Website Vulnerability Scanner
Our custom-built Website Vulnerability Scanner detects SQLi, XSS, command injection, XXE, and 75+ more web app vulnerabilities in record time, using proprietary test payloads to prove their exploitability.
Engineered for modern web apps architectures, it crawls SPAs and JavaScript-heavy sites, uncovers hidden API endpoints, and navigates complex authentication flows with ease.
Each scan delivers a clear, customizable report with prioritized risks, actionable evidence like screenshots and attack replays, and straightforward remediation steps so you can fix issues faster.
- Scan type
Light scan
- CLI scan
A light scan with the Website Vulnerability Scanner runs passive security tests to detect up to 10 types of web app issues: outdated server software, insecure HTTP headers, weak cookie and server settings, and more.
See the full list of testsOur custom-built Website Vulnerability Scanner detects SQLi, XSS, command injection, XXE, and 75+ more web app vulnerabilities in record time, using proprietary test payloads to prove their exploitability.
Engineered for modern web apps architectures, it crawls SPAs and JavaScript-heavy sites, uncovers hidden API endpoints, and navigates complex authentication flows with ease.
Each scan delivers a clear, customizable report with prioritized risks, actionable evidence like screenshots and attack replays, and straightforward remediation steps so you can fix issues faster.
Find exploitable web app vulnerabilities with documented evidence
Our proprietary Website Vulnerability Scanner gives security pros and appsec teams what they need: highly accurate, validated findings and actionable evidence - not just a long list of possible exposure points.
Unlike generic scanners that flag potential issues without context, our tool uses out-of-band detection to minimize false positives and ensure reliable results, collecting proof along the way.
Perform unauthenticated recon, deep authenticated testing, or automated compliance scans - all with a powerful, easy-to-use tool that blends into your workflow.
Get more from every scan. Test web apps like a real attacker
Simulate authenticated and unauthenticated attacks to uncover deeper security flaws, such as SSRF with access to an internal service, OS command injection, exposed credentials, and misconfigurations in SPAs, APIs, and traditional web apps.
The Website Vulnerability Scanner on Pentest-Tools.com mimics real attackers’ tactics and focuses on realistic, exploitable issues rather than ticking boxes.
We keep it sharp by battle-testing it every day in web app pentests that our offensive security services team performs.
Trust your results. Minimize FPs with proof-based validation
Our Website Vulnerability Scanner doesn’t just find web app security issues - it gives you the evidence you need to validate and report real security risks.
As it crawls and tests your web app, it captures payload execution results and collects evidence such as HTTP request/response with highlighted proof, screenshots, and extracted sensitive data. The scanner also uses out-of-band detection to find invisible vulnerabilities which don’t show up directly in the HTTP responses.
When it’s confident the vulnerabilities it found actually exist, the scanner’s automatic validation feature applies a "Confirmed" label. Where available, it also gives you an instant replay attack option.
Need more? Get additional proof for PoCs with one-click tests with our offensive security tools for web apps - the SQLi Exploiter and XSS Exploiter.
Get deeper findings, faster. Even from JavaScript-heavy websites
Our Website Vulnerability Scanner uses a powerful browser-based crawler to scan Single Page Applications (SPAs) and other JavaScript-heavy websites - fast and accurately.
Because it uses parallelization to detect cloud-hosted URLs, it speeds up discovery and attack surface mapping, giving you findings faster.
Scan results include deeper insights too, such as API endpoints detected during crawling, automated OpenAPI fuzzing, and improved detection for publicly accessible files and pages that should’ve been hidden.
This approach ensures comprehensive attack surface coverage and higher vulnerability detection rates.
Customize any scan. Advanced features for in-depth detection
The Website Vulnerability Scanner adapts to the complexity of the web apps you’re testing, offering flexible scan configurations to get precise results.
Adjust the spidering approach and depth and the number of requests per second to match your target's environment. You can even set custom scan times to make every second count.
