Buffer Overflows and Authentication Bypasses - exploiting CVE-2025-0282 and CVE-2024-55591

- Article tags
For security specialists juggling endless vulnerability assessments, early 2025 has already set a challenging pace. Two newly disclosed vulnerabilities—CVE-2025-0282 in Ivanti Connect Secure and CVE-2024-55591 in Fortinet FortiOS—highlight the persistent risks in perimeter security, with hundreds of thousands of exposed instances worldwide.
These flaws not only allow remote exploitation but also expose vulnerable targets to unauthenticated access, lateral movement, and persistent backdoors. Since public proof-of-concept exploits already exist, mitigating these issues is quite pressing.
For penetration testers and vulnerability managers, the challenge is always two-fold: accurately finding vulnerable assets and prioritizing what matters most before bad actors strike.
This is why we’re breaking down these critical vulnerabilities: to give you the technical depth, exploitability analysis, and real-world risk assessment you need to secure your organization or clients.
Let’s get into it!
CVE-2025-0282 in Ivanti Connect Secure
Published on January 8, 2025, CVE-2025-0282, along with CVE-2025-0283, is a critical vulnerability in Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti Neurons for Zero Trust Access (ZTA) gateways.
This security issue captured the cybersecurity community’s attention in early 2025 because CVE-2025-0282 in Ivanti Connect Secure is not only technically severe but also impacts a crucial enterprise VPN solution. When a vulnerability affects a widely deployed network gateway, it instantly becomes an attractive target for attackers, especially with public proof-of-concept (PoC) out there, which significantly lowers the barrier to exploitation.
Given that VPN gateways serve as crucial entry points into corporate infrastructures, organizations must act fast to mitigate risk, especially since this vulnerability has the highest exploitability score (EPSS) among CVEs published so far this year.
CVE-2025-0282 is a Stack Overflow vulnerability (CWE-121) discovered in the /home/bin/web binary, which manages HTTP connections and VPN protocols, including Ivanti's proprietary IFT-TLS protocol.
Let’s see what this means.
CVE-2025-0282 attack surface
As an exploitation vector, CVE-2025-0282 only requires remote access to the Ivanti Connect Secure access interface.
The following versions are known to be vulnerable:
Ivanti Connect Secure: versions from 22.7R2 up to and including 22.7R2.4.
Ivanti Policy Secure: versions from 22.7R1 up to and including 22.7R1.2.
Ivanti Neurons for Zero Trust Access (ZTA) gateways: versions from 22.7R2 up to and including 22.7R2.3.
By mid-February, according to Shodan.io, approximately 230,000 instances of Ivanti Secure Connect were exposed to the internet.
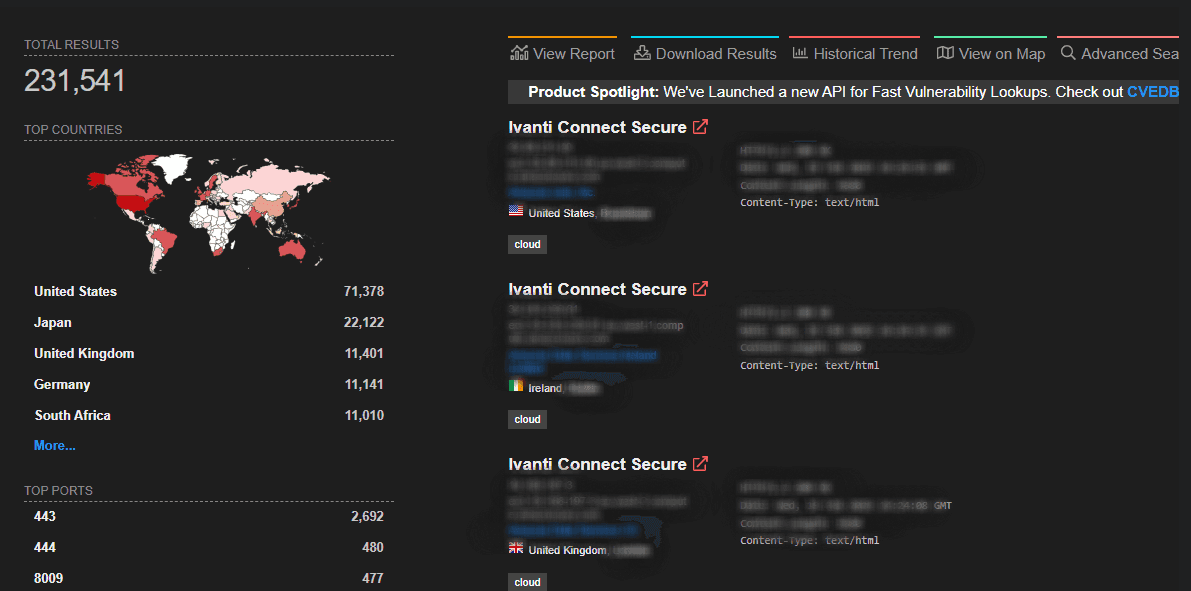
During the same period, Censys reported approximately 27,000 instances using the same query.
