Year in review: 2024 on Pentest-Tools.com

Too many tools. Too little integration. Too much pressure to prove your defenses work.
Your challenges become milestones on our product roadmap.
That’s why this past year we focused on improving accuracy and coverage, making vulnerability management actionable, and streamlining workflows that keep everything running.
And we didn’t just ship updates. We proved our impact, earning a spot on Deloitte's EMEA Fast 500 and becoming one of the fastest growing tech companies in Europe, the Middle East and Africa. 🚀
Let’s dive into the wins, lessons, and breakthroughs that made 2024 a memorable year.

1 scan every 5s in 2024 (and more Pentest-Tools.com numbers)
In 2024, our customers ran nearly 6.3 million scans. That’s 1 scan every 5 seconds!
They also saved countless hours with 1.6 million scheduled scans and over 1.2 million API-driven scans - twice the volume compared to 2023.
Automation took center stage, with 611,000+ scans powered by pentest robots. Their top picks were the:
Website Scanner - All Ports pentest robot, which scans all HTTP/S ports (1-65535) and checks for SQL injection, XSS, LFI, and other OWASP Top 10 vulnerabilities.
HTTP Lockpicker pentest robot that identifies web login interfaces, crawls URLs, and performs dictionary-based brute force attacks to test unauthorized access.