The scanner also navigates complex authentication flows and uses session recording, form-based authentication, headers, and cookies to test behind login pages and detect vulnerabilities to which only authenticated users get exposed. Think CSRF, broken access controls, session misconfigurations, and 75+ more web app vulnerabilities.
Enjoy benchmark-proven performance. See for yourself
The Website Vulnerability Scanner from Pentest-Tools.com delivers industry-leading detection accuracy, matching top commercial tools while keeping a notably lower false-positive rate.
Tested against 5 leading commercial and open-source scanners, it identified 98% of known vulnerabilities in realistic test environments, outperforming several competitors.
With standardized, transparent test criteria reflecting what pentesters and AppSec engineers need in a DAST tool, this benchmark confirms its superior accuracy, reliability, and depth.
With its ability to reduce false positives more effectively than tools like Qualys and Rapid7 InsightAppSec, our scanner helps security teams from 95+ countries find and validate real risks.
Generate proof-backed reports. Make sure remediation happens
Our built-in advanced reporting tool transforms raw findings into structured, actionable reports on which developers, IT teams, and management can act immediately.
Findings come with risk levels, risk description, and step-by-step remediation guidance to drive real fixes. Every report includes proof, such as screenshots, payload execution results, and highlighted HTTP request/response data to back up findings. Vulnerabilities are mapped to CWE and OWASP Top 10 (both 2017 and 2021) to help security teams prioritize risks effectively.
With customizable report formats, you can present Website Vulnerability Scanner findings to technical teams, executives, or auditors, making security issues impossible to ignore.
Website scanner introduction

Latest scanner updates
Improved detection accuracy for active detectors in the Website Scanner
We’ve improved the detection accuracy of active detectors in the Website Vulnerability Scanner to surface more real issues with less noise.
This update adds coverage for:
• CSRF bypass via POST/PUT to GET conversion
• Insecure CORS configurations caused by subdomain trust
• Serialized object detection in JSON payloads to flag potential deserialization risks
These improvements help reduce false positives and provide clearer signals during validation and triage.
SQLi detectors uses more payloads in all custom cookies and has reduced false positives
We’ve just rolled out an update to Website Scanner’s active SQLi detection: it now injects payloads into all custom, non-standard cookies and cuts down false positives by skipping cookies that were already checked. This means broader coverage on real-world apps that stash input in quirky cookie names, without noisy duplicates in your results.
Why it matters
SQL injection still shows up in places scanners can miss, especially in custom cookies used for state, feature flags, or tracking. By extending payload injection to every custom cookie, Website Scanner can uncover SQLi paths that previously hid outside “standard” cookie patterns. At the same time, the improved logic avoids re-testing cookies it has already validated, which reduces repeat hits and lowers the chance of false positives. Net effect: more real findings, less triage fatigue.
How to use
Run Website Scanner as usual → review any confirmed SQLi findings → validate further with SQLi Exploiter if needed → fix and re-scan to confirm remediation and ensure no custom-cookie vectors remain exposed.
Added CL.0 request smuggling detection in our HTTP desync attacks active detector
Inspired by James Kettle's article and to keep on top on latest research, we introduced the new CL.0 Request Smuggler in our HTTP Request Smuggling detector from Website Vulnerability Scanner. It is automatically enabled inside the detector and it helps uncover more request smuggling attacks.
