Quickly catch critical unpatched vulnerabilities with a full web app pentest toolkit
Pentest-Tools.com helps you assess the security posture of your web applications with the right level of automation for faster workflows, richer results, and more time for creative manual hacking.
20+ tools that detect fresh critical vulnerabilities so you can confirm your hypotheses quicker
A constantly updated proprietary Website Scanner designed for accuracy, speed, and depth (with automatic validation that minimizes false positives)
Authenticated scanning and attack simulation to find vulnerabilities only logged-in users face
Continuous monitoring so you don’t miss any new issues in your web app ecosystem
Watch the demo
Follow an in-depth walkthrough of our web app pentesting tools in action, alongside Caido and others.

Discover all that’s critical in the first run
A single toolkit to assist you with your entire web app pentesting workflow
From recon to reporting, we’ve got all the pentesting steps covered! Find high-impact security issues without switching between multiple tools.
Cost-effective resource management, unified and correlated results
Manage all your findings, reports, historical data, and more - in one place! No need to pay for more tools, more computing power, or more resources.
Highly accurate and up to date
Stay on top of versioning, critical CVEs, and misconfigurations with our constantly updated and optimized web app pentesting toolbox. Bonus: our proprietary Website Scanner scores on par with the top industry tools, according to our website vulnerability scanners benchmark.
Black box and gray box testing
Simulate both unauthenticated and authenticated attacks for more in-depth findings and increased coverage.
Pentest-Tools.com supports you at every stage of your web app pentest
With Pentest-Tools.com, you’ll gain a toolkit that boosts every stage of your assessment:
Recon: Website recon, Subdomain Finder, Virtual Hosts Finder, WAF Detector, URL Fuzzer, and more.
Vulnerability scanning: Website Scanner, API Scanner, Network Scanner, and more.
Vulnerability exploitation: SQLi Exploiter, XSS Exploiter, HTTP Request Logger.
Attack surface mapping to uncover weak spots at a glance.
Automated, custom reporting to document your findings faster, including one-click imports from Burp Suite for complex workflows.
Spend less time on repetitive pentesting tasks and more time breaking things creatively
Get recon insights faster with automated discovery
Quickly map your app’s attack surface
Use the Pentest-Tools.com scanners to detect the target’s technologies (versions, modules, WAF, etc.), indexed sensitive data, hidden files and directories, login interfaces, related subdomains, and more. Go deeper into the app’s business logic with our automated attack surface mapping.
Dig deeper into the web app’s functionalities
Detect API endpoints, check if other services use the same server, and even search for associated employees’ data exposure (names, emails, roles). Get a comprehensive view of the target’s potential weaknesses, at a granular level.
You'll need:
Network Vulnerability Scanner
Website Vulnerability Scanner
Google Hacking
URL Fuzzer
WAF Detector
Subdomain Finder
Port Scanner
People Hunter
Scale vulnerability discovery with comprehensive tools
Identify a wide range of web application vulnerabilities
Scan both standard applications and SPAs for any critical issues. Detect SQLi, XSS, exposed plugins, config backups, outdated server software, OS command injections, HTTP request smuggling, template and code injections, and many more vulnerabilities affecting your web app.
Detect server-side vulnerable components
Our toolbox helps you uncover critical version-based CVEs, service misconfigurations, and weak credentials in minutes. Know what to focus on next, without the noise.
You'll need:
Exploit and validate the right high-risk findings
Validate your vulnerability hypotheses and get the proof of exploitation you need for any CVEs, SQLi, XSS scenarios, and other critical findings. Check the low hanging fruit first, so you use your resources for creative manual pentesting.
You'll need your offensive hacking skills +
Build clear and actionable reports in minutes
Once you’re satisfied with the scan results and findings, automatically generate reports for your internal and external stakeholders with just a few clicks. Use our advanced reporting templates with pre-filled executive summaries, vulnerability and remediation information, or leverage our white label capabilities.
You'll need your unique security knowledge + our Report builder + our Burp Suite extension for issue imports
Catch new threats with continuous monitoring and integrations
Keep a close eye on your web app’s security posture with our scheduled scans and monitoring features. Integrate alerts and scan findings into your preferred channels — we support Jira, Slack, Discord, webhooks, Vanta, and many, many more. Don’t lose track of what’s critical!
