Phishing a company through a 7-Zip misconfiguration
- Article tags
Reading about phishing can sometimes feel tedious, as many articles simply rehash the same old scenarios and prevention strategies without diving into technical details or offering anything fresh. But don't worry, we've got you covered!
Specifically, we will cover how attackers can exploit a misconfiguration in 7-Zip to disable the Mark of the Web (MOTW) and launch more effective phishing attacks. We’ll also show how the Client-Side Attack feature in Sniper Auto-Exploiter can help eliminate the need to manually set up and configure reverse shells in this scenario.
Keep reading to gain a better understanding of how this technique works and what mitigation options there are. So grab a cup of coffee, sit back, and get ready to expand your knowledge on these important cybersecurity issues.
Disclaimer
This material is for educational purposes only and should not be illegally recreated. Pentest-Ground.com (formerly hacking-goodies.shop ) is owned by Pentest-Tools.com, which permits you to test the techniques described in this article. Please do not attempt to recreate any of the actions described in this material outside ethical hacking engagements governed by a legal contract.
Why we decided to write about this
Back in November 2022, Adrian Furtuna, the founder of Pentest-Tools, presented a new feature in Sniper: Auto-Exploiter at DefCamp called Client-Side attack.
Phishing attacks are a type of cyber attack that use email or other forms of communication to trick people into disclosing sensitive information, such as login credentials or financial information. As you probably know, you can use VBA macros to create various types of malicious attacks that can be delivered via email or other means. When the user opens the document or clicks on a link, the macro is executed and the attack is launched.
VBA (Visual Basic for Applications) is a programming language that is built into many Microsoft Office applications, including Excel, Word, and PowerPoint. It’s used to create macros, which are automated sequences of actions that are triggered by a user-defined event, such as clicking a button or opening a document.
VBA is used to create a wide range of custom solutions, including tools for data analysis, automation of repetitive tasks, and creation of custom user interfaces. However, malicious actors also love using it to create phishing attacks.
For a short period of time, Microsoft patched this type of attack when they introduced Mark-of-the-Web (MOTW). This feature prevents macros from running if the file is downloaded from the internet.
What makes 7-Zip such a good phishing vector
As you probably know, 7-Zip is a widely used file archiving software that allows users to compress and package multiple files into a single archive file. It is open-source and supports a variety of file formats, including its own .7z format, as well as others such as .zip and .rar.
In addition to its file archiving capabilities, 7-Zip includes a command-line utility called "7z" that enables various operations on archives, such as extracting files, adding files to an archive, or creating a new archive. This utility allows for great flexibility and versatility, making 7-Zip a useful tool for both personal and professional use.
Next up, we’re gonna see how a simple 7-Zip misconfiguration can disable the Mark-of-the-Web in Office apps such as Excel, Word, and PowerPoint, which you can then use in your phishing awareness simulations.
How does this misconfiguration arise?
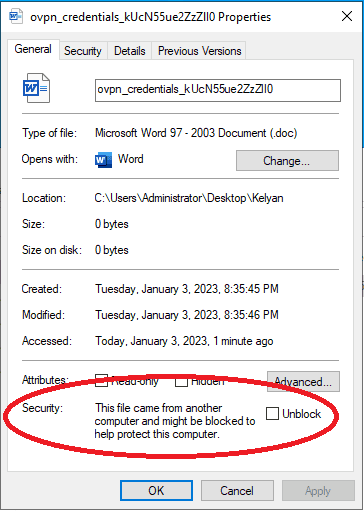
The vulnerability itself is pretty simple and straightforward. In simple terms, 7-Zip deletes the alert property when you archive a file and put a password on it.
