HTTP Request Logger
Technical details
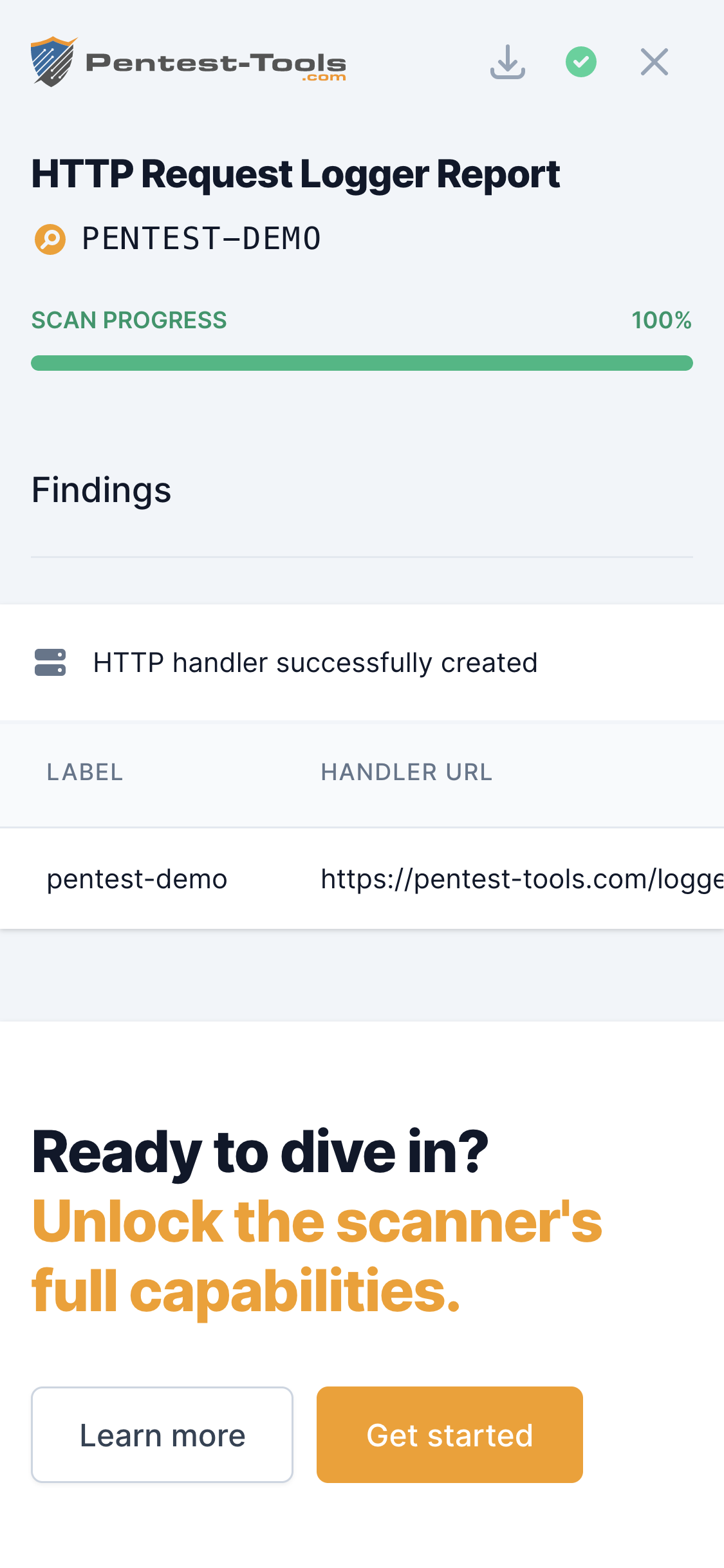
The HTTP Request Logger was created from a practical need of our pentesting team to have an always-on HTTP/S server and an easy interface to visualize the HTTP requests received.
The advantage of using this tool is that you no longer need to configure your own HTTP server, it has a valid SSL certificate and it has a simple web interface which you can also show to your clients to present the results.
Parameters
| Parameter | Description |
|---|---|
| Label | An identifier which you can associate to your HTTP handler. It can be useful to identify testing scenarios, groups of people, vulnerabilities, etc. |
How it works
The tool creates unique URLs (HTTP Handlers) which log all the requests received. The following information is recorded from the incoming request:
- Source IP address
- URL Parameters
- User Agent
- All HTTP headers
- Operating system (deducted from User Agent)
- Request date
The HTTP Handler is unique per user so no other Pentest-Tools.com user will be able to access it (unless he knows the exact URL).
The HTTP Handler has a lifetime of 15 days. After the remaining time expires, the handler will no longer log the requests received.
[Note] There is a limit of 100 requests that a single Handler can log.