You'll need Scheduled scans + Monitoring + your preferred channel (Jira, Slack, Discord etc.)
How customers use Pentest-Tools.com for web app pentesting

Overall a best tool for pentesting
This product is simple yet very powerful. They have wide range of tools used for Web Application pentesting, from recon to exploit. Helped secure environment with rigorous testing and quick results. Their Internal scanning is very powerful and identified hosts within restricted environment. The reporting is well made and executive summary is very intuitive with visual figures. Overall a best tool for pentesting.
IT Manager
Web app vulnerability scanning with high accuracy
Get all the data you need to make an informed decision about your DAST security tool. Our research team developed 2 benchmarks to help you zero in on the best scanner for the job
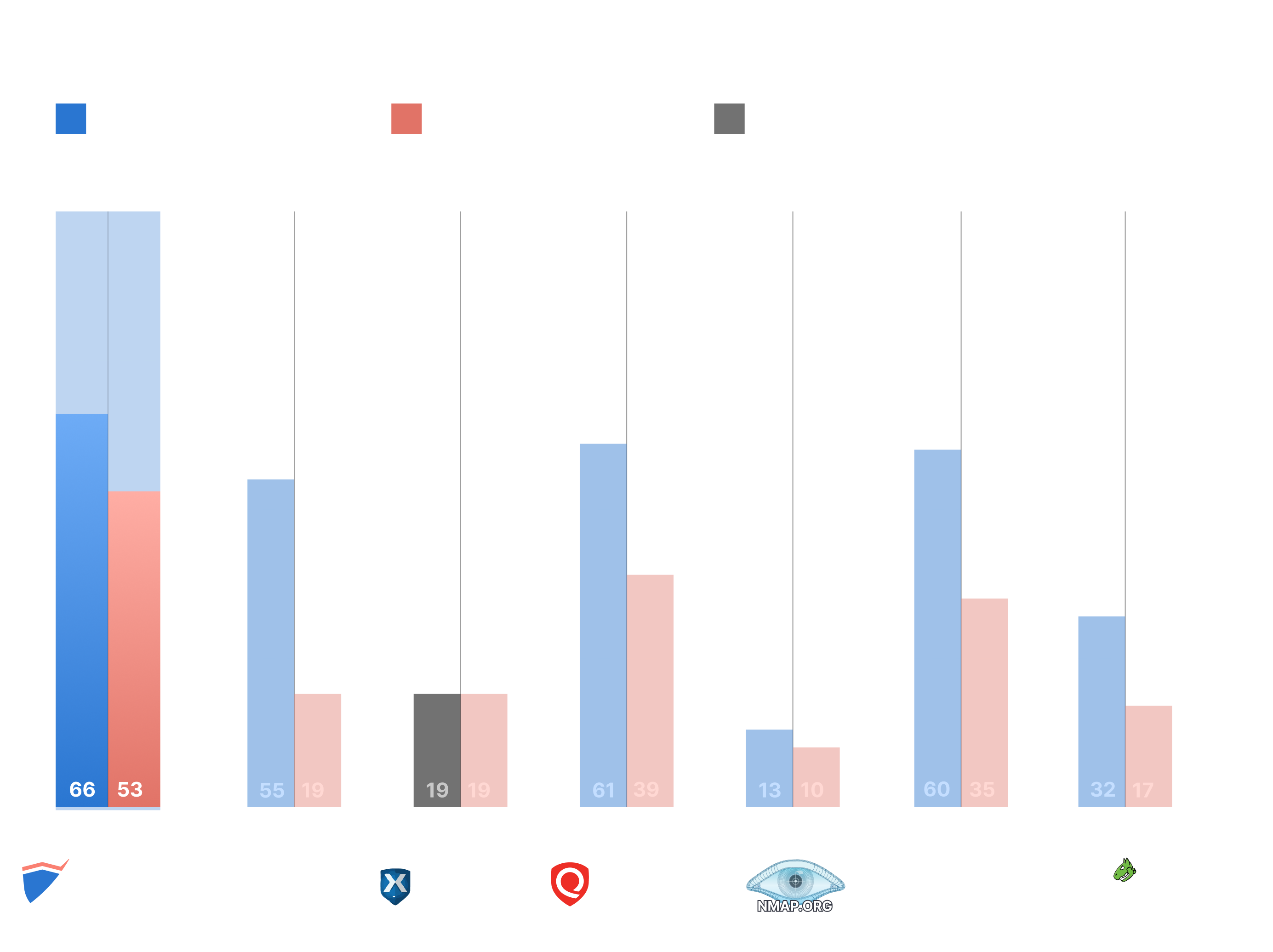
Website vulnerability scanners benchmark
This benchmark compares the 6 best website scanners against 2 independent testbeds (DVWA & Broken Crystals) and 107 vulnerable paths.

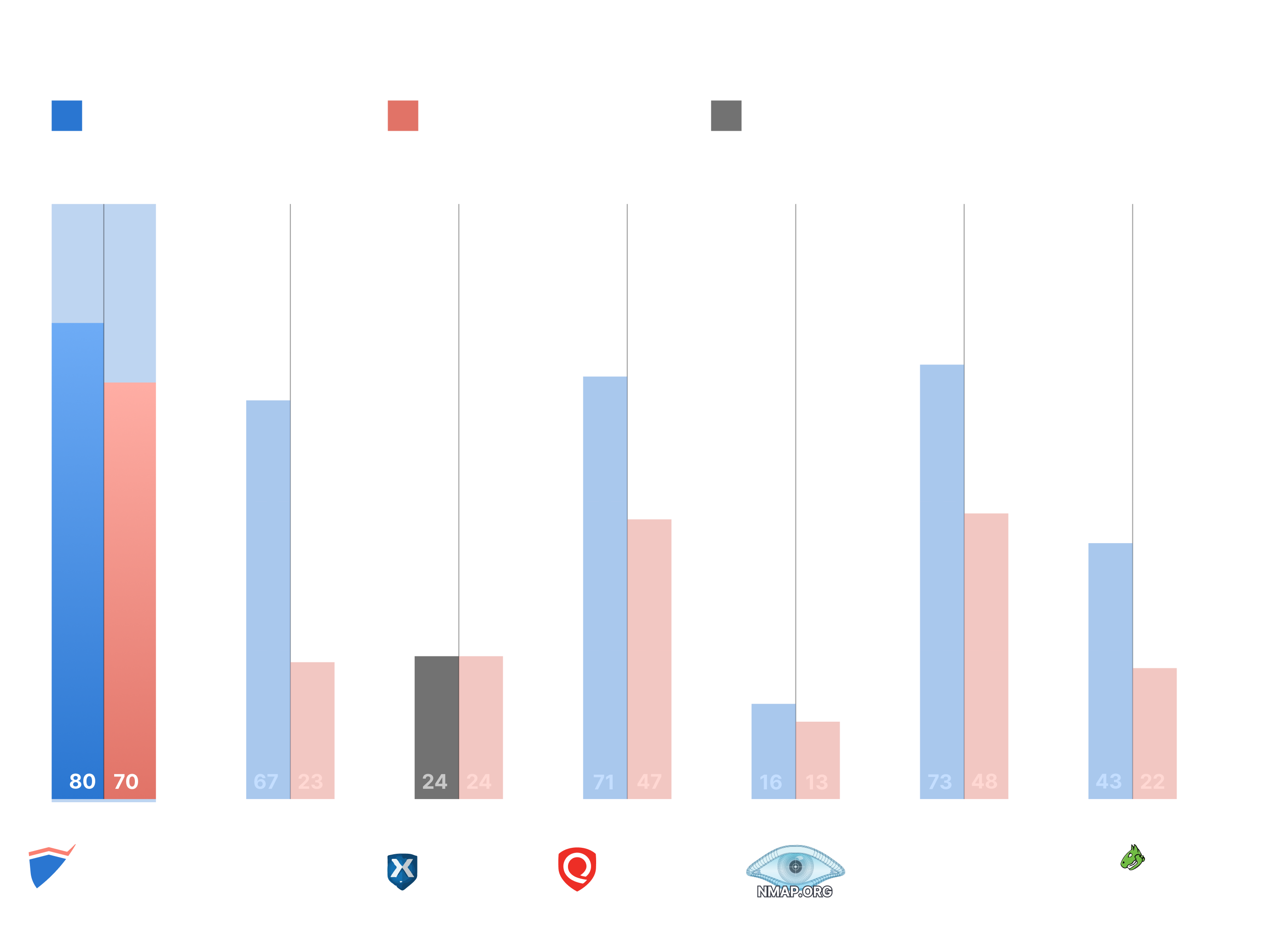
Network vulnerability scanners benchmark
This benchmark compares 7 of the best network scanners across 167 vulnerable environments to help you understand their detection capabilities and limits.
