January updates: new pentest robots and stronger integration
“Great for streamlining any security engagement” is the kind of feedback that keeps us working to roll our monthly updates.
Here’s what we did last month to honor this commitment. Now you can:
Confirm exploitability for 9 new high-impact CVEs with Sniper
Detect 11 widespread vulnerabilities with our Network Scanner
Automate network scanning tasks with these new pentest robots
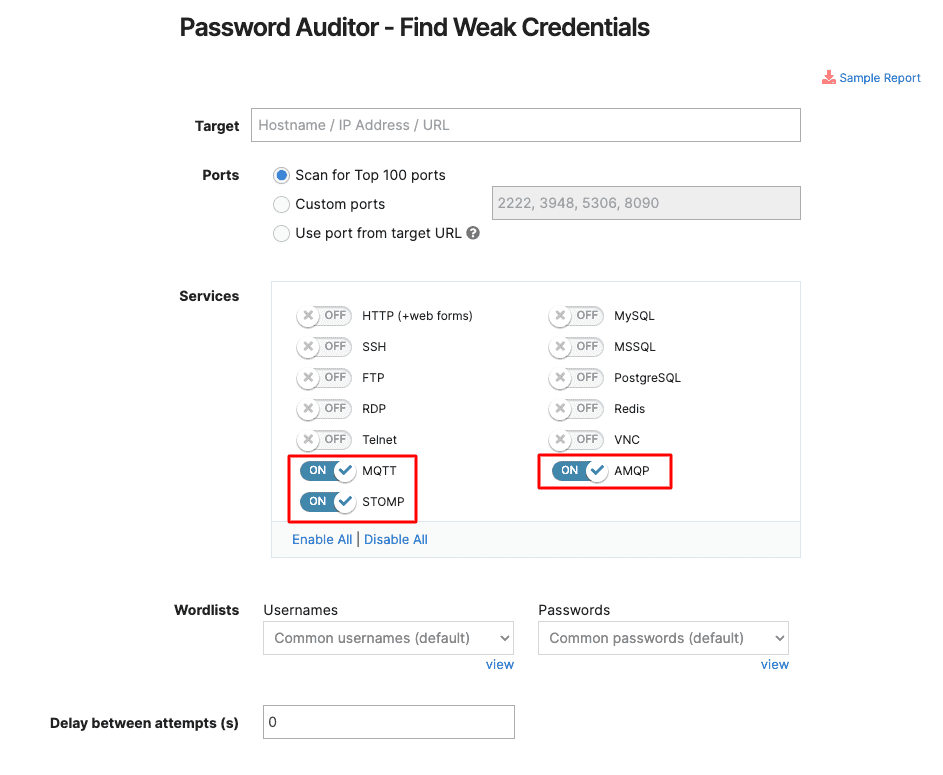
Find more weak credentials in MQTT, AMQP, or STOMP services
Exploit Network Scanner findings with Sniper faster
Notify team members about specific scan results in real-time (+ more triggers)
Let’s unpack these updates
1. Get exploitation proof for these 9 new critical CVEs with Sniper
Our vulnerability research team did a massive effort last month to integrate 9 more exploit modules for the latest high-risk vulnerabilities.
Sniper Automatic Exploiter now gives you exploitation proof in under 2 minutes for:
the RCE vulnerability in multiple Netgear routers that attackers can exploit without authentication – CVE-2020-1749 (CVSSv3 7.5) and CVE-2020-27866 (CVSSv3 8.8)
the notorious Log4j vulnerability in Java logging packages – CVE-2021-44228 (CVSS v3 10.0) and CVE-2019-17571 (CVSSv3 9.8)
the path traversal vulnerability in various Grafana versions – CVE-2021-543898
the REST API authentication bypass vuln in the Zoho ManageEngine ADSelfService Plus – CVE-2021-40539 (CVSSv3 9.8)
the high-risk RCE vulnerability in multiple Oracle WebLogic servers – CVE-2018-2894 (CVSSv3 9.8) and CVE-2020-14883 (CVSSv3 7.2)
another RCE vulnerability was discovered in various Apache Struts versions – CVE-2018-11776 (CVSSv3 8.1)
2. Detect 11 high-risk vulns with the Network Scanner
As one of the top 3 most used tools on the platform, we frequently update our Network Scanner with new detection capabilities. You can now use it to check for the above CVEs plus:
the Server Side Request Forgery (SSRF) vulnerability in Apache HTTP servers- CVE-2021-40438 (CVSSv3 9.0)
the widespread Log4Shell vuln in Apache Solr, Tomcat, Druid, and Flink instances plus VMware vCenter & Mobilelron Core servers – CVE-2021-44228 (CVSSv3 10.0)
For faster scans, use our Log4Shell pentest robot to effectively detect Log4Shell in your engagements.