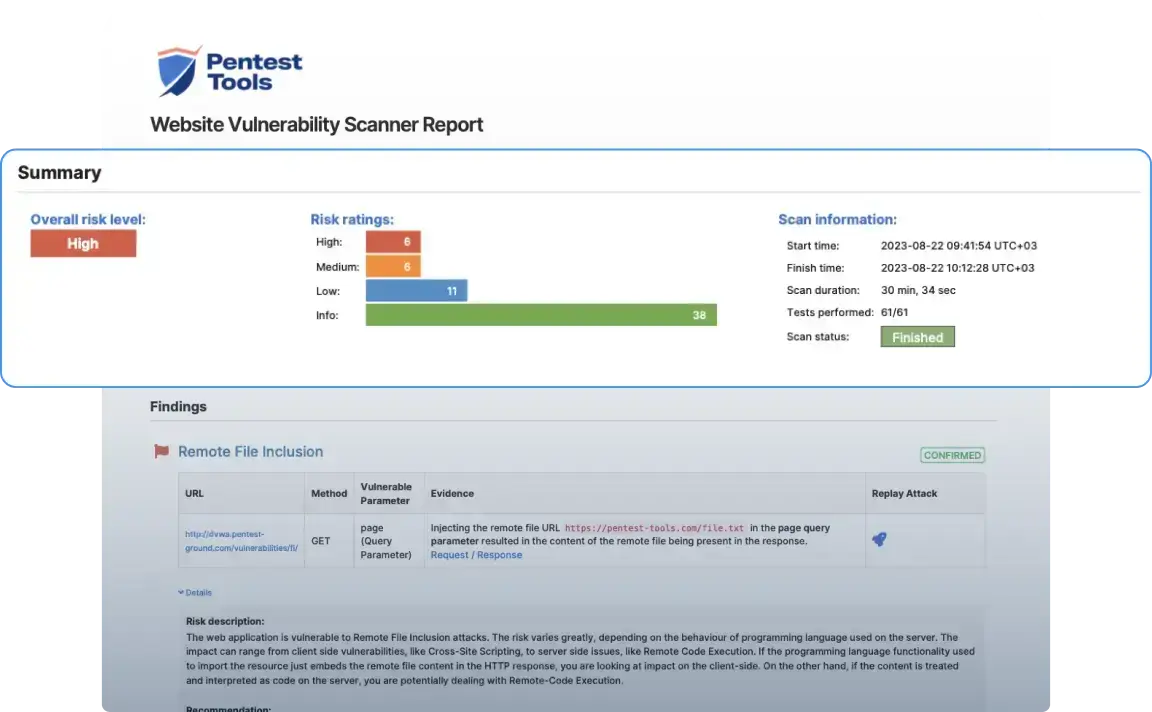
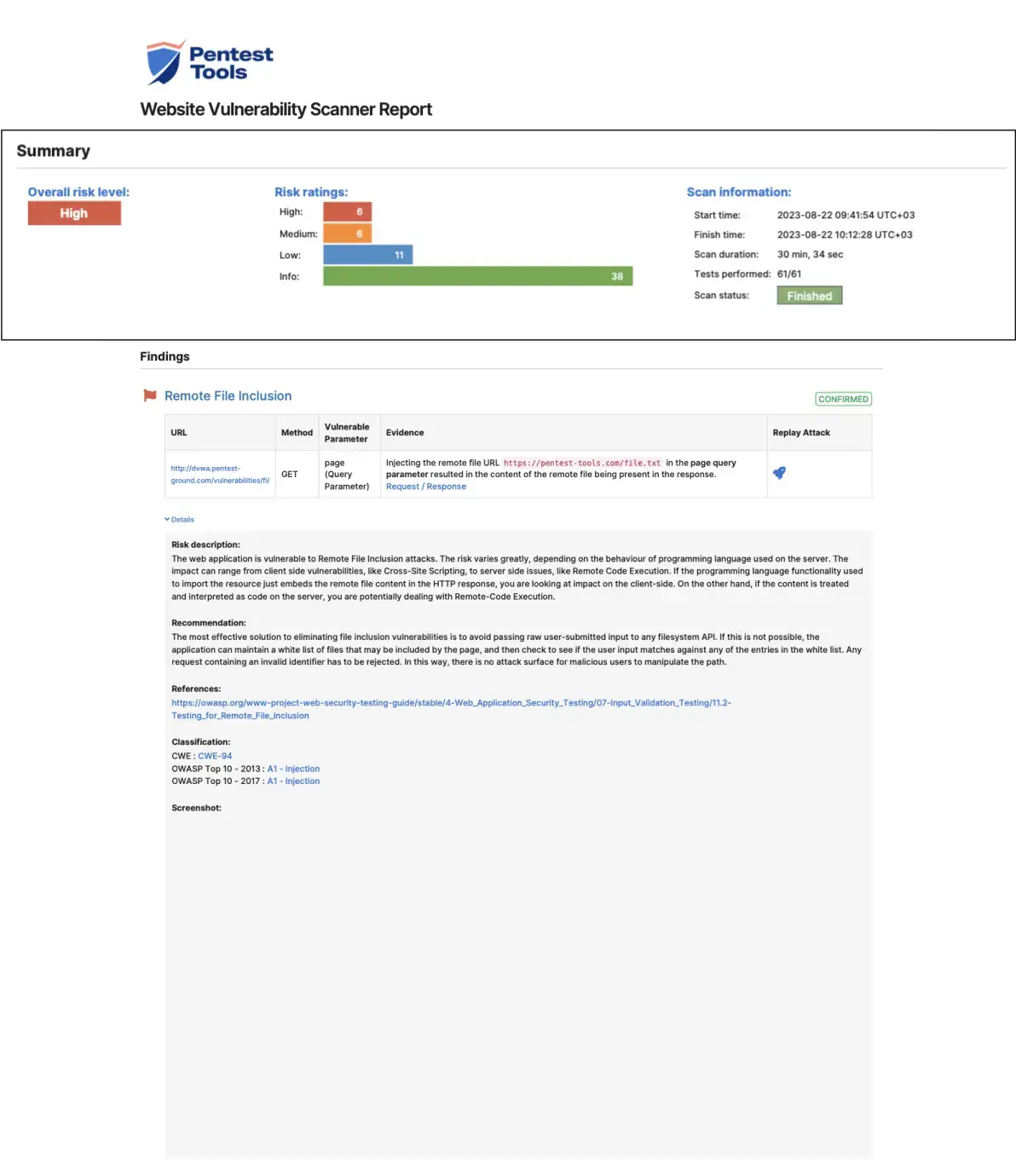
Sample Website Vulnerability Scanner report
This sample report from our scanner shows the main sections it includes, the look and feel, plus the level of detail for the findings.
This section provides a helpful overview of the findings and a visual representation of risk levels across all identified vulnerabilities.
A website is more than just web pages.

How does the Website Vulnerability Scanner work?
The Website Vulnerability Scanner is a DAST (Dynamic Application Security Testing) tool designed to discover vulnerabilities like XSS, SQL injection, HTTP Prototype Pollution, Directory Traversal, and 75+ more vulnerabilities in running web applications.
The scanner interacts with the target application by sending numerous HTTP requests with specific payloads. If the application is vulnerable, these payloads will determine the code to behave abnormally, informing the scanner that a vulnerability exists.
Resource discovery
First, the scanner attempts to discover various endpoints, sensitive files, and hidden paths on the target server. It does this by searching for predefined URLs (based on wordlists and other techniques) and it can discover paths such as:
/admin/logs/info.php/.env/.git/backup.zip
Spidering
Based on the target URL and endpoints it discovered in the previous phase, the Website Scanner starts to recursively visit each URL and create a map of the dynamic pages, together with their input parameters (called Injection Points). The scanner will use them as entry points for the active scanning component.
To be able to visit SPA applications (React, Angular, Vue.js, etc), the Website Vulnerability Scanner uses headless browsers which can load and render the entire web pages in memory.
Active scanning
While the Spider is running, another component of the Website Scanner takes each previously discovered Injection Point and injects multiple payloads to detect vulnerabilities. Such payloads may include:
“><script>alert()</script>"'--><img src onerror=alert()>'"--></noscript></title></textarea></style></script><svg/*/onload=alert()//>
and many more.
Passive scanning
To detect interesting information and leaked sensitive data, the Website Vulnerability Scanner also analyzes each HTTP response passively. This is how it detects juicy findings, such as:
- Email addresses
- Credit card numbers
- Directory listing
- API endpoints
- HTTP headers security, etc.
