From bypass to breach: how to get RCE in Confluence's latest CVEs

When a CVE - or two - start trending, every pentester instantly asks these three questions:
Why does this happen?
How does it happen?
How do I exploit it?
I’m gonna help you get the answers you need by demonstrating how to go beyond authentication bypass and achieve RCE using CVE-2023-22515 and CVE-2023-22518.
Together we’ll explore their root causes and how to demonstrate the risk involved if an attacker uses these CVEs successfully.
Let's jump right in!
Authentication Bypass in Atlassian Confluence (CVE-2023-22515)
The first CVE we'll examine is CVE-2023-22515. This is a Broken Access Control vulnerability that affects Confluence Data Center and Server instances, with a 9.8 CVSS score. Because it’s a particularly nasty security issue, CISA also added to their Known Exploited Vulnerabilities Catalog.
The root cause of this vulnerability is an access path that doesn’t have authentication checks. An attacker can access the /server-info.action path, which requires no authentication, to put the application in Setup Mode. In this mode, the attacker can create an admin user with no authentication requirements.
Let’s see how this works in practice.
How to exploit CVE-2023-22515
We have a vulnerable Confluence instance that we used when we developed the Sniper module for this CVE.
As you can see, we are logged in as admin, and there are a lot of other accounts as well.
There’s no demo user, so we’ll try to create it.
First, we need to put the app in setup mode, and we do this by performing a request to the /server-info.action path with the bootstrapStatusProvider.applicationConfig.setupComplete parameter set to false.
This tricks the app into thinking the setup is not finished yet, which allows us to create a new account, with admin privileges - without being authenticated.

/setup/setupadministrator-start.action endpoint.
Here, we’re prompted with a form, which allows us to create a new user.