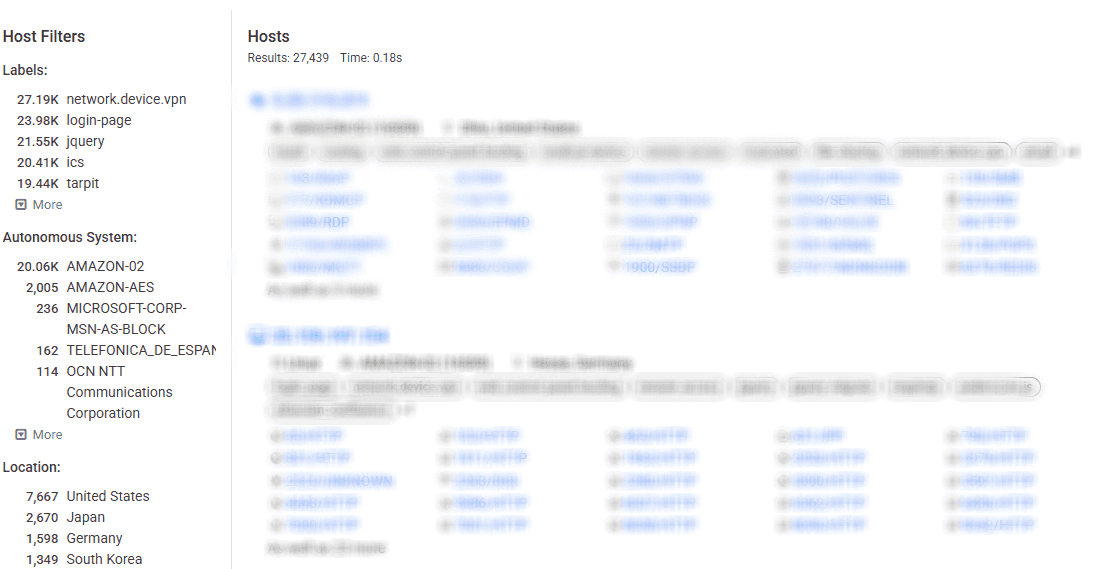
Although the numbers the two platforms report are significantly different, the higher count on Shodan could indicate a considerable number of honeypots. Another reason for the difference might be that there’s no standardized, public exploit for all vulnerable versions. We can safely assume these are solid reasons for the significant level of interest from the infosec community for this vulnerability.
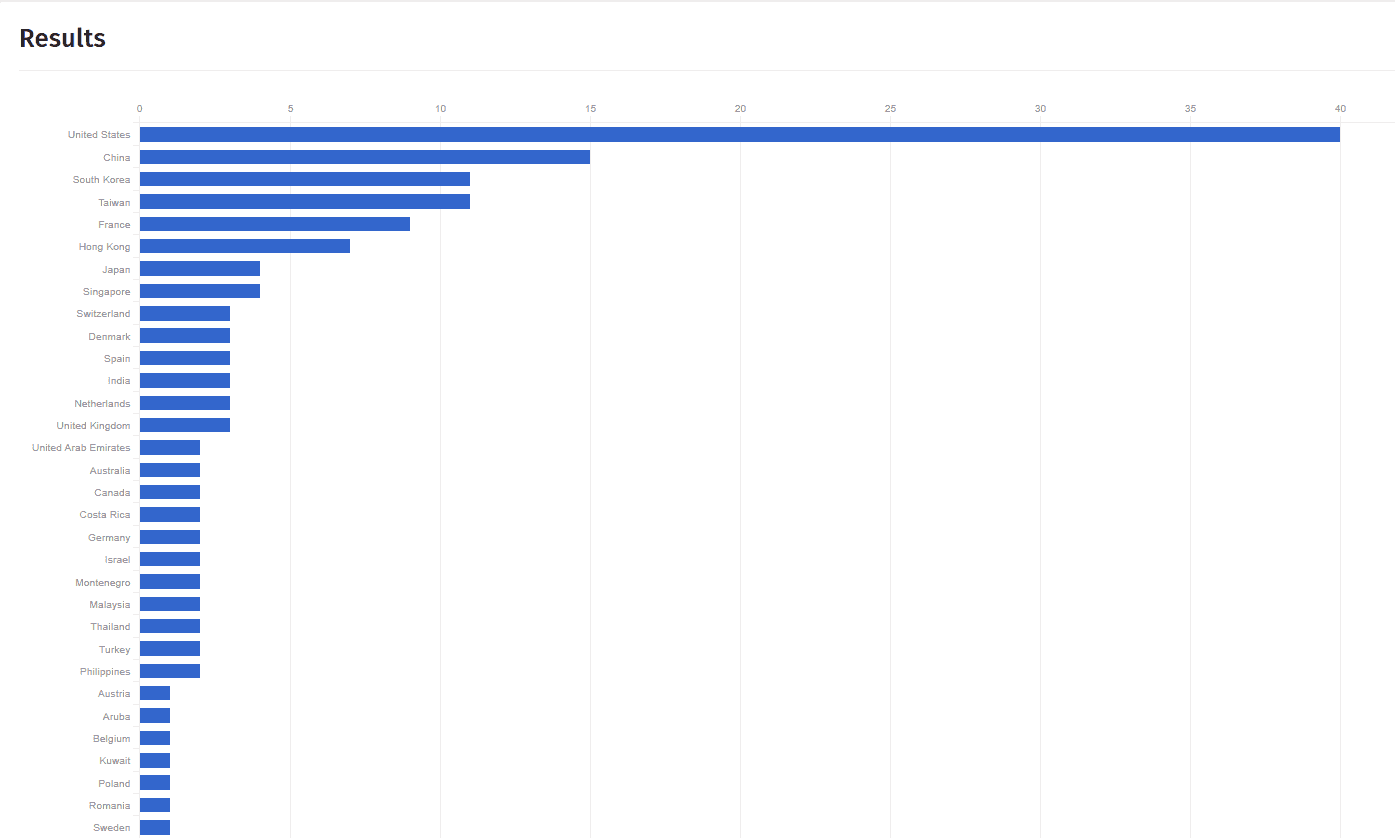
ShadowServer confirmed 262 instances where CVE-2025-0282 was exploited over the last 30 days (January 19 – February 19, 2025), with the main affected servers originating from the USA, China, South Korea, and Taiwan.
CVE-2025-0282 technical details
According to WatchTowr's analysis, the CVE-2025-0282 vulnerability in Ivanti Connect Secure is caused by the improper use of the strncpy function in the clientCapabilities parameter, which can lead to a buffer overflow when data exceeds 256 bytes.
This function copies a specified number of characters from a source string to a destination string without always ensuring null-termination (\0). In the case of CVE-2025-0282, the attacker can manipulate the number of characters.
Exploiting this vulnerability is not trivial and requires an attacker meets several conditions:
The starting address of a valid function from a library loaded by the web binary.
A ROP gadget for calling the system function.
A specific vulnerable version of Ivanti Connect Secure.
The server must allow switching the TLS protocol to IFT-TLS and must not require authentication when this protocol is used.
As you can see, exploiting this vulnerability requires advanced knowledge of operating systems, since the process is not straightforward. While there is a public exploit, it’s limited to a specific version, requiring significant adaptation and repeated testing to achieve success.
Also, operational security plays a crucial role, as attackers must use VPNs, Tor, frequent IP changes, and modified routes to remain undetected. These stealth measures help obscure both the attacker's identity and the exploitation techniques, reducing the risk of exposure and countermeasures.
Understanding these challenges highlights the technical and strategic complexity of such an attack - not that there aren’t bad actors out there with the stamina and resources to go for it.
Dipping further into this CVE, it’s important to know the ASLR (Address Space Layout Randomization) mechanism is enabled, which makes it difficult to locate the system function. However, since the web binary runs on an x86 (32-bit) architecture, ASLR entropy is only 9 bits.
This low entropy means there is a 1/512 probability that the system function address is correct, making it significantly easier to successfully exploit CVE-2025-0282.
