How these vulnerabilities pushed offensive security forward

Not all vulnerabilities are alike. Some are true game-changers, uncovering new possibilities, and more layers of complexity to explore.
Let’s look at what five of the most notorious vulnerabilities from the past decade taught us - and how they shaped the infosec community.
1. Shellshock - the Bash bug (CVE-2014-6271)
I found the Shellshock vulnerability on a big college website in 2020 and helped them remediate it via Skype (remember that?). It doesn’t matter that Shellshock had been found back in 2014. Ten years later, it’s still a major threat for most organizations because of an inefficient patch management system.
Shellshock vulnerabilities remain prevalent because of the widespread use of the Bash shell, delayed awareness, or challenges in applying patches.
How Shellshock works
The vulnerability affects the Bash shell, a widely used command-line interpreter on Unix-like operating systems, including Linux and macOS. It was discovered in how Bash handled environment variables.
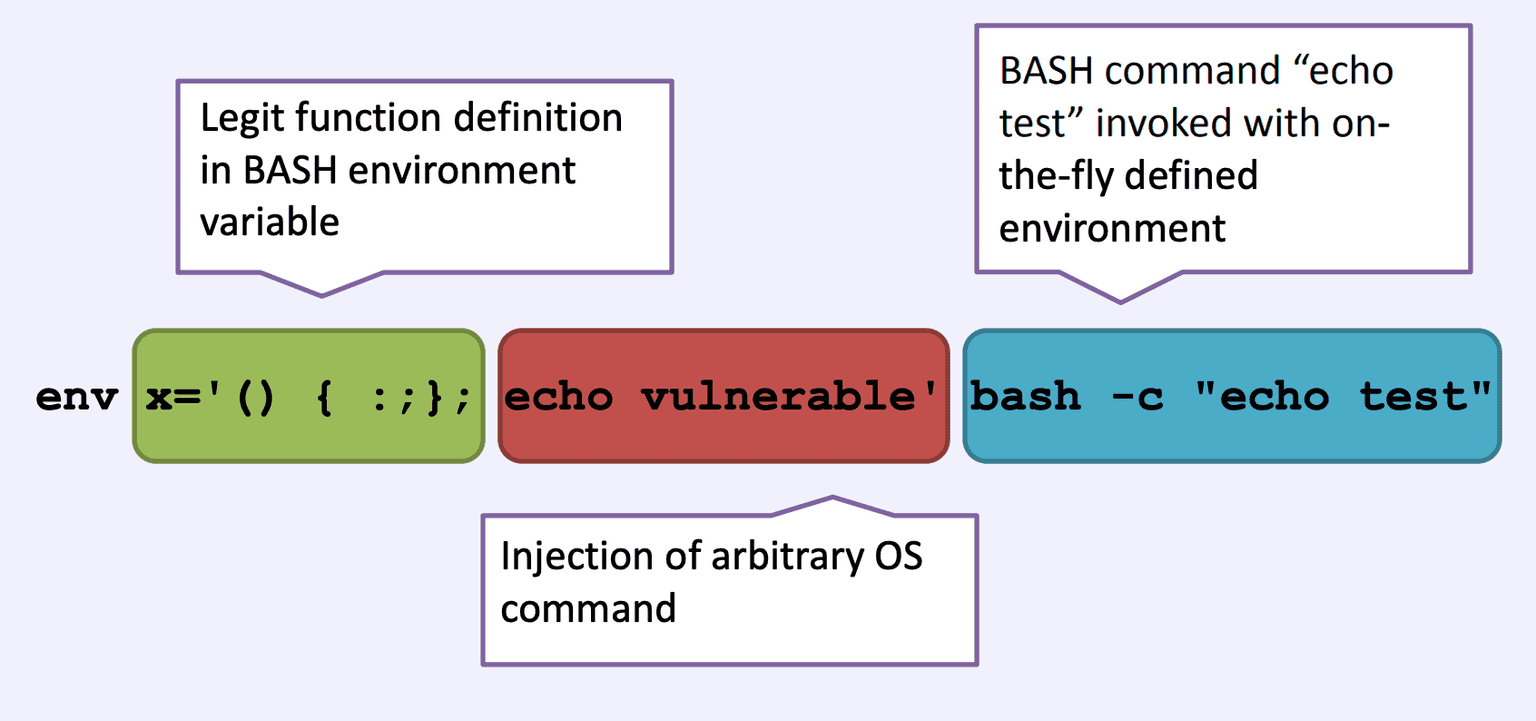
CVE-2014-6271 relies on the fact that BASH incorrectly executes trailing commands when it imports a function definition stored in an environment variable.