Version-based CVE detection
Besides specific application vulnerability detection, the Website Vulnerability Scanner also discovers vulnerabilities in libraries and standard components the application uses.
It first fingerprints third-party components like JavaScript libraries, programming frameworks, server software, etc., and tries to determine their running version. Based on this information, it interrogates a database of 100,000+ known vulnerabilities (CVEs) which may affect the specific version of software and return the results in the report.
Full list of security tests performed
The Deep version of the Website Vulnerability Scanner performs a complete security assessment of your target application. Here’s a list of all the 40+ vulnerability checks performed by the Deep version of the scanner, as compared to the Light version:
Tests performed Light scan Deep scan Fingerprint web server software Analyze HTTP headers for security misconfiguration Check the security of HTTP cookies Check the SSL certificate of the server Check if the server software is affected by known vulnerabilities Analyze robots.txt for interesting URLs Check whether a client access file exists, and if it contains a wildcard entry (clientaccesspolicy.xml, crossdomain.xml) Discover server configuration problems such as Directory Listing Check if HTTP TRACK/TRACE methods are enabled Check if security.txt is missing on the server Check if CORS is misconfigured Crawl website Check for SQL Injection Check for Cross-Site Scripting Check for Local File Inclusion and Remote File Inclusion Check for OS Command Injection Check for ASP Cookieless Cross-Site Scripting Check for Server Side Request Forgery Check for Open Redirect Check for PHP Code Injection Check for JavaScript Code Injection Check for outdated JavaScript libraries Find administrative pages Check for sensitive files (archives, backups, certificates, key stores) based on hostname and some common words Attempt to find interesting files / functionality Check for information disclosure issues Weak Password Submission Method Clear text submission of credentials Verify domain sources Check for commented code/debug messages Find login interfaces Sensitive Data Crawl Insecure Deserialization NoSQL Injection Session Fixation IDOR JWT weaknesses Fuzz OpenAPI specification locations Misconfigurations Find GraphQL endpoints
Cut web fuzzing false positives by 50% with the integrated Machine Learning Classifier
The ML Classifier, a purpose-engineered model integrated into our Website Scanner and URL Fuzzer, helps you filter out noise and zero in on real issues - automatically.
Instead of relying on brittle RegEx logic, the ML Classifier analyzes every HTML response during a scan and every HTML response and assigns it to one of four smart categories:
- HIT: High-value targets like login pages, backups, and exposed secrets
- MISS: Confirmed dead ends, even with misleading status codes
- PARTIAL HIT: Ambiguous but interesting responses, like firewalls
- INCONCLUSIVE: Pages needing browser rendering to confirm
This structured triage filters out dead ends, repeated templates, and language-specific error pages that traditional scanners often mistake for vulnerabilities.

Use this tool from your command line interface
If you prefer it, we also provide a CLI version of our Website Vulnerability Scanner. Through the Pentest-Tools.com CLI, you can run Light scans against your web apps and start gathering insights for your next move.
1. Installation
curl -s https://pentest-tools.com/cli-scan/linux/ptt.zip -o /tmp/ptt.zip
unzip /tmp/ptt.zip -d /tmp/ptt
chmod +x /tmp/ptt/main
sudo mv /tmp/ptt/main /usr/local/bin/pttIf you have docker or pip installed, you can use them to get ptt-scan:
docker run --rm -it pentesttoolscom/ptt-scan:latest run website_scanner https://pentest-ground.com:81/2. Usage
Quickstart: Run the following command in your terminal/command line to find the vulnerabilities of your website.
ptt run website_scanner <target_url>You can learn more options with the -h flag:
ptt -hEasy enough for quick scans. Advanced enough for deep testing.
Start scanning in seconds - no setup required
As a cloud-based scanner, the Website Vulnerability Scanner on Pentest-Tools.com works out of the box - no installation, configurations, or maintenance needed. Just create an account, enter your target URL, and launch a scan with a preconfigured scan setup - or choose the passive and active checks you need.