This compromises the confidentiality, integrity, and availability of the Confluence instance.
Using this vulnerability an attacker can achieve Remote Code Execution.
We’ll see exactly how to get to this point in the second part of this article, as the process is identical for the next vulnerability.
Improper Authorization Vulnerability in Confluence Data Center and Server (CVE-2023-22518)
The second security issue we’re dissecting is CVE-2023-22518, another critical vulnerability in the Atlassian Confluence Data Center and Server. It’s also part of CISA's Known Exploited Vulnerabilities Catalog and has a 9.1 CVSS score.
The root cause of this vulnerability is an access path that doesn't have authentication checks either.
An attacker can access the /json/setup-restore.action path, which requires no authentication.
A bad actor can use this endpoint to upload a restored zip file, which will overwrite the site's data with the data from the provided zip file.
This way, the attacker can upload an especially crafted zip file that contains an admin user with a known password - and achieve authentication on the target as admin.
How to exploit CVE-2023-22518
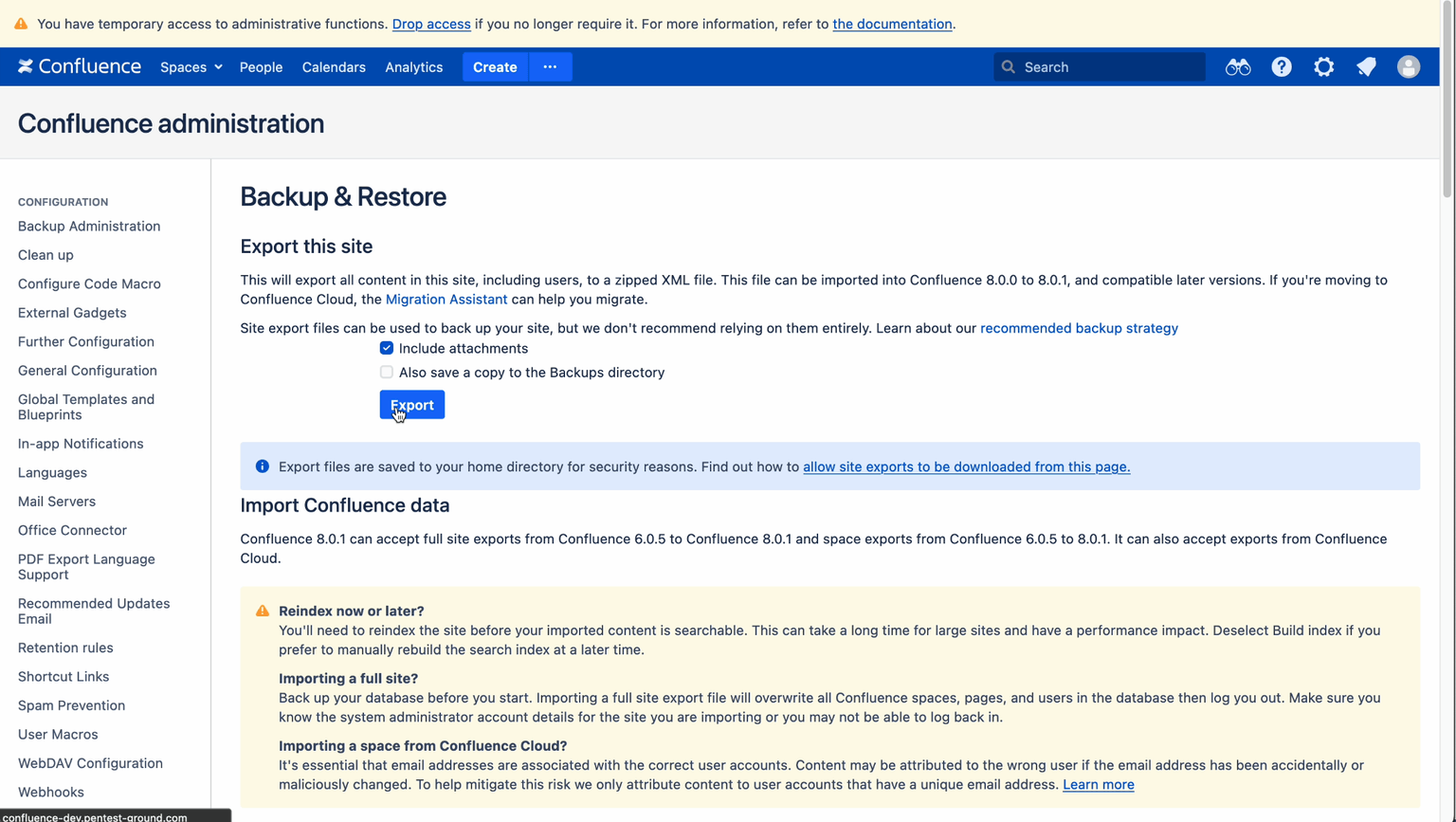
To exploit this vulnerability, we need to get a zip file with known users in it.
As a pentester, you can easily do this by going to Administration > General Configuration > Backup and restore and generate an archive here.

As you can see, this is a cleaner instance, with only one admin user. But things are about to change…
Let’s make a request to the /json/setup-restore.action endpoint with the synchronous parameter set to true.
The request also contains the data from the zip file in our request.