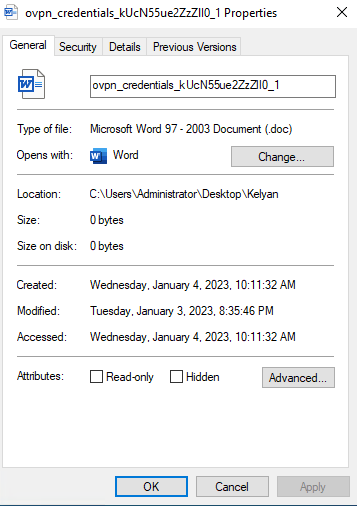
As you can see below, when you check the properties of a file downloaded from the internet, it shows an alert that won’t let you run macros.
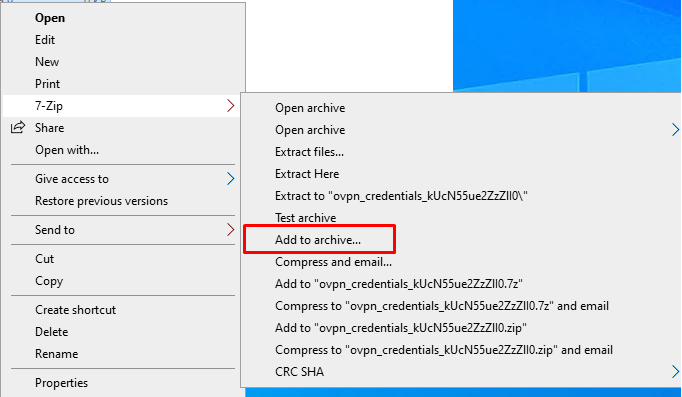
But, by archiving the file with a password in 7-zip, you can get rid of the alert and deliver it more stealthily. Right-click on the file and select Add to archive.
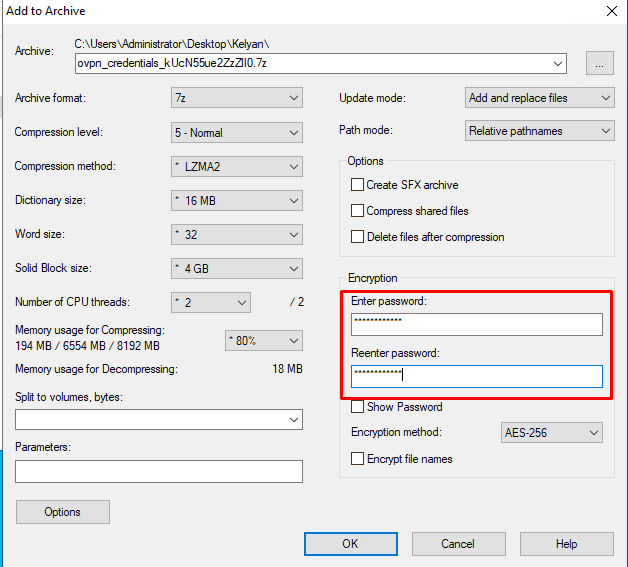
Ok, but how can an attacker profit from this scenario?
Below is a diagram explaining the steps for this scenario
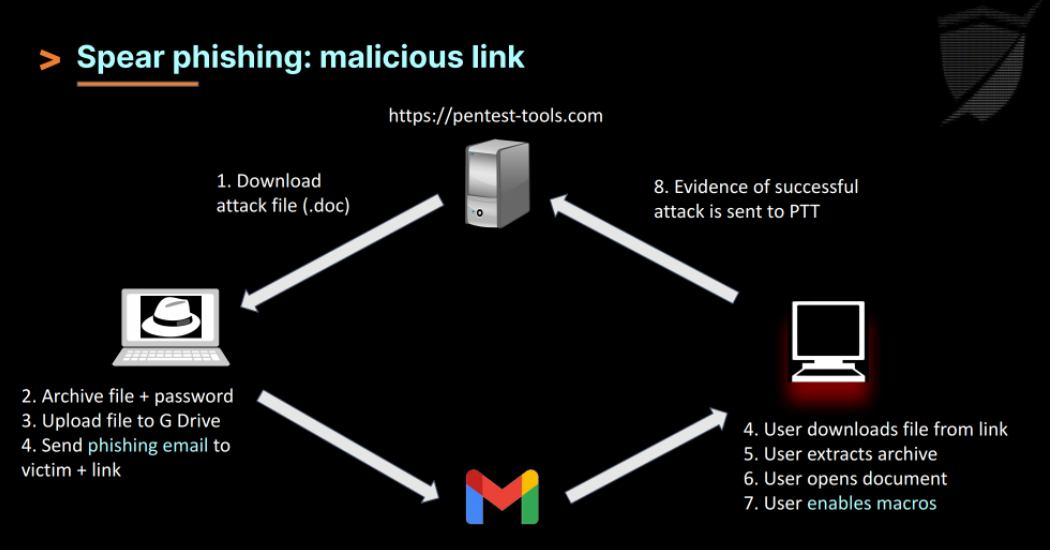
Picture the following scenario (in which we add this DMARC misconfiguration to our phishing campaign): you want internal access to hacking-goodies.shop so you can send yourself some free goodies.