As a result, an attacker could exploit this vulnerability in a relatively short timeframe - around 1 hour. Security researcher Sfewer from Rapid7 wrote a valid PoC that proves you can actually exploit the vulnerability in just 34 minutes!
Business risks associated with CVE-2025-0282
If compromised using CVE-2025-0282, Ivanti Secure Connect can serve as an entry point for attackers to infiltrate an organization’s infrastructure. Even low-profile intrusions can turn into opportunities for attackers to install software that exfiltrates critical data and makes lateral movement significantly easier. Privilege escalation, security bypassing, and long-term persistence are all realistic risks that emerge as a consequence.
Here are three scenarios of how these risks could play out.
Remote access infrastructure compromise leads to credential theft
Ivanti Connect Secure is widely used for remote workforce connectivity, and it is often integrated with Active Directory (AD) and Single Sign-On (SSO) solutions. If an attacker successfully exploits CVE-2025-0282, they could gain unauthenticated access to the VPN gateway. With this, they could:
intercept authentication requests
steal valid user credentials
and replay them for further access.
This can lead to widespread account takeovers, through which adversaries escalate privileges and move deeper into the network, potentially compromising cloud applications, privileged accounts, and critical internal systems.
Compromised third-party access causes supply chain breach
Many enterprises rely on third-party contractors, managed service providers (MSPs), or outsourced IT teams who use Ivanti VPN solutions to connect to corporate environments. An attacker who exploits CVE-2025-0282 could hijack these trusted connections, using them to infiltrate multiple partnered organizations in a supply chain attack.
This increases the risk of ransomware infections, intellectual property theft, or targeted attacks on critical vendors, which could disrupt operations way beyond the initial victim.
Data exfiltration brings on regulatory and compliance troubles and fines
Organizations operating in highly regulated industries such as finance, healthcare, or government must comply with GDPR, HIPAA, PCI-DSS, and a whole slew of data protection laws.
If an attacker exploits CVE-2025-0282 to exfiltrate customer data, financial records, or trade secrets, the affected business could face severe financial penalties, legal action, and even lose their compliance certifications - all terrible for business relations with customers and partners. Additionally, public disclosure of a breach definitely erodes customer trust, damages brand reputation, and impacts stock value, causing long-term financial consequences.