See detection availability and accuracy rates across 128 environments with remotely detectable CVEs and 39 environments with non-remotely detectable CVEs.
Ready to start pentesting web apps with Pentest-Tools.com?
Surface hidden vulnerabilities, missing patches, and misconfigurations with our extensive Pentest-Tools.com toolkit.
More reasons to use Pentest-Tools.com for your pentesting engagements
20+ tools for efficient security testing
Unauthenticated recon and deep authenticated testing
Unified findings and reporting management
Pentest robots for custom, automated testing flows
API access for large-scale testing and custom dashboards
Cloud-first product that supports your resource-intensive workflows
Team collaboration with shared workspaces
Continuous security monitoring with scheduled scans and custom alerts
Web app security testing resources
![Comparing the BEST Website vulnerability scanners [2024]](/_vercel/image?url=https:%2F%2Fcontent.pentest-tools.com%2Fassets%2Fcontent%2Fwvs-benchmark---yt-thumbnail.png&w=1536&q=100)
FAQs: using Pentest-Tools.com for web app pentesting
What differentiates Pentest-Tools.com from other solutions that assist security practitioners with web app pentesting?
Pentest-Tools.com provides a comprehensive toolkit for end-to-end web app pentesting that combines our automation with your manual control, ensuring you find high-impact vulnerabilities faster and with greater accuracy.
Our proprietary Website Scanner rivals top industry tools in accuracy and depth, eliminating false positives with automatic validation. Plus, our toolkit can improve the speed and accuracy with which you perform recon, vulnerability scanning and exploitation, reporting, and continuous monitoring, so you can manage everything in one place without switching between tools and data sources.
What web app pentesting methodologies does Pentest-Tools.com support?
Our platform aligns with industry-standard penetration testing methodologies, including:
With black-box and gray-box testing capabilities, authenticated scanning, and attack surface mapping, you can conduct a thorough web application security assessment with the right level of automation for you to focus on more creative hacking.
Can I use Pentest-Tools.com to continuously monitor the security of my web apps?
Yes! With scheduled scans, scan diff notifications, and more custom alerts, you can continuously monitor your web app's security posture.
Pentest-Tools.com supports integrations with Slack, Jira, Discord, webhooks, Vanta, and more, ensuring you never miss a new vulnerability or misconfiguration, as soon as it’s detected.
What kind of web applications can Pentest-Tools.com scan for vulnerabilities?
Pentest-Tools.com supports vulnerability scanning for a wide range of web applications, including:
Single-page applications (SPAs)
Traditional server-rendered web apps
APIs
CMS-based websites (WordPress, Joomla, Drupal)
Custom-built web applications
How do I validate web app vulnerabilities with Pentest-Tools.com?
Our product helps you confirm high-risk vulnerabilities efficiently through:
Automated validation embedded in our web and network vulnerability scanners, reducing false positives
Exploitation tools like SQLi Exploiter, XSS Exploiter, and HTTP Request Logger for proof-of-concept (PoC) testing
Remediation steps designed by our research team included in our automated reports
With these capabilities, you can prioritize real threats as you detect them.
Can I generate reports for web app vulnerabilities directly from Pentest-Tools.com?
Absolutely! Pentest-Tools.com offers both exportable scan results and custom reports that can include:
Executive summaries and detailed findings
Clear remediation recommendations
White-label branding for client-ready documentation
Generate relevant reports in minutes and share findings with both internal and external stakeholders effortlessly.
Can I use Burp Suite findings in my Pentest-Tools.com reports?
Yes — with our Burp Suite extension for Pentest Suite users.
You can send selected Audit Issues directly from Burp Suite Professional into your Pentest-Tools.com workspace. Each issue includes key data like severity, port, description, remediation advice, and more. For faster reporting and clearer results!












![Network vulnerability scanners benchmark [2024] - methodology & results](/_vercel/image?url=https:%2F%2Fcontent.pentest-tools.com%2Fassets%2Fcontent%2Fns-benchmark---yt-thumbnail.png&w=1536&q=100)