How to do a Basic Website Vulnerability Assessment with Pentest-Tools.com
- Article tags
Let’s see how to perform a basic security evaluation of your web application with the tools from Pentest-Tools.com.
The outcome of this assessment will be a rough security posture of your web application and you will also get the chance to see the capabilities of the platform in terms of web security testing.
Here are the main topics of this article:
1. Getting started
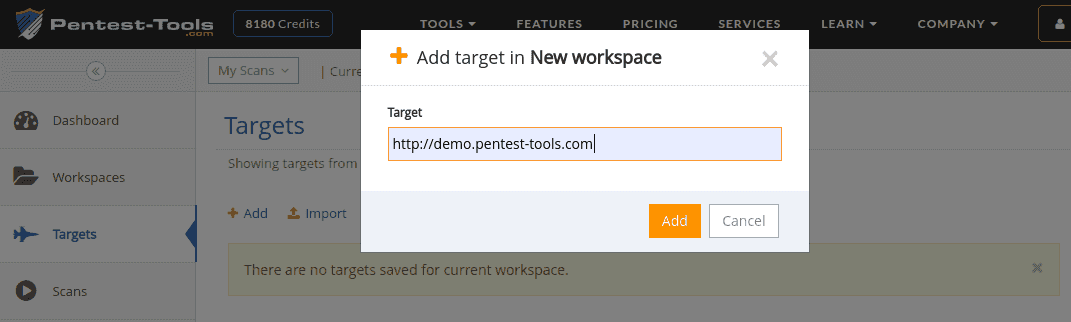
First, you need to add your target URL(s) on the Targets page. You can add targets one by one (use the Add button) or import multiple targets from a text file.
2. Choosing the tools
For a basic web application assessment, we recommend you to start with the Website Vulnerability Scanner, which is a comprehensive tool that tries to discover a broad range of specific web application vulnerabilities (ex. SQL Injection, XSS, Directory Listing, detection of sensitive files, outdated server software and many more). You can see the complete list of tests performed on the tool’s web page – scroll down to the Technical Details section.
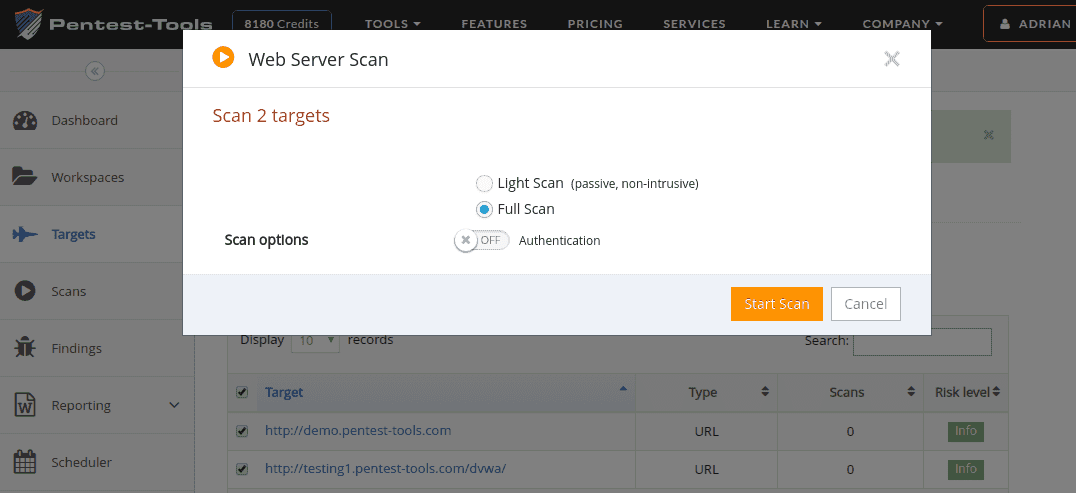
The Website Vulnerability Scanner can perform a Light scan and a Full scan (will be detailed below). Please note that the Full scan already tests for SQL Injection and Cross-Site-Scripting so it is not necessary to run the other tools on tops like the SQLi Scanner or XSS Scanner.
For more advanced tests, you should try more focused tools such as the URL Fuzzer and specific CMS tools like WordPress Scanner, Drupal Scanner, etc.
3. Light scan versus Full scan
You can see that many of our tools have two scan types: Light and Full. The Light scans are designed to be used whenever you don’t want to raise any alarms. They are mainly passive, performing just a few legitimate requests against the target system. However, as you can expect, the Light scans don’t go into much depth and they just scratch the surface in terms of security testing.
