The most exploited vulnerabilities in 2022

Offensive security is a fast-moving space, yet some security vulnerabilities persist for years, causing problem after problem. 2023 being no exception, you can spare yourself from repetitive work by learning to find and mitigate these top 10 CVEs.
These common vulnerabilities pose a significant risk to businesses and individuals alike, making them prime targets for cybercrime.
To give you the ethical hacker's perspective on the cybersecurity landscape, we're sharing the top 10 most exploited vulnerabilities of 2022. This list includes CVEs which offensive security pros most often proved to be a real risk to businesses and their customers.
While many of them are also listed in the Known Exploited Vulnerabilities Catalog maintained by the US Cybersecurity & Infrastructure Security Agency (CISA), this top 10 serves as a valuable filter to help you stay ahead of the game. Focusing on these high-risk, high-impact CVEs allows you to provide actionable reports and mitigation steps to your clients, dramatically reducing their risk.
10. CVE-2021-34473 (ProxyShell)
ProxyShell is an attack chain that exploits three known vulnerabilities in Microsoft Exchange servers: CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207. These vulnerabilities allow for remote code execution, making them critical.
Unlike other RCE vulnerabilities, ProxyShell is relatively easy to exploit, which has led to its widespread use among attackers. Security researchers first discussed the exploit at the 2021 Black Hat USA conference, leading to an initial wave of attacks against Exchange servers.
According to Unit 42 analysis by Palo Alto, ProxyShell was used 55% of the time out of the 6 CVEs which were most exploited for Initial Access.
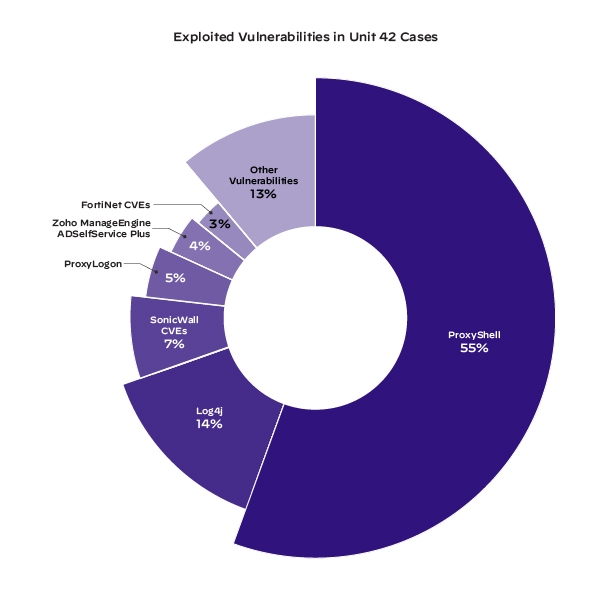
Source: ProxyShell: Deep Dive into the Exchange Vulnerabilities
Since then, security researchers have seen attackers use the exploit to create web shells and plant ransomware such as LockFile, Babuk, and Squirrelwaffle. Many organizations suffered from these attacks, including building manufacturers, seafood processors, industrial machinery companies, auto repair shops, and small airports.
To protect against ProxyShell vulnerabilities, organizations need to patch their on-premises Microsoft Exchange servers, perform a comprehensive malware scan, and run a deep network security scan to determine if their servers have already been compromised.
9. CVE-2021-44228 (Log4j or Log4Shell)
Log4Shell is a vulnerability in Apache Log4j2 that gained a lot of popularity in 2022. It is a Java-based logging utility that is related to the JNDI (Java Naming and Directory Interface) feature used in configuration, log messages, and parameters, which do not protect against attacker-controlled LDAP and other JNDI-related endpoints.
This means that an attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.
As the keeper of highly valuable sensitive data, the financial industry has suffered the most attacks using this CVE as the main vector.

Source: Log4Shell log4j Remote Code Execution – The COVID of the Internet
To fix the issue, upgrade to version 2.15.0 or later and apply the configuration setting log4j2.formatMsgNoLookups = true or disable Log4j and JNDI lookups.
Additional mitigation steps include a web application firewall (WAF), upgrading JDK, and disabling remote code bases.
This helpful infographic from the Swiss Government’s Computer Emergency Response Team (CERT) helps visualize how the vulnerability works and possible preventive measures.

