How to Perform Internal Network Scanning with Pentest-Tools.com

- Article tags
In this article, we show you how to scan hosts from your internal network using our security tools from Pentest-Tools.com. This is a new capability that we have recently added to our platform and it uses VPN tunnels to reach the internal networks.
[UPDATE June 2020] We’ve added a new method to scan your internal network that doesn’t require any special configuration. Just use the VPN Agent and start scanning. To learn how easily you can configure the VPN Agent and create a new VPN profile on Pentest-Tools.com, read our step-by-step technical tutorial.
1. How does it work?
Simply said, we use OpenVPN to create a secure tunnel between our scanning machines and your network. This way, our scanners can reach the hosts from your internal network through the VPN tunnel. For this, you need to have a properly configured OpenVPN server.
2. Is this secure for my network?
You should know that every packet reaching or leaving your network is fully encrypted and there is nobody else accessing your network through this channel.
Furthermore, you can configure your VPN server to allow access only to certain internal hosts that you want to scan and not to the whole network. This way you can be fully assured that nobody is messing with your network over VPN.
3. How to configure a scan through a VPN
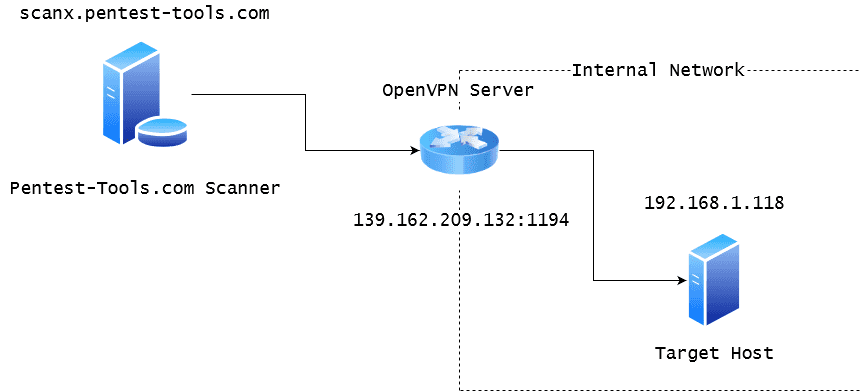
Let’s consider a scenario where we want to run the TCP Port Scanner against a target inside the private network 192.168.1.0/24.
The sample OpenVPN server can be publicly accessed at the IP 139.162.209.132 on port 1194 (default for OpenVPN service) and it is also set as the default gateway for your internal target host.
Let’s see how to configure this setup such that our scanner can reach the internal host, as in the diagram below:
Step 1: Export the configuration file from the OpenVPN Server
You should export the .ovpn configuration file from your OpenVPN server. This file contains information for an OpenVPN client to connect to the server. You can typically export this file directly from the web interface of your VPN gateway or router.
If you want to install a new OpenVPN server inside your network, we recommend checking out this script that simplifies the process.
The exported .ovpn file should look like the one below (this is just an example OpenVPN config file). You should pay attention to the following lines:
remote {your-external-ip} {port}– Make sure that your external IP is right and the port is not blocked by any firewall. Here is an iptables guide to properly open the VPN port.proto {TCP/UDP}– We recommend using TCP over UDP for a more reliable connection.dhcp-option DNS {internal-dns-ip}(Optional) – This is required if you have an internal DNS Server inside your local network and you want to scan targets by their hostname.
config.ovpn
client
dev tun
proto tcp
sndbuf 0
rcvbuf 0
remote 139.162.209.132 1194
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
verb 3
<ca>
-----BEGIN CERTIFICATE-----
MIIDQjCCAiqgAwIBAgIUBa2MqM7dbcE5eePAwPituT+RqZAwDQYJKoZIhvcNAQEL
BQAwEzERMA8GA1UEAwwIQ2hhbmdlTWUwHhcNMTkwOTEyMTI1NDEwWhcNMjkwOTA5
MTI1NDEwWjATMREwDwYDVQQDDAhDaGFuZ2VNZTCCASIwDQYJKoZIhvcNAQEBBQAD
ggEPADCCAQoCggEBAMnIwLMKPAg8BzPPslPoprPi8FmoNVQfGopCHAZg1BaHXqWS
g9pfWkUlNr4yIbsb9INw89pLYELsThDj+gBCRW/SMND/RaJo+VGBeThGnv31bXKe
tLtifO9sb8xucwnn0gfwr7yEBfkU/hAPYZM4gRPxjLBmWv8TEFdvrx6o6fGvCNuu
G9+2qXLCUDpHnuvHO4lfeRlM+RPU4LhrL2GUOvRRTf17Xv4ttEo6NdxRNKkE+DeFStep 2: Import the configuration file in Pentest-Tools.com
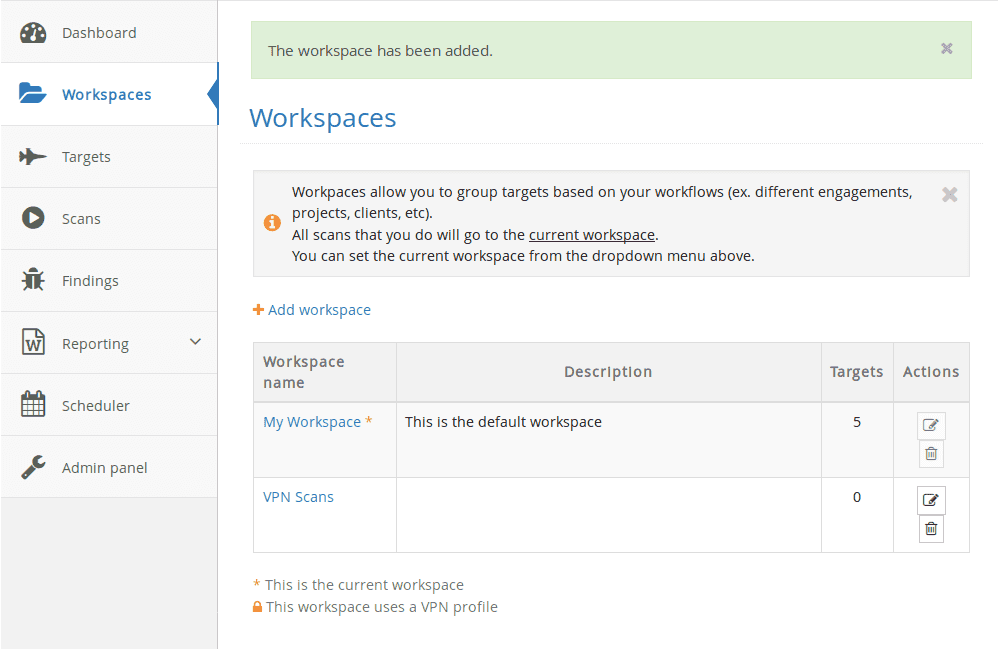
Once logged in to our platform, you have to create a new workspace for your internal targets. This workspace can contain internal IP addresses or hostnames, which you can separate from your external ones. Go to Workspaces and add a new workspace (in our case it will be called VPN Scans).
Then you have to go to My Account, VPN tab, to create a VPN profile which includes the Ovpn file. You also have to assign the VPN profile to one or more workspaces.
When a workspace has an associated VPN profile, all the targets from that workspace will be scanned over the VPN.

