OWASP & CWE vuln classifcation added, wordlist limit increased, and more updates

This month we rolled out 5 platform improvements that streamline your pentests so you can do more of the work you most enjoy:
1. Website Scanner findings – OWASP 2013/2017 & CWE vuln info added
2. Wordlists limit increased: add more lists with 5X more words each
3. NEW: the Password Auditor now supports NTLM authentication
4. Filter URL Fuzzer results based on customer matches
5. Custom request timing options with the URL Fuzzer
Let’s unpack them!
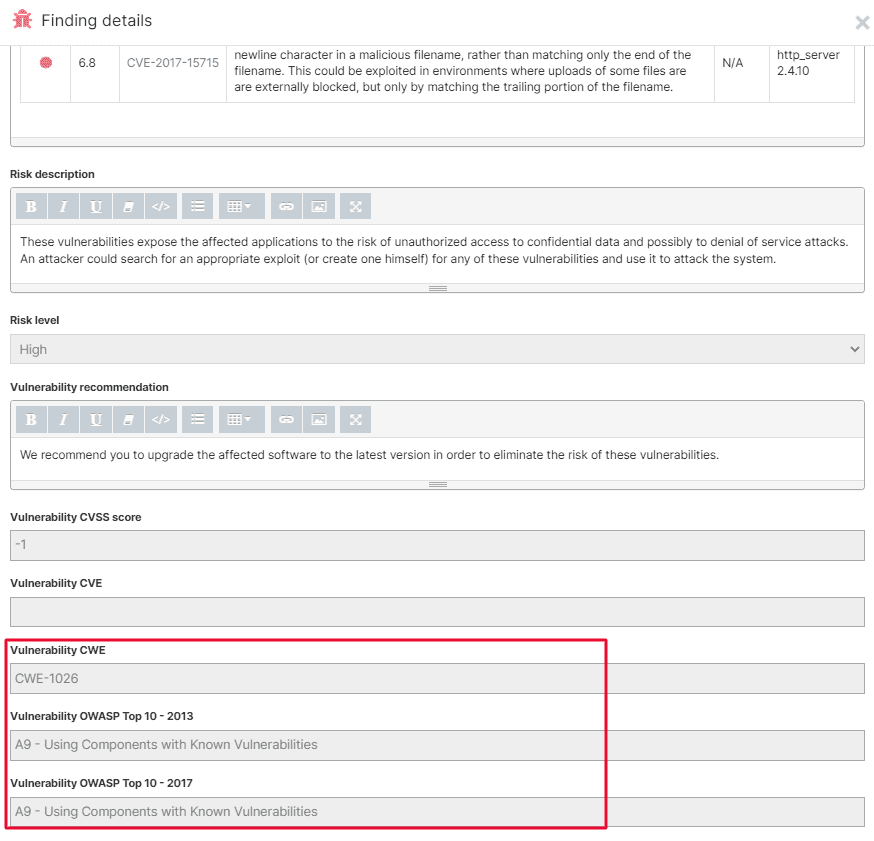
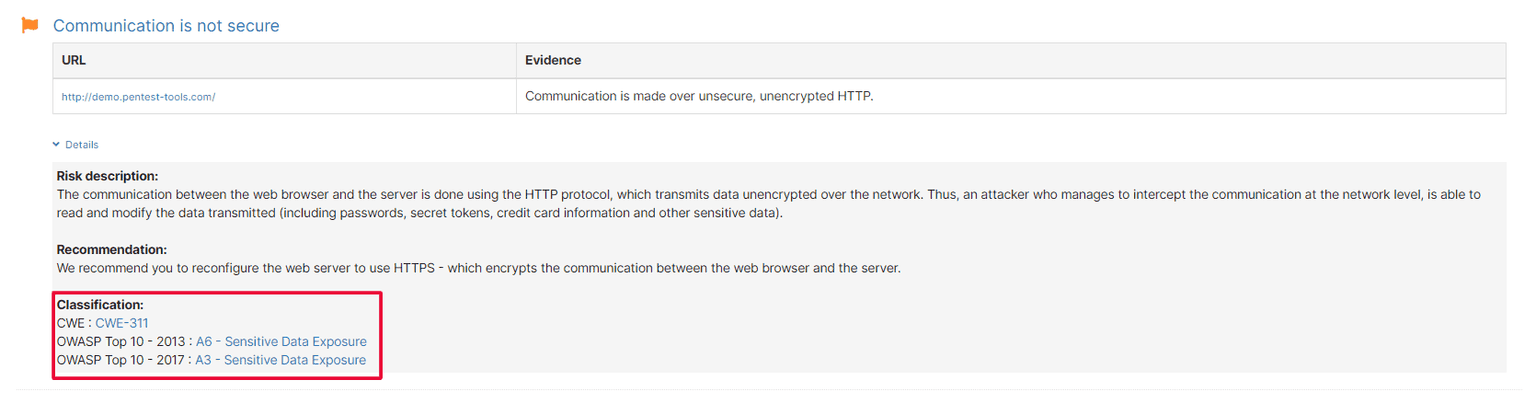
1. Website Scanner findings include OWASP 2013/2017 & CWE vuln info
The findings’ descriptions you get from our Website Scanner now include the class of OWASP Top 10 of 2013 and 2017 they’re part of and their assigned CWE number.
To see this info, go to Findings and select the ones you need to see more details. You can also visualize it from Scans, where you check the scan results of your target. Just click on the Details to see the Classification.
