Visualize exploit paths with the Sniper network graph

- Article tags
When we launched Sniper Auto-Exploiter in early September 2021, our initial goal was to help offensive security specialists validate, exploit, and do post-exploitation faster and more accurately.
This objective hasn’t changed, but the way offensive security specialists use Sniper has evolved. So we continue to strengthen Sniper with vulnerability exploitation capabilities that use automation not to replace the human expert, but to expand their capabilities.
Every bit of energy we spend straining to recall things is energy not spent doing the thinking that only humans can do: inventing new things, crafting stories, recognizing patterns, following our intuition, collaborating with others, investigating new subjects, making plans, testing theories.
Building a Second Brain, Tiago Forte
TL;DR Why we built Sniper Auto-Exploiter
Whether working in offensive or defensive security, we all see it: high-risk, widespread vulnerabilities cause significant disruptions to already struggling security teams.
In 2021, 1100+ CVEs with 9-10 CVSSv3 scores flooded the tech ecosystem. Pentesting statistics also show that fixing a critical vulnerability takes 100+ days on average, while some of them take years to eliminate through patching or other solutions. Case in point, Log4Shell, OMIGOD, ProxyShell, and ProxyLogon, to name a few.
Without dependable help, increasingly complex and voluminous VA (vulnerability assessment) and VM (vulnerability management) activities burden security pros until they burn out, which is already a common problem.
We believe focused automation can help them cope and scale, but it has to be reliable, under their control, and make an actual difference.
Because we care about this problem deeply, our research team built Sniper to help security teams confirm the real impact of a CVE with RCE or arbitrary file read risks much faster.
We integrate new, widespread vulnerabilities as fast as 72 hours (on average) from the moment they get a CVE, so ethical hackers can rely on Sniper to react with speed and precision and considerably reduce business risk.
We’re thrilled to see that a diverse range of security specialists use Sniper every day. They come for the tool’s ability to save time and stay because it offers transparency, control, and also removes the risk of accidental damage which manual exploitation can sometimes create.
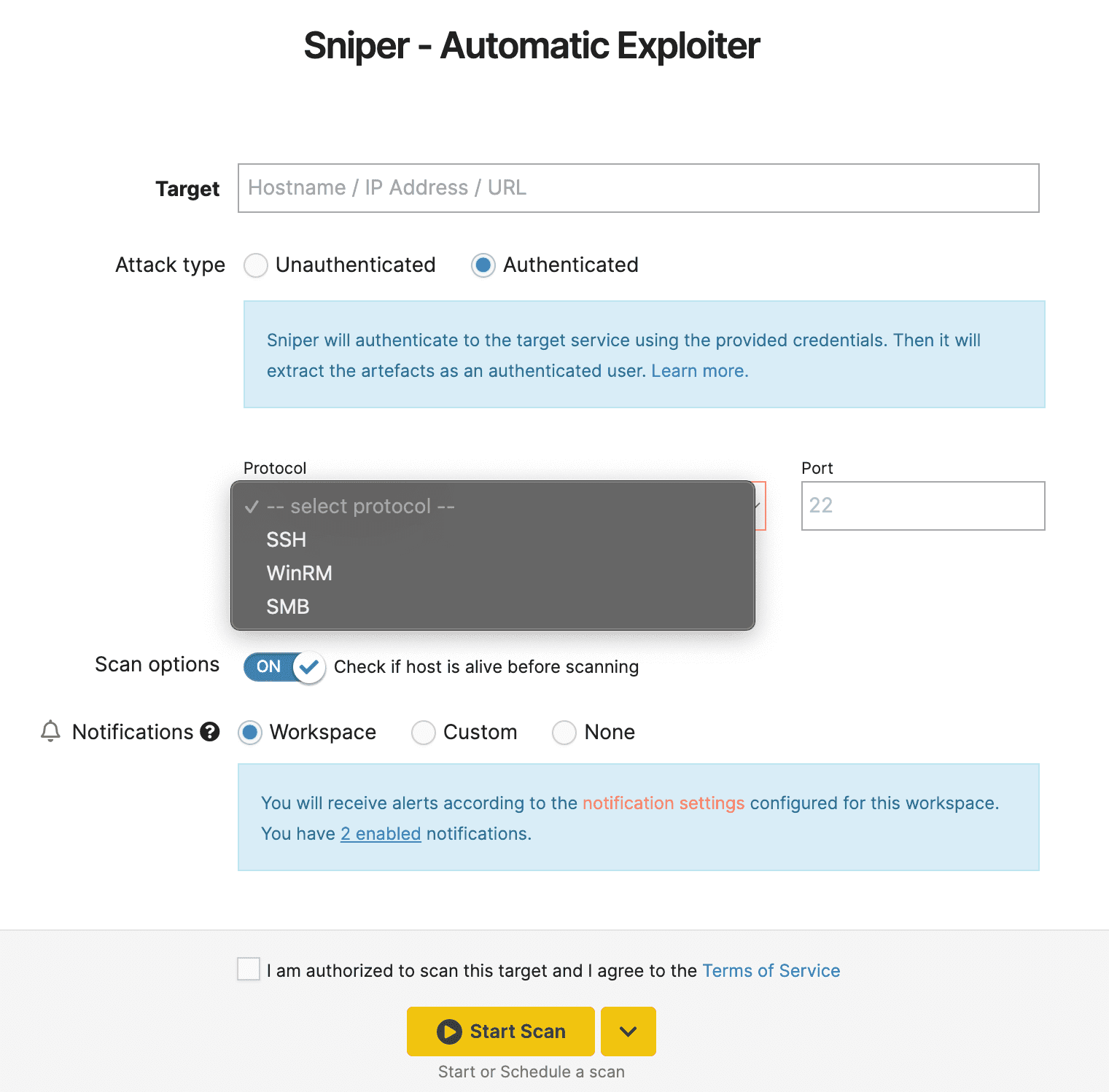
With Sniper, ethical hackers can simulate both external and authenticated attacks in a safe, controlled sequence. Each exploit automatically extracts data from the target either as an unauthenticated attacker or as an adversary with access to login credentials.
