Drupal Scanner
Technical details
This is a custom scanner that implements all the security checks performed by known Drupal scanners such as CMSMap or Droopescan but also adds new security tests on top.
The list of tests performed by the Drupal vulnerability scanner includes:
- Fingerprint the server software and technology
- Fingerprint the Drupal installation
- Find installed Drupal modules
- Find the current Drupal theme
- Search for vulnerabilities affecting the current Drupal version
- Check for directory listing
- Search for default install files
- Verify the communication security (HTTPS settings)
- Attempt user enumeration using Views module
- Attempt user discovery using Forgot Password
- Check if the login page is accessible
- Check if user registration is enabled
Parameters
| Parameter | Description |
|---|---|
| Target URL | This is the URL of the Drupal website that will be scanned. All URLs must start with http or https. Don't forget to specify the complete path to the base directory of the Drupal installation (if it exists) e.g. http://targetdrupal.com/path/. |
How it works
The scanner performs a series of passive and active checks to identify the Drupal version, modules, themes, and the current system configuration.
Furthermore, the Drupal core vulnerabilities are extracted from a local database which is periodically updated with the latest vulnerabilities which affect Drupal. The vulnerabilities are reported according to the identified Drupal version.
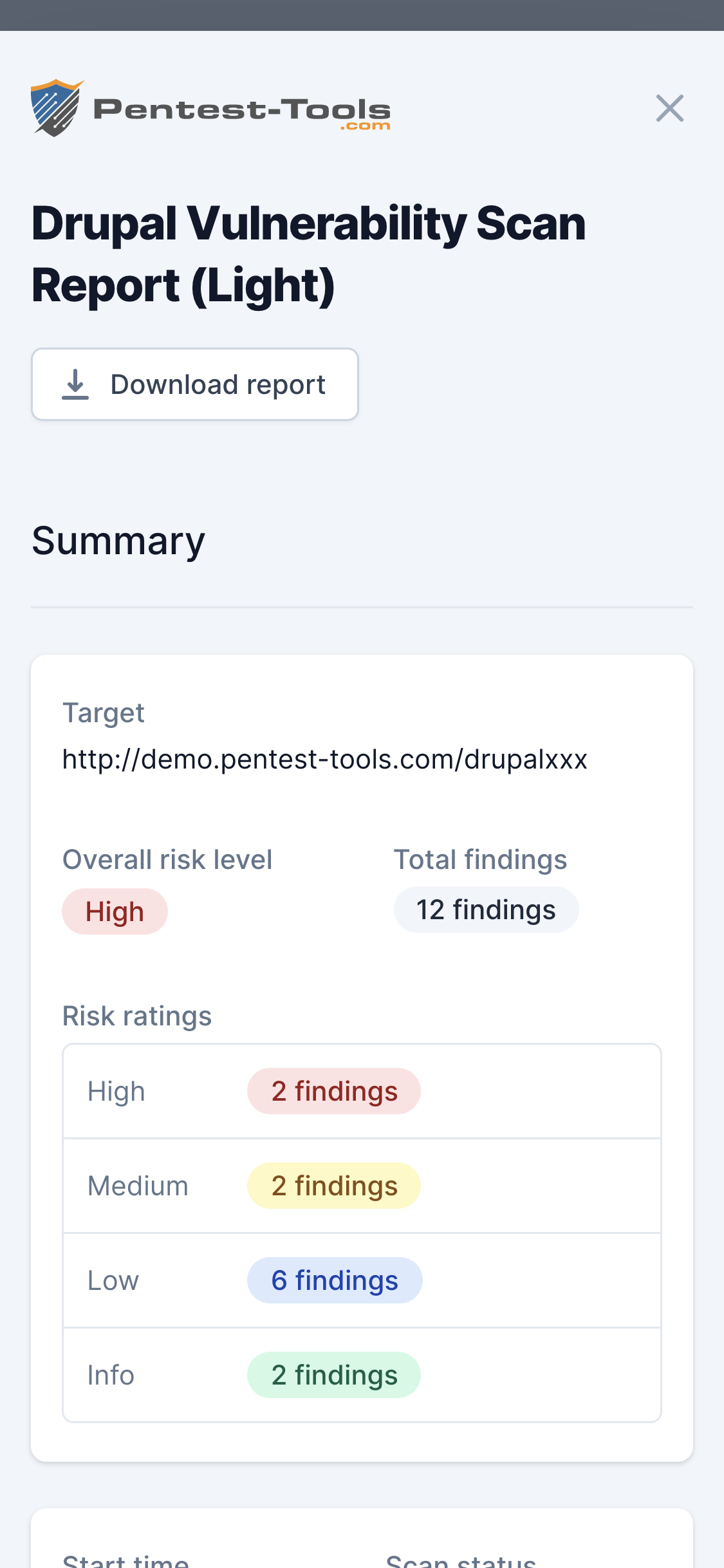
See the Sample report for a detailed output of the scanner.