SQL Injection Scanner
Our scanner crawls your app, tests inputs with real SQL payloads, and flags exploitable vulnerabilities you can fix immediately. Paid plans unlock deep SQL Injection scanning with additional options.
- Scan type
Light scan
This specialized free tool shows results and findings that are a part of the premium Deep Scan version of our proprietary Website Scanner. If you'd like to try it, check out our paid subscriptions.
Our scanner crawls your app, tests inputs with real SQL payloads, and flags exploitable vulnerabilities you can fix immediately. Paid plans unlock deep SQL Injection scanning with additional options.
Reporting
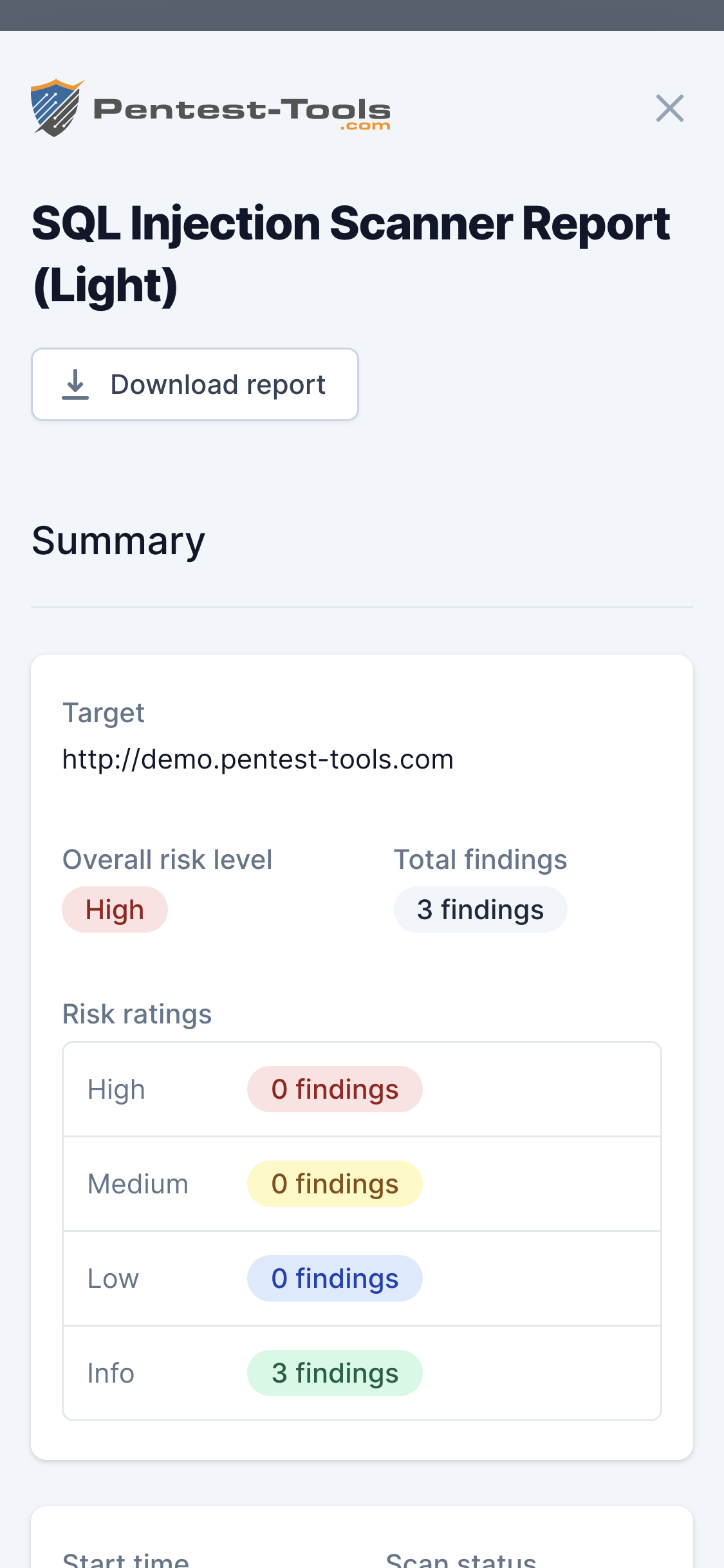
Sample SQL Injection Scanner report
Here is a sample report from our SQL Injection Scanner that gives you a taste of how our tools save you time and reduce repetitive manual work.

How to use the pentesting tool
Use Cases for SQL Injection Scanner
The online scanner identifies SQL Injection vulnerabilities found in web applications by crawling and performing a deep inspection of web pages and parameters. Here are various ways to use the SQL Injection scanner powered by the Pentest-Tools.com proprietary scan engine to make your pentests faster and more effective.
Website Penetration testing
Security Self-Assessment
Third-Party Website Audit
Better vulnerability discovery.Faster pentest reporting.
Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.