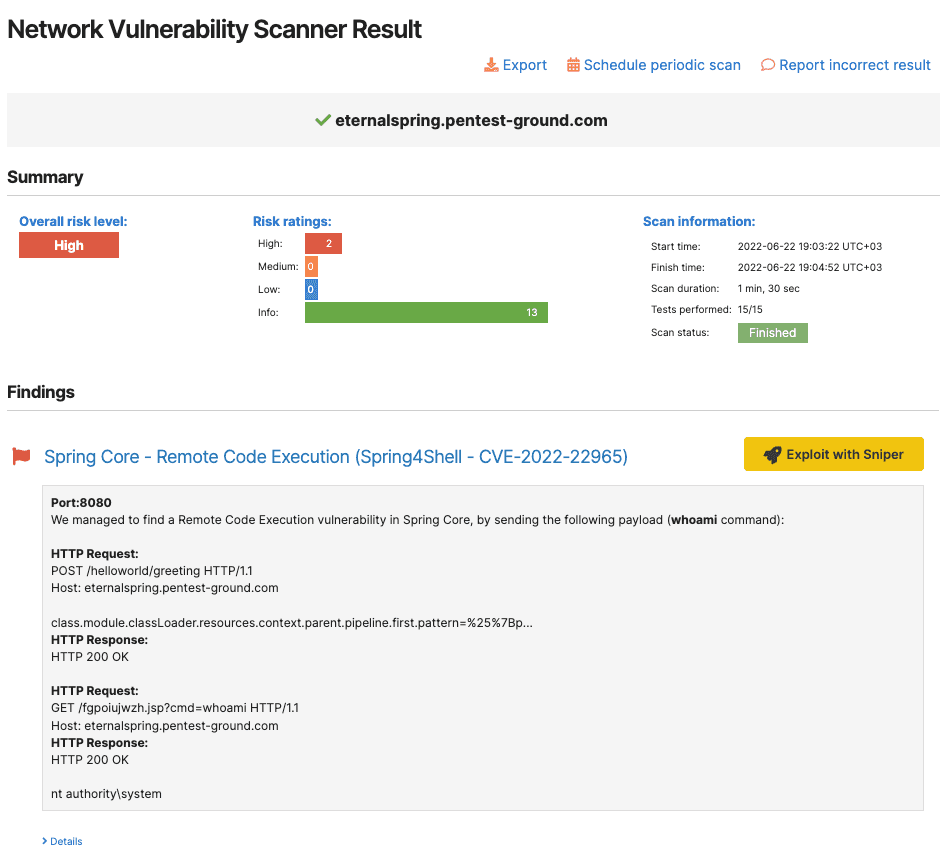
What makes Sniper Auto-Exploiter even more powerful is that it’s embedded into the Pentest-Tools.com platform. That means ethical hackers can use it alongside our Network Vulnerability Scanner, for example, and in safe, automated testing sequences through dedicated pentest robots (e.g. Network Scanner Full domain robot or Network Scanner – critical CVEs robot).
These focused scans produce accurate results that support urgent detection and validation for targets affected by critical vulnerabilities in high-profile software (e.g. Confluence, BIG IP, Struts, Redis, Magento, Zabbix, etc.).
You can now chain findings from our Network Scanner – which only detects a vulnerability – with the Sniper Auto-Exploiter tool with a single click on the ‘Exploit with Sniper’ button.
Daniel Bechenea, Security Research Lead
On top of its ability to bridge the gap between results that common vulnerability scanners produce and the attack methods real threat actors use, Sniper recently got an important upgrade. This recent improvement expands its role as a key tool for minimizing the window of opportunity for adversaries who focus on a few highly effective and targeted intrusion techniques.
Sniper network graph: safe auto-exploitation x instant visualization
We wanted to take Sniper’s capabilities further and help our customers understand the network architecture behind the exploited host with zero manual effort and in a fraction of the time compared to manual methods.
Why now?
