How supply chain attacks work and 7 ways to mitigate them

Your organization is a connected network of vendors, software, and people that keep your business operational. Each of these elements has various degrees of access to sensitive information which a bad actor can use as entry points in supply chain attacks.
According to the 2022 Software supply chain attacks report, 62% of organizations surveyed have been impacted by these threats. Enisa’s report on the threat landscape for supply chain attacks highlights that, in 66% of cases, malicious hackers focus on the supplier’s code, while in 62% of cases they rely on malware as the main attack technique. Additionally, Gartner estimates that, by 2025, 45% of organizations worldwide will experience attacks on their software supply chains.
Therefore, it’s essential for offensive security pros to help decision-makers understand the real business risks these attacks bring on.
As a penetration tester or security consultant, identifying and reporting supply chain risk can set you apart, especially if you can explain the potential fallout in business terms. So let’s help you do just that.
What is a supply chain attack? A quick refresher
Supply chain attacks are a growing type of threat that primarily targets software developers and service or technology providers with the goal to infiltrate a company’s infrastructure through a third-party supplier with access to sensitive data.
Malicious actors use these attacks to gain access to source code, development processes, or update mechanisms so they can distribute malware by infecting legitimate programs.
Supply chain attacks are a very successful method of introducing malicious software into targeted organizations. This happens because supply chain attacks rely on the trusted relationship that exists between a manufacturer or supplier and a client.
But what tactics do these attacks use?
Let’s dig into more details.
How supply chain attacks work
The most common scenario for a supply chain attack is when a third party or a partner – the supplier – has access to critical data or a part of the internal infrastructure. With these rights, threat actors compromise the third party’s security mechanisms and gain legitime access to the resources granted to the third party vendor.
For example, attackers inject malware before the program code is built and signed. This hides the malicious code behind regular security signatures and makes it more difficult for antivirus tools to detect it.
In other cases, attackers introduce malware into legitimate software releases and upgrades via updates, patches, or compromise the email infrastructure dedicated to sending legitimate emails to customers.
One of the most interesting things about this attack is that its efficiency increases with the number of collaborative tools used by organizations/customers.
The 3 main entry points threat actors focus on when launching supply chain attacks are:
email servers
software update infrastructures
CI/CD pipelines.
Companies often manage and share third-party apps such as email clients, web browsers, or software products like the Office suite, Windows OS, and its components. For instance, VMware has many products – like VMware workstations, VMware tools, vCenter, or VMware ESXi – which big organizations use at scale.
The key for a malicious actor is to penetrate the defense of a small company and implant its own malicious software there. These kinds of SMBs often act as a supplier for bigger companies and have less protected infrastructures.
The most common scenarios for supply chain attacks are:
Compromised software building tools or updated infrastructure
Hijacked code-sign certificates or malicious programs signed under the development company's name
Specialized code that has been hijacked and distributed into hardware or firmware components
Pre-installed malware on devices (e.g. cameras, USB, phones, etc.)
To better understand how this attack works, here’s a visual representation of its flow:

4 examples of supply chain attacks and their consequences
Moving forward, let’s look at some of the most notorious supply chain attacks. We’ll see what specific concerns offensive security can flag from there to explain to decision-makers and combat such attacks.
1. The SolarWinds supply chain attack
SolarWinds is probably the most illustrative example of this type of attack. Adversaries used the SUNBURST backdoor as the main attack vector to compromise SolarWinds’ Orion management platform.
They installed malware through a third-party vendor using a Remote Access Trojan (RAT) in the latest update of the SolarWinds Orion, an IT monitoring and management package.
Data shows that the SolarWinds cyberattack impacted over 100 companies, including government institutions, telecommunications firms, and Fortune 500 large companies. IronNet’s 2021 Cybersecurity impact report highlights that, on average, this incident cost affected companies 11% of their annual revenue. In this particular cyberattack, cybercriminals targeted (and exploited) application servers and associated software update channels.
As a penetration tester, you can help organizations better secure their infrastructure by detecting and reporting critical vulnerabilities found in key components of the supply chain (e.g. collaboration platforms like Jira, BitBucket, or GitLab).
2. The CCleaner supply chain attack
CCleaner, one of the most well-known tools for software maintenance, was also at the center of a supply chain attack, which impacted over 2.3 million devices.
This attack happened in three stages:
First, attackers compromised an unattended workstation of one of the CCleaner developers, which was connected to the Piriform network (the CCleaner developing network). To do that, they used the remote support software tool TeamViewer.
