New modules, methods & payload - April updates

It’s been a busy month for us and we’re excited to share what we worked on!
These 4 platform improvements focus on making your workflow easier, so you save time and effort for the essential tasks:
1. Detection module for the new Website Scanner: Sensitive Data Crawl
2. NEW: 3 detection modules we built for high-risk vulns
3. Use a sequence of numbers as payload with the URL Fuzzer
4. The URL Fuzzer now supports the POST method
Let’s unpack them!
1. New detection module for the Website Vulnerability Scanner
We’ve added a detection module to our new Website Vulnerability Scanner (currently in beta), which searches for sensitive information such as email addresses, social security numbers, and credit card numbers in your web applications.
To use it, go to Website Scanner, add your URL target, and select Full Scan.
Expand the Attack options, choose the Passive checks tab and make sure to enable Sensitive Data Crawl. Our scanner engine will analyze the HTTP responses from your target and look for personally identifiable information (PII).
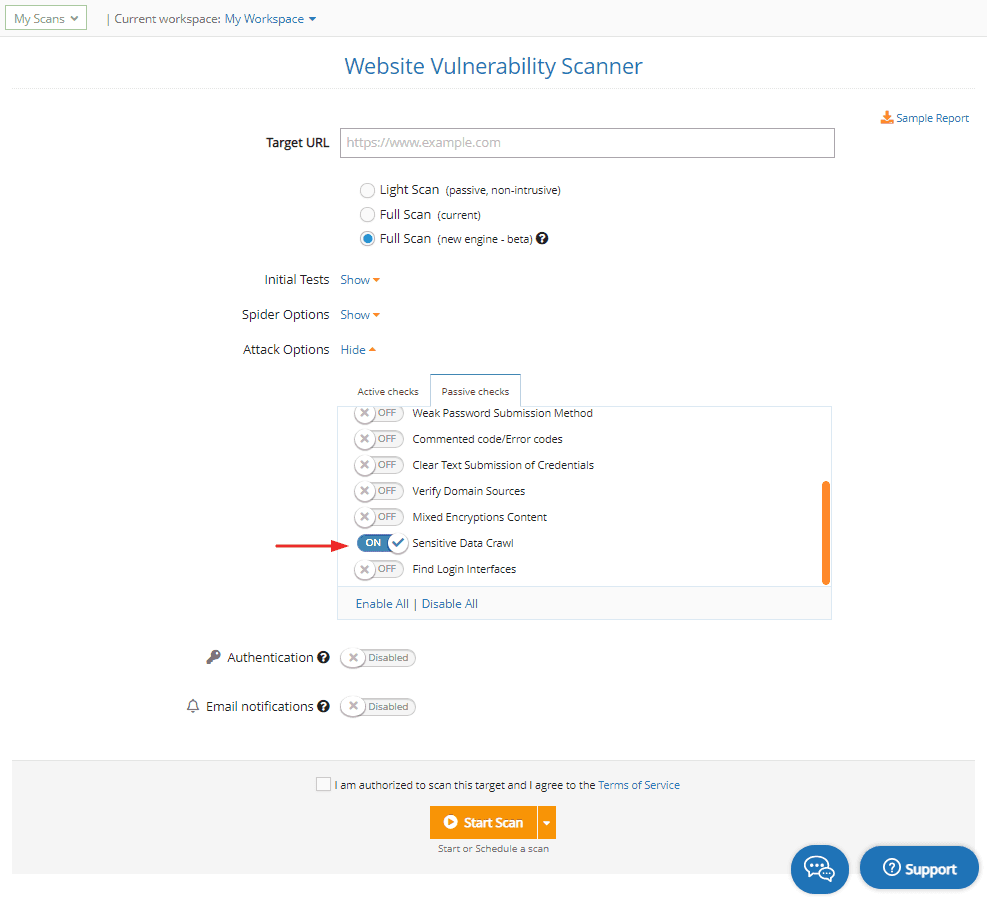
Run a Sensitive Data Crawl
2. Three new custom modules we built from scratch
We’ve added 3 custom detection modules to help you identify specific, high-risk vulnerabilities. Here’s what they do:
detect malicious web shells deployed by the Hafnium cybercriminals group on the compromised Microsoft Exchange Servers used in the ProxyLogon attacks
find potentially vulnerable F5 BIG-IP devices impacted by the unauthenticated RCE vulnerability (CVE-2021-22986)
check for systems exposed to VMware vCenter RCE (CVE-2021-21972).