Once added, it is recommended to test the configuration by clicking the Play button from the Actions column.

If your VPN connection is successful, you are ready for your first internal scan. However, if you encounter any problems with the connection, you can troubleshoot the problem by viewing the connection logs (Press the View button from Actions). Please make sure the OpenVPN port is open to the internet – this is the most encountered connection issue.
Step 3: Add an internal target to the VPN workspace
First, make sure you have switched to the recently added workspace (set VPN Scans as your current workspace).
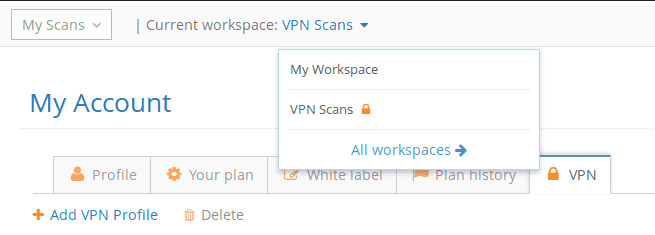
Notice the lock icon which indicates that this workspace has an associated VPN profile. Any scan performed within this workspace creates a VPN tunnel to the destination network using the imported config file. Please note that a new VPN tunnel is established for every new scan performed.
If you have multiple scans in parallel, you will have the same number of VPN tunnels established with the VPN server.

Now we can create the target. We are going to add the target IP address 192.168.1.118. This host will expose port 80 inside the local network. For this example, we are running a simple python web server:

Notice that the bind is on 192.168.1.0:80, so it is accessible only from the local network.

