Detect Microsoft Exchange RCE #proxynotfound with our Network Vulnerability Scanner

Running on-prem Microsoft Exchange servers?
If you didn’t catch the NSA boilerplate announcement, there’s another batch of vulnerabilities to scan for – and we built what you need.
We just added a new detection module to our Network Vulnerability Scanner. It checks if your Exchange servers are vulnerable to the attack chain that exploits four recent CVEs and results in Remote Code Execution.
Ours is the second scanning tool of its kind in the world that can identify vulnerable servers remotely. That means you can probe systems by connecting to the target through the network, without local access or credentials.
Here’s why we built it.
No advisory? No PoC? No problem!
Since these CVEs were published (April 13, 2021), we’ve been looking for a detailed technical advisory – but it never came. No solid PoC exploit scripts surfaced either, so we took matters into our own hands.
Our team built a detection module that identifies Exchange servers vulnerable to the combination of pre-auth and post-auth vulnerabilities the NSA disclosed:
CVE-2021-28480 – CVSSv3 9.8
CVE-2021-28481 – CVSSv3 9.8
CVE-2021-28482 – CVSSv3 8.8
CVE-2021-28483 – CVSSv3 9.0
Bad actors love these because the first two vulns don’t even require authenticating to the exposed Exchange Server. All they have to do is to do thorough recon and send specially crafted requests to their target to get RCE.
If you’ve already dealt with ProxyLogon (for which we launched a dedicated scanner in March), know these security weaknesses have a similar operation model.
Detect the Micrososft Exchange RCE
Find exposed servers with the Network Vulnerability Scanner
Patched or not? Detect the #proxynotfound attack chain
A malicious actor can only exploit the last two CVEs in this batch if they authenticate to the vulnerable Exchange Server. But, by chaining two of these flaws, they can skip that step altogether.
In April, we saw attackers use the same approach when they combined ProxyLogon with post-auth vulns to embed web shells and achieve persistence on unpatched Exchange servers. While this is not a replica of the ProxyLogon situation, we can use that cautionary tale to guide remediation efforts.
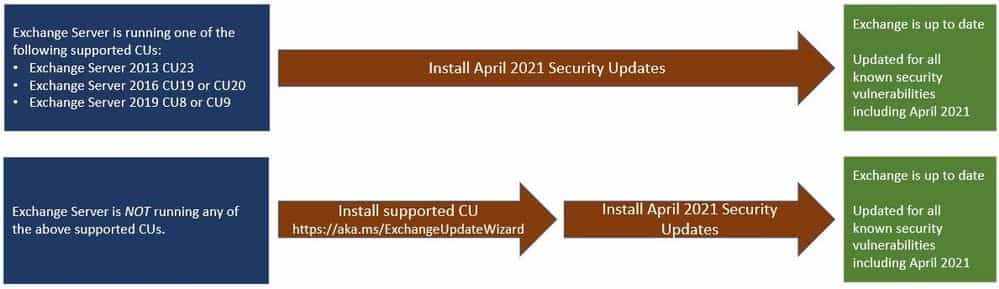
Once you know which servers need patching, you can deploy the cumulative update Microsoft released for these issues.