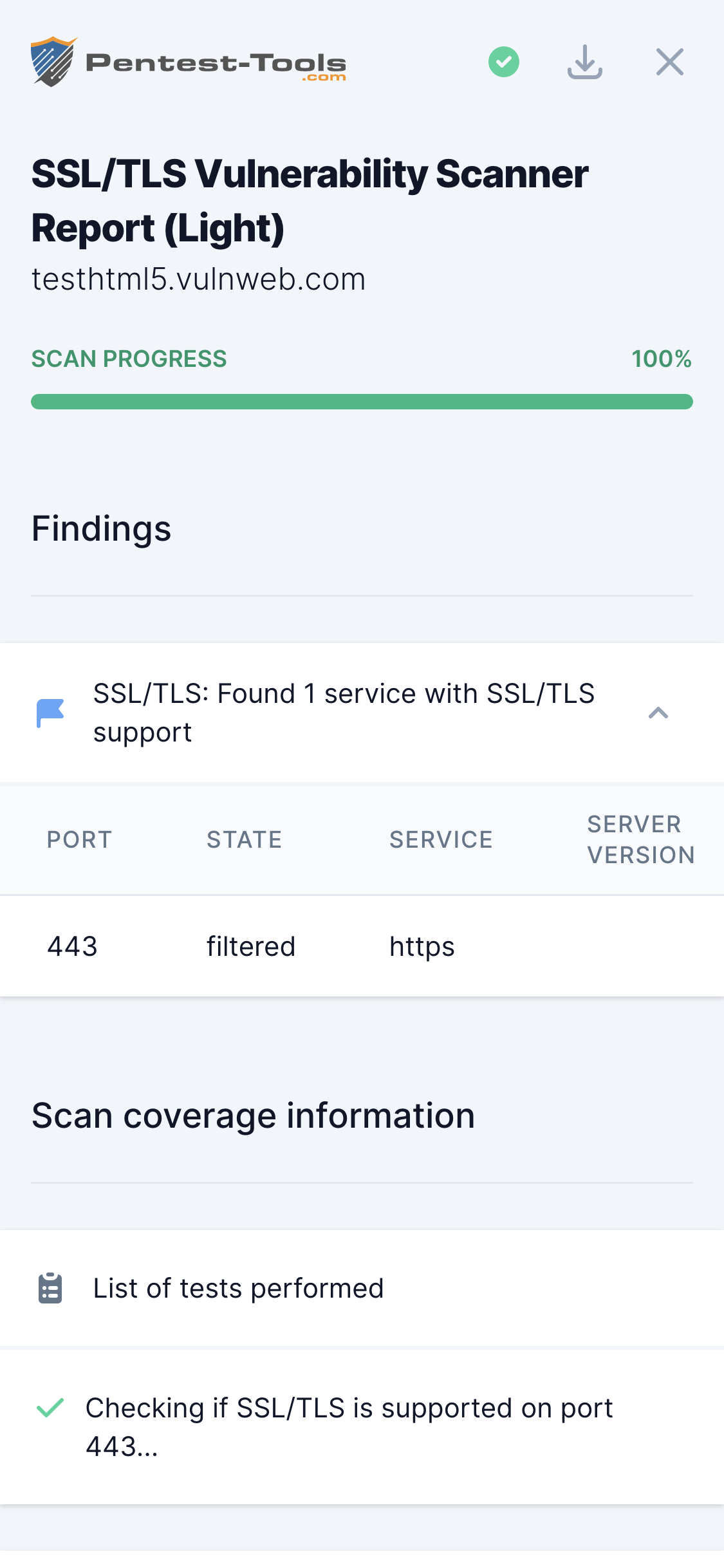
SSL/TLS Scanner
Technical details
Transport Layer Security (TLS) and (now deprecated) Secure Sockets Layer (SSL) are cryptographic protocols meant to secure communication between computer systems. They are used to provide an encrypted communication channel over which other clear-text protocols (HTTP, SMTP, POP3, FTP, etc.) can be securely used to transmit application-specific data.
However, since the introduction of SSLv2.0 in 1995 and the continuation to SSL v3.0, TLS 1.0, TLS 2.0, and the current TLS 3.0, multiple weaknesses have been discovered in these protocols, making them vulnerable to cryptographic attacks that can allow attackers to decrypt the communication and gain access to sensitive data.
The SSL/TLS Vulnerability Scanner performs a security assessment of the configuration of the target SSL/TLS service to provide a list of weaknesses and vulnerabilities packed with detailed recommendations for remediation.
The list of vulnerabilities detected by this scanner includes:
- Heartbleed
- Ticketbleed
- CCS Injection
- POODLE
- ROBOT
- DROWN
- Secure Renegotiation (server-side)
- Secure Renegotiation (client-side)
- CRIME
- BREACH
- FREAK
- SWEET32
- BEAST
- LOGJAM
Parameters
| Parameter | Description |
|---|---|
| Target host | The hostname or IP address of the SSL/TLS server to be scanned. |
| Target port(s) | The SSL/TLS port to connect to. Multiple ports can be specified at once (comma separated) like 443, 21, 25, 110. |
| Auto detect SSL/TLS | When this option is enabled, the tool automatically scans the target host for the top 100 most common TCP and UDP ports, identifying the ones that have SSL/TLS support. |
How it works
The SSL Scanner uses a scanning engine based on the testssl.sh tool, together with multiple tweaks, adjustments, and improvements.
The scanner starts by connecting to the target SSL server and trying various ciphers and SSL/TLS protocol versions to discover existing vulnerabilities.
All discovered issues are further interpreted by our scanner and integrated into a human-readable report.