Also, this can be done by running:
$sudo python -m SimpleHTTPServer 80 –bind 192.168.1.0
Step 4: Scanning the target
A simple TCP Port scan on the target host for the Top 100 Ports will detect port 80 open. Remember that the port was open only to the local network and not to the internet.
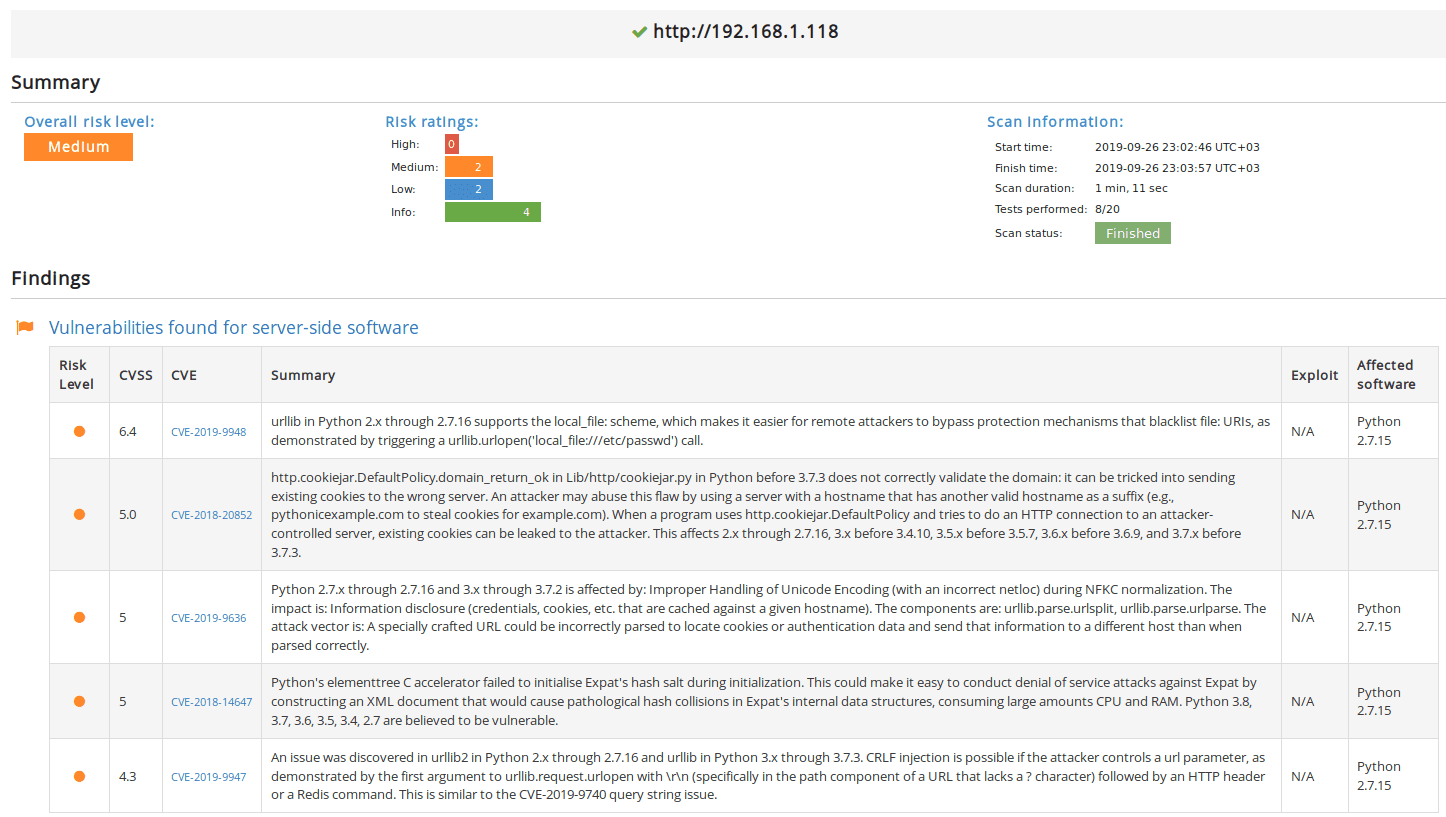
You can also scan it using our Website Vulnerability Scanner. It will detectSimpleHTTP 0.6 and Python 2.7.15.
It looks like Python’s BaseHTTPServer comes with a few CVEs:
4. Follow this technical guide to perform Internal Network Scanning with Pentest-Tools.com
To quickly discover vulnerabilities and potential security risks, you should perform regular internal and external scans. Scanning your internal network can help you identify:
Missing security patches and outdated network services
Ways to fix vulnerabilities found in your current infrastructure
Unexpected attack vectors
The bigger picture of your infrastructure’s security posture