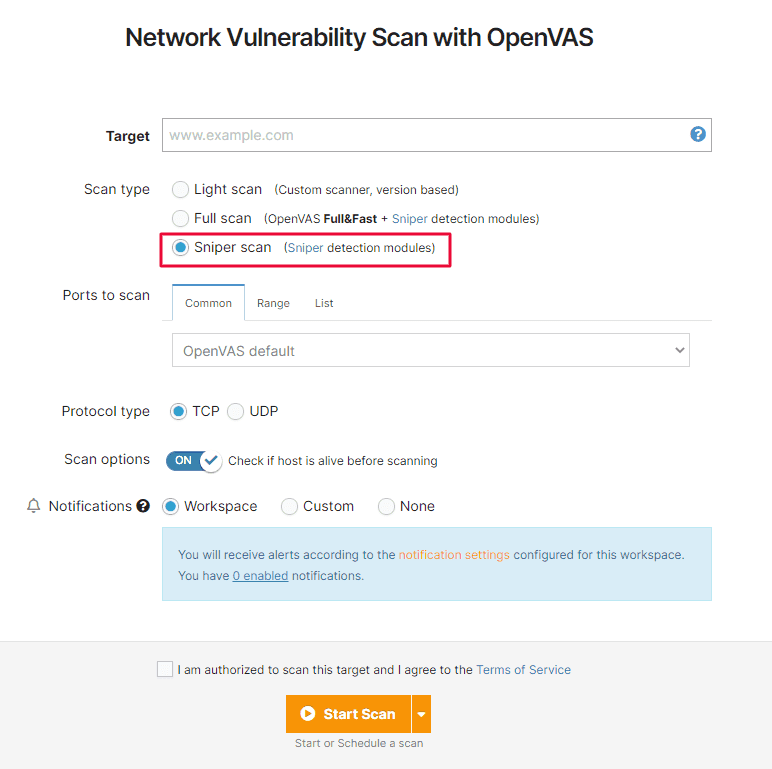
If you want to exclusively check for high-risk, exploitable vulnerabilities in a light, non-intrusive way, try the new option we added to the Network Scanner.
Go to the Network Vulnerability Scanner with OpenVAS, add your URL target, and select Sniper scan:
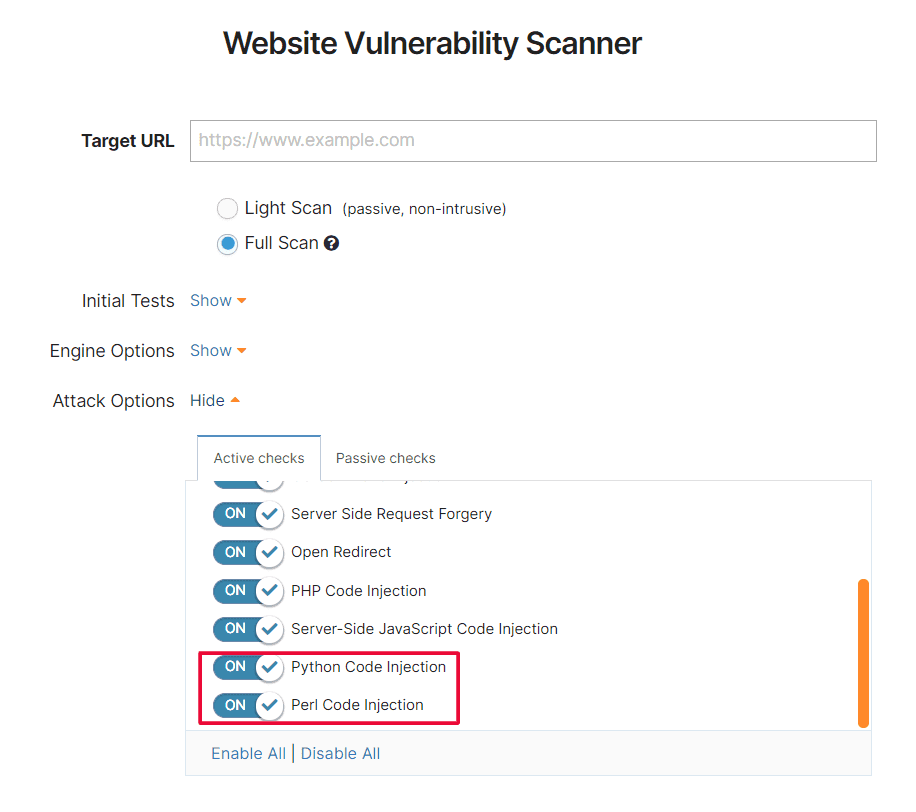
7. Stronger detection for code injection built into the Website Scanner
Our Website Vulnerability Scanner gets more powerful with two new detection modules for Python and Perl code injections in your web applications!
To use it, go to Website Scanner, add your URL target, and select Full Scan. Expand the Attack options, choose the Active checks tab and enable Python or Perl Code Injection (or both, if you need them).
Our scanner engine will analyze the HTTP responses from your target and check for arbitrary Python and Perl code.