You found out through OSINT that Steve is a new employee who works in the technical department, where he has access to a lot of confidential information. You also found the company uses the name.surname@hacking-goodies.shop format for employee emails.
With the collected data you can easily impersonate the CEO of the company by spoofing the mail and sending a malicious file (for security awareness purposes - obviously).
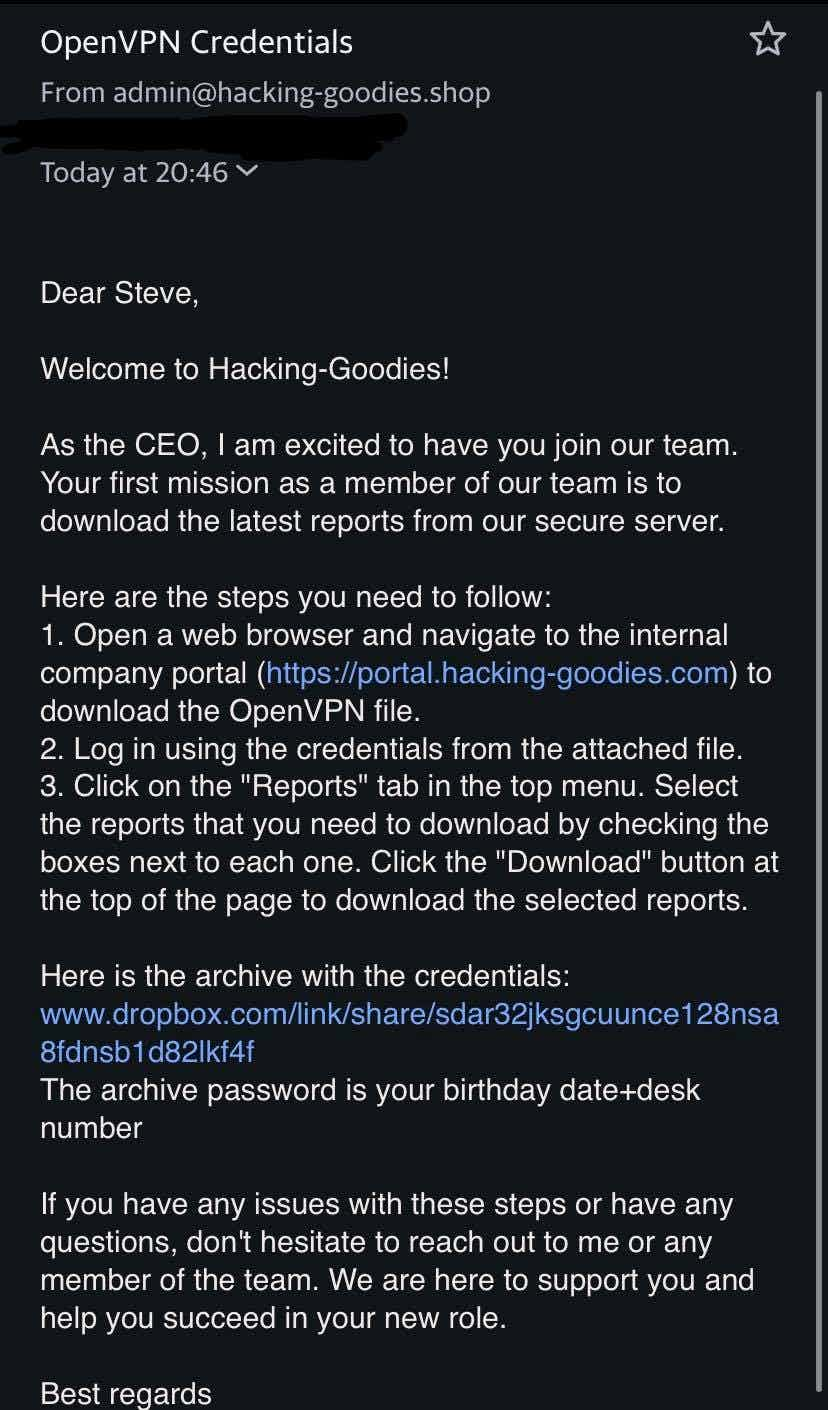
This is just a simple example, but imagine an Advanced Persistent Threat (APT) group or a State-sponsored attacker (SSA) using this misconfiguration and the power they can get from it!
Demo time: phishing simulation
Going deeper, you’re gonna get your hands dirty and practice what you’ve just learned.
Watch our colleague Stefan demonstrate how to run this scenario with Sniper: Auto-Exploiter’s Client-Side attack feature in a short video.
No target will be damaged during this phishing simulation.

How to create a more compelling report for your phishing awareness campaign
As an ethical hacker, it's important to not only be able to effectively identify and mitigate security vulnerabilities, but also to communicate the results of your work to your clients or team clearly and compellingly. This is where the new feature in Sniper comes in handy.
With the Passive attack feature, you can easily create attack handlers from our site, thus allowing you to get clear and concise results in a matter of time. This can save you valuable time and effort, as it eliminates the need to manually set up and configure reverse shells.
But the benefits of this new feature go beyond just convenience. The artefacts that Sniper extracts during the handler process can provide a much more accurate and persuasive picture of a company's exposure to potential threats. By collecting detailed data on system configurations, open ports, and installed software, you can paint a comprehensive and compelling picture of the vulnerabilities that need to be addressed.
How to mitigate this type of phishing attack