Bash, like many other shell environments, stores information in environment variables you can access via programs and scripts. These variables store configuration options, user preferences, and other information.
Environment variables: Bash uses environment variables to store the data you can use by running processes. These variables help programs and scripts share data.
CGI scripts and Bash functions: On web servers, Common Gateway Interface (CGI) scripts often use environment variables. When you execute these scripts, Bash processes the environment variables. Additionally, if you're writing scripts to interact with the server, ensure they are either written in Bash or can spawn GNU Bash subshells to apply the Bash functionality effectively.
Exploiting Bash functions: The vulnerability relies on how Bash handles specially crafted environment variables, specifically those related to defining Bash functions. An attacker manipulates these variables to inject malicious code.
Arbitrary code execution: By injecting malicious code into the environment variables, the attacker tricks Bash into executing unintended commands. This leads to unauthorized access, data theft, or the execution of harmful scripts.
What makes Shellshock unique?
There are two main reasons why CVE-2014-6271 stands out:
Exploitation versatility: because it’s easily exploitable, it poses a major risk to various Bash-based applications and services.
Large surface: it's been vulnerable since the 1.03 version, which was released in 1989. 25 years of vulnerable versions means a lot of unpatched servers around the world.
Which companies and systems Shellshock affected
Basically, everything that had the Bash Unix shell—IoT, servers, or anything that runs the vulnerable version (which is a lot).
How to mitigate CVE-2014-6271
The Shellshock vulnerability can be easily mitigated by updating the Bash version:
sudo apt-get update
sudo apt-get upgrade bashEasy and quick, this option will save you some headaches and also help strengthen your security posture.
Ignoring or skipping system updates is not a risk worth taking.
2. Heartbleed - the critical flaw in OpenSSL (CVE-2014-0160)
The Heartbleed vulnerability shook the cybersecurity community in 2014 when a team of independent security researchers from Google Security and Codenomicon found it. The OpenSSL cryptographic library had a bug - a nasty one!
How does HeartBleed work?
The developers of OpenSSL introduced a heartbeat function to monitor the vitality of a connection between a client and a server. This mechanism allows one party to send a small piece of data (the heartbeat) to the other and request acknowledgment to confirm the connection is still active.
Components of the Heartbeat message:
The heartbeat message includes three parts:
Request for acknowledgment: a request to the server to acknowledge the heartbeat message.
Randomly chosen message: a short, randomly chosen message (e.g., "network scanner").
Message length: the number of characters in the chosen message.

Heartbleed appears because the server trusts the input without any proper verification.
For example, a user could say that the message is longer than it actually is, and the server will respond.

The result? A memory leak results in data extraction. The extracted data may contain sensitive data, such as usernames, passwords, or encryption keys.
What makes Hearbleed unique?
Flaws in software are like passing storms, patched by updates. Yet, this one led to significant exposure of private keys and secrets online (passwords, cryptographic keys). With its widespread visibility, ease of exploitation, and stealthy attacks, this breach was no joke. Case in point, when it got out, Heartbleed impacted 17% of all SSL servers.
Understanding the real impact, large companies decided to contribute to the Core Infrastructure Initiative, a community of software developers and security engineers working together to secure open-source software.
Which companies and systems Heartbleed affected
Google, Yahoo, Dropbox, Netflix, and Facebook are some of the biggest companies impacted by Heartbleed. Imgur, OKCupid, Eventbrite, and the FBI's website were also the affected systems running vulnerable versions of OpenSSL.
This severe vulnerability also compromised the healthcare system, with malicious actors stealing the sensitive data of about 4.5 million patients of a US hospital group.
Additionally, any business using the experimental version of OpenSSL, which included code from German software developer Robin Seggelmann, was also at risk.
How to mitigate CVE-2014-0160
Update your machines to the latest version available and regularly check your certificates.
3. EternalBlue - the notorious Windows flaw (CVE-2017-0144)
The exploit, known as EternalBlue, was designed to leverage a weakness in how Microsoft implemented the Server Message Block (SMB) protocol.
The United States National Security Agency (NSA) discovered the EternalBlue vulnerability, which was also part of their secret toolkit. It became public when a hacking group, the Shadow Brokers, leaked it in 2017.
One month after Microsoft released the patch for CVE-2017-0144, the exploit played a crucial role in the propagation of the WannaCry ransomware outbreak.
How does EternalBlue work?