With this backdoor, attackers tried the lateral movement technique to get access to a second unattended computer connected to the same network. They compiled a version of ShadowPad, a backdoor that allows attackers to download further malicious modules or steal data.
Then, threat actors installed another payload on four computers in the Piriform network (as a mscoree.dll library) and a build server (as a .NET runtime library). This allowed attackers to replace the official version of the CCleaner program with their backdoored version of the CCleaner, which was pushed to millions of users.
Security researchers at Cisco Talos detected the malicious version of the software, which was distributed through the company's official website for more than a month, and notified Avast immediately.
The malicious version of CCleaner had a multi-stage malware payload designed to steal data from infected computers and send it back to an attacker-controlled command-and-control server.
3. The FishPig supply chain attack
Another interesting supply chain attack was against the FishPig software, a vendor for the Magento e-commerce platform which provides Magento-WordPress integration software.
Cybercriminals injected the malicious code into the license source code aka license.php, but it wasn’t detected for some weeks. During this time, the software was downloaded approximately 200.000 times.
The malicious payload included some PHP code for interaction with the compromised license through which it downloaded a binary designed to install the Rekoobe remote access trojan.
The impact was high enough for researchers to say:
“Any Magento store that installed or updated paid Fishpig software since then is now likely running the Rekoobe malware”.
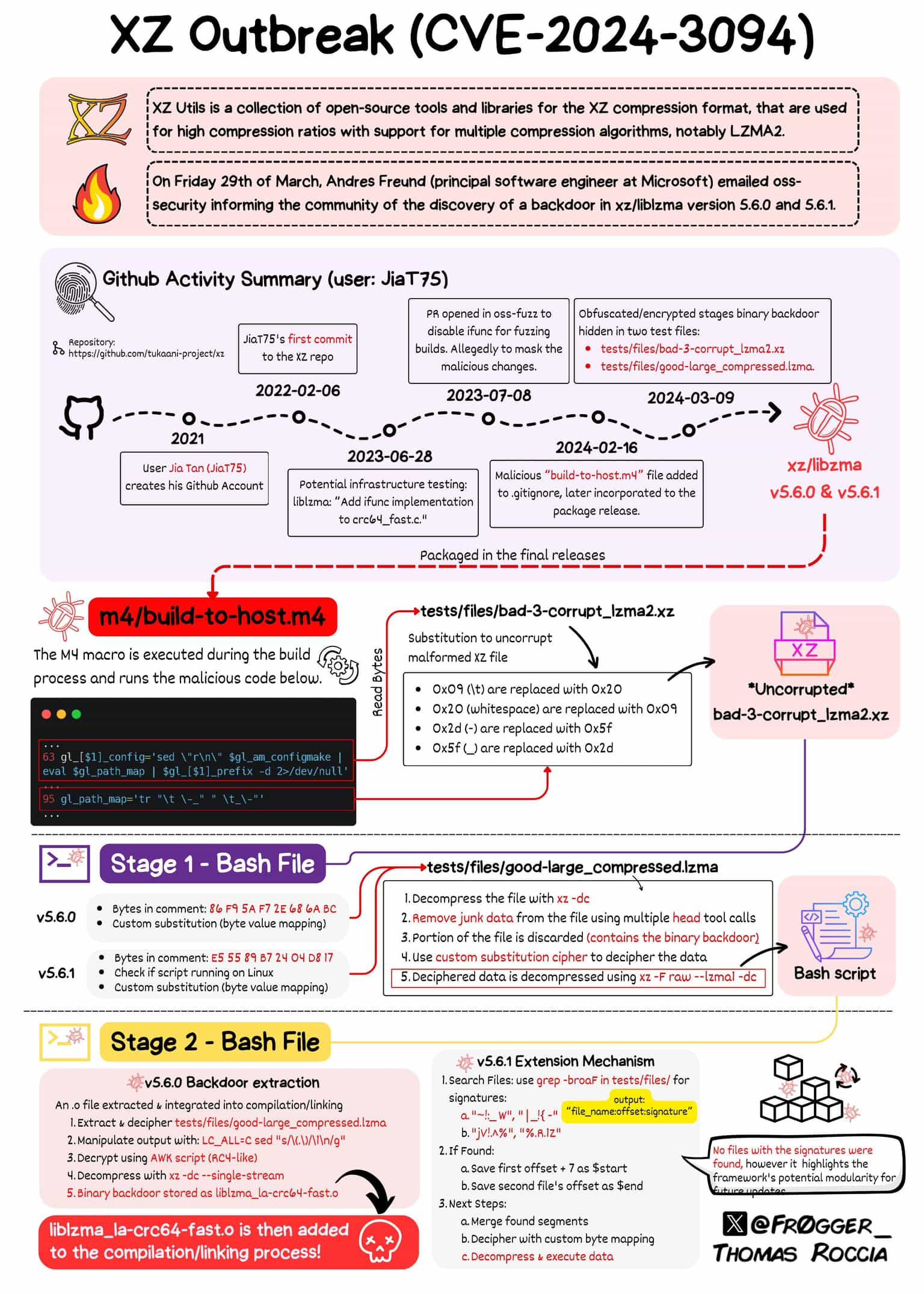
4. The XZ Utils Backdoor in Linux (CVE-2024-3094)
At the end of March 2024, a Microsoft software engineer unintentionally discovered a SSH backdoor in a toolset that comes installed by default on most modern Linux distributions.