Automate website security scans with flexible scheduling
New vulnerabilities love to pop up at the worst times - Friday nights, weekends, you name it. Stay ahead with scheduled scans on your terms - daily, weekly, or whenever you need. The moment our scanner finds a new exposure, it alerts you instantly via email, webhooks, or security tools, so you can strike before attackers do.
Integrate, automate, and streamline with our API
Many security teams prefer to trigger scans programmatically using our REST API. This enables quick integration with CI/CD pipelines, security dashboards, vulnerability management tools, or custom applications - eliminating repetitive, time-consuming work and making security testing an integral part of your development process.
Scan internal web apps without making assets public
Need to scan apps behind firewalls, on private clouds, or internal networks? Our VPN Agent securely routes traffic from our cloud-based scanner to your internal infrastructure - so you can detect risks without exposing your assets to the internet.
Integrate scans results into the tools you already use
Keep vulnerabilities out of spreadsheets and in the tools that matter. Sync findings with Jira, Slack, CI/CD pipelines, GitHub Actions, Microsoft Teams, and Vanta. Need more control? Use webhooks or the Pentest-Tools.com API to push security issues into your custom dashboards.
Customer reviews
Pentest-Tools.com is my team's first go-to solution. Anytime we are preparing to deploy a new version of our software, we run many tools to monitor and secure our environment, but the simplicity and ease we have with Pentest-Tools.com to run network and web server scans to highlight issues is unmatched.
Michael Dornan
CEO at Tili Group
Israel 🇮🇱


Common questions about web vulnerability scanning
What is a web vulnerability scanner?
A web vulnerability scanner is a specialized software tool designed to automatically identify security flaws within web applications. A reliable, robust website security scanner should be able to mimic real attacker tactics and identify realistic, exploitable security issues.
Our Website Vulnerability Scanner is a robust example of this type of tool, offering a comprehensive scan that identifies threats and also validates them to reduce false positives.
It works by interacting with the target application, sending a series of HTTP requests with specific payloads, and analyzing the responses to detect potential vulnerabilities such as Cross-Site Scripting (XSS), SQL injection, OWASP Top10, and other pressing security issues and misconfigurations.
What types of web vulnerabilities can the Website Vulnerability Scanner detect?
The Website Vulnerability Scanner detects SQL injection, XSS, command injection, SSRF, HTTP Prototype Pollution, and 75+ other security flaws. It also finds misconfigurations, outdated software, and sensitive data leaks.
How long does a website security scan take?
Our Website Vulnerability Scanner is optimized for speed, depth, and accuracy, so time to completion for specific scans depend on the complexity of the web app you're assessing. When you use the Light Scan version, completion time is typically under 2 minutes.
Most website scans which use the Deep scan version finish in under 1 hour, but can last for up to 24h, depending on how elaborate the web app is.
What’s the difference between a Light Scan and a Deep Scan with the Website Vulnerability Scanner?
The Light Scan performs passive tests by analyzing the HTTP responses of the crawler and active detectors. It discovers basic misconfigurations, sensitive resources and other security issues, while the Deep Scan runs 40+ advanced security tests to find SQLi, XSS, SSRF, OS command injection, prototype pollution, and more.
Can I use it to scan Single Page Applications (SPAs) and JavaScript-heavy websites?
Yes. Our proprietary Website Vulnerability Scanner uses a browser-based crawler that renders React, Angular, and Vue.js applications in memory, allowing it to detect API endpoints, client-side injection points, and hidden vulnerabilities.
How does the Website Vulnerability Scanner detect vulnerabilities in third-party components?
Our custom Website Vulnerability Scanner fingerprints JavaScript libraries, frameworks, and server software, then quickly matches them locally against the standard NIST database of known CVEs, identifying vulnerabilities in outdated components.
How do I scan a password-protected site for vulnerabilities?
Being able to perform in-depth scanning and uncover critical vulnerabilities that an attacker can exploit after logging into the website (or web apps) is absolutely essential for a high-quality assessment.