Remember you can automatically pull these details in your reports when you choose which Findings to include in them.
2. Wordlist limit now increased up to 50.000 words
Good news! We increased wordlist limits from 10.000 words to 50.000 words. You can now add even more words (usernames, passwords, config files, etc.) to test against your targets from your Pentest-Tools.com account.
For each wordlist you create, you can include up to 50.000 words, where each word has a maximum length of 200 characters.
Use default wordlists we provide or add your own for faster, smoother pentests.
Create your wordlist
3. The Password Auditor now supports NTLM authentication
We also improved the Password Auditor by adding support for the NTLM (New Technology LAN Manager) authentication protocol.
Authentication through NTLM uses a challenge-response protocol and, as a form of Single Sign-On (SSO), does not require users to send unprotected passwords over the network.
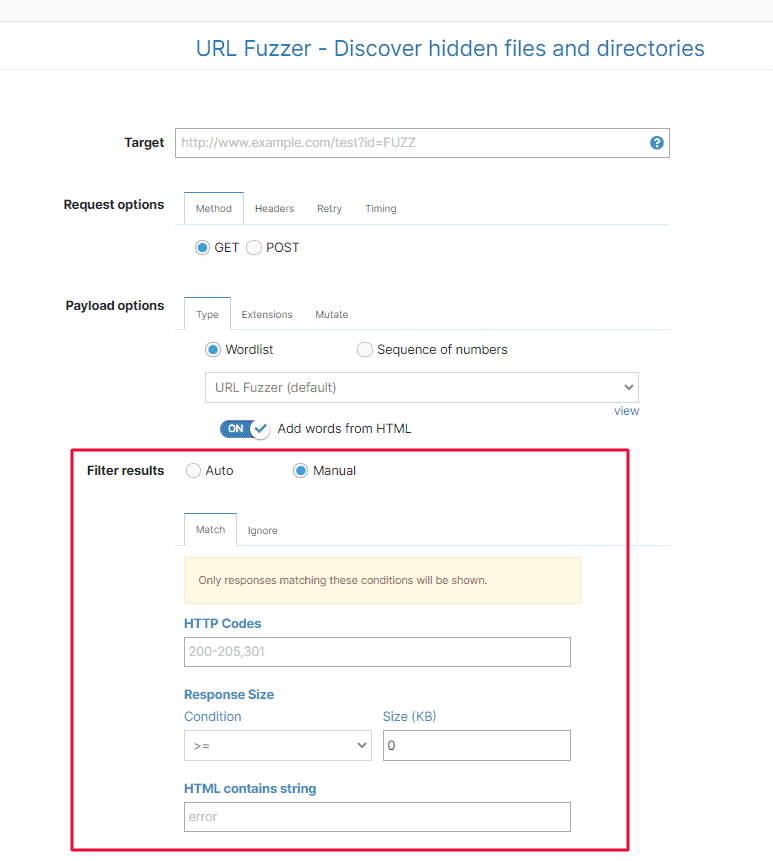
4. Filter URL Fuzzer results based on custom matches
Another improvement we made is the option to automatically filter URL Fuzzer results based on the conditions you choose.