So what’s there to do about this nasty CVE?
Mitigation recommendations for CVE-2025-0282
To mitigate the security and business risks that CVE-2025-0282 causes, organizations need to implement continuous monitoring, enforce strict patch management, and require multi-factor authentication for all remote access.
Apply patches: update your Ivanti VPN systems to Ivanti VPN version 23.5.2 or later, as these versions include the necessary fixes for closing CVE-2025-0282. Ivanti has released these updates specifically to address this vulnerability and recommends immediately applying them to all affected appliances, including Ivanti Connect Secure versions before 22.7R2.5.
Increase monitoring: create rules and log files for your systems and check for any indicators of compromise (IoCs). You can get them from Palo Alto Networks or Beazley Security. This includes checking logs and network traffic for any unusual activities that could signal a breach or an ongoing attack.
Detect CVE-2025-0282 with our Network Vulnerability Scanner
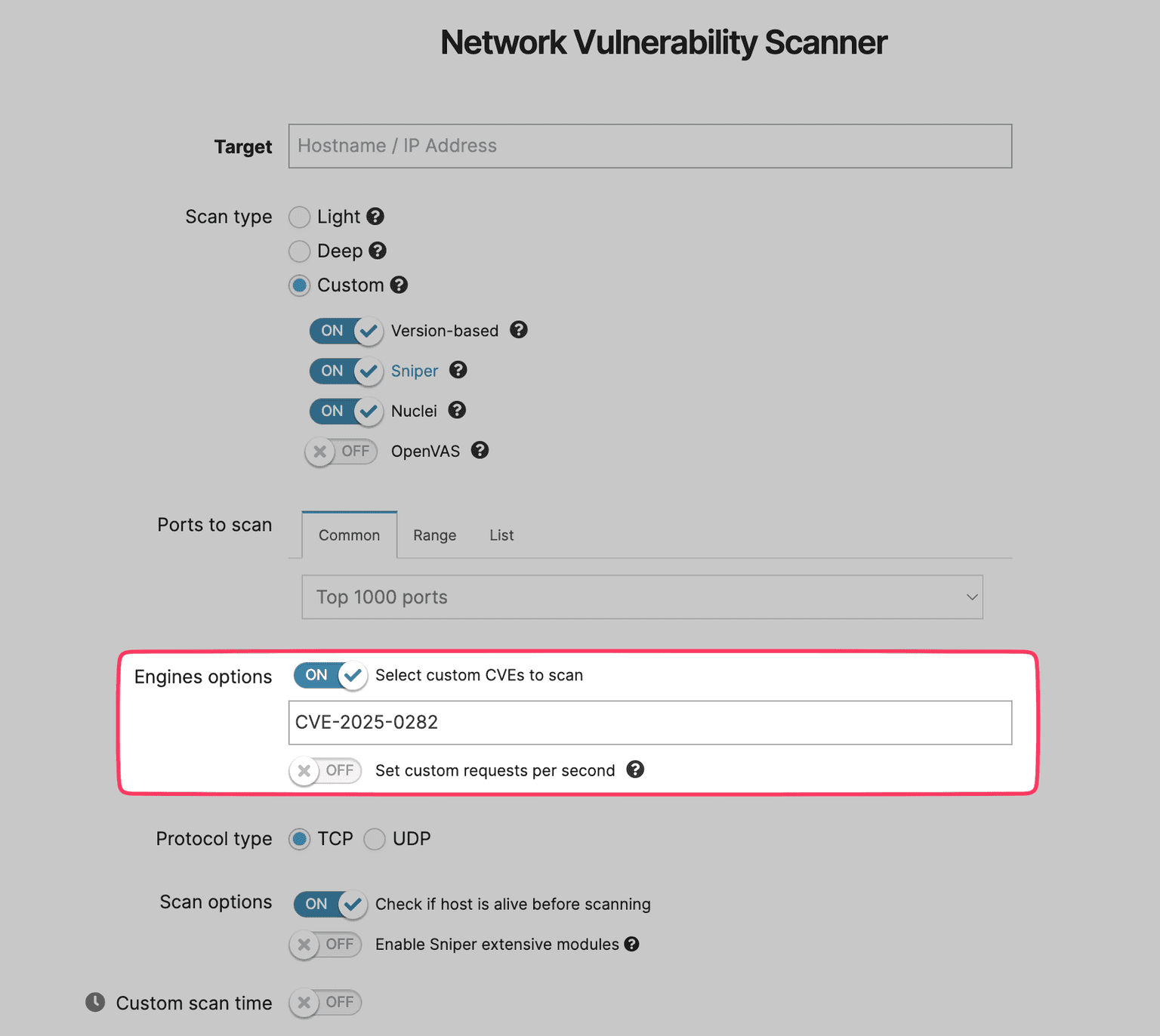
Naturally, we also made sure you can detect CVE-2025-0282 with Pentest-Tools.com, specifically with our Network Vulnerability Scanner. To make sure you get reliable results, our Network Scanner team looks for vulnerable versions and checks if a bad actor can use IFT-TLS anonymously, since these are conditions under which an attacker can exploit CVE-2025-0282.
Pressed for time? You can run a custom scan with our tool (in its full version), telling it to specifically look for CVE-2025-0282. This precise scan will help your team move fast through your potentially exposed Ivanti instances.
But wait! There’s more!
CVE-2024-55591 and CVE-2025-24472 in Fortinet
On January 14, 2025, CVE-2024-55591 popped up as a critical vulnerability in Fortinet FortiOS and FortiProxy. Almost a month later, on February 11, 2025, a similar vulnerability emerged - CVE-2025-24472, which exploits a different endpoint. Interestingly, the patches for CVE-2024-55591 are also effective for CVE-2025-24472.
Let’s see why!
CVE-2024-55591 is an Authentication Bypass Using an Alternate Path or Channel (CWE-288) vulnerability in the WebSocket module that Node.js uses for the FortiOS management interface.
As expected, the cybersecurity community was quick to react to it, since ShadowServer reported approximately 50,000 vulnerable servers on January 20. By February 20, this number later dropped to around 20,000.