Phishing is all about attention to detail. You probably received phishing emails that seemed too obvious to fall for them. However, even the best trained ethical hackers can meet their match.
Here are 3 simple steps to follow to protect against this attack scenario, which you can steal and add to your pentest report:
1. Implement network segmentation
Implement network segmentation to limit the spread of any potential malware or other malicious code. This can help to contain an attack and make it more difficult for attackers to gain access to critical systems.
2. Train employees
Provide regular training to employees on how to identify and report potential security threats, such as phishing attacks, suspicious emails, and malicious links. This can help reduce the risk of employees falling victim to an attack and inadvertently exposing the company to risk.
3. Pay attention to details
Paying attention to details can mitigate almost all phishing attacks. Checking domain provenience, MOTW, email sender and grammar is essential in preventing being a victim.
Conclusion
This 7-Zip misconfiguration can be a powerful tool for hackers looking to bypass Microsoft Word's warning about files downloaded from the internet. in phishing campaigns. By using the 7-Zip command-line utility and strategically configuring the archive file, attackers can trick victims into downloading malware by wiping the "Mark-of-the-Web" property that is designed to prevent macros from running if the file is downloaded from the internet.
Individuals and organizations need to be aware of this potential vulnerability and take steps to protect themselves, such as implementing the appropriate defenses and training team members to be cautious when downloading files or using email, and practicing safe browsing habits.
Overall, the new artefact extraction capabilities in Sniper Auto-Exploiter are valuable additions for any ethical hacker looking to save time. These features can save you effort while providing a more accurate and persuasive picture of a company's exposure to potential threats.