Treasure Hunter (host) pentest robot, which discovers open ports, services, and hidden files or directories to uncover secrets and sensitive information.
Auto HTTP Login Bruteforcer pentest robot, which targets HTTP Basic Authentication (401) URLs and performs brute force attacks using common credentials across all HTTP/S ports.
Network Scanner - Critical CVEs (domain) pentest robot, designed to map subdomains, identify machines behind a domain, and scan for critical vulnerabilities using Sniper Auto-Exploiter detection modules.
Using the findings and results they got from our tools, customers downloaded almost 73.000 reports in their preferred formats: PDF, customizable DOCX, HTML, XLSX, CSV, aggregated scan reports, and JSON.
Now let’s talk about the top tools they used to make this happen.
The most used pentesting tools in 2024 - free and paid
This past year, people from all over the world ran over 1.8 million scans at no cost on our website with our stack of free pentesting tools. They preferred these 5 tools:
Top 5 free pentest tools in 2024
TCP Port Scanner - with almost 560.000 free scans
Subdomain Finder - with over 410.000 free scans
Website Vulnerability Scanner - with almost 400.000 free scans
URL Fuzzer - almost 157000 free scans
Network Vulnerability Scanner - almost 120.000 free scans
Almost 110.000 people created a free account in the past year to enjoy parallel scans, exportable attack surface results (CSV, JSON), up to 30 days access to reports, and more.
Many of them wanted to get a feel of Pentest-Tools.com as a full product, so they decided to upgrade to a paid plan, joining the 1900+ security teams in 119 countries who rely on us for attack surface management and penetration testing activities.
Here are their go-tos for accurate results and rich evidence for vulnerability validation:
Top 5 paid pentest tools in 2024
Network Vulnerability Scanner - almost 1.5 million scans!
Port Scanner - almost 1.3 million scans
Website Vulnerability Scanner - over 1.2 million scans
Subdomain Finder - almost 700.000 scans
URL Fuzzer - over 220.000 scans
Keep in mind these aren’t the final numbers since 2024 isn’t over yet!
Top 5 launches on Pentest-Tools.com in 2024
We rolled out hundreds of improvements through our monthly updates this year, but let’s boil them down to our top five:
1. New tool: the Kubernetes Vulnerability Scanner
A customer request turned into a new tool: the Kubernetes Vulnerability Scanner, which quickly became a favorite.