8. CVE-2018-13379
The CVE-2018-13379 vulnerability is a security weakness in Fortinet FortiOS versions 5.4.12 to 5.6, 5.6.3 to 5.6.7, and 6.0.0 to 6.0.4, and FortiOS devices that use FortiProxy versions 1.0.0 to 1.0.7, 1.10 to 1.1.6, 1.2.0 to 1.2.8, and 2.0.0 under the SSL-VPN service.
This security weakness allows threat actors to download FortiOS system files using malformed resource requests, which enables them to read session files that include plaintext credentials.
The CVE is easy to exploit and bad actors have used it as an entry point for privilege escalation and deeper, organization-wide attacks.
Kaspersky's ICS-CERT conducted an incident investigation and published a report on the Cring attack. The investigation revealed that the root cause of the breach was linked to insecure firmware versions on the FortiGate VPN server, with CVE-2018-13379 serving as the entry point for the attacker to gain access to the enterprise network. The attack culminated in the deployment of Cring ransomware.

Source: Vulnerability in FortiGate VPN servers is exploited in Cring ransomware attacks
To prevent attacks targeting FortiOS systems, organizations need to update to the latest version of FortiOS, limit the number of users with administrative access, restrict access to the SSL-VPN portal, and monitor the system for suspicious activity.
Additionally, organizations should use security tools to detect and block malformed resource requests to avoid data breaches.
7. CVE-2020-14179
CVE-2020-14179 is an Information Disclosure vulnerability in Atlassian Jira Server and Data Center that allows remote, unauthenticated attackers to view custom field names and custom SLA names through the /secure/QueryComponent!Default.jspa endpoint.
The affected versions are before version 8.5.8 and from version 8.6.0 before 8.11.1. The CVSS score of this vulnerability is rated as 5.0. Remediation consists of upgrading your Jira instance to the latest version will remove the threat.
Here is a simple PoC we found helpful.
6. CVE-2021-26086
An investigation into the /WEB-INF/web.xml endpoint of Atlassian Jira Server and Data Center uncovered a path traversal vulnerability that allows remote attackers to read certain files.
Atlassian Jira is a widely used ticketing tool that organizations from around the world rely on. The affected versions of Jira Server and Data Center are:
All versions below 8.5.14
Versions 8.6.0 to 8.13.6
Versions 8.14.0 to 8.16.1.
This CVE is classified as a directory traversal vulnerability and has a CVSS Score of 5.3. Although it enables partial information disclosure, it does not negatively impact the integrity or availability of the system. A bad actor can exploit it without the need for authentication, but this does not grant the attacker access.
Threat actors exploiting this vulnerability poison server logs and achieve remote code execution or steal sensitive files and information.
To mitigate this CVE, users need to update their Jira Server and Data Center to version 8.5.14 or later, 8.13.6 or later, and 8.16.1 or later respectively.
5. CVE-2019-8442
An attacker can exploit an Information Disclosure vulnerability in Atlassian Jira by sending a specific request to the target server, because of insufficient validation of user input.
The affected endpoints are:
/META-INF/maven/com.atlassian.jira/atlassian-jira-webapp/pom.xml/META-INF/maven/com.atlassian.jira/jira-webapp-dist/pom.xml/META-INF/maven/com.atlassian.jira/atlassian-jira-webapp/pom.propertiesThe vulnerable versions of Jira are 7.13.4, 8.0.0 to 8.0.4, and 8.1.0 to 8.1.1. To prevent this, update to the latest patch or upgrade from Atlassian.
The impact is quite high since the vulnerability leads to information disclosure. When including this CVE in your penetration testing reports, it’s helpful to demonstrate how remote attackers can exfiltrate sensitive information from vulnerable systems.
4. CVE-2018-2894
This security issue enables unauthorized access to the path (/ws_utc/config.do) on port 7001, which can only be accessed in development mode. To exploit the vulnerability, the attacker must first establish a writable Work Home Dir and then upload a Java Server Page (JSP) file through the security tab.
Executing the uploaded JSP file can result in complete server compromise.
To prevent exploitation, security teams need to verify that the WebLogic server is not operating in development mode and that port 7001 is blocked.
Malicious hackers can leverage this CVE remotely, without authentication, which makes it particularly dangerous and urgent to address.
Here's a quick PoC with a good explanation that shows how easily this vulnerability can wreak havoc on the victim’s infrastructure.
The vulnerability affects Oracle WebLogic Server versions 10.3.6.0, 12.1.3.0, 12.2.1.2, 12.2.1.3, and 12.2.1.4. Oracle has released a patch to address this, which is highly recommended, and there’s also the option to upgrade the version to protect exposed systems.
3. CVE-2020-1938 (GhostCat)
CVE-2020-1938 is a vulnerability that affects Apache Tomcat, an open-source Java Servlet Container. It’s a result of a flaw in the way the Apache Tomcat server handles HTTP requests that contain multiple Content-Length headers.
This CVE allows a remote, unauthenticated attacker to perform a denial of service (DoS) attack or potentially execute arbitrary code on a vulnerable system. It’s worth mentioning that reaching RCE is very hard and requires using non-default configurations.
A bad actor can exploit this vulnerability by sending a specially crafted HTTP request to a vulnerable Apache Tomcat server. The request would include multiple Content-Length headers, which would cause the server to crash or become unresponsive.
The CVE affects Apache Tomcat versions 9.0.0.M1 to 9.0.31, 8.5.0 to 8.5.51, and, 7.0.0 to 7.0.100. Mitigation includes upgrading to a version of Apache Tomcat that addresses this issue or applying the appropriate patch to protect exposed systems.
You can learn how to manually exploit this vulnerability on tryhackme.
2. CVE-2022-24086
CVE-2022-24086 is a remote code execution vulnerability in Adobe Commerce and Magento Open Source because of inadequate input validation.
Bad actors can exploit this vulnerability without authentication. As it is pre-authenticated, this CVE allows attackers to bypass protections by running scans for web vulnerabilities. Successful exploitation can result in the complete compromise of the targeted system.
This vulnerability affects all platforms running Magento Open Source 2.4.3-p1, 2.4.3-p2, and earlier versions (2.3.7-p2 and earlier versions), as well as Adobe Commerce 2.4.3-p1, 2.4.3-p2 and earlier versions (2.3.7-p2 and earlier versions).
Adobe has released patches to address this CVE, which has a severity rating of 9.8 out of 10, and advises customers to update their installations to the latest version.
Here’s a short demo showing you how to detect this vulnerability with Sniper Auto-Exploiter:

1. CVE-2020-3452
CVE-2020-3452 is a read-only path traversal vulnerability that affects Cisco ASA and FTD software. Sending a specifically crafted HTTP request to a vulnerable system allows a remote, unauthenticated attacker to take advantage of this security issue.
If they successfully exploit the vulnerability, an attacker can only access arbitrary files from the web services file system, which may also contain data like WebVPN configuration, bookmarks, web cookies, partial web content, and HTTP URLs.
According to Cisco, an intruder can only access these files if WebVPN or AnyConnect are set up on the system. To understand why this vulnerability received a 7.5 CVSSv3 score, it’s crucial to remember that an attacker could not read files from the ASA, FTD, or underlying operating system. This restricts the impact of the vulnerability.
Prediction for the future
We’ll most likely continue to see a rise in cyber threat activity targeting vulnerabilities in web applications and cloud environments, since these CVEs will probably remain exploitable for years to come.
The increasing use of IoT devices in both personal and professional settings may also lead to an increase in attacks targeting security holes in them. Statistics show that IoT grows each year, breaking adoption rate records from the previous 12 months:
There are well over 7 billion connected IoT devices around the globe
IoT devices surpassed non-IoT devices in 2020
It’s expected there will be 25.4 billion IoT devices by 2030
There are more than 400 active IoT platforms in existence.
Keeping up with all the latest high-risk vulnerabilities is a huge challenge for any organization, but it’s also the only way to improve their reaction and risk mitigation capabilities.
It’s also worth noting that ethical hackers (penetration testers, bug bounty hunters, etc.) play a major role in securing the internet by using the Pareto principle: helping blue teams prioritize the 20% security issues which account for 80% of the risk and business impact.
Monitoring and prioritizing assets, investing in threat intelligence, vulnerability management, and incident response plans make a powerful – and necessary – combination for organizations whose businesses depend on keeping operations and teams safe. Ethical hackers have never played such an important part of this as they do now.
Wrapping Up
It’s no surprise that vulnerabilities in web apps and misconfigurations in cloud environments were among the top exploited vulnerabilities in 2022. That’s why the same key advice remains relevant: regularly updating software, patching critical vulnerabilities, and properly configuring cloud environments.
Stay up-to-date with new cybersecurity issues and hot topics by:
Subscribing to security mailing lists and newsletters for timely updates on newly discovered vulnerabilities and threats
Joining cybersecurity communities for access to information and resources from other professionals, including their first-hand experience
Following security researchers and organizations on social media for updates on new vulnerabilities
Checking out our exploit database and staying up to date with new CVEs.