Need to see if your environment is affected by one of these specific vulnerabilities?
Choose the Full Scan option from the Network Vulnerability Scanner with OpenVAS and see them in your Findings.
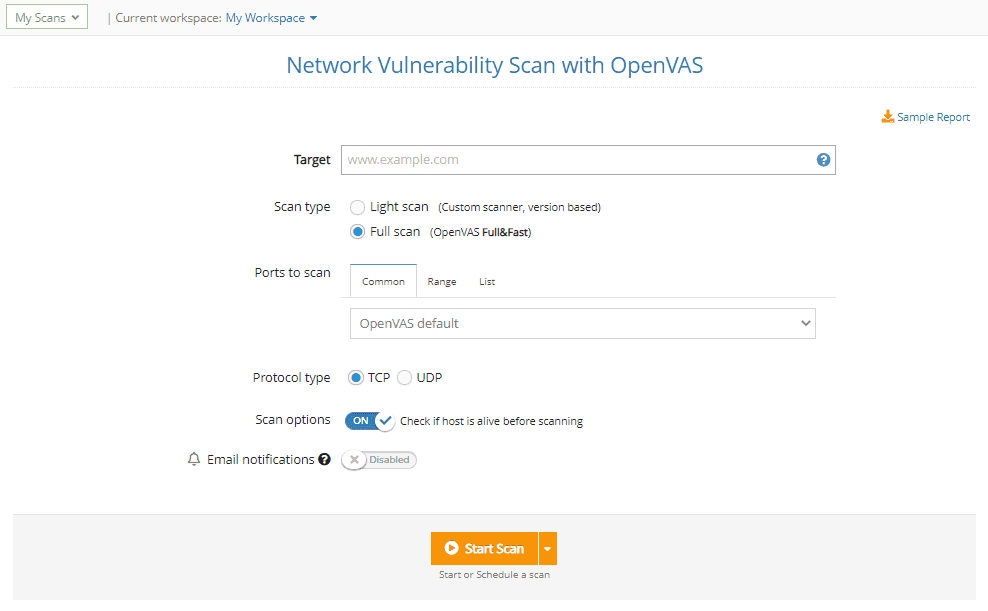
Check for critical vulns
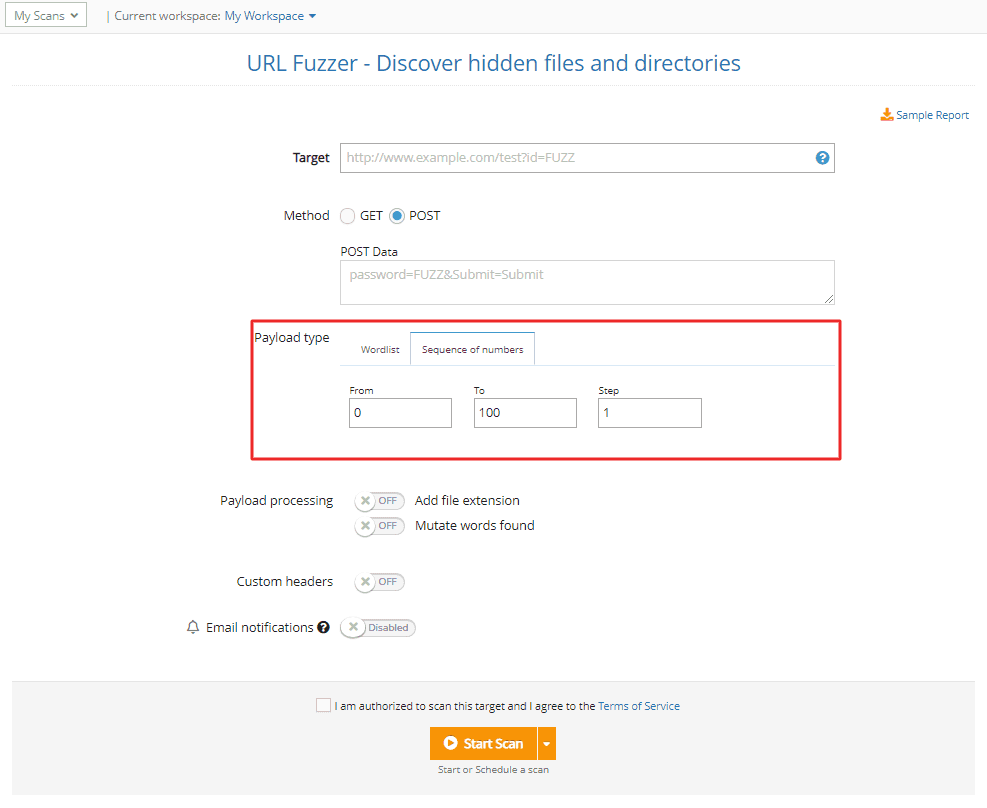
3. Use a sequence of numbers as payload with the URL Fuzzer
In addition to default and custom wordlists, you now have the option to use a sequence of numbers as payload with the URL Fuzzer.