The SSH backdoor in XZ Utils (CVE-2024-3094), the compromised toolset, would allow remote unauthenticated attackers to achieve remote code execution on the infected systems by passing the authentication in place.
While the backdoored package only managed to find its way into unstable releases (e.g. Debian unstable, Fedora Rawhide, etc.), this critical SSH vulnerability stands out through the calculated approach of the bad actor. Investigations showed that the first suspicious contributions on Github date as far back as 2021.
Given how deeply embedded open-source software is in the technical infrastructure everyone uses, the challenges of handling a supply-chain attack against its core components are massive.
CVE-2024-3094 reminded the tech community that supply chain attacks still don’t get enough attention and that ethical hackers can do more to highlight this risk and help organizations tackle it.
Common attack vectors and patterns in supply chain attacks
The NCSC (National Counterintelligence and Security Center) published a list of supply chain attacks classified based on the vector used to spread the malicious code.
Here are 5 examples of common attack vectors adversaries used to compromise companies in 2021:
VGCA
VeraPort
Twilio SDK
GoldenSpy
Copay

Source: The Director of National Intelligence
As we can see, most cyberattacks that exploit supply chain risk focus on a segment from a PKI (Public Key Infrastructure) to bypass the mechanism which grants integrity, authenticity, and non-repudiation.
It also helps to know the 3 common patterns you can find in most supply chain attacks:
Malware distribution
Exploiting the trust chain between the supplier and the final client
Attacks focus on the code of the infected product.
Attack surface management is a helpful technique that allows organizations to identify where deviations occur. It guides immediate action because this type of attack highlights how cybercriminals relentlessly search for unprotected network protocols and infrastructures that companies use on a daily basis.
How pentesters can demonstrate the risk of supply chain attacks
As an offensive security pro, you focus on understanding how vulnerabilities are exploited in threats like malware, ransomware, or supply chain attacks. In most cases, it helps to know, identify, and prove:
the type of vulnerability (Remote code execution, Local File Inclusion, Unrestricted File Upload, etc.)
the type of software, its purpose, and its widespread use.
For example, remote code execution in a software collaboration tool indicates it can be used in a supply chain attack.
To put things into perspective, in 2022, through focused scans running with the Network Vulnerability Scanner (Sniper modules option), our team detected approximately 23 targets impacted by one of the CVEs involving Exchange servers which could be used for supply chain attacks.
To better prevent and report these issues at scale, you can use a dedicated tool like our Sniper Auto-Exploiter and validate the impact of high-risk CVEs, extracting evidence for your reports.
In addition, Sniper’s feature Network Graph offers a helpful view of the inbound and outbound connections that show all paths a supply chain is made of.


Sniper’s modules offer detection through the Network Scanner and also automatic exploitation capabilities that extract solid evidence, especially for a Remote Code Execution vulnerability. This feature helps you report and mitigate the widespread exploitation of vulnerable Microsoft Exchange Servers, one of the most relevant targets in this attack.
Microsoft Exchange servers exposed around 250.000 organizations vulnerable to supply chain attacks and also generated the risk of a potential attack spreading to other organizations from various areas like banking, universities, law or government agencies, etc.
To exploit an Exchange server, a threat actor could use social engineering to attack the supply chain with the goal to spread a legitimate email to customers or another partner company and compromise their infrastructure as a result.
Should your client or organization be affected by a critical vulnerability in its most used software, you can jump straight into action and use Sniper to validate its real impact. For instance, you can cover various high-risk vulnerabilities in Exchange servers to get proof of compromise and understand the risks:
ProxyLogon - Remote Code Execution (CVE-2021-26855, CVE-2021-27065)
ProxyShell - Remote Code Execution (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207)
Each of these exploits consists of a chain of multiple vulnerabilities detectable with our Sniper modules.