Since its launch, it’s found Kubernetes vulnerabilities and misconfigurations ranging from reconnaissance (Node/Master cluster components) to initial access vulnerabilities (exposed pods, logs, Kubelet API endpoints etc.). And it can even emulate an authenticated adversary!
Here’s a quick look at how it works - and how we built it:

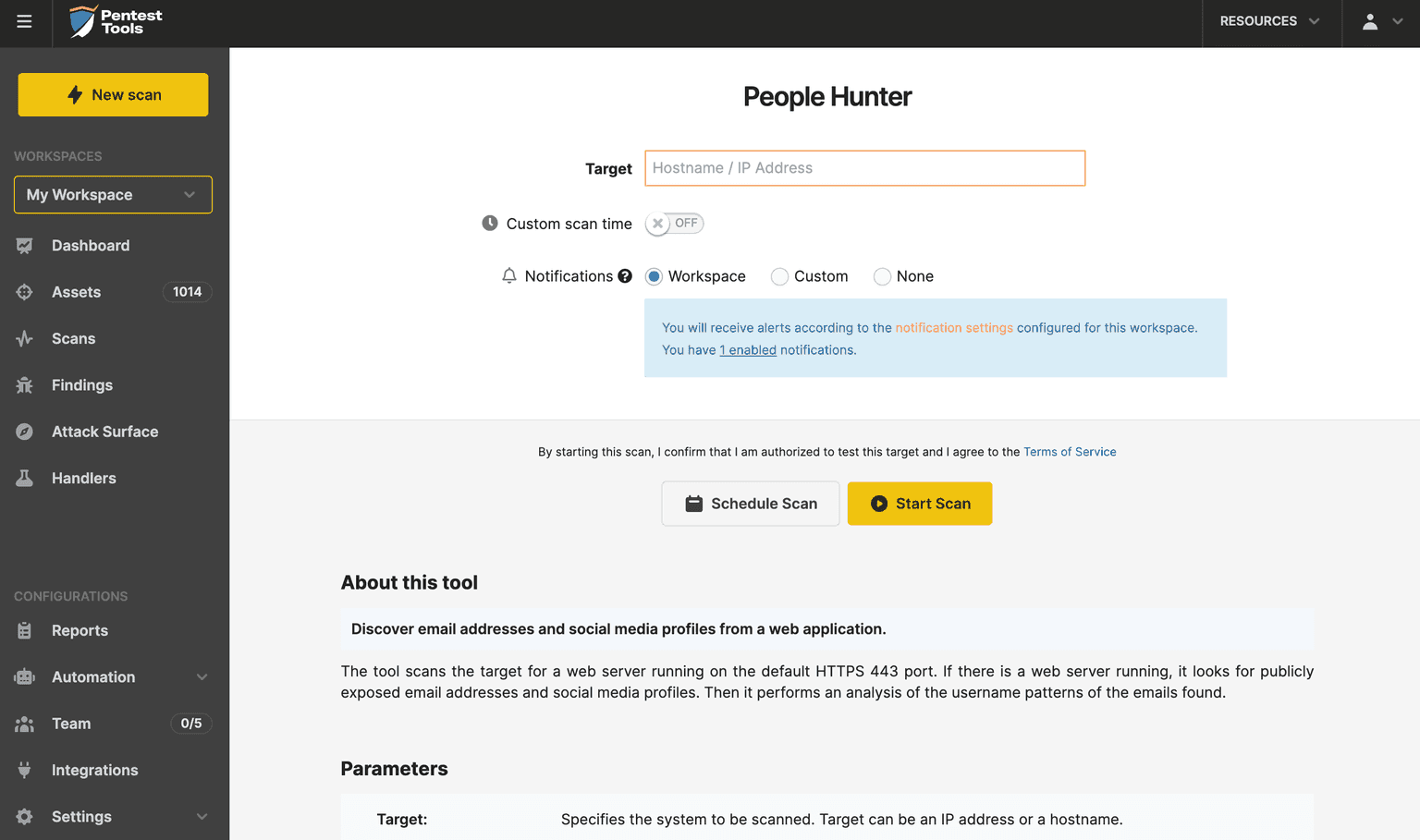
2. New tool: know your targets better with People Hunter
We also added a tool called People Hunter this year, which identifies the people associated with the target, using publicly available information from web server responses.
Details such as email addresses (and their patterns) and social media profiles help you identify potential targets for social engineering attacks.
This one’s available just for Pentest-Tools.com customers at the moment in case you’re wondering why you can’t find it on the website.
3. Continuous exposure monitoring made (even) easier
First we introduced the scan diff notification, so you can easily track changes in your targets' security posture.
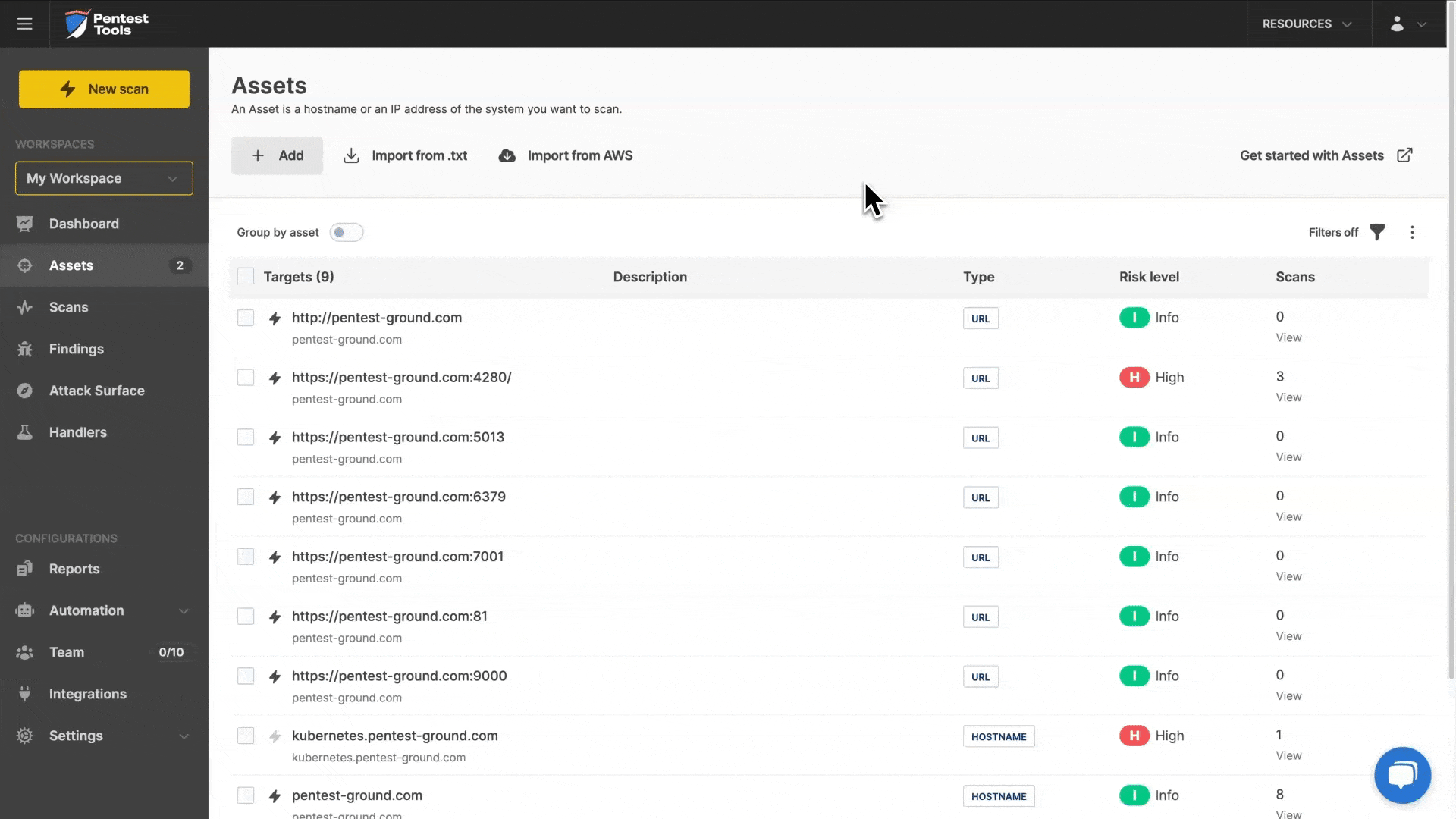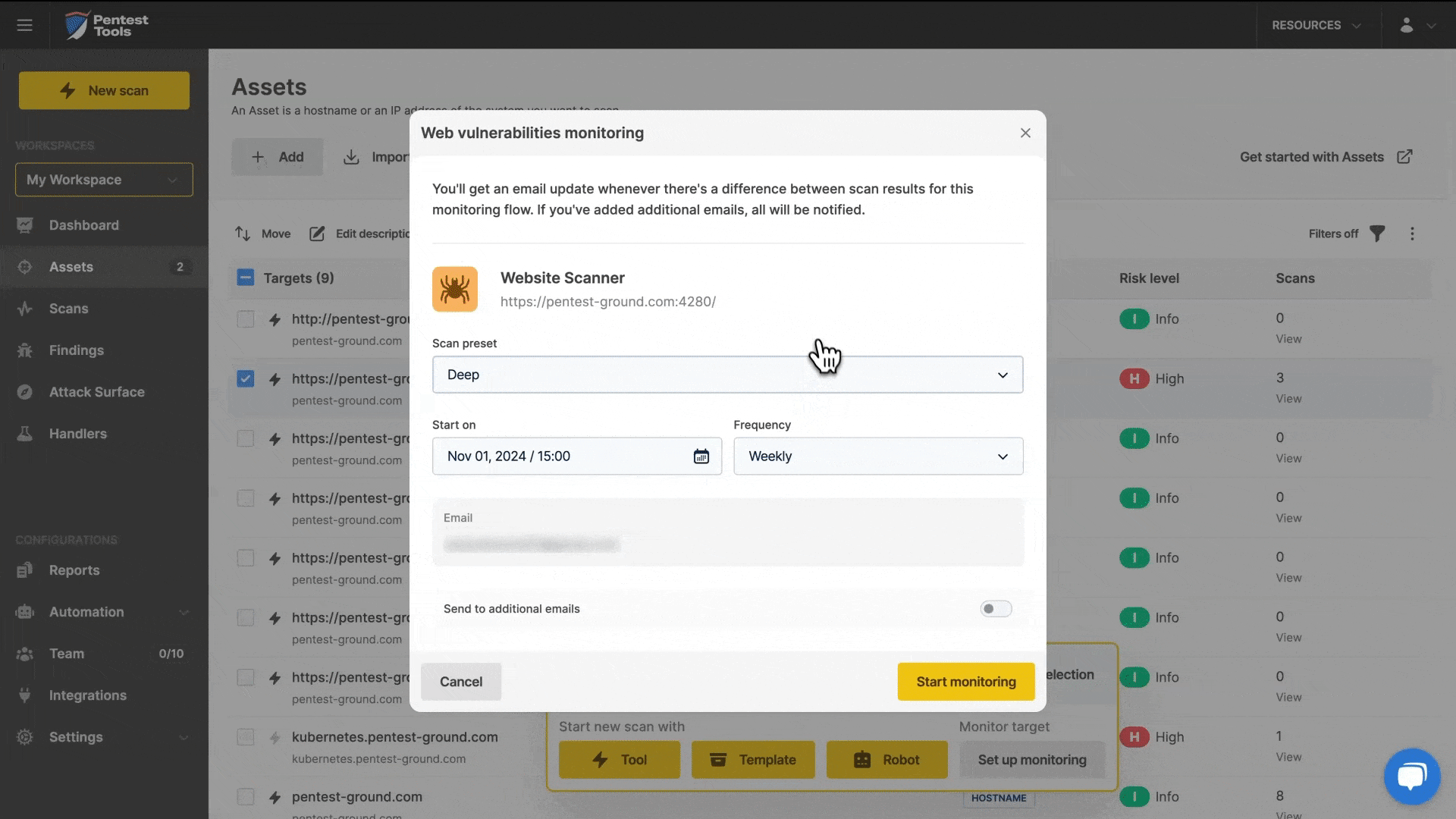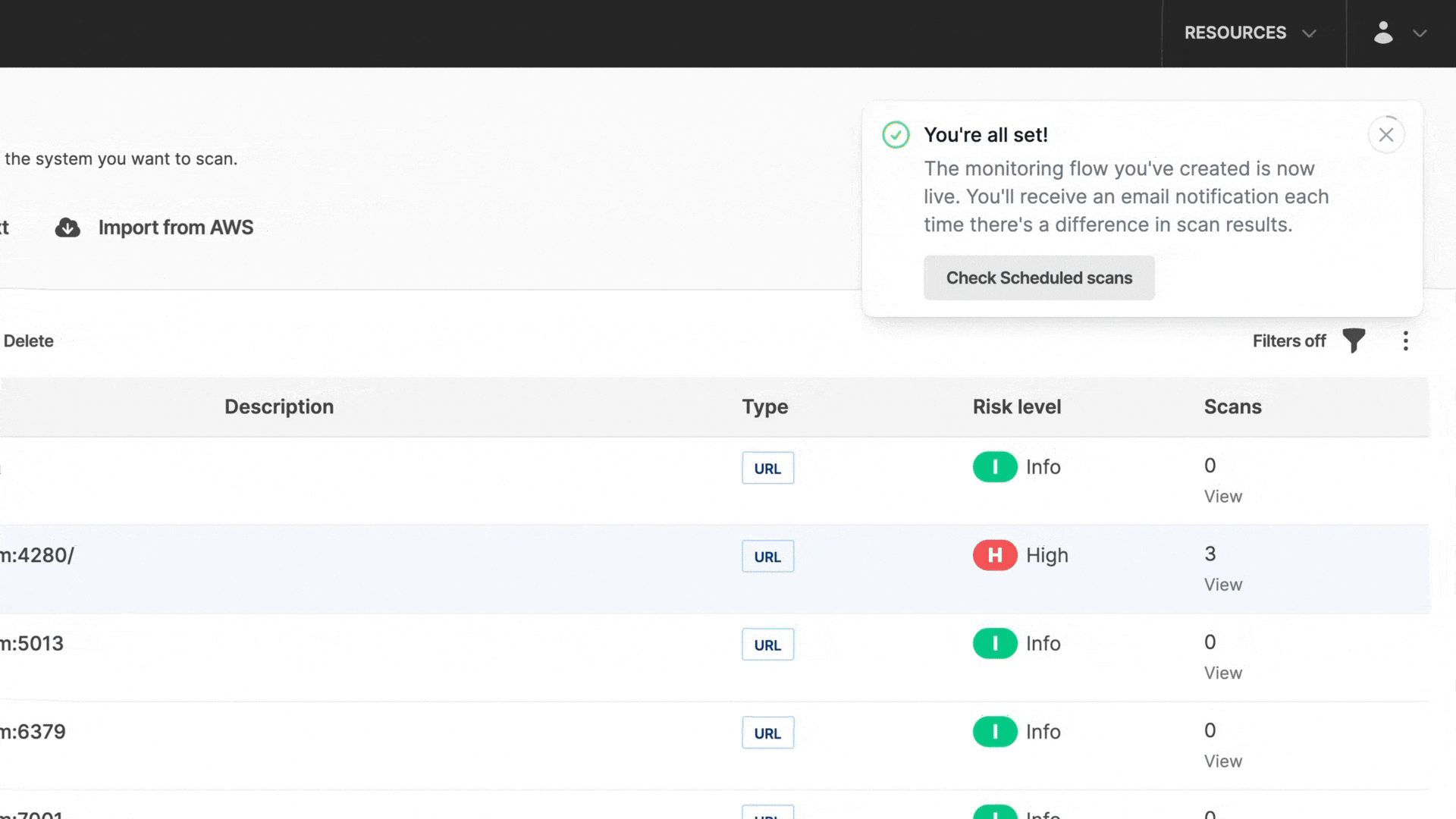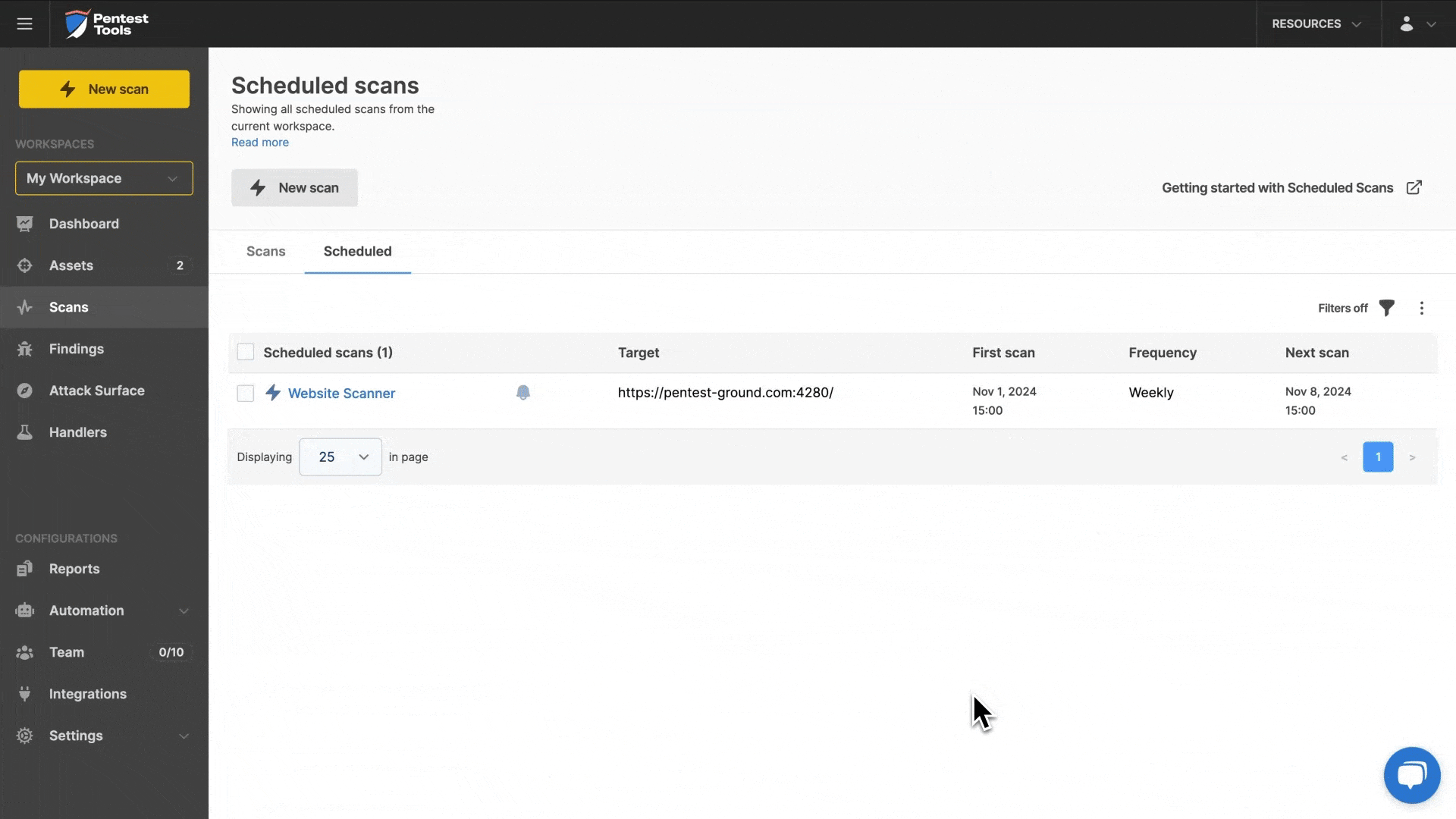
Then we made it even easier to set up a complete monitoring flow using our Network and Website Vulnerability Scanners, Port Scanner, and Subdomain Finder.
Customers can just select their target(s) and follow the Monitor setup process. Once done, they’ll automatically get email alerts whenever there's an update.
Because we know attack surface management is a major concern for everyone, we also made this exposure monitoring feature available to the 100.000+ people who use our free toolkit!

4. Exploit selected CVEs with Sniper
In 2024, we gave you even more control over our most powerful offensive security tool - Sniper Auto-Exploiter.
Automatically getting proof of exploitation for specific CVEs became an option for everyone who wants laser-focused results:

Our Vulnerability & Exploits Database now includes over 150 custom exploits for critical CVEs which you can also use as input for Sniper.
And don't forget that, whenever we add new exploits in Sniper, it means our Network Scanner can also detect those CVEs for you.
5. Import your AWS targets (fast!)
Besides integrations with Discord (for custom notification flows) and Vanta (for automatic PDF reports from scheduled scans), we also added an AWS integration to make importing AWS targets into your account quick and effective.
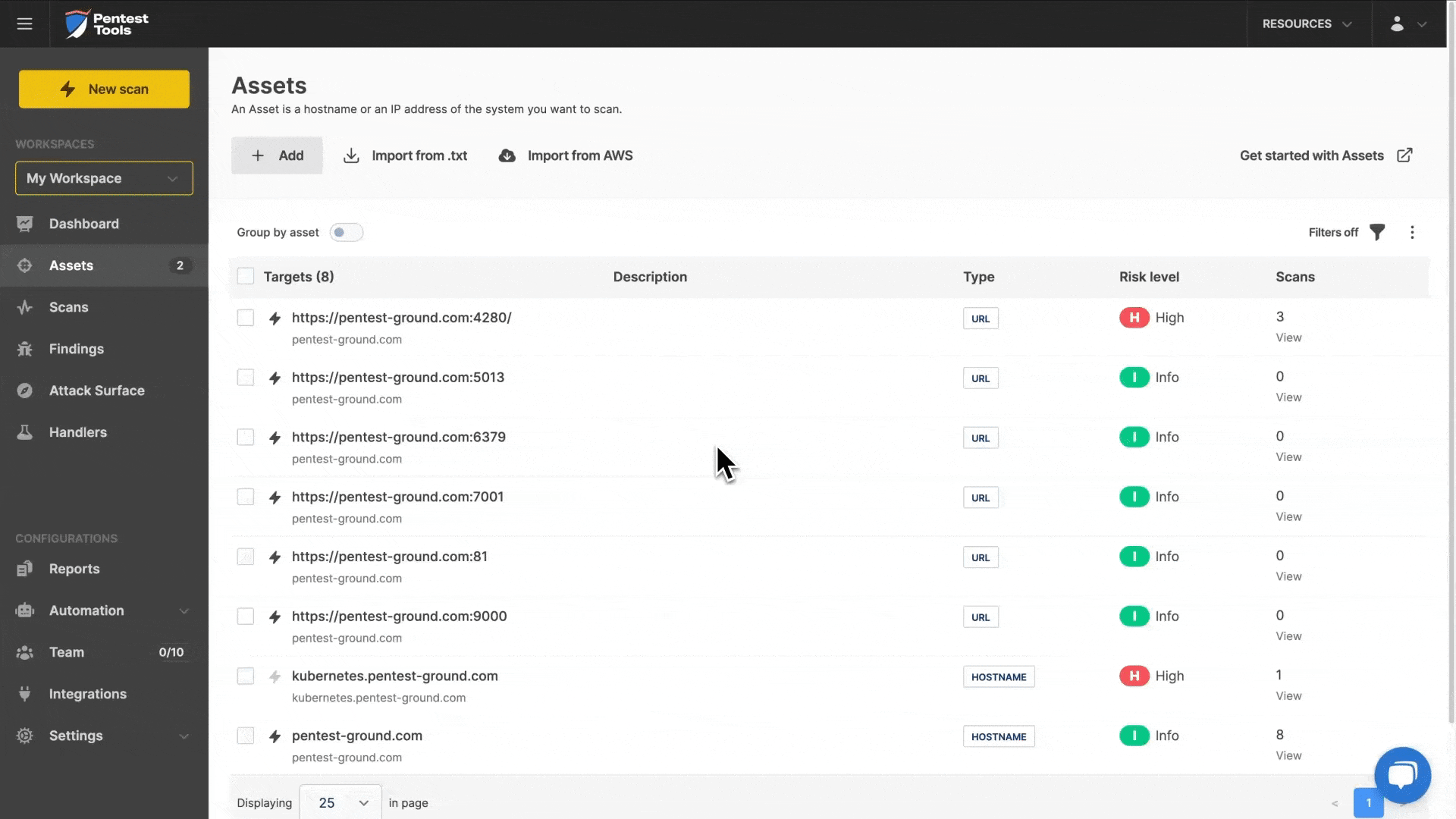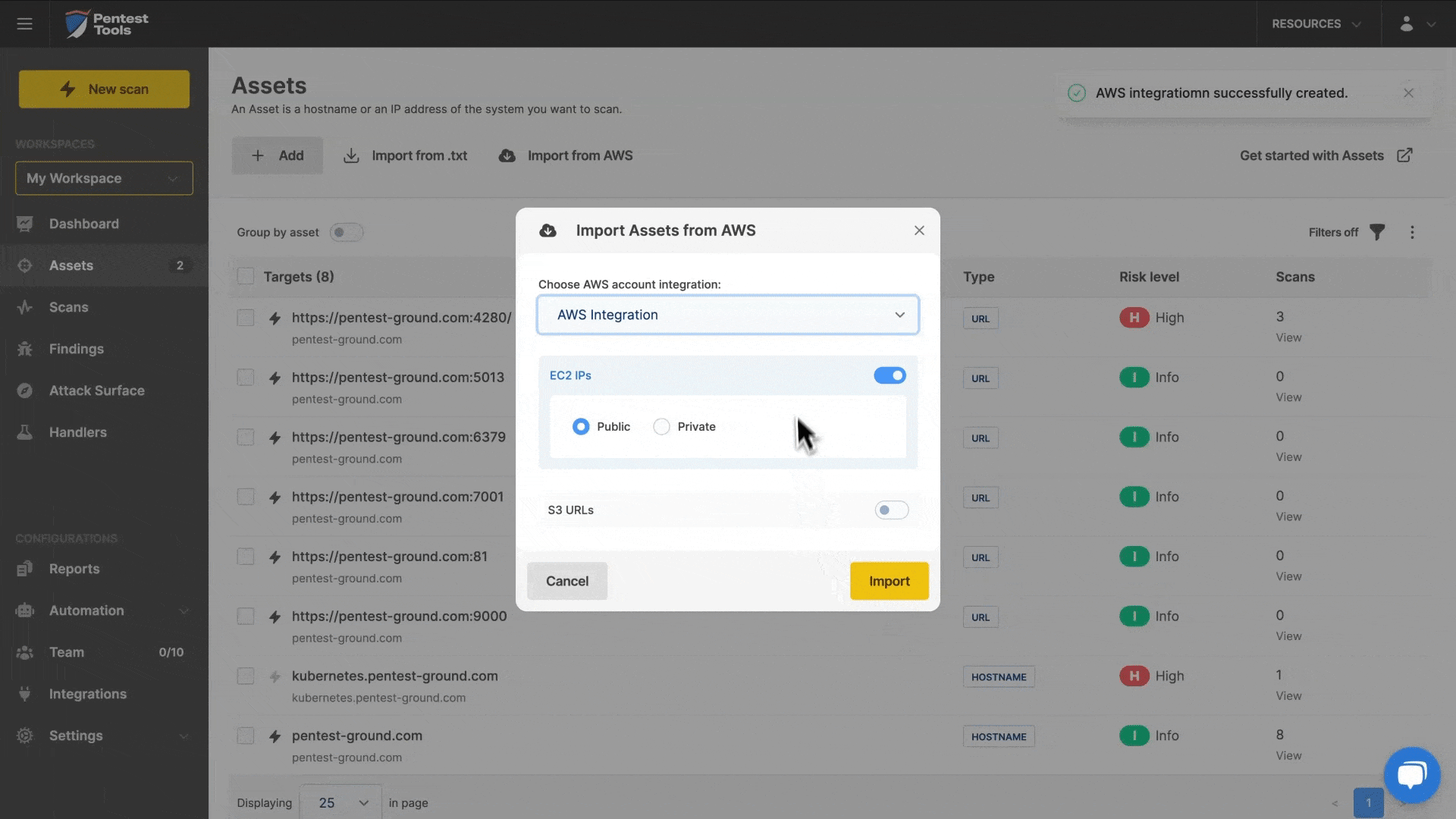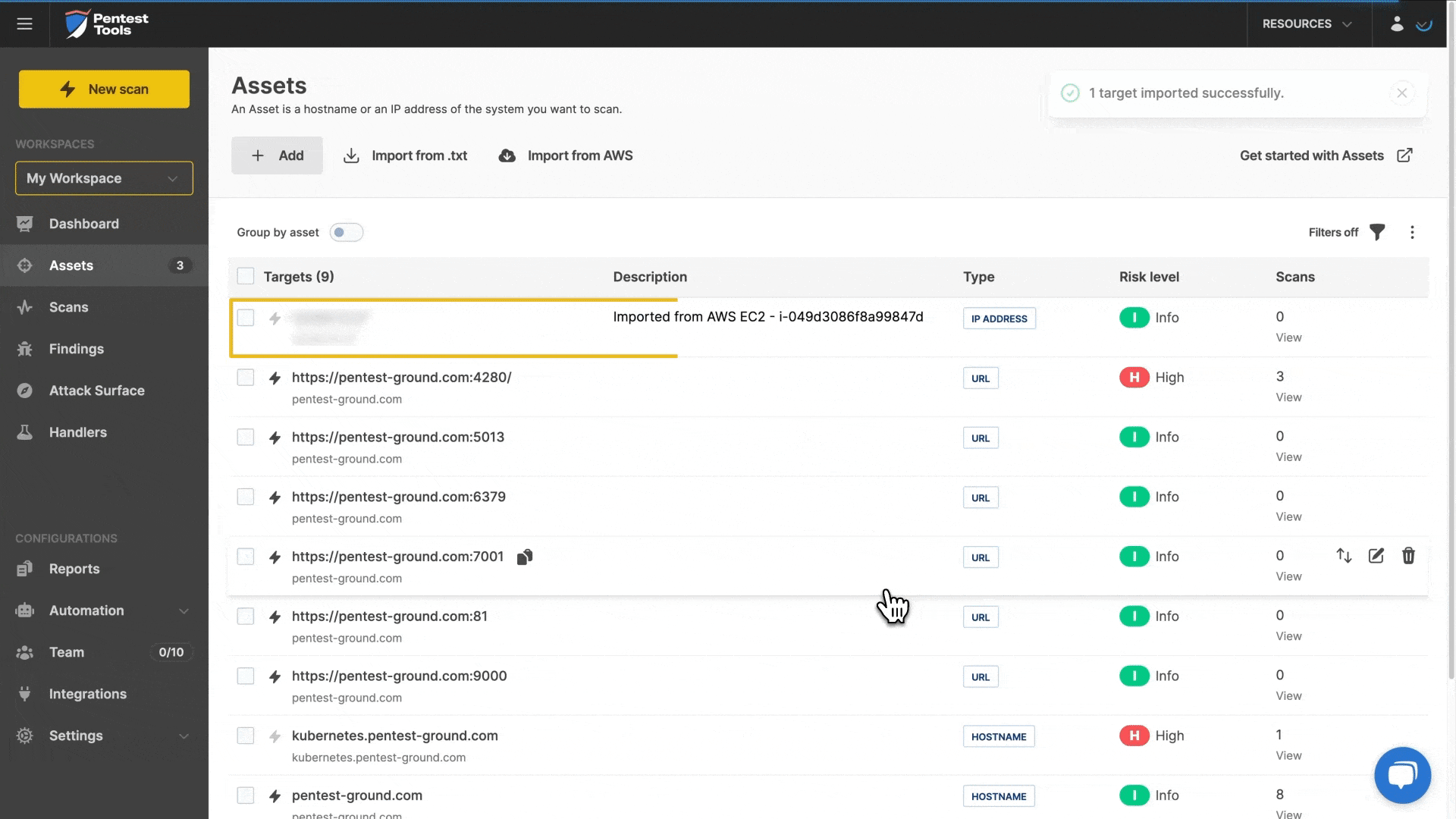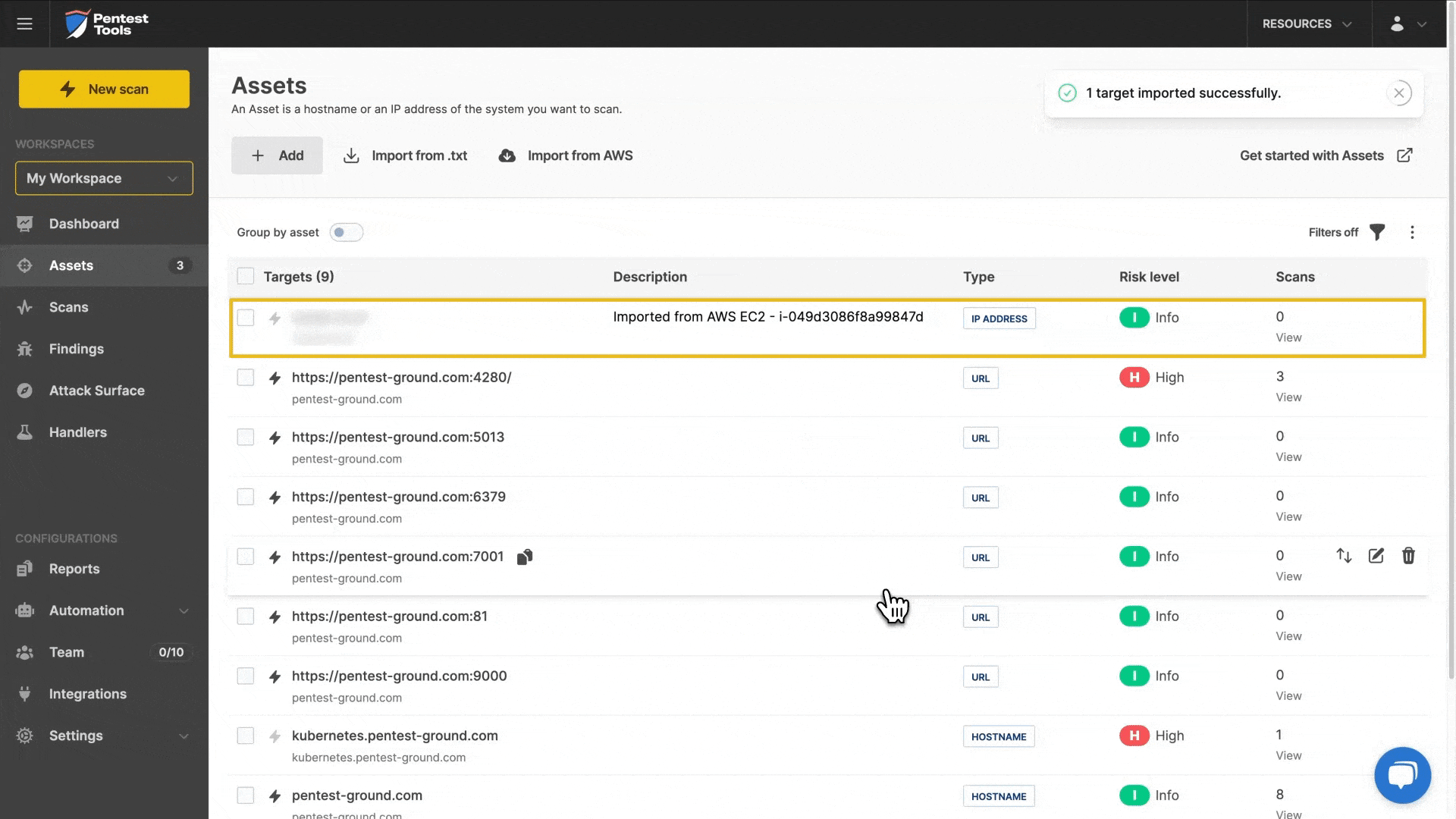
A LOT more than we can summarize here happened in 2024 and our change log is always there if you want to browse through or dip into details.