The Full scans go into much more depth and they attempt to cover all the attack surfaces of the target system (crawl the application, discover hidden files, use many more attack vectors, etc). A full scan contains all the tests performed by a Light scan so it is not necessary to run them both.
Running a Full Website Vulnerability Scan
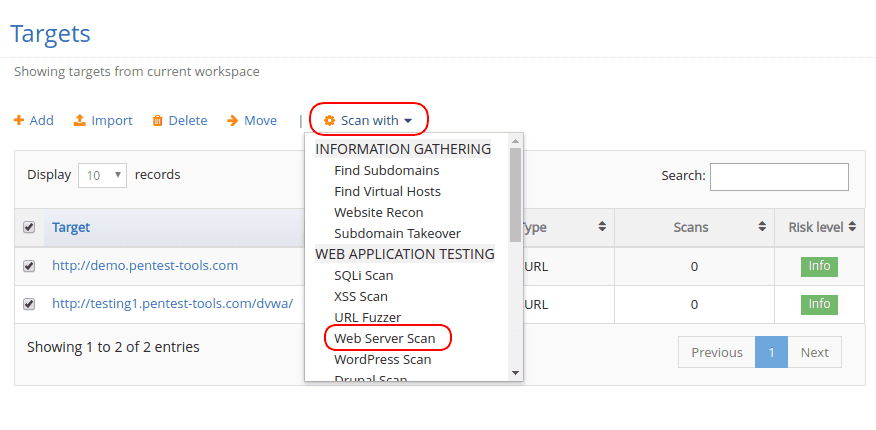
Starting a Full Website Vulnerability Scan is just a matter of going to the Targets page. Select which targets you want to scan, then choose the tool from the ‘Scan with’ dropdown. Note that you can easily start scans against multiple targets at once, which is useful for bulk scanning.
user/password authentication