This visual diagram above shows a scenario for exploiting an Exchange server (ProxyLogon)
Combat supply chain attacks with these 7 mitigation strategies
As a security researcher, I recommend having at least two stages of security evaluation of the critical infrastructure:
First, do an audit of your own infrastructure to validate all endpoints’ input and interaction between exterior and interior flows. You can implement this kind of mechanism through: an IDS (Intrusion Detection System) or IPS (Intrusion Prevention System), a vulnerability scanner, periodic logs checks, and manual verification to assess how correct the traffic data and evidence provided by the vulnerability scanner are.
The second stage consists of implementing a cooperative policy with a third-party software vendor for a security audit of their infrastructure. Even if you trust the vendor, recent supply chain attacks reveal how difficult it is to ensure protection against them. The main focus of this collaborative process is to identify critical vulnerabilities that a potential threat actor could use to compromise the supply chain (e.g. remote code execution, authentication bypass, arbitrary write files, etc.).
Here are 7 actionable strategies you can use in your ethical hacking reports to help customers reduce the impact of supply chain attacks:
1. Implement the principle of least privilege
Organizations often provide their employees, partners, and software unnecessarily broad access and rights. These excessive permissions facilitate supply chain attacks. Try to implement the principle of least privilege and only provide the permissions they actually need to do their jobs.
Pro tip: In case of an attack, the threat actors will be limited only to the compromised operating system and won’t be able to go further to deploy their malicious code.
2. Deploy network segmentation and Zero Trust
Third-party software and partner companies do not require complete network access. To divide the network into zones depending on business functions, make sure to use network segmentation. As a result, even if a supply chain attack compromises a part of the network, the rest remains secure, while Zero Trust ensures that only authorized parties can gain access in the first place.
Pro tip: Applying this measure, you get more control over your network traffic and streamline your security policies.
3. Follow DevSecOps best practices
Add powerful security practices in the development workflow to help you detect fraudulently updated software and respond to changes quickly.
Pro tip: This kind of measure is often ignored but it is highly recommended because serious security breaches often originate in a bad chain of developing operations.
4. Assess critical assets
Start by understanding precisely which components are your organization's most valuable IT assets. Then, examine the worst-case scenario and use it as the foundation for building your incident response plan.
Pro tip: This method can also help to distribute existing resources to areas where they’ll have the most impact in critical situations.
5. Conduct regular vendor checks
Take the time to examine the complexity of the product before implementing a new application or technology. Check the vendor's help forums to see whether other users encountered similar issues and how fast the seller reacts to complaints.
There are types of programs that use old, outdated software code with no regular review for critical vulnerabilities, which you should absolutely avoid. Creating a culture of open and transparent communication with selected software providers and gaining a comprehensive knowledge of their security procedures is also essential.
Pro tip: This practice will help your company make more informed business decisions and build better vendor relationships, reducing security and non-compliance risks.
6. Review Remote Monitoring and Management (RMM) tech
If your company has an external technology partner who receives access to your infrastructure using RMM technologies, be extra careful. If that organization's RMM tools are compromised, attackers may obtain direct access to your network.
Pro tip: Do a monthly (or yearly) review of your RMM tools and check if they lack any security updates.
7. Help management understand the risks
Because supply chain security is less known than other aspects of IT security, it is vital to explain business impact and its risks in plain terms to management and other non-security decision-makers. This way, your company can take the necessary actions to prevent such attacks: identifying key risks, building a risk-management framework, monitoring, and reviewing
Pro tip: Make sure the team responsible for developing, deploying, or integrating the vendor’s software is well-trained to recognize the possible types of attacks (e.g. phishing attacks, data breaches, or other security incidents).
Develop an incident response process for supply chain attacks
As a pentester, you focus on helping decision-makers prioritize supply chain security and use the right risk management processes to better respond to these attacks.
One challenging aspect is helping others understand how a serious vulnerability opens up the business to serious and costly implications. For example, threat actors often use RCE to compromise services or programs from inside the network to trigger another supply chain attack.
If, as a pentester, you execute a successful remote code execution for a client, I recommend investigating the internal network further and looking for more vulnerable entry points.
If the exposed target has enough potential to carry out a supply chain attack, work with business owners to implement a good incident response process. This way, you can help the organization handle such attacks quickly and minimize risks across business areas (e.g. financial, reputational, compliance, etc.).