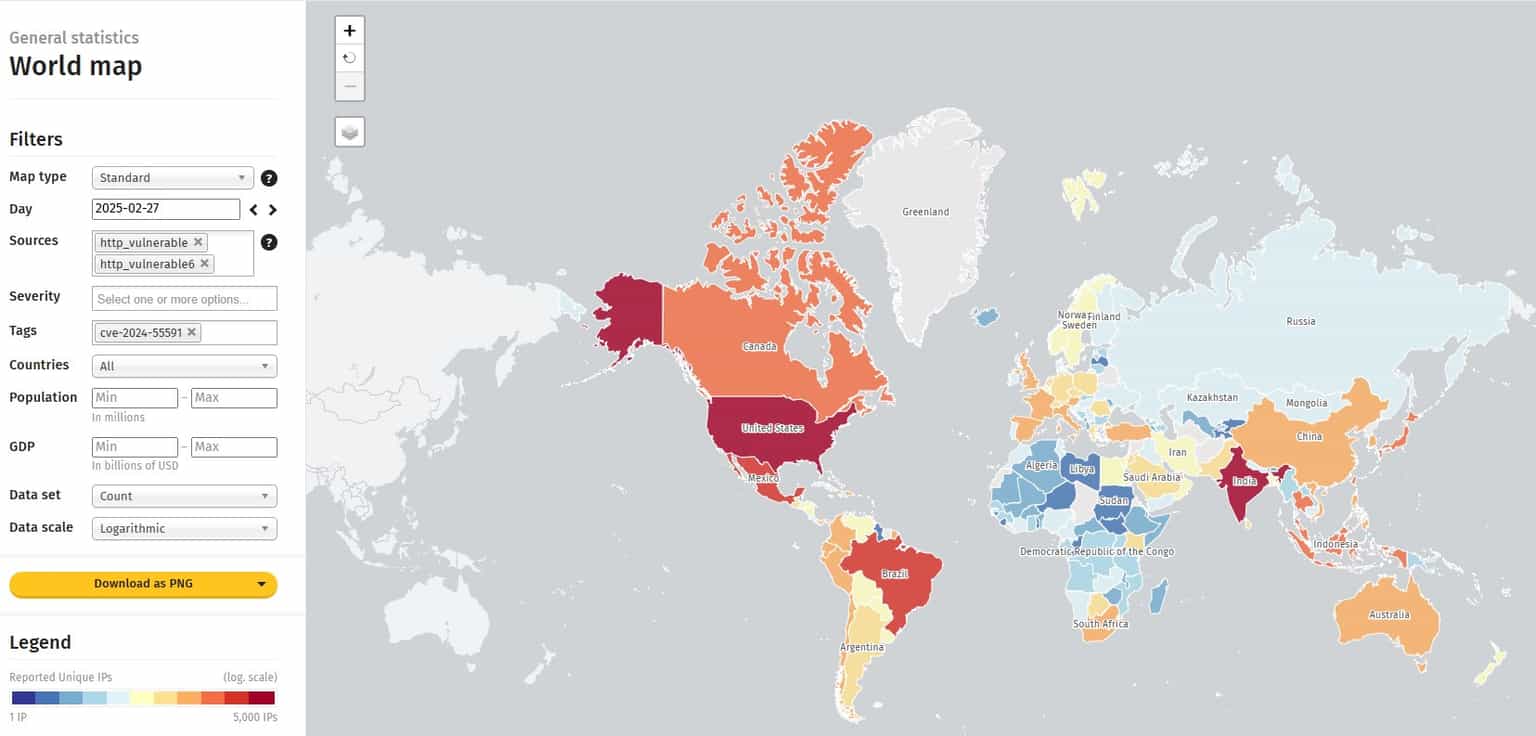
CVE-2024-55591 and CVE-2025-24472 attack surface
To exploit CVE-2024-55591, an attacker needs access to the FortiOS or FortiProxy administration interface exposed to the internet. So far, we know the following versions are vulnerable:
FortiOS: versions 7.0.0 to 7.0.16
FortiProxy: versions 7.0.0 to 7.0.19 and 7.2.0 to 7.2.12
By mid-February, approximately 265,000 Fortinet interfaces were exposed to the internet, according to Shodan.io.
