How to simulate phishing attacks with the HTTP Request Logger
- Article tags
As a penetration tester or a Red Team security consultant, you probably deal with lots of challenges when you want to simulate phishing attacks using social engineering techniques.
From luring victims to click on a link or open a Word document to monitoring who clicked on a phishing link, when and how many times – there’s a wide range of tactics and details to consider.
Because our team’s goal is to make your job easier by providing the right tools, we’ve put together a hands-on guide you can use straight away!
Stick with us to explore these practical scenarios in which you can use the HTTP Request Logger tool to deploy phishing campaigns faster and more effectively.
Let’s dig in!
What is the HTTP Request Logger?
The HTTP Request Logger is a tool that lets you easily create unique HTTP endpoints (handlers) which can log all requests received, including source IP, User-Agent, URL parameters, timestamp, etc.
Here’s what the format of the handler looks like:
https://pentest-tools.com/logger/<10_chars_random_string>/<optional_parameters>The “10 characters random string” attribute makes the HTTP Handler unique, meaning that no other Pentest-Tools.com user has access to it (unless they know the exact URL). Also, the optional parameters are an essential part of the URL in the context of phishing campaigns.
You could very easily customize specific URLs per victim, using the same HTTP Handler root URL.
For example, let’s assume there are 3 targets: John Snow, Arya Stark, and Jaime Lannister. You might add a custom parameter to the HTTP Handler for each of the three targets. This way, you’ll get three different and valid phishing URLs, which tell you all about the victim who clicked the link, when, and how many times.
