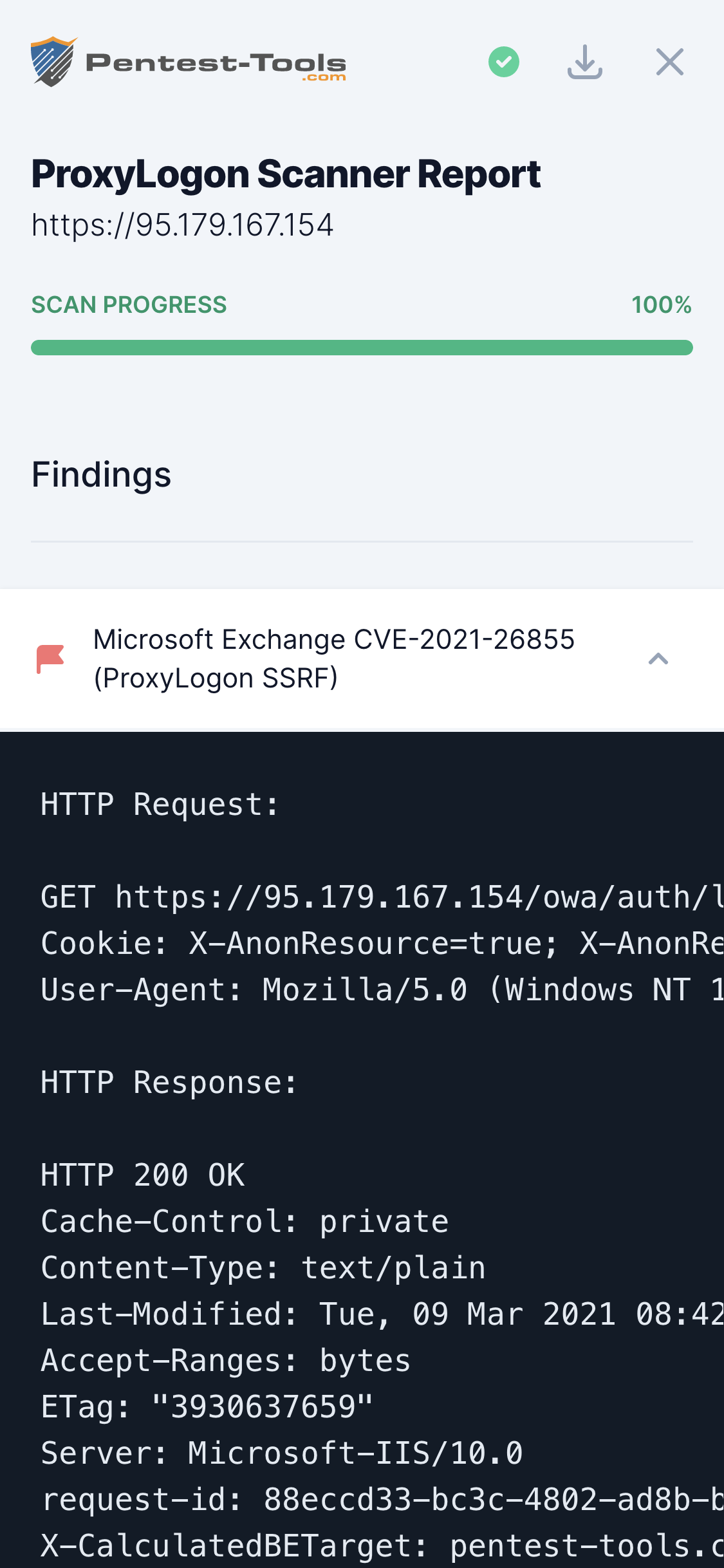
ProxyLogon Scanner
Technical details
CVE-2021-26855 is a Server-Side Request Forgery (SSRF) vulnerability in the Microsoft Exchange Server. An unauthenticated, remote attacker can use it to check if the Exchange service initiates HTTPS requests to arbitrary locations. These requests are done in the name of the Exchange service, so they are authenticated and include access tokens and other sensitive data.
As a direct result, the malicious could forge requests to read emails of the users configured on that email server.
A forged request includes interesting pieces of data like X-Sourcecafeserver, X-Commonaccesstoken, ClientId, etc. Here is how a full HTTP request initiated by the Exchange server looks like:
Connection: Keep-Alive
Cookie: X-AnonResource=true; X-AnonResource-Backend=pentest-tools.com/logger/etlWuwSzO8/ecp/default.flt?~1; X-BEResource=localhost; ClientId=9HWXKYJ0HUEBVKM0GMVIFW
Host: pentest-tools.com
X-Vdirobjectid: 3f80c757-01a3-4edc-b546-371ee214b8ed
X-Commonaccesstoken: VgEAVAlBbm9ueW1vdXNDAEUAAAAA
X-Sourcecafeserver: EXH01-1.AVDOC.LOCAL
X-Isfromcafe: 1
Msexchproxyuri: https://10.137.1.30/owa/auth/abcd.png
X-Msexchangeactivityctx: V=1.0.0.0;Id=2310929a-3832-4ef5-851d-80927454aafa;C=;P=
X-Originalrequesthostschemeport: 443:https:10.137.1.1
X-Originalrequesthost: 10.137.1.30
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:60.0) Gecko/20110101 Firefox/60.0
Accept: */*
X-Excompid: ClientAccessFrontEnd
X-Forwarded-Port: 47750
X-Forwarded-For: 10.137.1.1
Content-Length: 0
When exploited together with another vulnerability, such as CVE-2021-27065 (post-authentication file write), this vulnerability can lead to unauthenticated Remote Code Execution on the Exchange server. This attack chain was named ProxyLogon.
The ProxyLogon attack was massively used to exploit a large number of Microsoft Exchange servers exposed to the Internet by creating web shells in various locations on the file system.
We recommend performing an in-depth review of vulnerable Exchange servers to check if they are exploited by malicious actors.
Microsoft has released a tool to verify if there are new files present on the exchange server: https://github.com/microsoft/CSS-Exchange/tree/main/Security
More details about this vulnerability:
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855
- https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
- https://msrc-blog.microsoft.com/2021/03/05/microsoft-exchange-server-vulnerabilities-mitigations-march-2021/
Parameters
| Parameter | Description |
|---|---|
| Target | This is the URL of the target Outlook Web Access (OWA) server. |
How it works
The scanner attempts to trigger the SSRF vulnerability by determining the target Exchange server read a remote file located at: https://pentest-tools.com/file.txt
If the file contents are found in the server's HTTP response, the target is declared vulnerable.