Depending on your engagement, you can now:
ignore or match certain HTTP codes
ignore or match if the HTML contains a string
ignore or match certain conditions for Response Size.
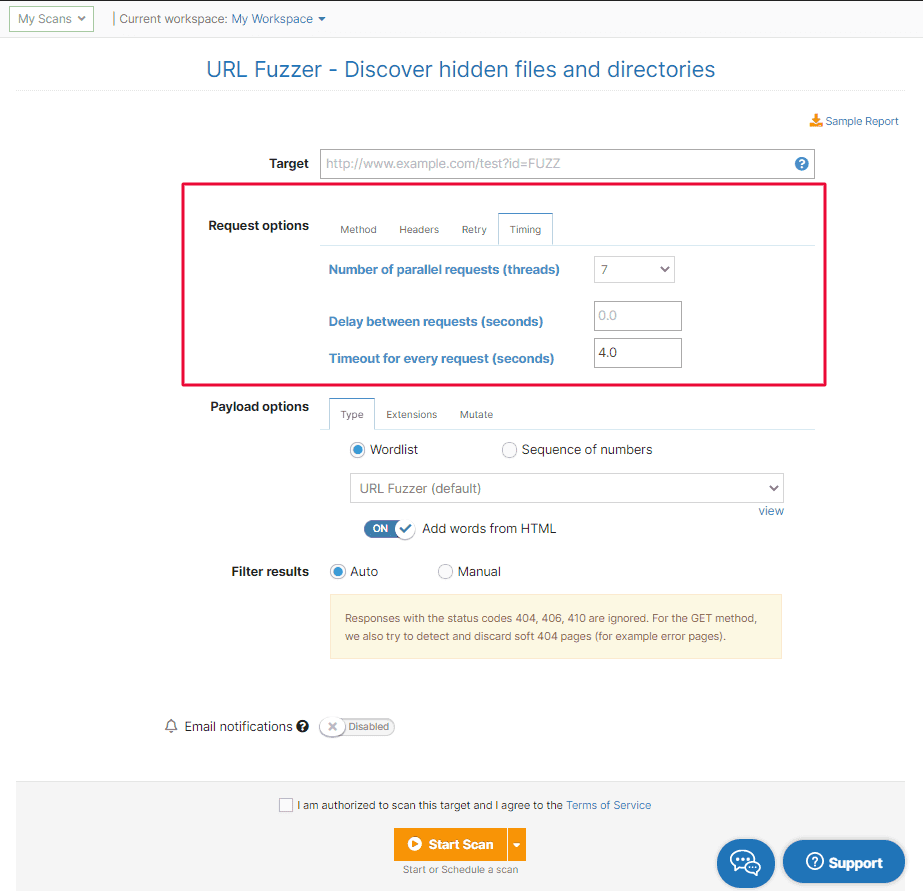
5. The URL Fuzzer now includes custom request timing options
We’ve also added a custom request option to the URL Fuzzer, which allows you to define specific timing for your HTTP requests.
When you go to URL Fuzzer, add your URL target, and select Timing, you can define the number of parallel requests the tool will run for you.
You can also set a maximum of 10 retries per request.
Here’s a snapshot of the new option: