Detect critical CVEs, scan stats + more updates

- Article tags
If you’ve had an intense summer, that makes two of us. We worked hard to roll out new and helpful updates, so let’s break them down:
Detect 4 critical & high-risk CVEs with the new Network Scanner modules
Control the delay between requests & recursion options in the URL Fuzzer
Get scan stats with the new Website Scanner
Run scheduled scans on demand
Use the HTTP Request Logger through our API
Add targets using the CIDR notation
Enable more enumeration options in the WordPress Scanner
Let’s unpack them!
1. Detect 4 crucial CVEs with the new detection modules we built from scratch
When you run our Network Vulnerability Scanner against your targets, they’ll also check them for:
the critical Microsoft Exchange Server RCE vulnerability – CVE-2021-28480
the Node.js Systeminformation Command Injection – CVE-2021-21315
the entry point for the ProxyShell attack chain – CVE-2021-34473
the path traversal vulnerability in Fortinet’s FortiGate SSL VPN appliance – CVE-2018-13379
Use the Full Scan option from the Network Vulnerability Scanner with OpenVAS and see the scan results in Findings.
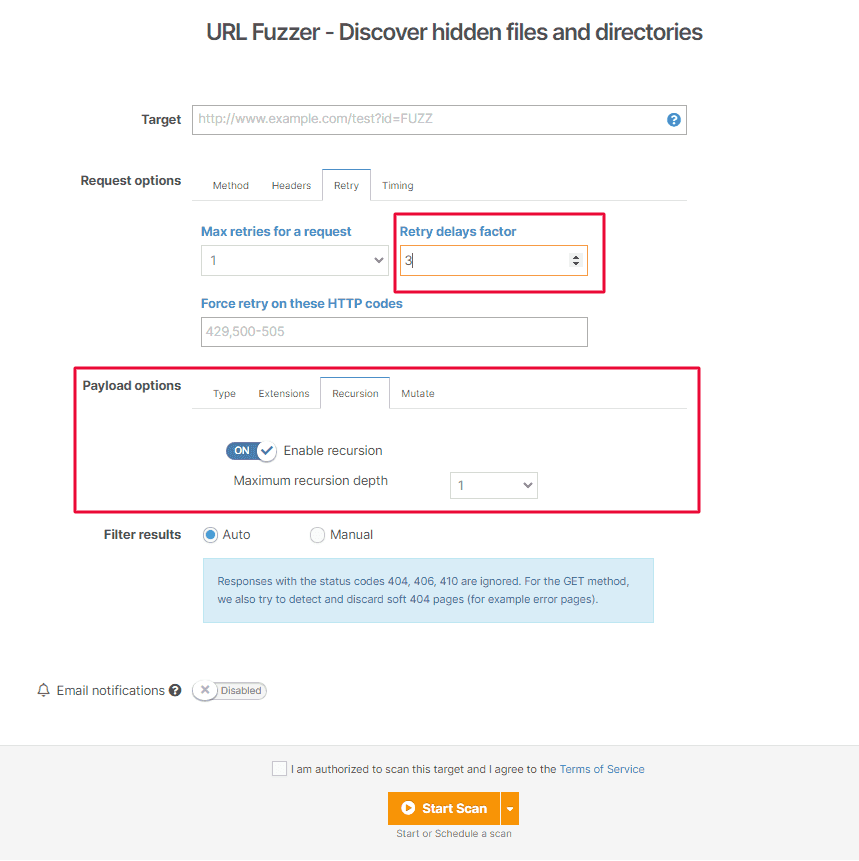
2. Control the delay between requests and use recursive searches with the URL Fuzzer
You now have the option to control the delay between the HTTP requests you make with the URL Fuzzer. To exponentially increase the delay, make sure to add up to 120 retry delays/request.
If you need to validate payloads with the URL Fuzzer, you can now automatically run recursive searches inside all the directories you’ve already discovered.
Go to URL Fuzzer, add your URL target, select Payload options, and enable Recursion. You can set a maximum of 3 recursion depth levels/payload.
Here’s a snapshot of these two options:
3. Get specific scan stats about your targets with the new Website Scanner
Scan results for our new Website Scanner come with a richer summary section!
When you scan your URL target with our proprietary Website Scanner, you get detailed, specific scan stats such as URLs spidered, the total number of HTTP requests, error count, injection points detected, and more.
Check it out:

4. Run scheduled scans on demand
Another improvement we added is the option to run a scheduled scan whenever you need to.
To keep your work flexible and productive, select Scheduler from the Dashboard, select a Tool name and Run a specific scan.

5. API support available for the HTTP Request Logger
This latest platform update allows you to programmatically create HTTP handlers through the API. Using specific parameters, you can automate scanning and save invaluable time.
6. Add targets using the CIDR notation
On Pentest-Tools.com we now support the CIDR (Classless Inter-Domain Routing) notation, which lets you add your IP targets accordingly (e.g: 192.168.1.0/24).
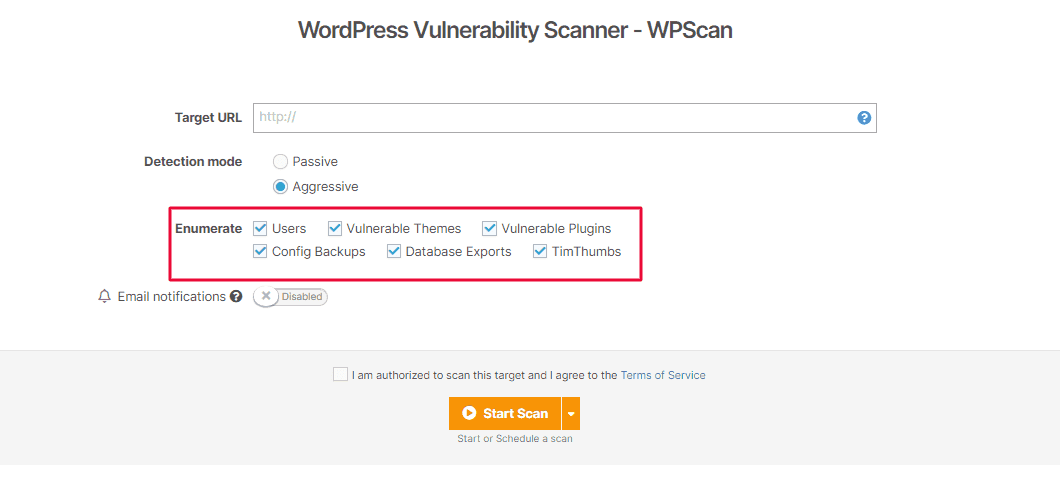
7. More enumeration options available in the WordPress Scanner
The WordPress Vulnerability Scanner can now search for config backups, database exports, or TimThumbs!
Add your URL target and select specific enumeration options to uncover juicy findings in WordPress sites.