Like any other great feature, we wish we had it years ago. But, like everything else, Sniper is under continued development and, as a result, new cool features continue to emerge every month.Ruben Condor, Security Research Engineer
Since visualizing network topology is an essential step for both offensive and defensive information security specialists, we built a network graph into Sniper Auto-Exploiter results.
In the visual summary section of this tool’s results, Pentest-Tools.com customers can now find an instant visualization of their target host’s network configuration. They can explore the automatically generated network graph to see:
All TCP connections (inbound or outbound) between your target and other hosts on the network (routers, workstations, etc.) and their system information
Interfaces configured on the exploited host
The exploit path(s), which Sniper used to safely compromise the machine
Communication protocols for each connection (SSH, HTTPs, HTTP, ms-wbt-server, etc.)
A list of adjacent hosts from nearby network subnets
ARP routes and host groups, especially helpful for multiple targets that communicate on the same port with the exploited target.

The Sniper network graph pulls data from the artefacts it extracts and automatically correlates the network information when the tool gains RCE on a target. With this new capability, Sniper removes time-consuming manual work, gives you the big-picture context of your target, and frees up your schedule for more stimulating work.
Sniper now has great exploitation abilities that include custom network artifacts.
Based on these, it was the perfect moment to put all the network information into a network graph to quickly assess the network architecture and understand how the systems are connected.
We built the Sniper network graph to help other offensive security specialists save massive amounts of time they currently spend understanding the network architecture behind the exploited host.
As a red teamer, it’s easy to spot cherry-picks (sensitive and important targets) on a graph and pivot to them. As a blue teamer, you want to discover all unknown connections made by and to the target, so you can audit them and identify if a system has been exploited and if it has a backdoor connection the malicious attacker maintains.
Daniel Bechenea, Security Research Lead
As you can see, we’re extremely passionate about building tools that both solve real, painful problems for offensive security professionals, and that also fit into the logic of their workflow.
We created the Sniper network graph to give our customers a way to easily get the network topology after a successful exploit, or even after an authenticated scan.
Their time is extremely valuable, so we made it our goal to provide as much information as possible – in the friendliest representation.
Using the network graph, you can easily see network connections, the relevant processes on the system, and even the network protocols and interfaces, without necessarily having extensive experience in the field of networking.
Ruben Condor, Security Research Engineer
Our goal with the entire range of tools and features on Pentest-Tools.com is to remove a large chunk of the cognitive burden and many of the inefficiencies from security professionals’ workflow. We strongly believe:
Only a human can understand the network behind a target, but, with Sniper and its network graph, you can save a lot of time correlating all the network information you have when remote code execution is achieved.
Daniel Bechenea, Security Research Lead
We’re also pragmatic in our approach because there’s no other way to make meaningful progress on issues that matter. There’s no need for embellishment when there are so many systemic problems we need to solve as members of the infosec community.
The network graph doesn’t include any information that a good pentester might not be able to get. However, this pentester would need considerably more time than Sniper to aggregate and correlate the information so they can see the big(ger) picture.
You have to wonder: what’s worth focusing your limited time and energy on?
Plus, as the target infrastructure becomes more complex and the number of active connections increases, correlating all the data becomes exponentially more difficult.
Unburdened from doing this task manually, the security professional can use their time and headspace to showcase their unique talent and expertize based on the information they get from Sniper in a few minutes.
Ruben Condor, Security Research Engineer
This visual representation of the target’s network architecture makes it easy to understand how systems are connected. It also highlights the impact of a vulnerability, offering proof to make persuasive arguments with peers in security and IT or with decision-makers in business units.
For example, the Sniper network graph helps you see if multiple targets communicate on the same port with the exploited target, essentially opening them up to malicious exploitation.

If someone needs a network graph for other targets, they can also get it from a system that is not vulnerable, by running an authenticated Sniper scan.
At this time we support SSH, WinRM, and SMB scanning options for authenticated scenarios, and we continue to add options for our customers.
Ruben Condor, Security Research Engineer
There are plenty of use cases for Sniper Automatic Exploiter in your security testing workflow. Use it to:
considerably speed up vulnerability validation
run safe, controlled exploitation
gain initial access automatically
visualize network topology
methodically reduce the attack surface
find targets for pivoting and lateral movement.
The best part about building the Sniper network graph
Turning an idea into reality is the best part.
Transforming a bunch of text that, in the beginning, is very difficult to correlate into a visual representation that’s easy to understand is very rewarding. Seeing it in the hands of our customers even more so.
Daniel Bechenea, Security Research Lead
Although I had access to the information presented on the graph, after it took shape there were several moments when I was testing the graph and it surprised me.
This is clear proof that it’s very easy to miss essential information if it isn’t presented in a clear and usable way.
Ruben Condor, Security Research Engineer
Whether you empathize with Ruben’s experience of expanding his knowledge of networking with this new feature or with Daniel’s excitement to use tools that enable visual representations of network configurations, we’re excited to see what you do with Sniper Auto-Exploiter!
If you’re interested in getting updates for new critical CVEs that we integrate into our vulnerability exploitation tool, subscribe to our Youtube channel to get demos and walkthroughs the moment we publish them.