3. Automate network scanning tasks with these 2 new pentest robots
To make the most of your time and detect critical vulns in your networks, you can run our ready-to-use pentest robots or build your own.
We’ve just added 2 new Network Scanner robots you can use the moment you log into your Pentest-Tools.com account.
The Network Scanner Full (domain) starts by discovering all subdomains of a target domain and continues by checking for unique IPs on each machine. Then it runs the Full Network Scanner for each machine within the network of the target domain to detect potentially vulnerable systems.
The Network Scanner – Critical CVEs (domain) runs more focused scans using a domain as an entry point. It identifies all the target’s subdomains and continues to checks for unique IPs on the machines. Then it runs the Network Scanner with Sniper’s detection modules Sniper detection modules for each machine within the network of the target domain.
Both pentest robots compile a thorough report with rich findings to use in your engagements.

4. Discover more weak credentials with support for these services
If you’re using MQTT, AMQP, or STOMP services, run our Password Auditor against your targets to automatically find default and weak credentials in them.
Go to Password Auditor, add your target, and enable the service of your choice. Yes, that’s all!
5. Exploit Network Scanner findings with Sniper faster
When you run a Full Scan with our Network Scanner, it also includes Sniper’s detection modules by default.
If you discover interesting findings you’d like to exploit further, you can do it quickly with the new “Exploit with Sniper” button.
Here’s where you’ll find it:
Add another phrase about what happens after they click the button.
After clicking on it, run a focused scan with Sniper to exploit and extract artifacts from the target system. 
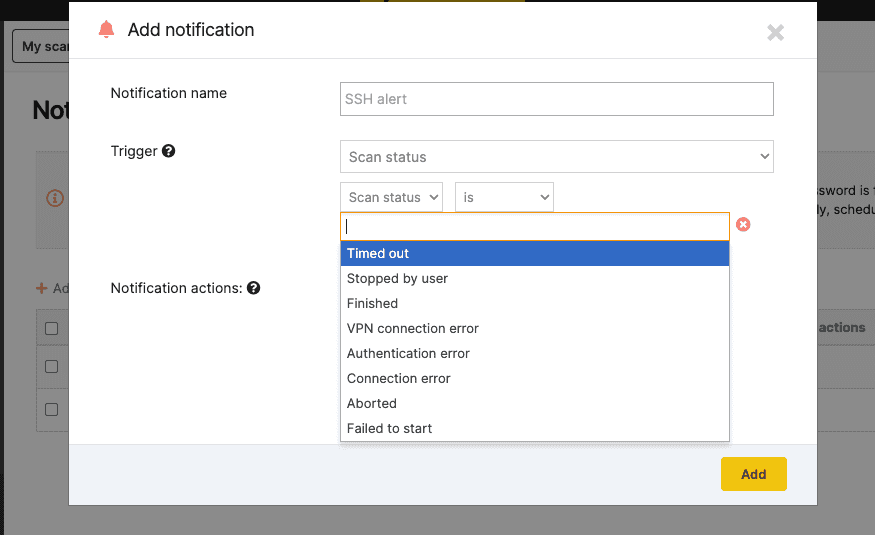
6. Send real-time scan notifications to specific users
Need to notify your team or multiple users about specific scan results? There’s an easier way to do it on Pentest-Tools.com.
Go to Settings, select Notifications, and fill in specific conditions for your scans.
When scan results match all your selected conditions, the users you added get an email with all the details.