As I said, EternalBlue is in the SMBv1 protocol, particularly in the way it handles specific requests. An attacker sends a malicious request to the server that exploits a buffer overflow in the server’s handling packet. After executing the buffer overflow, the attacker injects arbitrary code into the system and executes it.
CVE-2017-0144 effectively gives the attacker a powerful tool for creating a self-propagating worm. The malware doesn’t require any user intervention. It automatically and quickly propagates from one machine to another, exploiting the same vulnerability and leaving compromised systems behind.
EternalBlue was more than an exploit, it was the driving force behind WannaCry's widespread file encryption. Panic broke out, holding organizations hostage - a clear illustration of the massive impact this attack had in the real world.
What makes EternalBlue unique?
The capability to propagate through a network is what makes EternalBlue uncommon. If an endpoint is compromised, the threat actors use the exploit to infect additional vulnerable Windows systems on the same network.
More than an exploit, WannaCry’s enabler quickly encrypted files worldwide. Organizations became so overwhelmed that it fueled widespread panic - a stark testament to the real-world impact of this extensive cyberattack.
WannaCry is known as the biggest ransomware attack in the history of the Internet. Ransomware is commonly crafted for specific targets, but not this one. This successfully exploited a vulnerability in the SMB protocol, resulting in widespread global impact.
Which companies and systems EternalBlue affected
Eternalblue’s impact extended beyond Microsoft products to any system using the SMBv1 server protocol, including devices like Siemens ultrasound medical equipment.
Here are some figures to understand its huge impact:
In 2017, there were 4332 servers and operating systems exposed on the Internet with Eternalblue.
Merck, FedEx TNT Express, Maersk, and Mondelez were among the largest companies impacted by CVE-2017-0144, losing millions of dollars.
The staggering cost of EternalBlue was estimated at $1 billion.
The affected systems included:
Windows 7
Windows 8, 8.1
Windows 10
Windows Server 2003, 2003 R2, 2012, 2016
Windows 95
Windows 98
Windows 2000
Windows XP, Vista, NT
How to mitigate CVE-2017-0144
If you still have vulnerable machines to EternalBlue, update any older versions of Windows and apply the MS17-10 security patch.
4. Meltdown - the Intel CPU vulnerability (CVE-2017-5754)
Meltdown is a type of hardware-based vulnerability that affects Intel microprocessors. At the beginning of 2018, two founding members of Cyberus Technology GmbH were among the first experts to discover the Meltdown vulnerability.
Even after its disclosure, security researchers continued to study Meltdown and various ways of exploitation. CVE-2017-5754 allows attackers to retrieve private data (e.g. credentials) from vulnerable systems. This capability makes it easier to pivot through the network.
How does Meltdown work?
Shortly said: You can exploit the speculative execution of x86 processors to read arbitrary kernel-memory.
CVE-2017-5754 leverages a race condition that exists between memory access and privilege level checking during instruction execution.
Meltdown attacks operate by exploiting a flaw in how modern microprocessors handle “speculative execution”. This technique makes modern computer systems faster and more efficient.
Here’s a modern CPU execution engine:
Even if an attacker lacks the necessary rights or privileges to access the data, they can still access and read sensitive information kept in the processor's memory thanks to a design fault.
What makes Meltdown unique?
Meltdown is a hardware-based vulnerability that impacts the core architecture and design of modern microprocessors. It is challenging to patch or solve only through software updates. Instead, a mix of hardware and software-based solutions is essential.
Which companies and systems Meltdown affected
Meltdown is a pervasive vulnerability that impacts desktop, laptop, and cloud systems. It specifically targets Intel processors that use out-of-order execution, which exists in almost all Intel CPUs since 1995, except for Intel Itanium and Intel Atom before 2013.
Tests confirmed Meltdown's presence in Intel CPU versions dating back to 2011. Its impact on AMD processors remains unknown, while ARM acknowledges that some of their CPUs are vulnerable.
How to mitigate CVE-2017-5754
Keep your systems safe and apply the latest security patches available.
Follow the best security practices for hardware and software security, including enabling mitigations and virtualization-based features.
Avoid running untrusted code on vulnerable devices.
Last but not least, be ready for potential Meltdown attacks. Report any unusual activity or behavior to the relevant device maker or operating system vendor for a thorough investigation.
5. Zerologon - the critical Active Directory vuln (CVE-2020-1472)
Zerologon, officially known as CVE-2020-1472, was discovered by Secura researchers and fixed by Microsoft on August 11, 2020.
The vulnerability occurs in the Netlogon protocol, specifically in the authentication process, where the cryptographic function compromises the security of the Active Directory, resulting in a critical CVSSv3 10.
