March updates: Spring4Shell: find and confirm exploitable targets and more updates
- Article tags
If you instantly thought of Log4Shell when Spring4Shell emerged just a few days ago, you’re not alone. A coolheaded analysis reveals this CVE is not as severe as last year’s Log4j vulnerability. Nevertheless, it remains a priority in terms of detection and patching. Here’s why.
CVE-2022-22965 affects the Spring Core Framework (MVC and Spring WebFlux applications) running on Java, which developers widely use in their work. CISA also added this CVE to its catalog of Known Exploited Vulnerabilities, emphasizing that malicious actors are actively using it in their attacks.
To help you find vulnerable targets and prioritize business-critical ones for patching, our security research team just launched detection and exploitation modules for Spring4Shell.
Log into your Pentest-Tools.com account to search for targets affected by this CVE with our Network Scanner and Sniper.
And that’s not all we did.
In the past month, we also rolled out a new stack of updates to support your security testing efforts:
3 new high-risk CVEs you can exploit with Sniper
Option to define a minimum weight value in Find Domains scans
The ability to run authenticated scans with Sniper Auto-Exploiter
Let’s unpack them!
1. Confirm exploitation risk for these 3 critical CVEs with Sniper
Besides Spring4Shell, our security research team also updated Sniper Automatic Exploiter with exploitation capabilities for:
the RCE vulnerability affecting specific Spring Cloud Gateway and Function versions – CVE-2022-22947 (CVSSv3 10.0)
another RCE vulnerability that impacts different Spring Cloud Function versions – CVE-2022-22963 (CVSSv3. 9.8)
the critical RCE vulnerability found in Apache Struts – CVE-2017-12611 (CVSSv3 9.8)
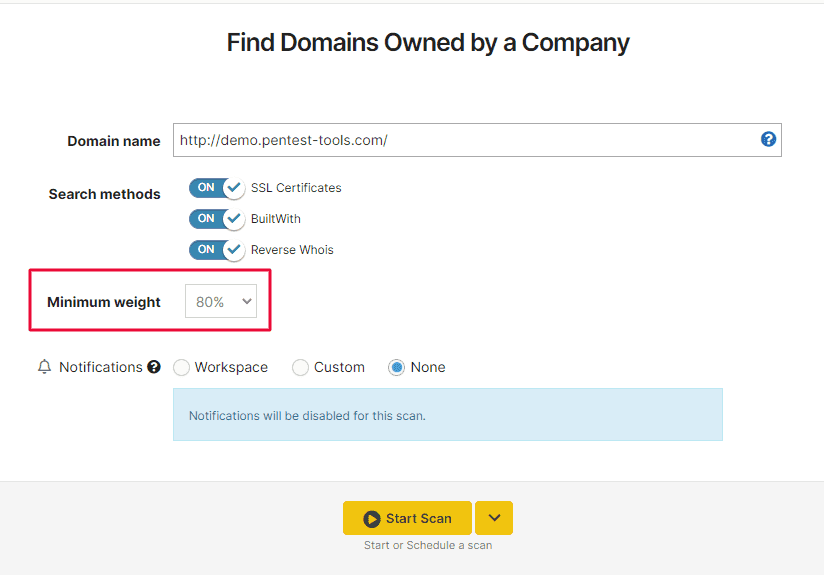
2. Specify a minimum weight value and use it with Find Domains
You now have the option to set up a specific minimum weight value when running scans with Find Domains. This allows you to better filter scan results and validate the accurate ones.
To use it, go to Find Domains, add your target, and select a minimum weight to get more detailed results filtering.
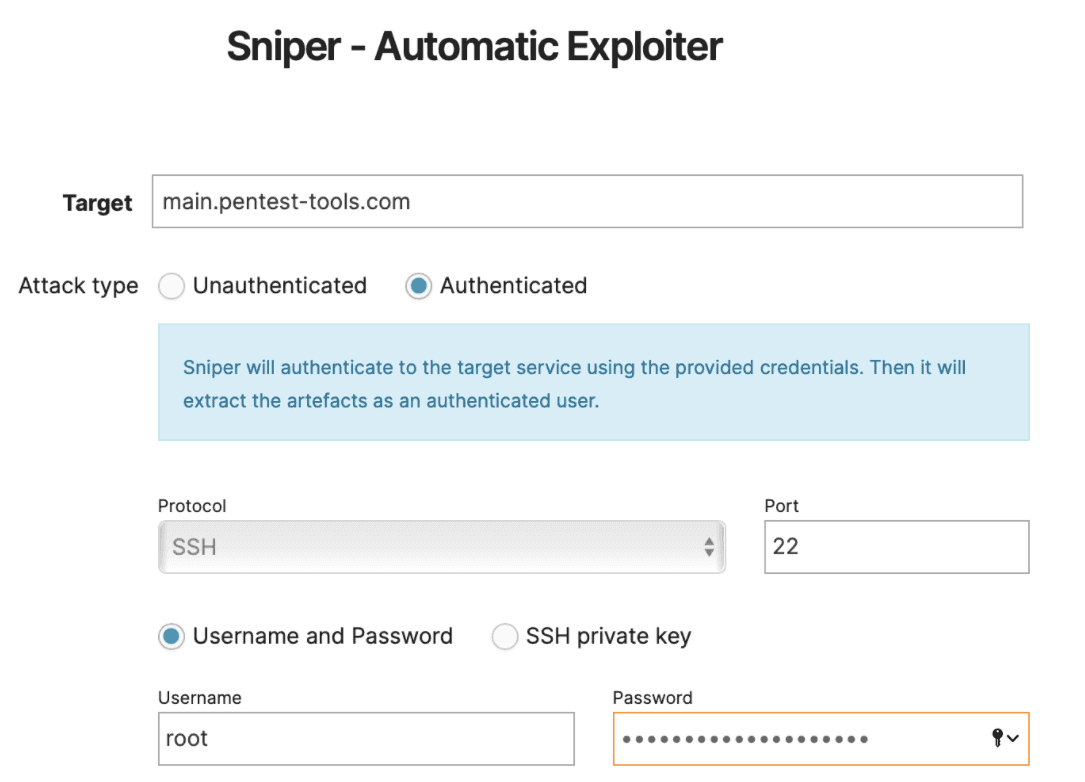
3. Get better PoCs with Sniper authenticated scans
We enhanced Sniper Auto-Exploiter with a new feature that allows you to perform authenticated scans and get even richer details about your targets for PoCs.
Sniper authenticates to your target system with the credentials you provide and extracts the artefacts as an authenticated user.
Check out the steps in our dedicated support article to learn how to use this new Sniper feature.
Hope these updates help you streamline your pentesting engagements and do more of the things you enjoy.