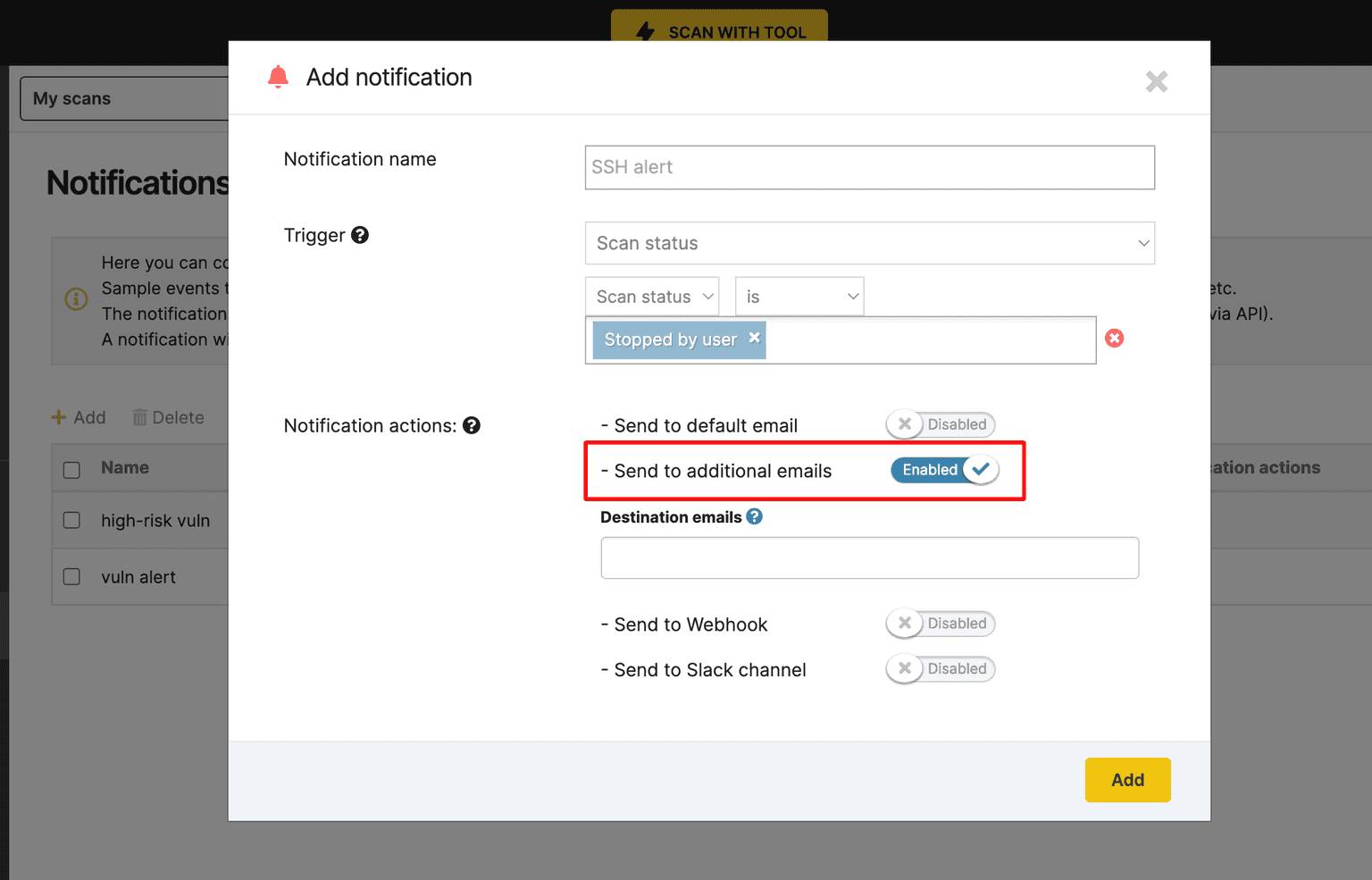
What’s more, we’ve added new triggers (e.g. stopped by user, VPN connection error, Authentication error) to make notifications more helpful to you and your team.
Send laser-focused scan notifications to your inbox or to your webhook URL to streamline collaboration and keep everyone in the know.
Do these updates improve your pentesting workflow? Let us know in a comment below or send us your feature requests.