If exploited, an attacker can gain unauthorized access to Windows domain controllers by impersonating any computer, including the root domain controller.
How does Zerologon work?
The Netlogon Remote Protocol is an essential component of how Windows domain controllers authenticate users and computers across a network. It uses a unique kind of encryption to maintain security when doing specific actions such as logging in users and updating passwords across networks.
What differentiates the Netlogon protocol from others is its unique method of certifying that both parties (such as a user and a server) know a secret key that uses a bespoke protocol.
However, one fundamental issue in the Netlogon protocol is the way it generates credential values using a specific encryption algorithm known as AES-CFB8. This method, called ComputeNetlogonCredential, takes a small piece of information (8 bytes) and uses a secret key to convert it into another item of data with the same
length. Without the secret key, an attacker cannot determine or estimate the proper answer, demonstrating they do not have the key.
This function uses an AES encryption mode (AES-CFB8), which is less used than others. It operates by encrypting each byte of the original data with a particular starting value known as an Initialization Vector (IV).
Secure researchers have documented more technical details in their whitepaper.
What makes Zerologon unique?
CVE-2020-1472 can orchestrate an attack against the Microsoft Active Directory Domain Controller, allowing malicious actors to manipulate it and manage the environment with administrator privileges.
Which companies and systems Zerologon affected
Cybercriminals targeted many organizations and companies worldwide with improper Netlogon configurations. They impacted the election support systems, UK organizations, and so on.
The affected systems were:
Windows Server version 2004
Windows Server version 1909
Windows Server version 1903
Windows Server 2019
Windows Server 2016
Windows Server 2012 R2
Windows Server 2012
Windows Server 2008 R2
Windows Server 2008
Windows Server 2003 R2
Windows Server 2003
How to mitigate CVE-2020-1472
Mitigation includes:
Installing available updates on all DCs and RODCs
Monitoring new events
And addressing non-compliant devices that use vulnerable Netlogon secure channel connections.
How these 5 vulnerabilities shaped the infosec community
Shellshock, Heartbleed, Eternalblue, Meltdown, and Zerologon remind us how fragile systems and infrastructures still are and what business impact they can have.
Sharing details about a large-scale privacy investigation, Inti de Ceukelaire stated:
What is deemed to be secure today, may be considered easily hackable tomorrow.
That’s why learning from experience, but also cultivating our awareness of the tech environment in which we operate, are essential conditions to make a meaningful contribution to security - no matter your role.
Remember that security technologist Bruce Schneier called the Heartbleed story “a catastrophic bug”.
Basically, an attacker can grab 64K of memory from a server. The attack leaves no trace and can be done multiple times to grab a different random 64K of memory.
This means that anything in memory—SSL private keys, user keys, anything—is vulnerable. And you have to assume that it is all compromised. All of it.
Catastrophic” is the right word. On a scale of 1 to 10, this is an 11.
If you think it’s an exaggeration, there’s more data. The Pew Research Center’s findings on Heartbleed impact highlighted that 29% of Internet users think Heartbleed exposed their personal data, while 6% of them believe they’ve been stolen.
Shellshock also caused global panic - and rightfully so. In the first four days of its disclosure, the Incapsula web application firewall discovered 217,089+ exploit attempts on over 4,115 domains.
With Bash so deeply ingrained in organizations’ systems for over 20 years, the extent of the Shellshock bug could be huge.
said FireEye security experts at that time.
EternalBlue, the biggest Windows exploit ever, "is by far the most powerful cache of exploits ever released," as security expert Matthew Hickey told ArsTechnica. Because of EternalBlue and automatic propagation, the WannaCry attack had epic proportions: 300,000+ computers compromised across 150 countries and billions of dollars worth of damages.
Meltdown was so trivial to exploit – hadn’t it been patched, we would have seen real-world attacks”, added Daniel Gruss, a security researcher and part of the team that disclosed this vulnerability. He also prescribed a biological approach to computing systems because “they have exceeded the complexity of something that we can study another way.
As for Zerologon,
this is what we see as a trend with a lot of attackers, a ubiquitous protocol like Netlogon … attackers love those because they are looking for a vulnerability that will get them bang for buck
Tenable researcher Claire Tills explained. But the bigger issue with Zerologon was its chaining capabilities.
Seeing these five notorious vulnerabilities in action, we can’t help but ask:
What more can we do, as offensive security specialists, to help organizations get the best results for their limited resources?
That’s for each of us to reflect on and answer through our actions.