How to detect sensitive data exposure with Pentest-Tools.com

- Article tags
The best security specialists have a very strong grasp of fundamental vulnerabilities, the kind that pops up in every engagement.
When it comes to web apps, that means keeping an eye on the OWASP Top 10 and knowing how to look for and report the types of vulns in it for maximum effect.
To make this easier, we’re dedicating an entire series to how you can detect OWASP Top 10 vulnerabilities with Pentest-Tools.com.
We’ve refined this workflow and now we’re sharing it to make your life as a pentester easier and your work more enjoyable.
Enough chit-chat – let’s get into the details about the types of issues associated with Sensitive Data Exposure.
What is Sensitive Data Exposure?
This category of security vulnerabilities occurs when an application exposes sensitive data which includes any information that is supposed to be protected from unnecessary access.
For example, it can include personal data, customer information, configuration files with database credentials inside, internal team notes, and so on.
Data Breach versus Sensitive Data Exposure
Before moving on, let’s clear up the terms.
The difference between these is similar to the one between a garage with a lock on the entrance and one without.
A data breach is the consequence of weak and vulnerable protection mechanisms where an attacker has to break the “lock.”
Sensitive data exposure happens when there are no protection mechanisms, so the attacker doesn’t have to break anything because there’s no “lock” to begin with.
It’s just as bad as it sounds.
The root cause for Sensitive Data Exposure issues
The main reason this web application risk happens is the app gets misconfigured while setting up authorization control. We get into the details below.
How is Sensitive Data Exposure different from other OWASP issues?
Vulnerabilities in this category mainly occur because of human error. Lack of security awareness or carelessness leads to misconfigurations – which are still one of the top causes of security issues in software worldwide.
Why is Sensitive Data Exposure so pervasive?
For two reasons:
because there are so many people involved in developing software and
because still too few of them have a strong understanding of fundamental security practices.
As a consequence, misconfigurations slip into much of the software we use.
As you’d expect, attackers love this because you need very low-level technical skills to exploit this vulnerability.
Most web applications today are vulnerable to this security flaw and the attack almost always goes undetected – unless the information is later disclosed through the dark web or cracking forums.
Types of data most vulnerable to Sensitive Data Exposure
As it happens, two types of data are the most prone to this security issue:
Data in Transit
Data that is usually inside the network is often on the move, flowing across your servers, applications, and users. It’s highly vulnerable while traveling across your network as it moves through unprotected data channels or Application Programming Interfaces (APIs) which allows the applications to communicate with each other.
You can launch attacks like man-in-the-middle (MiTM) to intercept this data and monitor clear text communications to find and harvest sensitive information from it.
Another communication security issue tied to protocols is not using cryptographic techniques like SSL (Secure Socket Layer) and TLS (Transport Layer Security) to encrypt data in motion. If you place yourself between the client and your target server, the unencrypted data will be exposed, including the credentials the client used to authenticate against the server.
