December updates: 6 new ways to make your workflow smoother

- Article tags
Hope 2022 is off to a great start for you!
Supporting your security efforts is what we do, so here’s a fresh batch of platform updates we rolled out at the end of 2021.
Why check them out?
Because they’ll help you get more work done, faster with the same tools and features you know (and hopefully love!).
TL;DR
Exploit 4 new RCEs with Sniper Automatic Exploiter
Detect a high-risk XSS in Microsoft with our Network Scanner
Discover weak credentials in Redis service with our Password Auditor
Control the delay between login attempts with the Password Auditor
Find Broken Authentication & Ruby code injection issues with the Website Scanner
Add specific info about your targets to your focused scans
Here’s how everything works
1. Automatically confirm exploitability for these critical CVEs with Sniper
No rest for our vulnerability research team! They built 4 new exploit modules while everyone else was easing into their holidays.
This means you can now automatically validate, exploit, and do post-exploitation in under 2 minutes with Sniper Auto-Exploiter for:
the RCE vulnerability in Laravel PHP framework – CVE-2021-3129
another high-risk RCE found in Exim Mail Server that enables malicious actors to execute arbitrary commands via an especially crafted email – CVE-2021-10149
the Tomcat RCE vulnerability discovered in Apache Tomcat HTTP Server that lets attackers upload a JSP file to the server via a crafted request – CVE-2017-12617
the RCE deserialization vulnerability in multiple Apache OFBiz versions – CVE-2021-26295
2. Detect this critical XSS in Microsoft with the Network Scanner (+ Log4Shell)
Run our Network Vulnerability Scanner against your targets and check if they are vulnerable to the critical pre-auth POST-based reflected XSS vulnerability (CVE-2021-41349) in Microsoft Exchange Server.
Try the Full Scan option from our Network Vulnerability Scanner and get a ready-to-use report with rich, useful findings.
PRO Tip: Don’t forget you can use Pentest-Tools.com to find targets impacted by the Log4J RCE vulnerability (CVE-2021-44228).
With both the Website Scanner and the Network Scanner tools, you can effectively detect Log4Shell in your pentesting engagements. We even provide a faster option: the ready-to-use Log4Shell pentest robot!
Curious about how our detection techniques for the Log4J vuln work? We shared all about it.
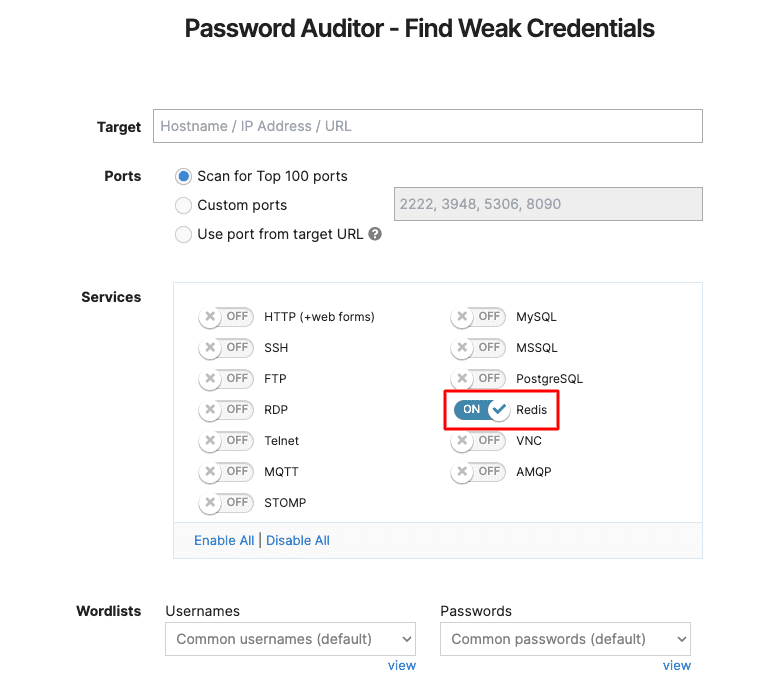
3. Discover weak credentials in Redis
If you’re using Redis, you can now run the Password Auditor to automatically discover weak and default credentials in it.
Go to Password Auditor, add your URL target, and enable the service. Sounds easy? It’s because we made it so.
4. Control the delay between login attempts with the Password Auditor
Now you have the option to control the delay between two successive authentication attempts you make with the Password Auditor. Make sure to add up to 43.200 delays between attempts.
Here’s where to find the option:

5. Two more detection modules make the Website Scanner even stronger
Our Website Scanner gets better each month! We recently added two new detection modules that search for Broken Authentication and Ruby code injection in your web apps.
To use them, go to Website Scanner, add your URL target, and select Full Scan. Expand the Attack options, choose the Active checks tab and enable Broken Authentication or Ruby code injection.

6. Add specific info about your targets when running focused scans
Having all the information you need in one place saves a lot of time and energy. Here’s how we help you keep things simple and efficient.
Our team has improved the Pentest-Tools.com dashboard interface by adding the option to easily visualize the target description for all your scans, including scheduled ones.
Scan for SQLi, XSS, and other critical vulns in web apps
Find outdated network services, misconfiguration servers, and more critical flaws
To enable it, go to Scans, navigate to View Settings and check Show target description.
Here’s how to do it:

Each pentesting report you’ll generate combines your targets’ description with scan results. Useful, right?
Hope these updates help improve your pentesting workflow every day!