New VPN agent formats, API methods, filters & other updates

- Article tags
Here are 4 platform improvements we’ve worked on in the current update to make Pentest-Tools.com a must-have asset for your pentesting toolbox.
1. VPN Agent in Hyper-V and VirtualBox formats
2. New API methods and updates added
3. More filters to generate faster reports
4. An enhanced version of the pentest report (.docx)
Let’s unpack them!
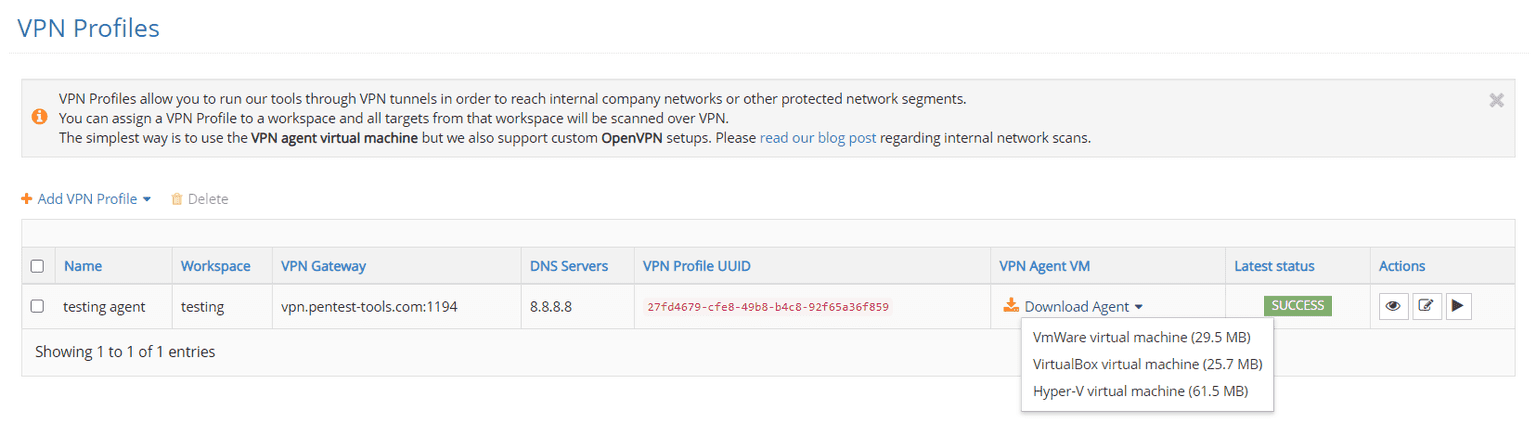
1. Set up internal scans easier with 2 new VPN Agent formats
You can now use the VPN Agent virtual machine in two new formats, Hyper-V and VirtualBox, and run them in your internal network.
To download any of these formats, log in to your account, go to VPN Profiles, and select Download Agent.
To learn how easily you can configure the VPN Agent and add a new VPN profile, check out the step-by-step tutorial from our Support Center.
2. New API methods and updates!
We’ve added new API methods to help you improve your target management on Pentest-Tools.com.
The add_target operation creates a new target with an optional description.
The updatetargetdescription operation updates the description of a target.
The startscanby_targetid operation starts a new scan using a specific target_id.
We’ve also included new parameters for the get_scans method to provide more granular results based on the workspace_id and target_id filters.
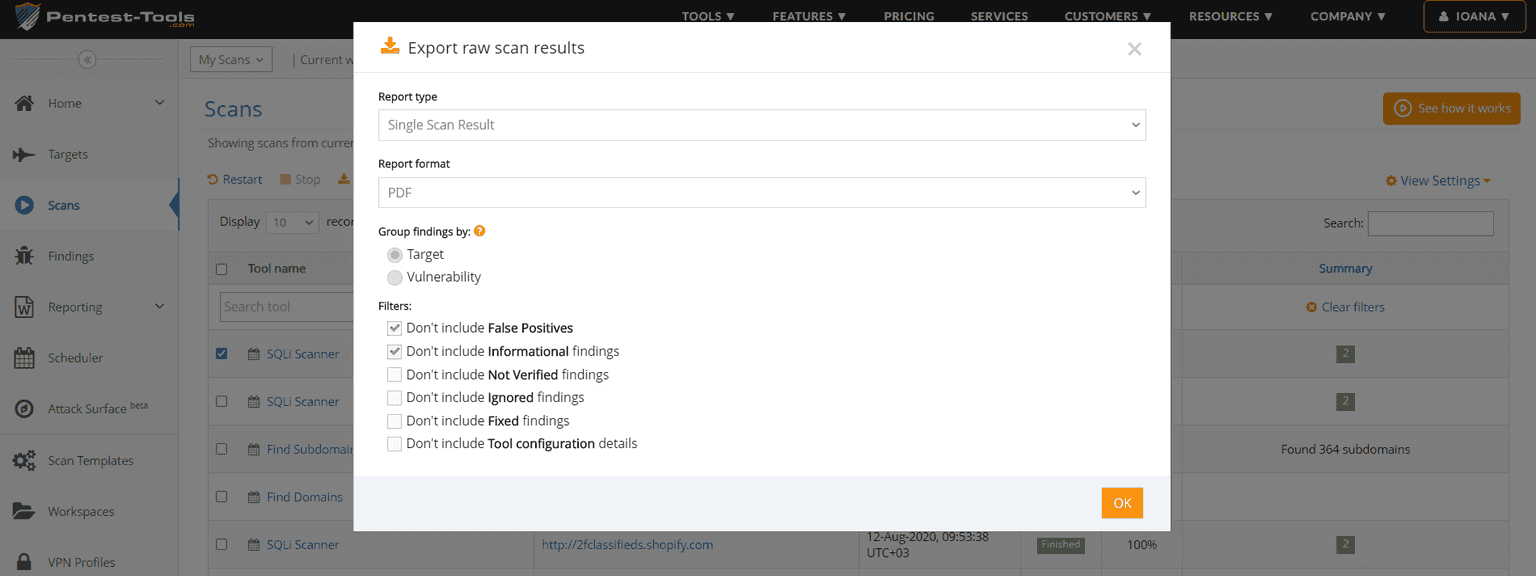
3. More filters to export specific reports faster
When you generate single scan reports from tool results, now you can exclude from these reports findings marked as Ignored Findings, Fixed Findings, Tool configuration details, and more.
To do this, go to Scans, select which scan results you want to include in the report, and then click on the Export button.
4. Customizable, enriched pentesting report for the editable .docx format
Get rich, pre-filled information on your findings, including a new Appendix section which includes the list of tools and techniques used during the penetration test.
From your account, choose the findings you want to include in the report, select the Editable .docx Pentest Report type and click OK.

We also added the low-risk vulnerabilities to the executive summary section of the report so you can have a better overview of all findings.
“All of the scans I’ve used run fast and the reports contain the details that you need, no fluff. “
This is one of the reasons customers use the reporting section.
Create and generate customizable reports, packed with vulnerability details and risk information, ready-to-use remediation advice, and more!