Now let's try to get RCE.
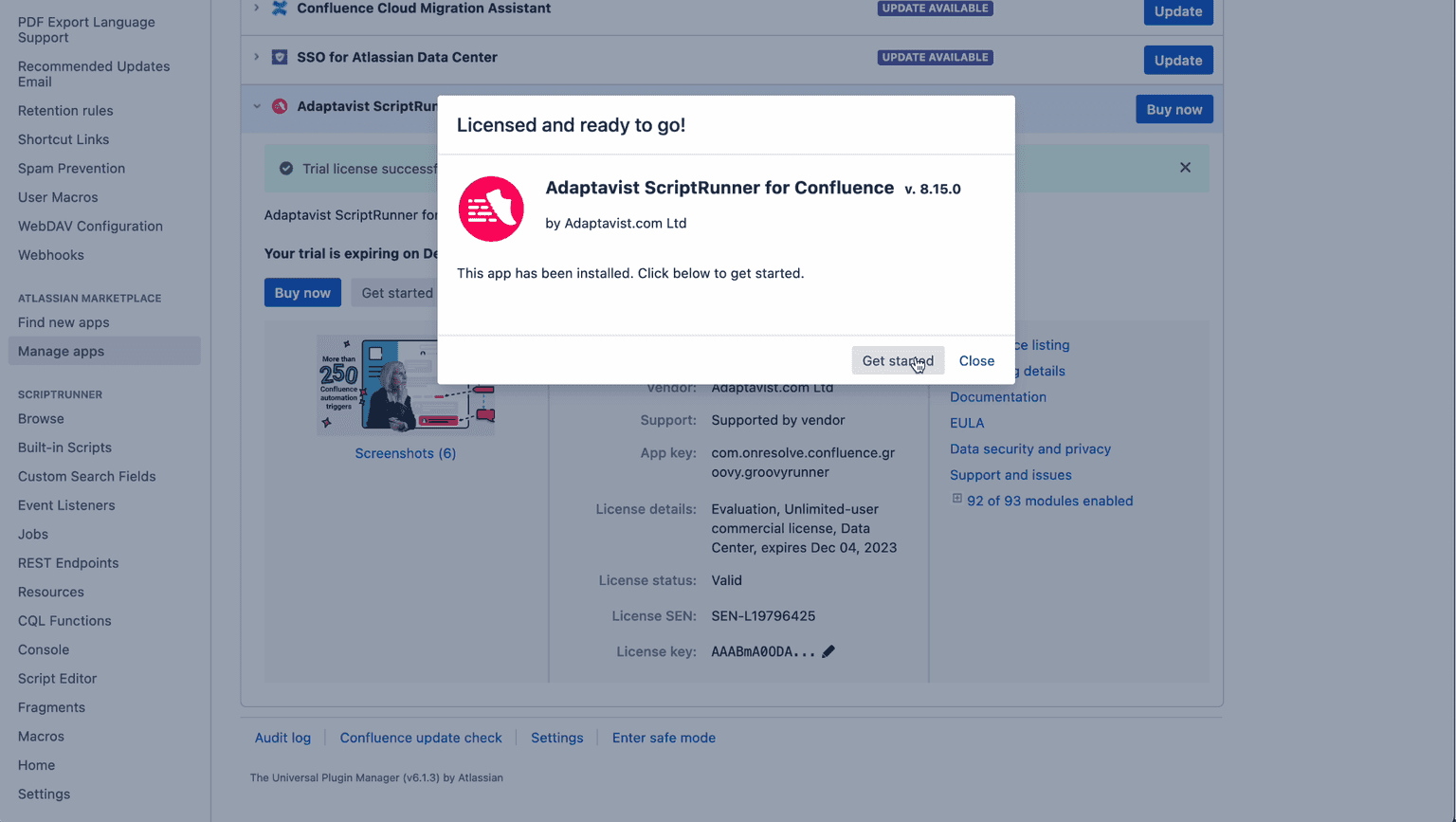
We can achieve this by using our admin privileges to install ScriptRunner. ScriptRunner is a paid app, but we can get a free trial license for it, as 30 days are enough for our goal.
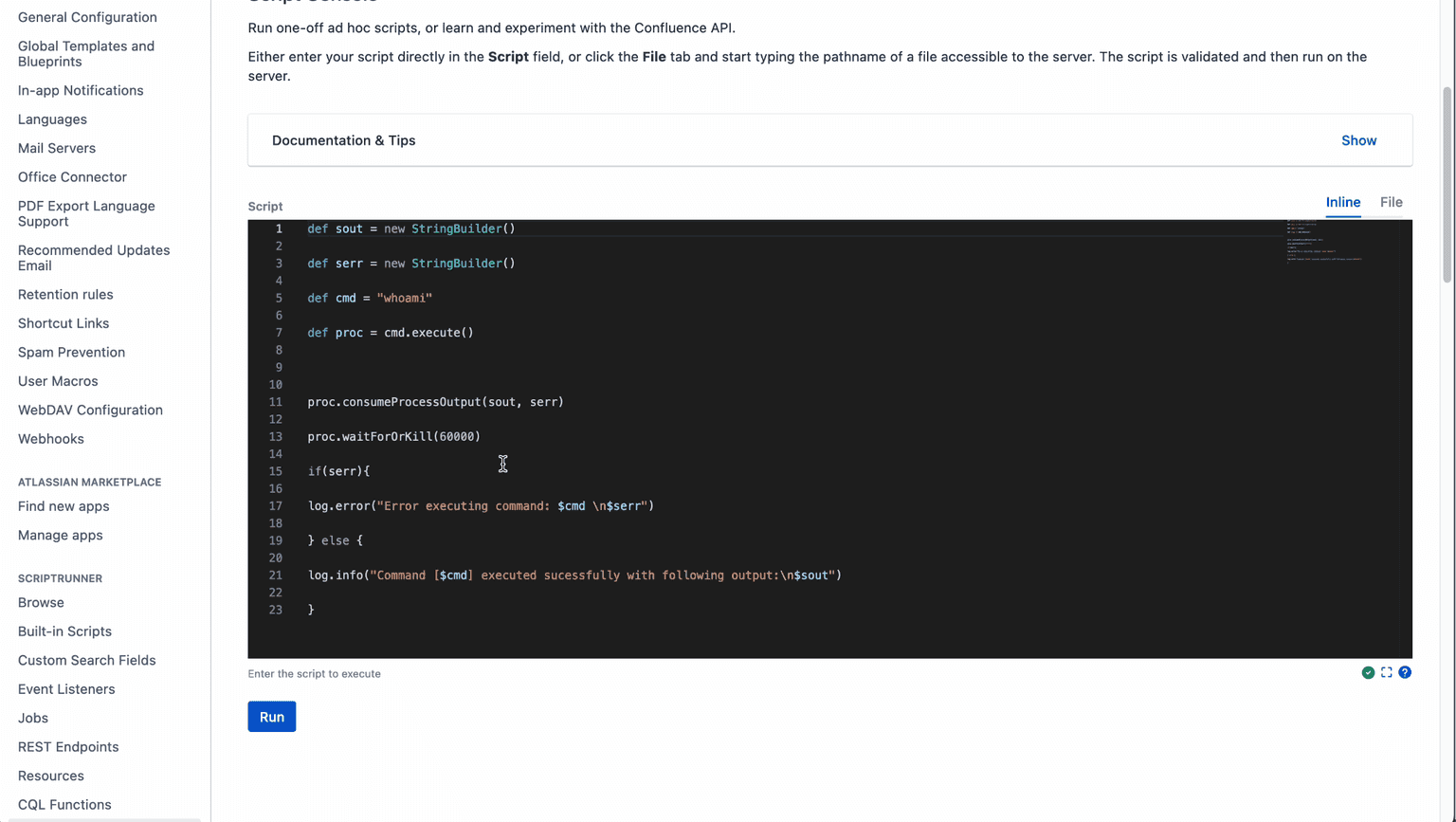
We created the handler, and now let's perform a post request containing the data from /etc/passwd to it.
Looks like it worked and we got the data on the handler! 💪

The good news is that, if you're compromised, the attacker can’t access any confidential data. The bad news is that neither can you.
The vulnerability can allow an unauthenticated attacker with network access to the Confluence Instance to restore it and eventually execute arbitrary system commands.
At Pentest-tools.com we have integrated both detection and exploitation capabilities for these vulnerabilities if you choose to use our Network Scanner and Sniper Auto-Exploiter.
I hope you found this article useful and learned something insightful about these high-risk CVEs!
If you want to see this article as a video PoC, here it is:

For which other vulnerabilities would you like me to demonstrate the exploitation process? Let me know in a comment on the video above.