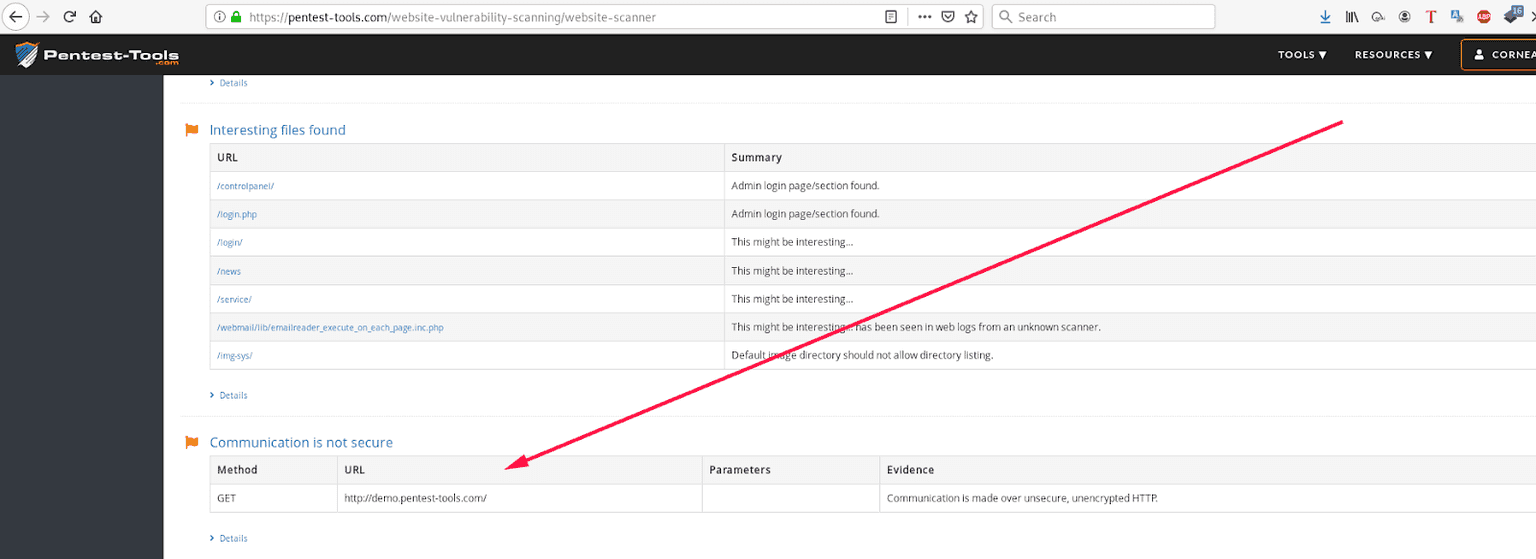
How to detect sensitive data exposure issues around data in transit with Pentest-Tools.com
Here’s what we recommend as a workflow to test this particular category of vulnerabilities. One of our tools is even part of NSA’s list of resources to eliminate obsolete TLS/SSL config issues and vulns!

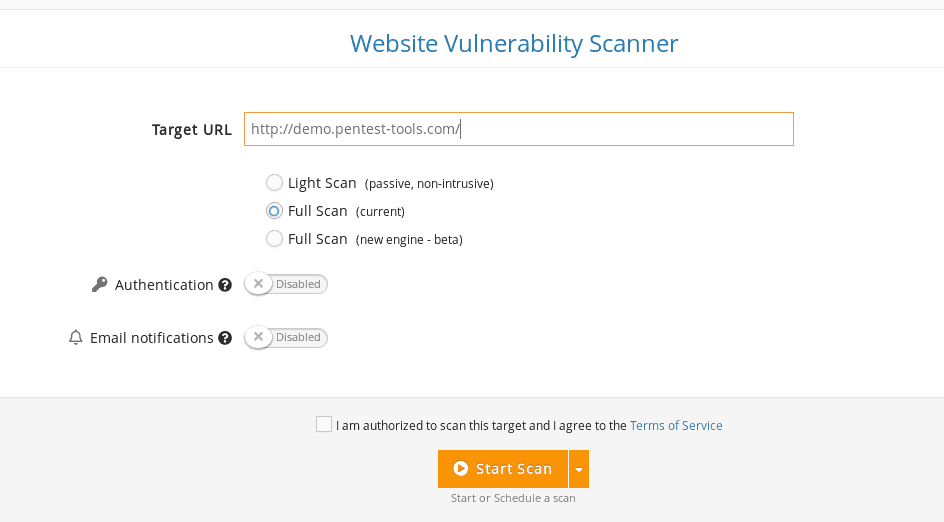
1. Log into your Pentest-Tools.com account.
2. Under Tools and the Web Application Testing menu, select Website Scanner.

Data at Rest
Data at Rest refers to data stored or saved in a system:
File Servers and Network Shares
Document Management Systems
External Physical Storage
Databases
Endpoints: laptops, PCs, tablets
Mobile Devices
Cloud.
It is considered less vulnerable as it doesn’t have the risks related to moving across systems. Security misconfigurations are the main reason data at rest gets exposed.