The URLs can look like this:
https://pentest-tools.com/logger/<10_chars_random_string>/victim=John_Snow
https://pentest-tools.com/logger/<10_chars_random_string>/victim=Arya_Stark
https://pentest-tools.com/logger/<10_chars_random_string>/victim=Jaime_LannisterThe HTTP Handler has a lifetime of 60 days, and after the remaining time expires, it will no longer log the requests it received.
How to generate the HTTP Logger
Before diving into some practical examples, here’s how you can create an HTTP Handler:
While logged into your Pentest-Tools.com account, go to Tools -> EXPLOIT HELPERS & UTILS -> HTTP REQUEST LOGGER and set its Label to a desired value.
The newly created handler will look as follows:

Scenario #1 – How to check who clicked on a phishing link
You can use the HTTP Request Logger to simulate phishing attacks.
To show how it works, let’s use our three famous targets: Arya Stark, John Snow, and Jamie Lannister.
For this demo, we created disposable email addresses for them, using mailinator.com. We also used guerrillamail.com to create a fake email address for the “IT Guy” who will try to persuade the victims to click on the phishing links.
Let’s assume that Arya receives the following email:
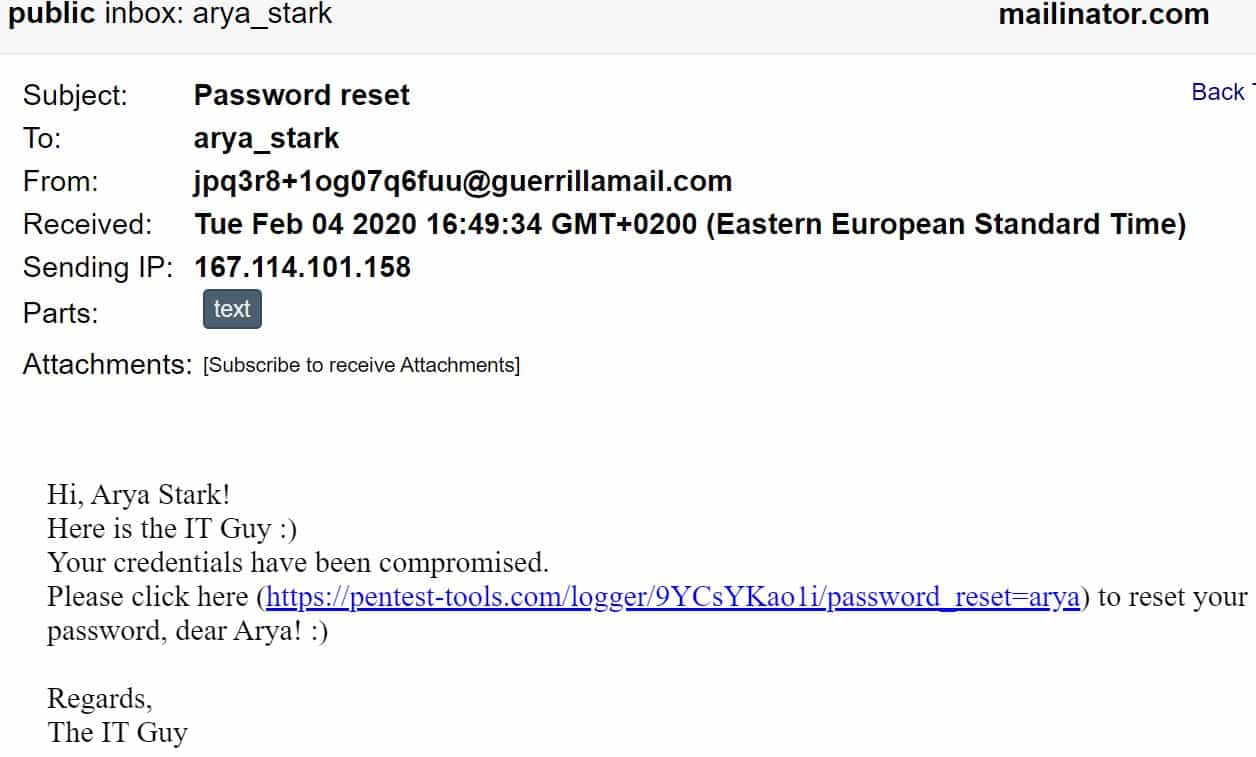
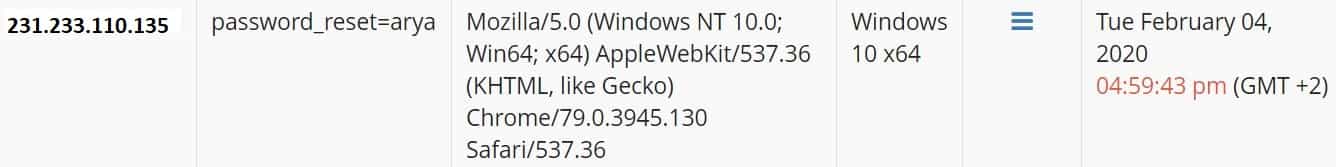
Notice that we created a custom parameter for Arya Stark (password_reset=arya). This way, we can count exactly how many times she clicked the link, from which IP addresses, and what operating system she used (based on the User-Agent set by the victim’s Browser).
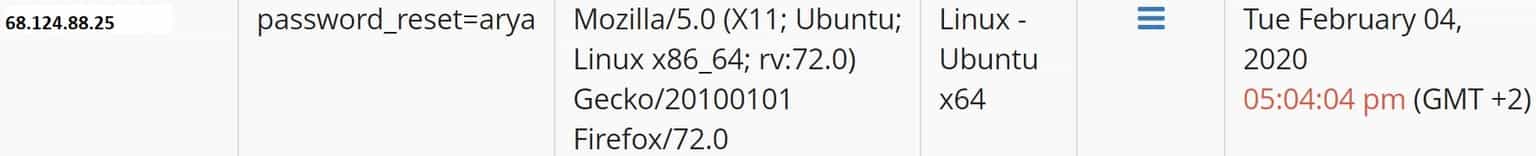
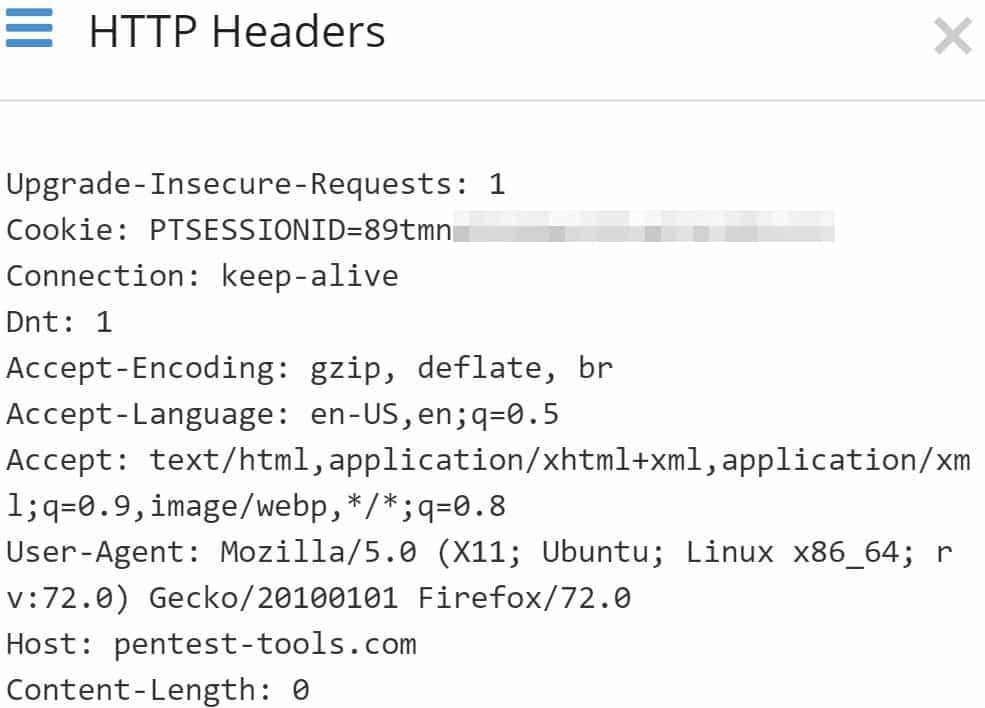
Moreover, we can check the HTTP Headers the request includes:
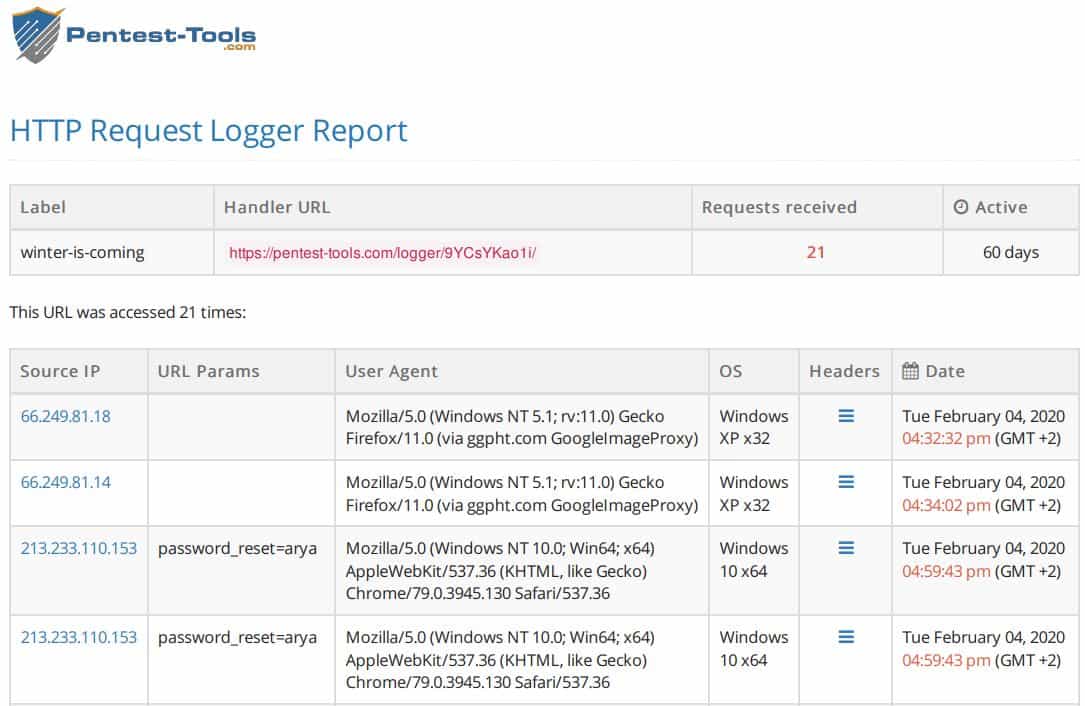
Following the same pattern, we simulated that John Snow and Jamie Lannister were also victims of this phishing attack.
You can embed the phishing link in other – more discrete – ways too! You can use images, tracking pixels, and so on, but these techniques are for another article.
Our tool monitors constantly if the targets have been persuaded or not, how many times and when. Whenever you consider, you can export these results in a PDF report file .
Scenario #2 – Advanced phishing attack using Word documents
In this scenario, we counted how many victims try to open a Word document delivered to their email address. We didn’t place any macro inside the document, we only embedded a picture object that is loaded from an external URL (our HTTP handler).
Each time the user opens the document, Microsoft Office makes an HTTP request to our handler to load the image, disclosing the user’s IP address and other details.
In order to craft a deceptive document, start with an empty docx file and press CTRL+F9 to embed an external Object.
You will see that { } appears.
Right-click on it and go to “Edit Field…”
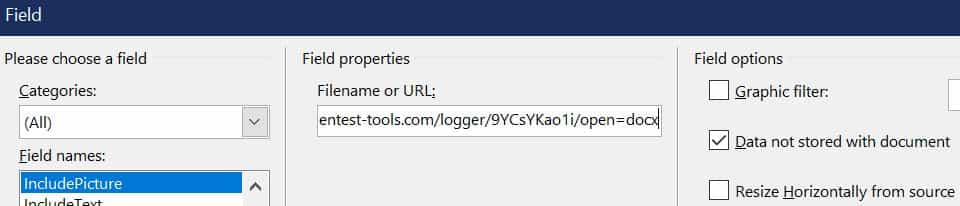
Create the requested fields as shown below (Field names -> IncludePicture; URL: https://pentest-tools.com/logger/9YCsYKao1i/open=docx and check “Data not stored with the document”), and click OK:
Next, resize the “image” to 1×1 pixels so it’s not visible and easily detected by the victim. Save the document and send it to the victim.
Once they open it, the request is performed. You can check the results in the dashboard right away!

If you try to analyze what happened behind the scenes when you embedded the External image resource, you can open the .docx file with 7-zip and go to file.docx\word\_rels\document.xml.rels file.
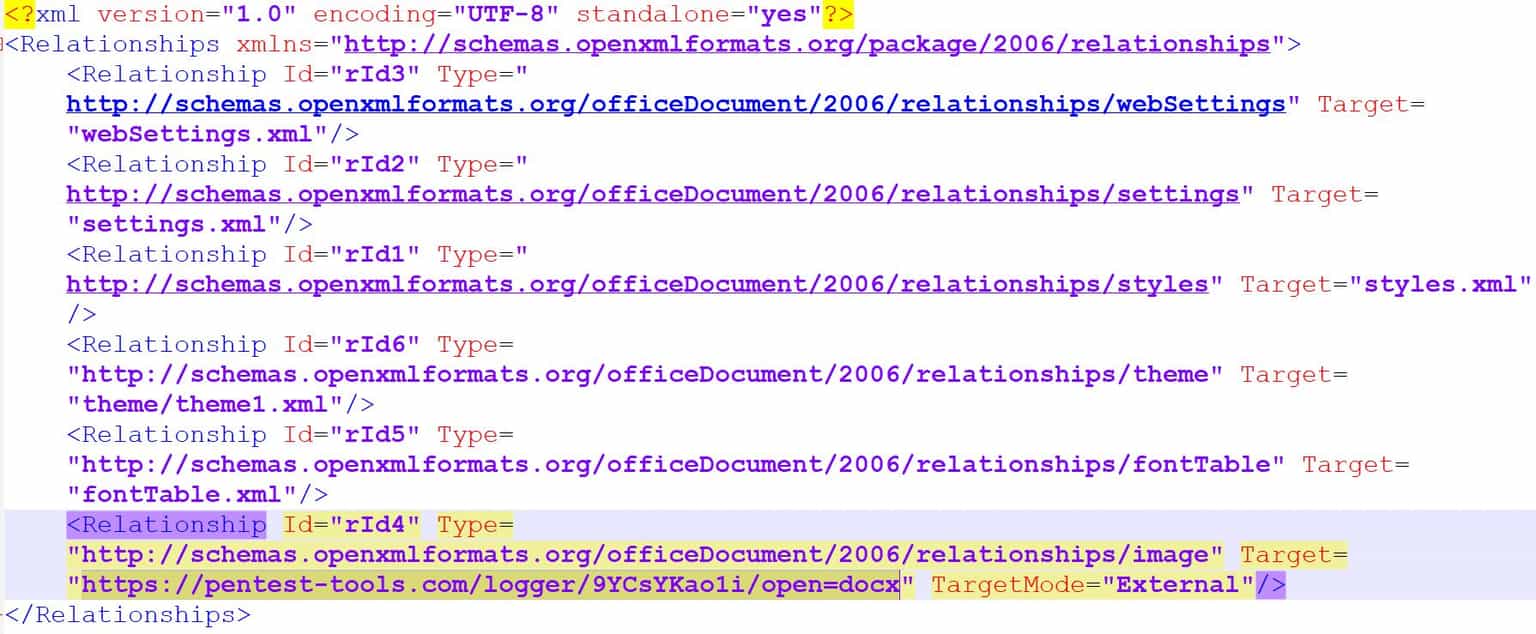
From here, you can observe the Relationship parameter with id rId4, which includes our HTTP Request Logger link set as Target. Also, the TargetMode parameter has the value “External”.
Pro tip: The key idea of this phishing scenario is that the victims have to open the Word document received. They don’t have to enable macros or click on any “OK” button. This shows that users can be easily tricked into clicking on a link or opening a document without recognizing a phishing attack.
Simpler, faster phishing tests with the HTTP Request Logger
Now that you’ve seen these practical scenarios in which you can use the HTTP Request Logger to make your work easier and faster, you’re ready to get going!
We built this tool to simplify your workflow, whether you’re a pentester or a security consultant, by providing a custom HTTP server that records and shows all HTTP requests in one place.
You can use the tool to better simulate phishing attacks and perform faster security tests.
If you found this short tutorial useful, don’t hesitate to use the HTTP Request Logger tool in your future penetration testing engagements to create better security awareness for your customers!