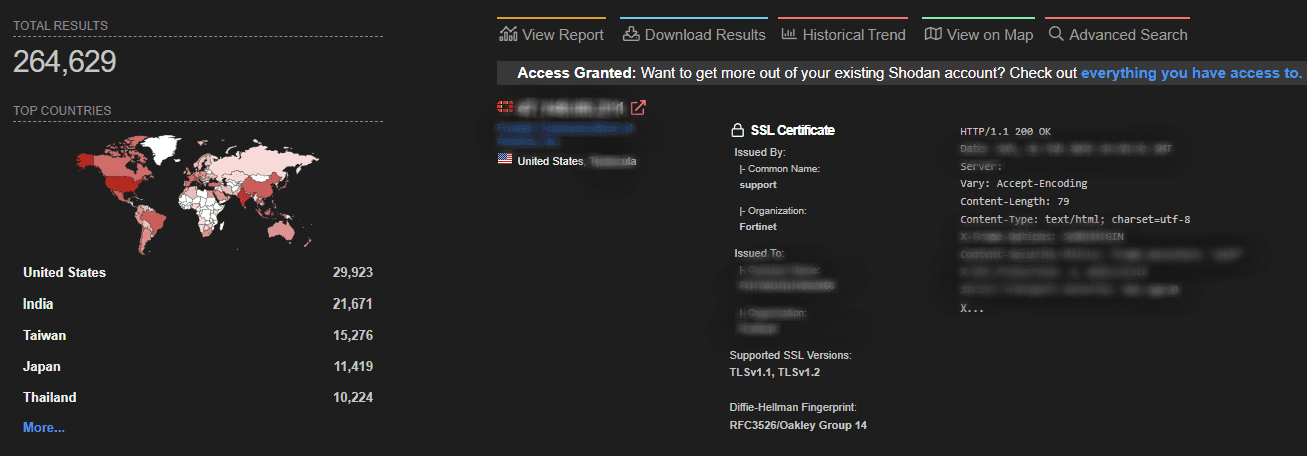
Checking Censys, which features more granular filtering, reveals up to 2,900,000 Fortinet interfaces that are potentially affected by CVE-2024-55591.
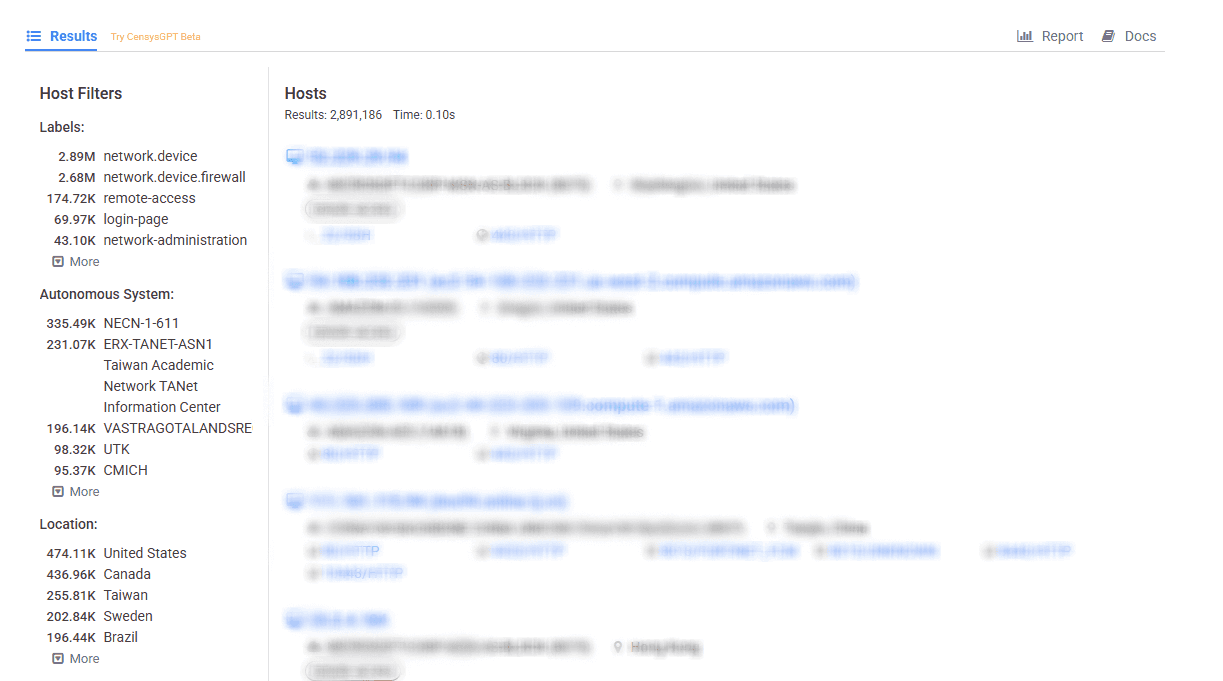
CVE-2024-55591 and CVE-2025-24472 technical details
A detailed analysis from WatchTower Labs highlights how a bad actor can exploit CVE-2024-55591. Essentially, the issue lies in the dispatch() function within the device's source code, which manages WebSocket connections. This function calls getSession() to validate the user's session. If it can’t find a valid session, getAdminSession() is called as a last attempt to retrieve a session.