cookie authentication
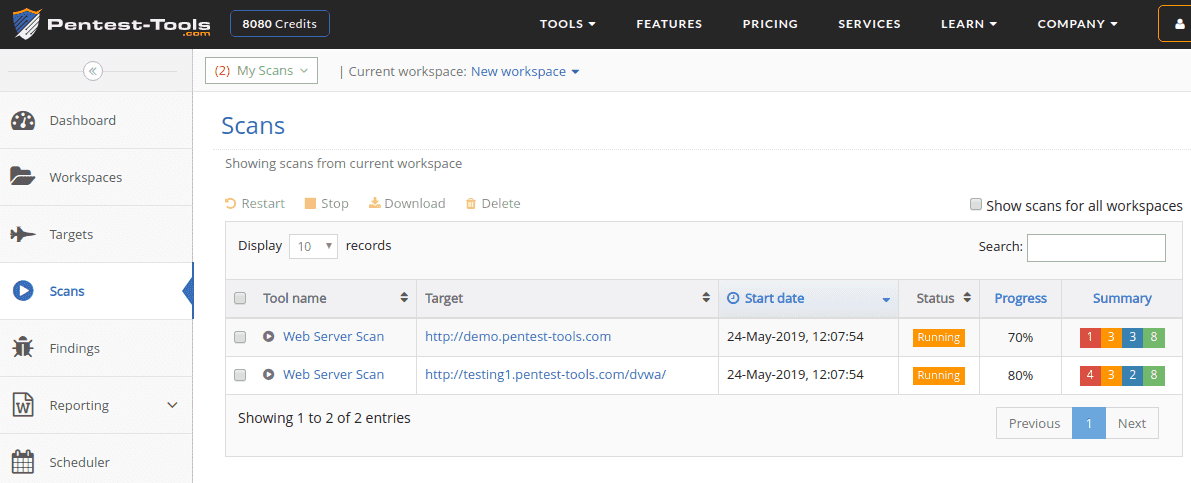
Viewing the Scan Results
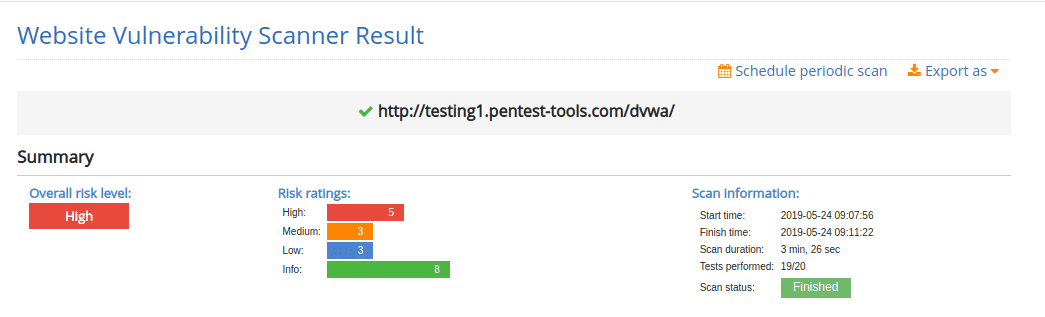
The result of a vulnerability scan contains a short summary of the findings followed by a section with the finding details. Here you can see the results against an instance of DVWA (Damn Vulnerable Web Application), which contains numerous intentional web vulnerabilities:
Vulnerability Details and Recommendations
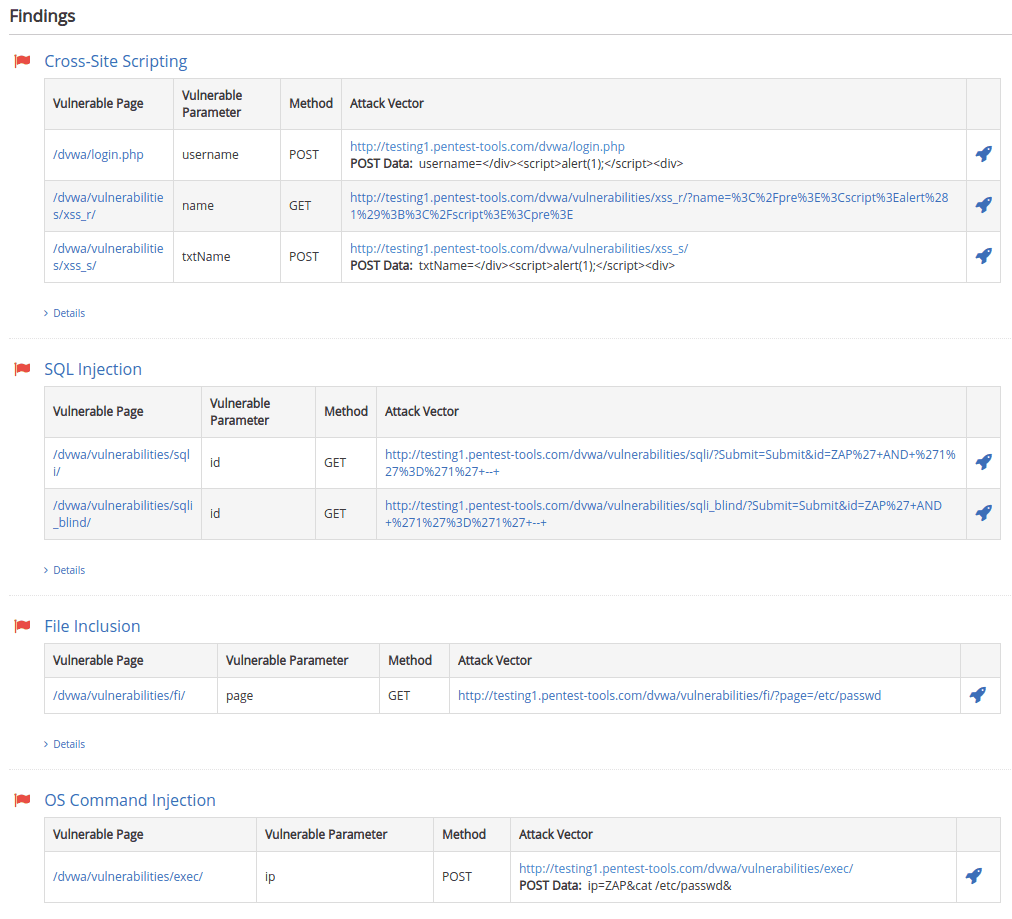
All vulnerabilities returned by the Website Vulnerability Scanner contain detailed Risk Descriptions and a Recommendation section which allows you to easily understand the vulnerability and learn how to fix it.