2024 pentest tools benchmarks & hacker collabs
Which vulnerability scanners actually deliver when it counts?
Our 2024 benchmarks put them to the test against realistic vulnerable testbeds - separating signal from noise. Plus, you got to watch pros like John Hammond and NahamSec stress-test Pentest-Tools.com in live hacking and bug bounty recon scenarios. Let’s recap the highlights!
Find out which vulnerability scanners actually deliver
Tired of vendor claims that don’t hold up in the real world?
Our 2024 vulnerability scanner benchmarks cut through the noise with hard data, so you know exactly which tools can handle real-world threats.
Network vulnerability scanners benchmark 2024 - our Network Scanner set the bar high, leading in accuracy across 167 vulnerable environments, especially for remote CVE detection. Nuclei edged out Qualys for second place in spotting remotely exploitable flaws, while Nessus fell short, revealing a 55.09% availability rate but only 18.56% accuracy.

Web app vulnerability scanners benchmark 2024 - Acunetix dominated complex testbeds like Broken Crystals (REST APIs, JWT flaws, SQLi), while Burp Suite led on DVWA, catching 29 out of 39 vulnerabilities. Our Website Scanner held steady in second place across both tests, balancing coverage and precision. Meanwhile, ZAP flagged 88 false positives on DVWA—proof that noise can still drown out real threats.

Wondering how we tested the tools? Eager to see the comparisons? Use the links above to see the full materials (no personal data required to download them).
Watch John Hammond test-drive our toolkit
So this was pretty cool!
What started as a paid collaboration with John Hammond turned into a full-blown product walkthrough (which we didn’t plan for but are SO glad happened!).
This is your chance to see how an industry pro uses Pentest-Tools.com and why Sniper Auto-Exploiter seems to have made quite an impression:

NahamSec uses Pentest-Tools.com for bug bounty hacking
How do you zero in on the assets really worth your hacking energy and focus?
The awesome NahamSec explains how he combs through hundreds of domains that branch into even more subdomains to find targets with the highest potential of having a bounty-worthy vulnerability (which he actually finds)!
Check out his video, which we had the pleasure of sponsoring:

2024 events and community support
We kicked off the year by supporting UNbreakable Romania, a national competition for high school and university students who want to pursue cybersecurity as a career. Six of the winners of the individual contest qualified directly for the Romanian Cyber Security Challenge 2024 Final and everyone walked away with tons of valuable knowledge!
In March, part of our team travelled to Cluj-Napoca for the first edition of Security BSides Transylvania, where we made new friends and reconnected with old ones.
Spring was also a mentoring season for some of our colleagues, who became guides for the young startup founders working through the intense Innovation Labs program. This program is particularly special to us as it was the first important milestone in the history of Pentest-Tools.com: we got our first award here, taking home the Grand Prize and an even stronger incentive to build a great product for our customers.
In May, two of our colleagues Iulian Birlica and Razvan Pricop took the stage at PeakIT to talk about the untapped potential of DAST tools. They taught fellow practitioners how to integrate dynamic security testing into their CI/CD workflows to boost security without sacrificing speed.
Come the end of May, we were thrilled to sponsor NahamCon, whose 2024 hosts were John Hammond, Joel Margolis, and Justin Gardner! Special props go to Ben Sadeghipour for the community he's built and all the people he's been supporting on their way to bug bounty and ethical hacking growth!
We couldn’t miss a London getaway for Infosecurity Europe in June, an experience packed with great people and persistent reminders about moving on from PDF reports to interactive custom dashboards, staying on-prem (or moving back to it), and attack surface monitoring woes.
Some of our colleagues became teachers and mentors over the summer for Security Summer School in Bucharest. They shared their experience with building Pentest-Tools.com, helping their students develop new cybersecurity skills and knowledge they can actually use in real life.
Two of our team members travelled to Las Vegas for Black Hat US and DEF CON 32, where they met John Hammond and Nikhil Mittal, whose Active Directory pentesting training our Head of Professional Services attended while studying for his CRTP certification. Getting together IRL with Vivek Ramachandran was equally exciting, with his generous demeanor just as vivid offline as it is online!

In October we levelled up our business and growth skills at How to Web, as we believe it’s important to match our passion for cybersecurity to an equally dedicated way of building a product and a business that speaks to our values and principles.
Almost at the same time, other colleagues traveled to Paris for Hexacon, which we also had the pleasure of sponsoring this year. The innovative spirit that defines both French culture and the hacking mindset meshed into a great experience rich in technical deep-dives. It was definitely inspiring for our own security researchers!
And of course we wrapped up the year with a roam around our favorite hacker playground: DefCamp 2024! Through the steady pings of shared knowledge, we rewarded curious hackers with exclusive swag, attended fascinating talks, and made awesome new memories!

Plus, this year, our colleagues Alex Postolache and Catalin Iovita presented their research on fuzzing the most popular server-side HTML sanitizers to see how they handled a tags with an unexpected structure.
We’ll soon publish their talk on our Youtube channel, where we have over 200 videos on topics ranging from how to run authenticated web app scans to how to do a full pentest with Pentest-Tools.com on a free target (you can also use!) to how our offensive security services work.
Let’s wrap it up and get some R&R
2024 was about building smarter workflows, sharper tools, and stronger connections with the cybersecurity community. From powering over 6.3 million scans to launching new features like the Kubernetes Vulnerability Scanner and People Hunter, we focused on making vulnerability management faster, easier, and more effective.
As we head into 2025, expect even more automation, accuracy, and innovation to help you stay ahead of threat - and make your work count.
Thank you for being part of our journey and have a peaceful end of your year!













