Google Hacking
Technical details
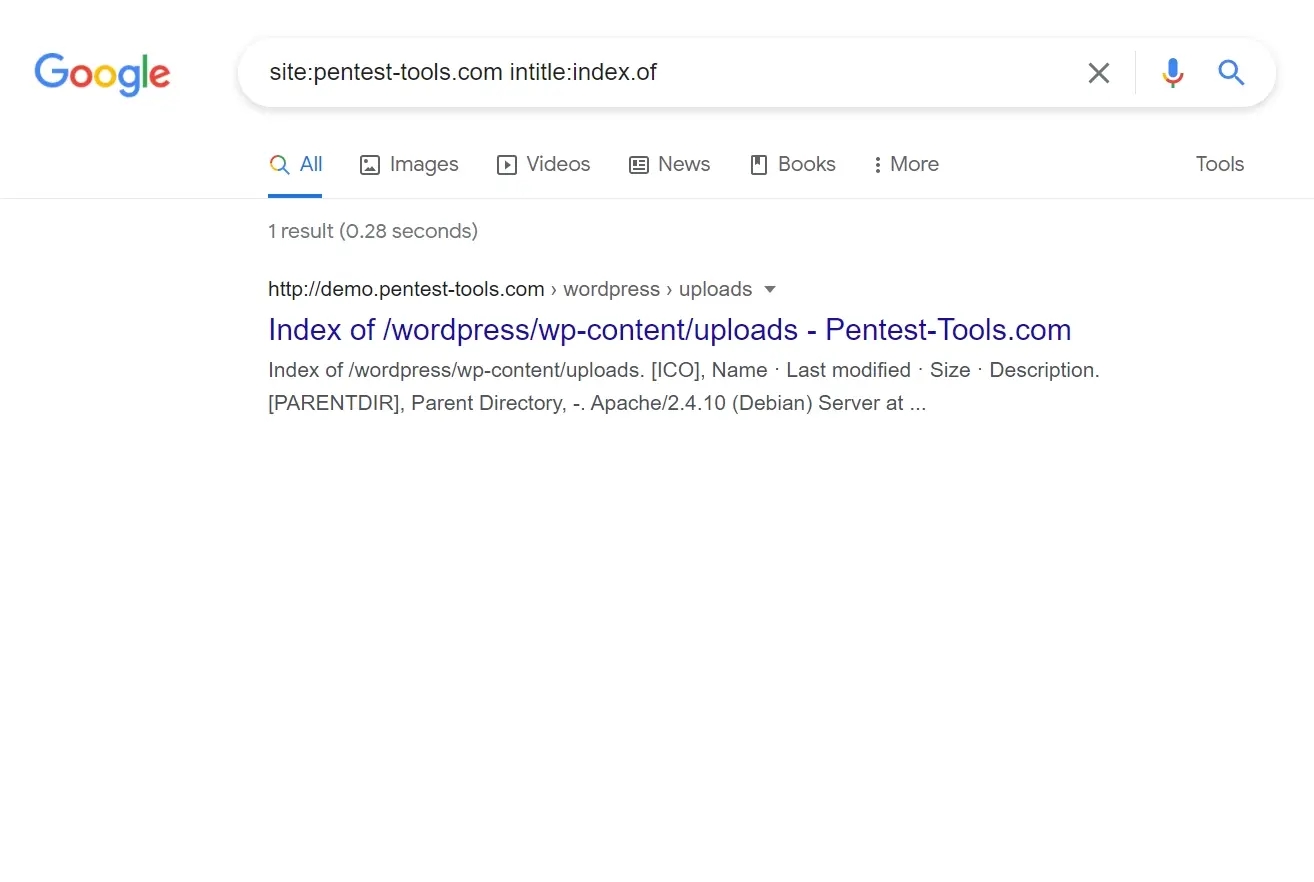
Every penetration test should start with a passive reconnaissance phase. Public search engines gather amounts of information about almost every website from the Internet. It's a good idea to make specific queries and get relevant data. Use them to discover sensitive information or data that’s not supposed to be public.
Google has a set of advanced search operators to use and find interesting information about a target website or domain.
Our free tool aggregates different Google dorks sources you can use to extract sensitive information. Discover more Google dorks here.
Parameters
| Parameter | Description |
|---|---|
| Target website / domain | As the name says, this is your target website or domain for which you are querying Google. When you specify a domain name (e.g. adobe.com), Google will return results for all subdomains of adobe.com such as: repo.adobe.com, get.adobe.com, rmsdemo.adobe.com etc. |
How it works
The Google Hacking tool uses your browser to run queries to Google. Use the free Google dorks to run queries fast and discover interesting information about your targets.