Our custom Website Vulnerability Scanner supports session-based authentication, including form-based login, headers, cookies, session recording and automatic login to test behind protected pages and detect vulnerabilities affecting authenticated users.
So here is how easy it is to use our Website Vulnerability Scanner to scan password-protected websites , along with the various authentication methods we provide.
How does the Website Vulnerability Scanner minimize false positives?
It uses proof-based validation, capturing screenshots, payload execution results, HTTP request/response data, and running out-of-band detection to confirm vulnerabilities before reporting them.
Can I schedule recurring website vulnerability scans?
Yes, you can use the Website Vulnerability Scanner to schedule scans to run daily, weekly, monthly, quarterly, or yearly, to ensure consistent monitoring and get automatic alerts when new risks appear.
Does the Website Vulnerability Scanner support integrations with other security tools?
Yes. You can send findings and sync them with Jira, Slack, Microsoft Teams, GitHub Actions, Vanta, and more. We also offer webhooks and a REST API for custom integrations to easily find and monitor security vulnerabilities.
What kind of reports does the Website Vulnerability Scanner generate?
The Website Vulnerability Scanner we built in-house generates customizable, proof-backed reports that include risk prioritization, OWASP and CWE classifications, step-by-step remediation guidance, screenshots and technical evidence for each finding.
Report formats include PDF, HTML, JSON, CSV, XLSX, and even customizable DOCX reports with personalized branding options.
How does the Website Vulnerability Scanner compare to other tools in the industry?
The Pentest-Tools.com Website Vulnerability Scanner was benchmarked against five leading commercial and open-source scanners, identifying 98% of known vulnerabilities in realistic test environments.
It demonstrated industry-leading accuracy, a lower false-positive rate, and stronger out-of-band detection compared to tools like Qualys and Rapid7 InsightAppSec. Check out the full benchmark results for detailed technical information and performance graphs.
How effective is the Website Vulnerability Scanner for penetration testing?
The Website Vulnerability Scanner from Pentest-Tools.com is built for penetration testers who need accurate, in-depth, and proof-based results. Unlike compliance-driven scanners, it focuses on real exploitability, using techniques inspired by manual penetration testing.
- Deep attack surface mapping – Uses browser-based crawling to uncover hidden endpoints, API routes, and injection points in SPAs, APIs, and traditional web apps.
- Out-of-band detection – Actively detects SSRF, blind SQL injection, XXE, and exfiltration-based vulnerabilities that wouldn’t be visible in direct HTTP responses.
- Automated injection testing – Executes SQLi, XSS, OS command injection, NoSQL injection, prototype pollution, and deserialization attacks, capturing payload execution proof for validation.
- Authentication-aware scanning – Supports form-based, header, cookie, and session recording authentication to identify broken access controls, session misconfigurations, and privilege escalation flaws.
- Exploit validation – Confirms vulnerabilities with HTTP request/response logs, screenshots, attack replay, and extracted sensitive data, minimizing false positives.
- Pentest-ready reporting – Generates customizable DOCX reports with CWE and OWASP mapping, detailed remediation steps, and exploitability insights - ready for clients, developers, or compliance teams.
- Integration with offensive tools – Works with SQLi Exploiter, XSS Exploiter, and provides raw HTTP requests for manual exploitation and PoC development.
This Website Vulnerability Scanner doesn’t just detect vulnerabilities - it validates, documents, and helps you act on them, making it a powerful addition to any penetration tester’s toolkit.
What is the best free web application vulnerability scanner?
The best free website security scanner is the one you can rely on and that is developed and maintained by a trustworthy company with transparent expertise and strong cybersecurity experience.
We take pride in offering 2 free scans every day for our proprietary Website Vulnerability Scanner on our cloud platform, as well as for many of our 20+ security testing tools on Pentest-Tools.com.
Compare capabilities of both the free and the paid versions to know exactly what you get after a free scan and how you could further expand and deepen your security testing work.
Ready for your next step? Try these tools
Web
Network & Cloud
Try the light version for free

