Within this function, a query parameter called local_access_token is extracted from the URL, and if present, authentication is considered successful—even without proper validation of the token.
This omission allows an attacker to append the local_access_token parameter to their request targeting the /ws/cli/ endpoint, thereby gaining access to the device's command-line interface (CLI) without providing valid credentials.
Access to this CLI interface effectively compromises the entire device, as it makes it possible to execute privileged commands and modify critical configurations.
Business risks associated with CVE-2024-55591 and CVE-2025-24472
CVE-2024-55591 affects FortiOS, the core operating system for FortiGate, Fortinet’s flagship firewall and VPN solution. A successful exploit could allow attackers to bypass security controls, leading to unauthorized access, data breaches, and service disruptions.
The following situations are very likely to happen in a business impact context.
Full admin takeover of network security infrastructure
CVE-2024-55591 allows unauthenticated attackers to bypass authentication in the FortiOS WebSocket module, granting them privileged access to the FortiGate firewall’s administrative interface. Once inside, attackers can disable firewall rules, manipulate security policies, create rogue admin accounts, and reroute traffic, effectively turning the firewall into a tool for malicious activities. This could result in network-wide security collapse, exposing critical internal systems to further attacks such as data exfiltration, lateral movement, and malware deployment.
Man-in-the-Middle (MitM) attacks to intercept traffic
Since FortiGate firewalls act as a primary security layer, a successful exploitation of CVE-2024-55591 enables attackers to intercept and manipulate network traffic, potentially capturing unencrypted credentials, financial transactions, or sensitive corporate data. In organizations where FortiGate is used for VPN access, attackers could decrypt VPN traffic, impersonate internal users, and gain unauthorized access to internal applications, making it extremely difficult to detect an ongoing breach before significant damage occurs.
Unauthorized configuration changes cause regulatory violations and disrupt business ops
Many enterprises rely on FortiGate firewalls to enforce compliance with industry standards such as ISO 27001, GDPR, PCI-DSS, and HIPAA. So exploiting CVE-2024-55591 could allow attackers to tamper with security policies, disable logging, and modify network segmentation rules, potentially leading to non-compliance, regulatory fines, and legal consequences.
If attackers disrupt firewall operations or create backdoors for persistent access, businesses may experience prolonged outages, operational disruptions, and expensive incident response efforts to recover from the attack.
Similar to the risks associated with CVE-2025-0282 in Ivanti Secure Connect, this vulnerability threatens the integrity of corporate networks because it can enable lateral movement and persistent access. Organizations that rely on FortiGate need to apply patches right away, implement multi-factor authentication (MFA) for remote access, and monitor for suspicious activity to mitigate potential attacks.
Mitigation recommendations for CVE-2024-55591 and CVE-2025-24472
To mitigate CVE-2024-55591, it’s essential to update your affected devices to the patched versions:
FortiOS: Update to version 7.0.17 or later.
FortiProxy: Update to version 7.0.20 or later.
Additionally, you can:
Disable the HTTP/HTTPS administrative interface to prevent unauthorized access through the web interface.
Restrict access to the administrative interface by configuring local policies that allow access only from trusted IP addresses.
Monitor system logs for suspicious activities, such as successful admin logins from unexpected IP addresses and newly created admin accounts with unusual names.
Securing the Perimeter: A Continuous Battle
The vulnerabilities in Ivanti Connect Secure (CVE-2025-0282) and Fortinet FortiOS (CVE-2024-55591) remind us of a harsh reality for security and IT specialists: even the most trusted security solutions can become a liability.
When VPN gateways and firewalls—the very tools designed to protect networks—become vulnerable, the attack surface expands dramatically, forcing defenders to react faster than ever. Malicious actors don’t wait for companies to patch; they exploit CVEs like these within hours or days, leaving little room for error.
For those doing vulnerability management, this means prioritizing real-world exploitability, impact analysis, and proactive defense—not just chasing CVE scores. The ability to detect, assess, and mitigate vulnerabilities before they become breaches is what separates a resilient security strategy from a reactive one.
If you want more technical, practical breakdowns for security issues with high business impact, drop your email below and we’ll send you our next articles (and nothing else).
Stay informed—because attackers certainly are.