To enable it, go to the Payload type, select Sequence of numbers, and fill in the numbers for the sequence you need to run specific security testing assessments.
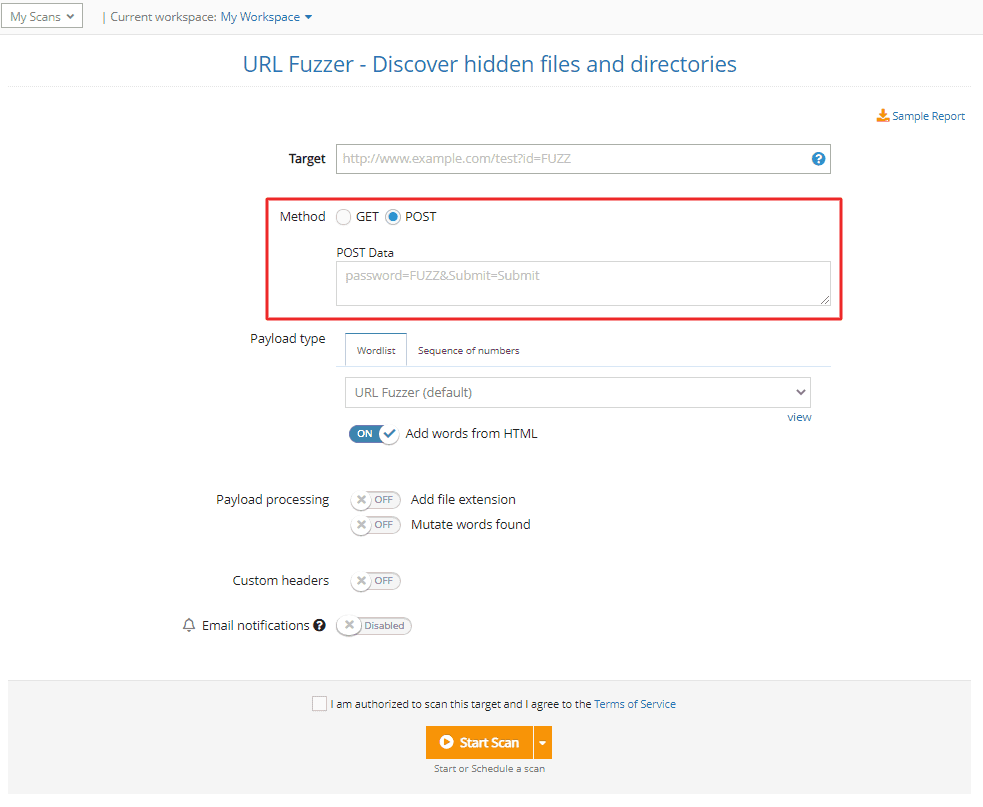
4. The URL Fuzzer now supports the POST method
Another improvement we’ve added to the URL Fuzzer is the option to use the POST method, one of the most common HTTP methods.
To do that, go to URL Fuzzer, select the POST option and add the data you want to send with every HTTP request using the “FUZZ” maker.