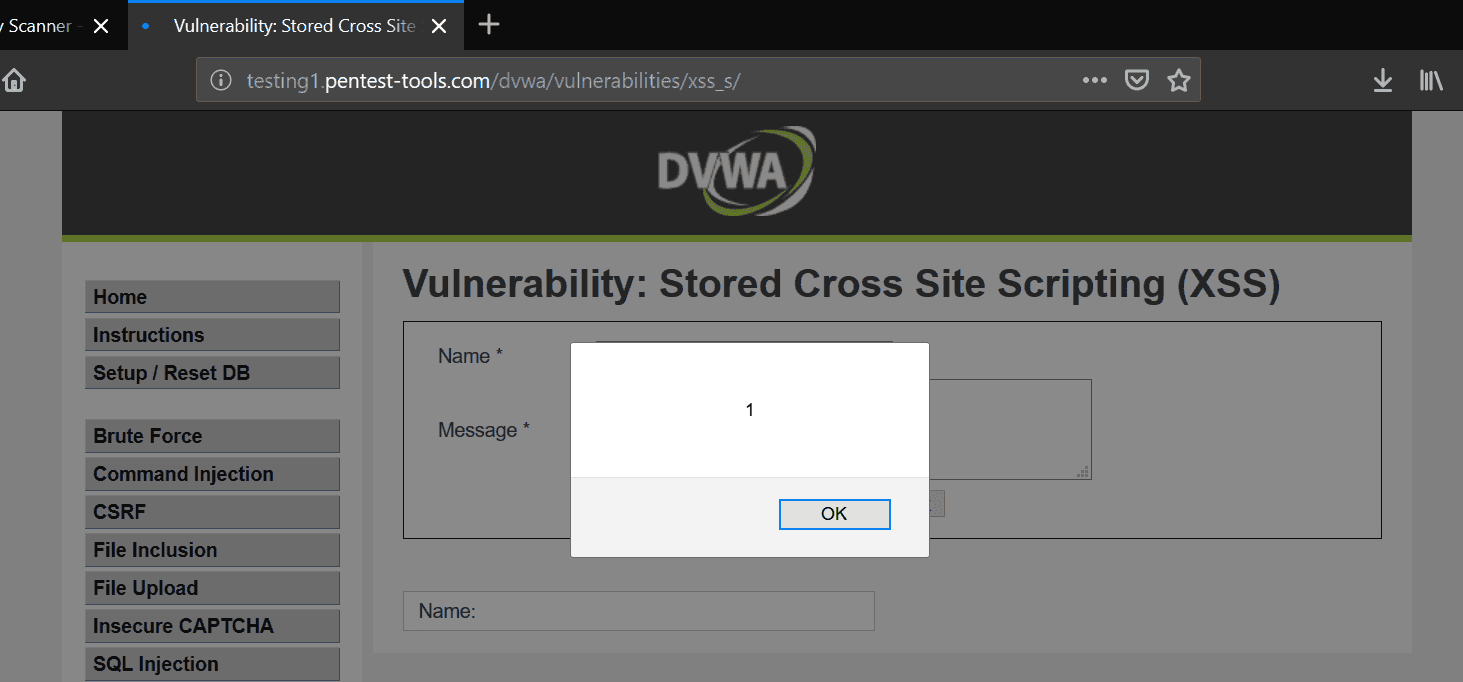
Furthermore, the evidence for the vulnerability also contains the Attack Vector which you can use to trigger the vulnerability and validate it. Here is an example of how to trigger the Cross-Site Scripting on a vulnerable form using the POST method. You need to click on the rocket sign and the POST request will be done automatically against the target application with the attack parameters prefilled.
Reporting Capabilities
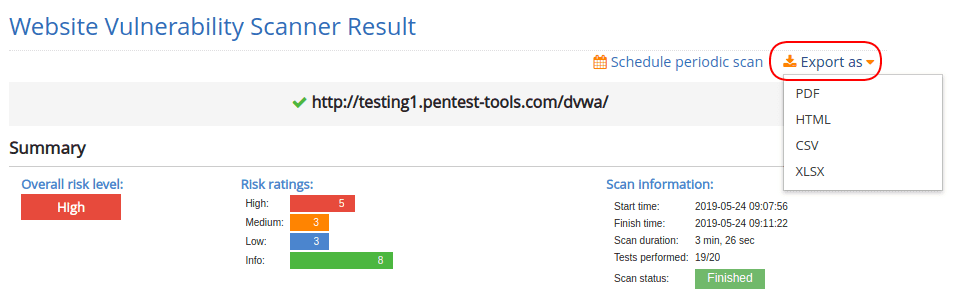
You can download simple reports as PDF or HTML, which contain the result of a single scan against a single target.
However, the platform also has an Advanced Reporting capability which you can use to generate editable Docx reports with the findings from all the targets in the current workspace. Read more in the Advanced Reporting Page and this blog post Pentest Report Writing in 5 Minutes.
The simple report can be obtained by pressing the ‘Export as’ dropdown and choose the desired format.
4. Learn to do a basic vulnerability evaluation with Pentest-Tools.com
This article has just scratched the surface of what you can do with Pentest-Tools.com, the online platform for penetration testing and vulnerability assessment.
There is much more to it, from advanced information-gathering tools to network infrastructure testing and exploitation tools.
Check out our Pricing page to get full access to the platform.