How to exploit Zabbix Unsafe Session Storage (CVE-2022-23131)
- Author(s)
- Publisher
- Pentest-Tools.com
- Updated at
- Article tags
Zabbix is a strong, configurable open-source security monitoring platform that gives a comprehensive view of the whole IT infrastructure, whether it is on-premise or in the cloud. You can use it to collect and track metrics like network traffic across a variety of devices in similar ways to other solutions such as Nagios and Pandora FMS.
Due to its increasing popularity and administrative access to most companies’ infrastructure, Zabbix has become a high-profile target for threat actors. So of course a security issue like the Unsafe Session Storage vulnerability attracts motivated cybercriminals.
If it’s up to you to find exploitable targets and gather proof for vulnerability validation for your ethical hacking engagements, this guide is for you!
What is CVE-2022-23131?
CVE-2022-23131 is affecting Zabbix, an enterprise-ready product used as a network security solution with detailed monitoring for devices and infrastructure components. To be more precise, it refers to the Zabbix Web Frontend, a dashboard that system administrators use to collect metrics and configure Zabbix Server.
This is a high-risk vulnerability (CVSSv3 9.8) under active exploitation that advanced persistent threats are using and which CISA also warned about.
Cookies have been the culprit for many CVEs, particularly in how they’re handled in relation to web applications or interfaces. Developers commonly use cookies for storing authentication data, which makes them a target for attackers – as it is the case for this CVE. 🙂
It’s difficult to estimate the impact in numbers, as Zabbix is widely spread across the world and its reseller program propagates it even further, thus making it unlikely to be tracked. However, it is safe to assume that the number of devices and companies affected by this security issue is nothing to be ignored.
Threat actors can gain access to multiple infrastructure endpoints by exploiting this CVE:
IoT devices that monitor and control temperature, humidity, or air quality in an industrial work environment
On-premise infrastructure
Assets in the cloud, as Zabbix is a solution that can be used for both cases.
How the Unsafe Session Storage in Zabbix works
One can exploit this vulnerability using SAML authentication. This feature is not enabled by default. Still, it is one of the most commonly used SSO (Single-Sign-On) methods. This type of authentication is frequently used in enterprise environments, a setup that, in fact, is supposed to enhance network security.
There are many security standards mistakes such as writing down passwords, reusing the same password for personal accounts or using weak passwords susceptible to brute force attacks. In these scenarios, users could compromise one or more of their passwords. In this context, Zabbix enhances network security by reducing the risk of password exhaustion using SAML authentication.
As an enterprise-focused network security solution, Zabbix also collects metrics from OS level monitoring, network devices, IoT sensors, databases, applications, cloud services, containers, virtual machines, etc.
Compromising a product that works at this scale can lead to an attacker having access to your entire infrastructure, collecting data from all the sources monitored by Zabbix and possibly gaining SSH/RDP access to those devices depending on your infrastructure setup and Zabbix deployment.
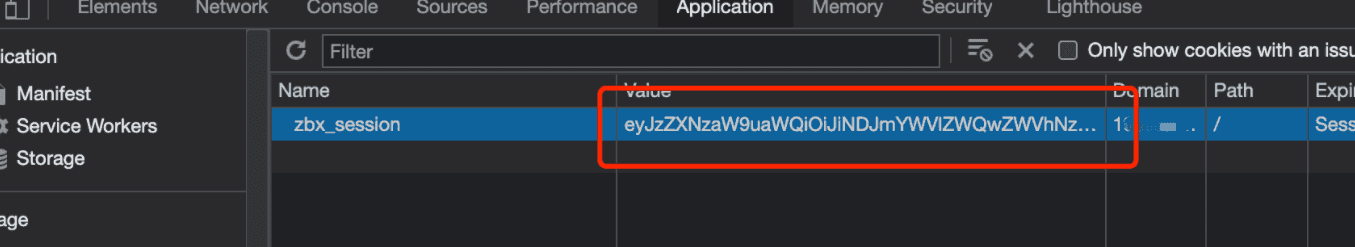
From an attacker’s point of view, successfully exploiting CVE-2022-23131 is fairly simple and requires access to the Zabbix enterprise deployments. A malicious actor can craft a session cookie and use the SAML authentication option to achieve a successful login as a Zabbix Admin privileged account.
The exploit is publicly available on Github.
After running the exploit that generates an admin cookie value, the next step is to replace this value in your browser developer tools and use the SAML authentication.
Vulnerable Zabbix versions
The discovered vulnerabilities affect all supported Zabbix Web Frontend releases at the time of our research, up to and including 5.4.8, 5.0.18, and 4.0.36 versions.
The business impact of CVE-2022-23131
Successful exploitation of CVE-2022-23131 can result in business owners losing access to critical systems, leaks of confidential information, and, ultimately, financial loss.
Affected infrastructures can be used for various malicious purposes such as botnets, phishing campaigns, or abusing the company’s trusted status to exploit another company. This is highly dangerous depending on the company’s status and resources.
Depending on the company’s profile, information leaks, blackmailing, or even false reports can be created and shared publicly to damage the company’s reputation or another public image (for example, a media company compromised through this CVE and whose infrastructure is used to spread false information publicly can give this fake news traction and influence decision-makers.
It is possible for this vulnerability to lead to supply-chain attacks depending on the nature of the business as it provides access to the infrastructure devices.
How to find targets vulnerable to CVE-2022-23131
There are multiple ways of finding vulnerable targets and one of them is using Shodan:

A search for “Zabbix” generated 3.705 results at the time of writing this guide.

The resulting 6422 web pages include Zabbix deployments that may be vulnerable to this CVE.
A less popular and equally interesting choice for OSINT is Zoomeye:

Although not as popular as other options, Zoomeye generates a considerable number of results: 332,179.
How to mitigate CVE-2022-23131 in Zabbix
One of the first things you can do now is to upgrade your instances running a Zabbix Web Frontend to versions 6.0.0beta2, 5.4.9, 5.0.19, or 4.0.37 to protect your infrastructure.
Also, note that, if the Zabbix deployment is not using SAML authentication, the exploit is not applicable.
Unpatched systems are still a pain point for businesses
Finding that security solutions are vulnerable can be a shocking truth to many security specialists. Just because a product is designed with security in mind does not mean it is bulletproof, and that is completely normal. Symantec and SolarWinds are two examples of big companies that suffered cyberattacks with a high impact on both customers and other organizations.
The fact that mistakes happen does not automatically make software less trustworthy. However, the vendor’s approach towards fixing the vulnerability is authentic proof of how mature and responsible they are as a business and as a team.
Although some companies may have been impacted by this CVE, Zabbix is still a solid solution that follows many security standards. Security teams should work on implementing the fixes already available to make sure they can continue to use it safely.