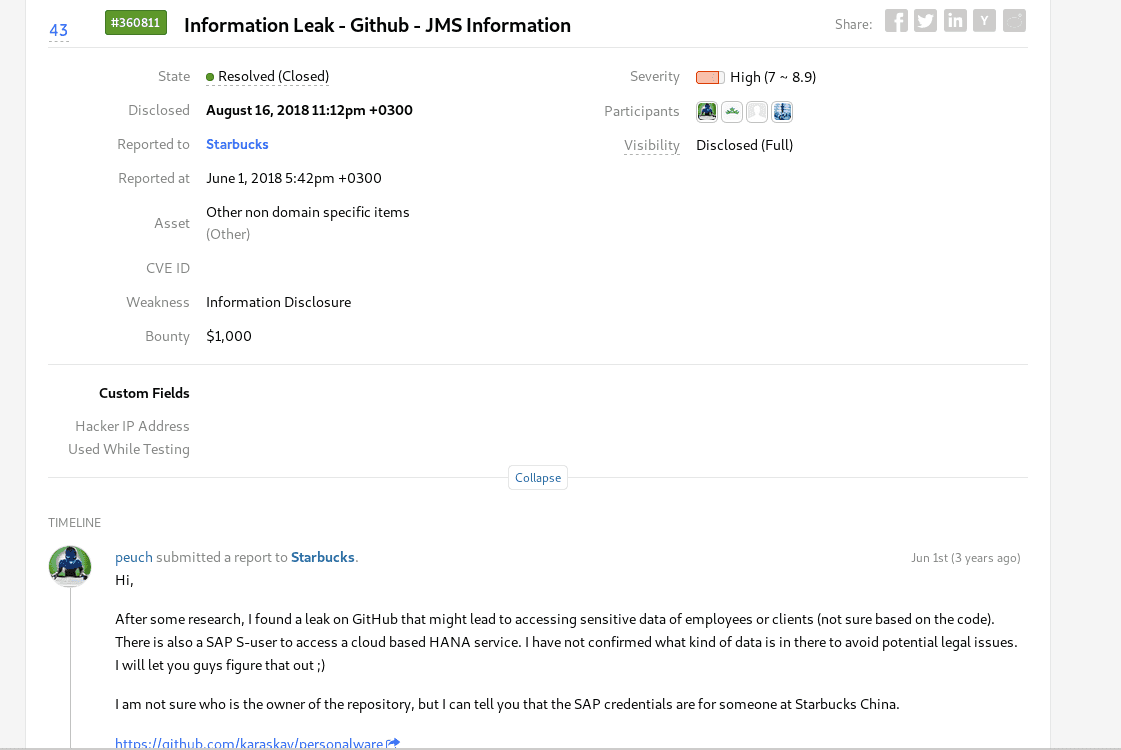
For example, developers create awesome platforms, products, and applications, but sometimes they expose private keys and secret tokens through their GitHub/GitLab repositories.
Here’s an example of a disclosed vulnerability report:
Another big issue happens when web administrators create backups of their website unprotected by a strong password, which anyone can access through the browser. Once they retrieve the backup, all the source code is disclosed.
And what does the source code include in 99% of situations? A config file.
What does a config file include? Exactly! A database connection string that also includes the login credentials.
How to identify Sensitive Data Exposure Issues on Data at Rest with Pentest-Tools.com
