How to automate vulnerability detection & reporting for SOC 2
July 9, 2025
11:00 AM EDT / 8:00 AM PDT / 4:00 PM BST

Highlights from the session
Everyone was on deck
From leadership to marketing, the team came together to host our first webinar - CEO Adrian Furtuna, Product Manager Dragos Sandu, and Product Marketer Mario Popescu.

Thanks for joining us from across the globe
There were over 78 of you from over 14 different countries
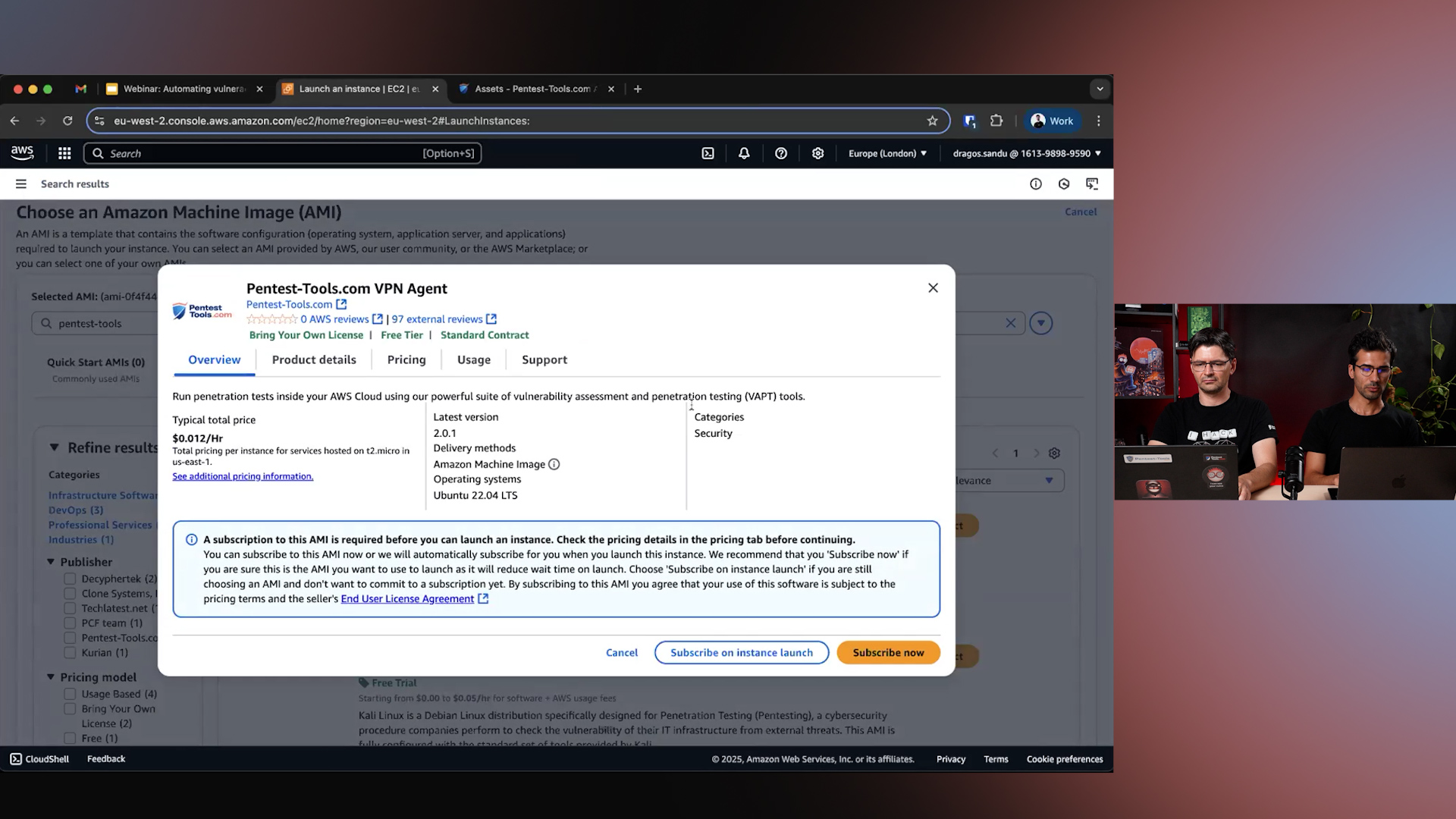
Hands-on from the start
Adrian and Dragos took the lead in setting up the Pentest-Tools.com VPN Agent from the AWS Marketplace.
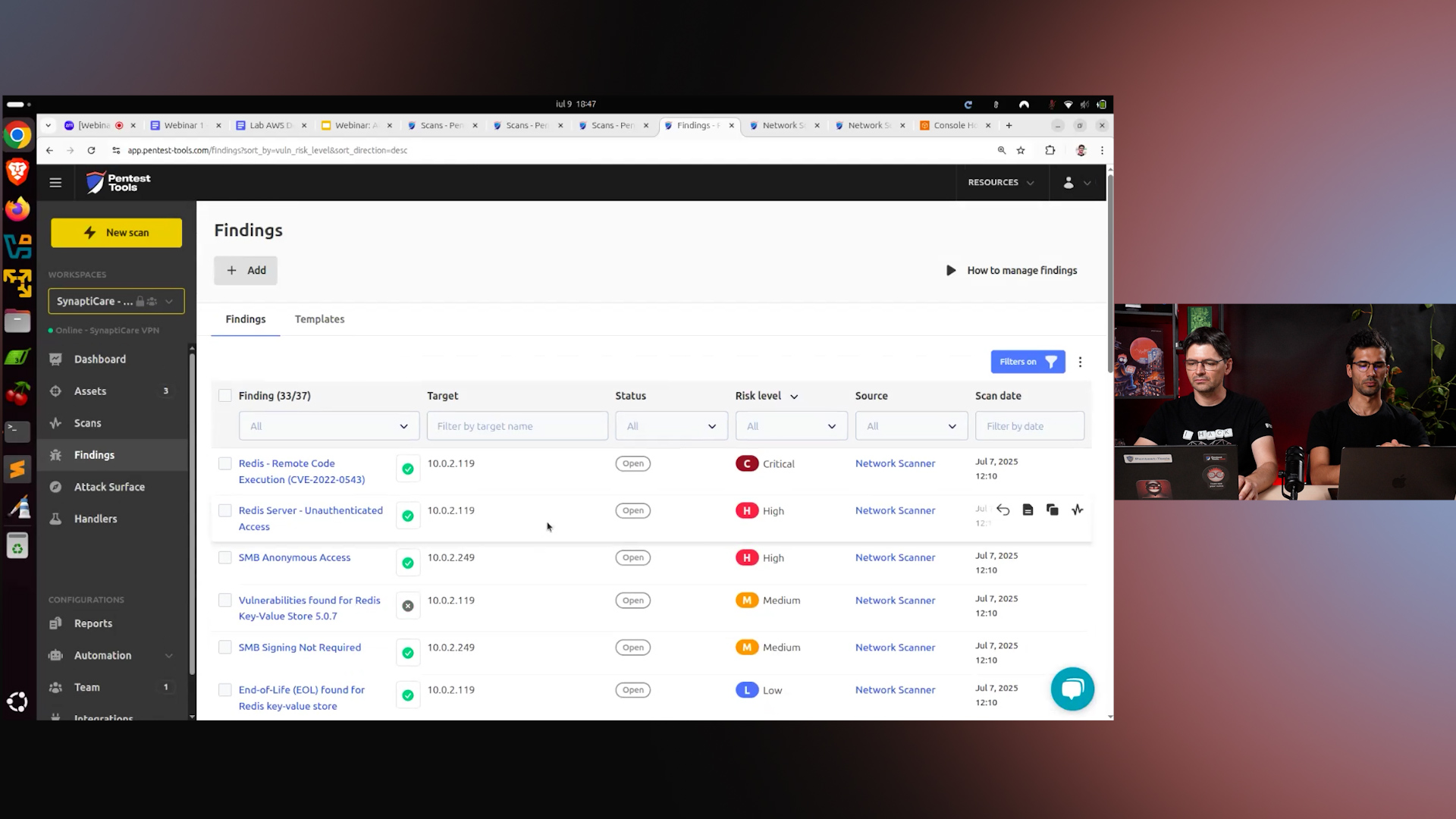
From scan to insight
During the webinar, the team walked through the findings page, showcasing critical and high-severity vulnerabilities identified by Pentest-Tools.com.
What you’ll learn
Chasing vulnerabilities manually doesn’t scale — especially when SOC 2 audits are on the line.
In this live webinar, you’ll learn how to build an automated vulnerability detection and reporting workflow that fits private cloud environments and meets SOC 2 requirements.
We’ll show you how to:
Discover internal assets behind firewalls
Run validated scans that cut through noise
Deliver audit-ready reports without the manual grind
Live demo included
Built for security consultants, MSPs, and internal teams who care about speed, accuracy, and staying compliant.
Speakers

Adrian Furtuna
Founder & CEO
Using his deep technical expertise and 20+ years of hands-on IT security work, Adrian Furtuna founded and built Pentest-Tools.com. He enjoys building and breaking stuff (mostly related to infosec). He also teaches penetration testing classes, does bug bounty hunting, and speaks at international security conferences (Hack.lu, ZeroNights, Hacktivity, DefCamp, OWASP).

Dragos Sandu
Product Manager
Starting his career in code, Dragos moved into Product Management to better connect technical capabilities with real-world user challenges.
For over 5 years he has been shaping the product at Pentest-Tools.com to match real customer needs and help clients navigate a highly complex technical landscape with constantly expanding needs, while building a deep, nuanced understanding of the cybersecurity ecosystem, along with its drivers and pervasive challenges.
Why it’s worth your time
This isn’t a sales pitch
It’s a live, realistic walkthrough of a vulnerability management workflow used by real security teams in private cloud setups.
You’ll walk away with practical tips you can actually use
Whether you're prepping a client for an audit or tightening up your own internal process, these insights will apply.
Couldn't make it live?
No problem! Here's the full recording for you to pause, rewind, or share with your team







