February updates: run deeper, more comprehensive scans

Supporting your ethical hacking engagements is what we do with each new batch of monthly updates we roll out.
Here’s how we walk the talk:
Confirm exploitation risk for 4 critical CVEs with Sniper
Detect 7 critical vulnerabilities with the Network Scanner
Find CORS config issues & SSTI vulns with our Website Scanner
Automate your workflow with the new All Domains Recon robot
Use wordlists with Find Subdomains
Let’s unpack these updates:
1. Confirm exploitability for these 4 critical CVEs with Sniper (CVSSv3 scores 9.0+)
Our security research team continues to work each month to integrate new exploit modules for the latest high-risk vulnerabilities.
With Sniper Automatic Exploiter, you get exploitation confirmation in under 2 minutes for:
the critical RCE vulnerability in Zabbix instances. This is part of the CISA (the US Cybersecurity and Infrastructure Security Agency) catalog of actively known exploited vulnerabilities that threat actors use – CVE-2022-23131 (CVSSv3 9.8)
the high-risk vulnerability affecting specific Apache Struts 2 versions – CVE-2021-44228 (CVSSv3 10.0) and CVE-2021-45046 (CVSSv3 9.0)
the authentication bypass vulnerability in Zoho ManageEngine Desktop Central – CVE-2021-44515 (CVSS v3 9.8)
2. Detect 7 high-risk vulns with the Network Scanner
Our Network Scanner, which you’re probably already familiar with, constantly gets new detection modules.
Case in point, you can scan your targets and check for the above CVEs plus:
the authentication bypass vulnerability discovered in Oracle WebLogic servers CVE-2020-14882 (CVSSv3 9.8) and CVE-2020-14483 (CVSSv3 7.2)
the RCE vulnerability (EternalBlue) found in Microsoft Windows SMB Servers CVE-2017-0144 (CVSSv3 8.1)
Use the Full Scan option from our Network Scanner and get a comprehensive report pre-filled with helpful remediation info to prioritize your most important business assets.
3. Better detection with 2 new Website Scanner modules
Our Website Scanner just got stronger with two new detection modules for CORS (Cross-Origin Resource Sharing) misconfiguration issues and SSTI (Server-Side Template Injection) in your web applications.
To make the most of it, go to Website Scanner, add your URL target, and select Full Scan.
Then, enable CORS misconfiguration from Initial Tests and Server-Side Template Injection from the Attack options (Active checks tab). Or choose one, if you don’t need both.
Our scanner engine will analyze the HTTP responses from your target and look for misconfigured CORS mechanisms and improper input validation.

4. Automate your workflow with the new All Domains Recon robot
To automate those tedious tasks and have more time for the work you enjoy, run focused scans with the new All Domains Recon Pentest Robot.
The All Domains Recon Robot is an enhanced version of the Domain Recon Robot and starts by discovering all domains of a target. It only filters high-certainty results (greater or equal to 80%) and continues to discover all subdomains found on the target.
Then, it does a Top 1000 port scanning and service discovery. Finally, it runs the Website Recon to gather services, technologies and take screenshots. The robot aggregates all the data in the central, unified Attack Surface view.

To use it, go to Targets, choose Scan with Robot and run focused scans with the new All Domains Recon Pentest Robot:

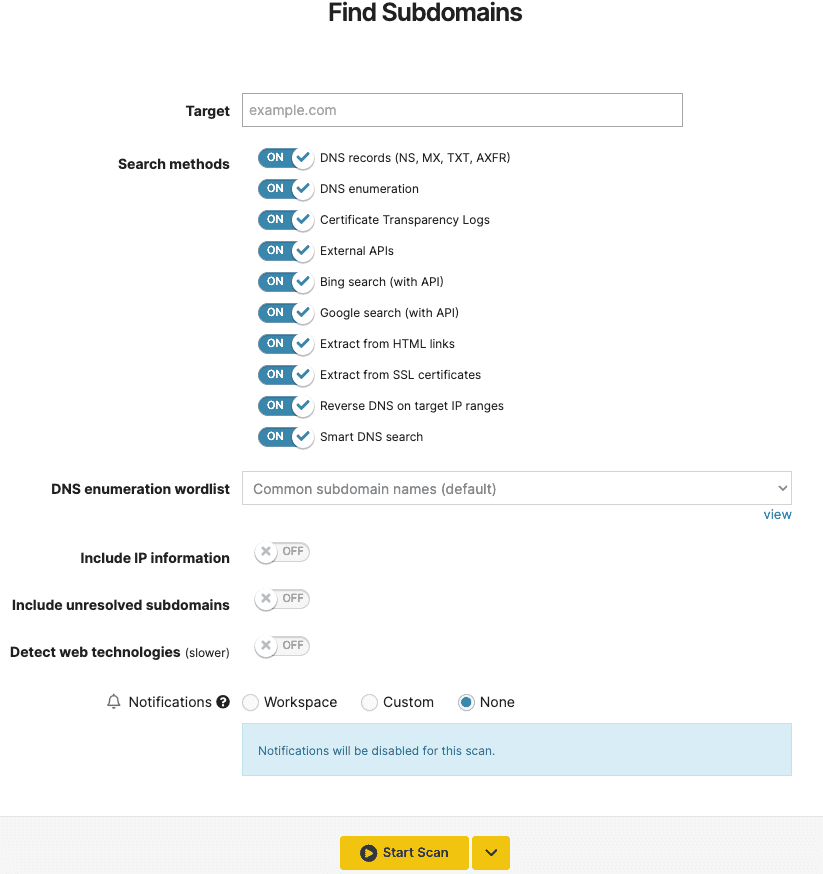
5. Set up your own wordlist and use it with Find Subdomains
As promised, we continue to add more wordlists for our security tools.
The Find Subdomains tool now includes the option to create your own list of usernames and passwords or use a default one.
This speeds up how you detect new subdomains using DNS Enumeration.
To create your own, go to Wordlists, select Add, and start including the list of words you need to run specific pentesting tasks.
After creating your custom wordlist, go to Find Subdomains, insert your target, select the specific wordlist, and run a focused scan with it. That’s all!
Hope these updates make your workflow and help you focus on the tasks that you enjoy the most.