1. Log in to your Pentest-Tools.com account.
2. Under Tools, look for the Web Application Testing menu and select URL Fuzzer.

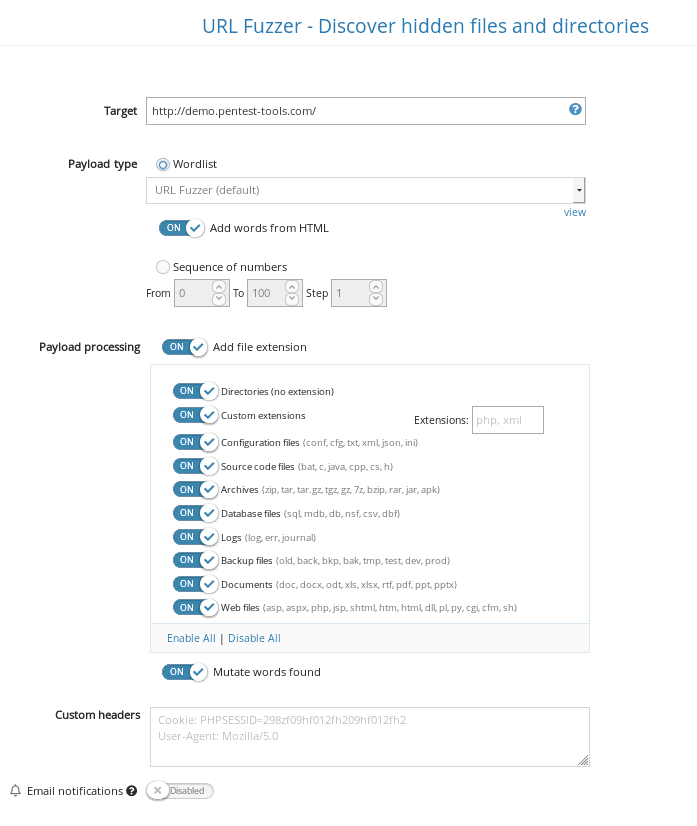
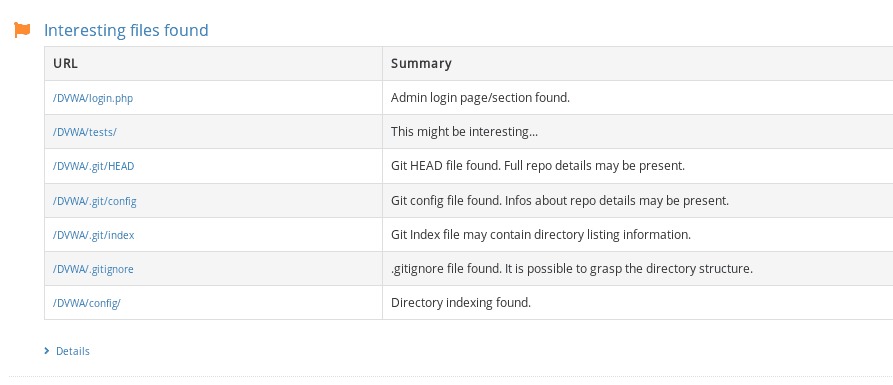
How do I prevent Sensitive Data Exposure?
When an organization lacks fundamental security controls, there is a high risk of data exposure.
Leaking sensitive credentials can cost an organization millions, bringing about penalties and fines from regulators because of lack of compliance with standards such as PCI DSS, HIPAA, GDPR, and CCPA. This vulnerability also has the potential to destroy the company’s reputation.
To enhance your prevention against attacks that seek to trigger data exposure, security and development teams should have a firm grasp of the application/system architecture.
Other than that, the following guidelines can also be of huge help:
Install an SSL certificate on the web application to protect data in transit
Never transmit or store data in plain text. Always encode/encrypt the data using strong algorithms and ensure your website application uses hashing for stored passwords
Remove any files that contain private keys, secret tokens, credentials, PII data, or any backup archive from your GitLab/Github repository, and also from your web application
Update and use the latest version of applications and patches
Employ a user behavior monitoring program to detect insider threats that could leak sensitive data.
How can system administrators fix this type of vulnerabilities?
System administrators can prevent the exploitation of this class of security weaknesses by scanning their infrastructure for assets that communicate over unencrypted/plaintext protocols with Pentest-Tools.com.
We also recommend identifying all the sensitive files that anyone can access over the internet with our URL Fuzzer.
Key takeaways
Use encrypted communication protocols: SSH over TELNET, HTTPS over HTTP, SFTP over FTP, and so on.
Review which files are publicly accessible through your web application and sanitize them.
Audit your project repository for any forgotten tokens, keys, or other confidential details left there by accident.