Use cases
Online Vulnerability Scanner
Hit all your targets with our online vulnerability scanner that's optimized for painless reporting
Right now, security teams and pentesters must pick between a wide variety of diverse, specialized tools. Why? Because purchasing and trialing every tool out there is an unaffordable drain on resources. Selection and compromise are business necessities.
But properly testing new options takes time. Qualitative data from our research suggests it takes as long as a full business quarter to thoroughly assess a single scanning tool. It doesn’t have to be this way every time.
Pentest-Tools.com is an online penetration testing platform that incorporates a range of online vulnerability scanners and features so you don’t need to test or maintain an expensive toolstack. We offer a way to integrate pentesting favorites – from online vulnerability scanners to issue tracking (e.g. Jira), and reporting – so you can reduce your technical debt and maintenance costs.
Pentest-Tools.com is a multi-functional, high-quality toolkit with the must-have usefulness and versatility you need. Our advanced tools and features are designed to elevate your work and expertise through practice.
Multiple target types
Optimized settings
Quality findings
All online security scanners are not equal
Here are a few ways that Pentest-Tools.com supports you to deliver successful engagements and enjoy the process.
Comparison
Other external scanners

Pentest-Tools.com
Range of tools
Setup speed
Pentesting workflow
Types of scans
Reporting options
You need an online scanner with range, flexibility, and impact
The good news is you don't need to find multiple scanners or large chunks of extra time to configure and use them one by one. We built Pentest-Tools.com to provide you with online vulnerability scanners with wide target ranges, adjustable settings, and actionable results.
You need an online vulnerability scanner that matches different target types you have in your engagements. Pentest-Tool.com provides you with a range of web vulnerability scanners that:
- Discover common web app vulnerabilities and identify web server configuration issues
- Find exploitable vulnerabilities in different Content Management Systems such as our online WordPress vulnerability scanner
- Map all services exposed on the network perimeter and discover vulnerabilities relevant to external and internal networks
You can use any of these tools to scan the target application as an authenticated user. And you can perform scans remotely, without authentication, simulating an external attacker.
We also provide scanners with optimized and flexible settings. Our pentesters already configured them with optimal settings for best performance and results. This simplifies and speeds up your workflow and engagements.
And all our scan settings are fully configurable. You can choose between light and deep scans, or whether to skip some initial security checks. You also have the ability to select between different attack options.
An online scanner with comprehensive coverage and specialized settings produces high-quality results. All our scan results are:
Pentest-Tools.com has all the features we need
Prior to Pentest-Tools.com, we used several different tools that performed a wide range of functions for us. Now, we don't use them anymore because we don't need to. Pentest-Tools.com has all the features we need, like API, VPN and network scanning. It reports quickly and well. It maps attack surfaces. And it automates a lot of our manual work
And test the Light version of our free online vulnerability scanner
What online vulnerability scanners do you offer?
We've talked about the wide scope of our vulnerability scanning tools. But what do you get for your investment?
Web Vulnerability Scanners
Network Vulnerability Scanners
Web CMS Scanners
Our tools centre around web vulnerability scanners that discover common web app vulnerabilities (e.g. SQL injection, cross-site scripting, and others in the OWASP Top 10) and identify web server misconfigurations (e.g. missing HTTP headers). You can also use them to scan the target application as an authenticated user.
Next, we have network vulnerability scanners. They map all services exposed on the network perimeter and discover vulnerabilities relevant to networks, like outdated services, missing security patches, and badly configured servers.
Finally, our web CMS scanners find exploitable CVEs in the most popular content management systems, such as our Joomla vulnerability scanner. Our reports include discovered plugins, themes, and information about out of date versions and components.
There are various reconnaissance tools and offensive tools too that help with your discovery and attack surface mapping, so you can identify and prioritize for remediation those security vulnerabilities that malware might use as entry points.
Why security and IT pros are switching to Pentest-Tools.com for online vulnerability scanning
The range of tools and the quality of reports are just two of the compelling reasons why professional pentesters and security experts are investing in Pentest-Tools.com.
- 1
Reliable scan performance and intelligent results
Unreliable vulnerability scanners are the scourge of your security team. They waste valuable time, effort, energy and other scarce resources. You need an online security scanner with tools that work every time and get rigorous updates with detection for new vulnerabilities to provide accurate results.
Pentest-Tools.com has provided online vulnerability scanning tools since we started in 2017. The founder and CEO of Pentest-Tools.com, Adrian Furtuna , is an ethical hacker and pentest team leader, performing technical cyber security projects. Adrian understands the need for a reliable online resource to use for performing security tests and founded Pentest-Tools.com to solve this industry-wide issue.
Our online tools are pre-configured and optimized for performance by expert penetration testers. We update our scanners monthly, to ensure ever more precise detection and performance. And, we're proud that Pentest-tools.com was recognized as a High Performer in G2's Winter 2021 Grid Report.
Quality is one of the three key values around which our company is built.
We don't like poorly written software and unreliable results. That's why we strive to build a platform our users can always rely on.
The support you enjoy from Pentest-Tools.com is another top quality feature of our platform. One of our customers, cyber security researcher Cristian Cornea , not only appreciates the quality of the results, but also the support.
"The team is friendly and amazing, so I know I can get reliable help when I need it."
- 2
All scan settings fully under your control
Pentest-Tools.com provides you with full control over the scan settings for deep scans in paid plans. This includes passive and active checks. (see Website scanner options in the logged-in area.
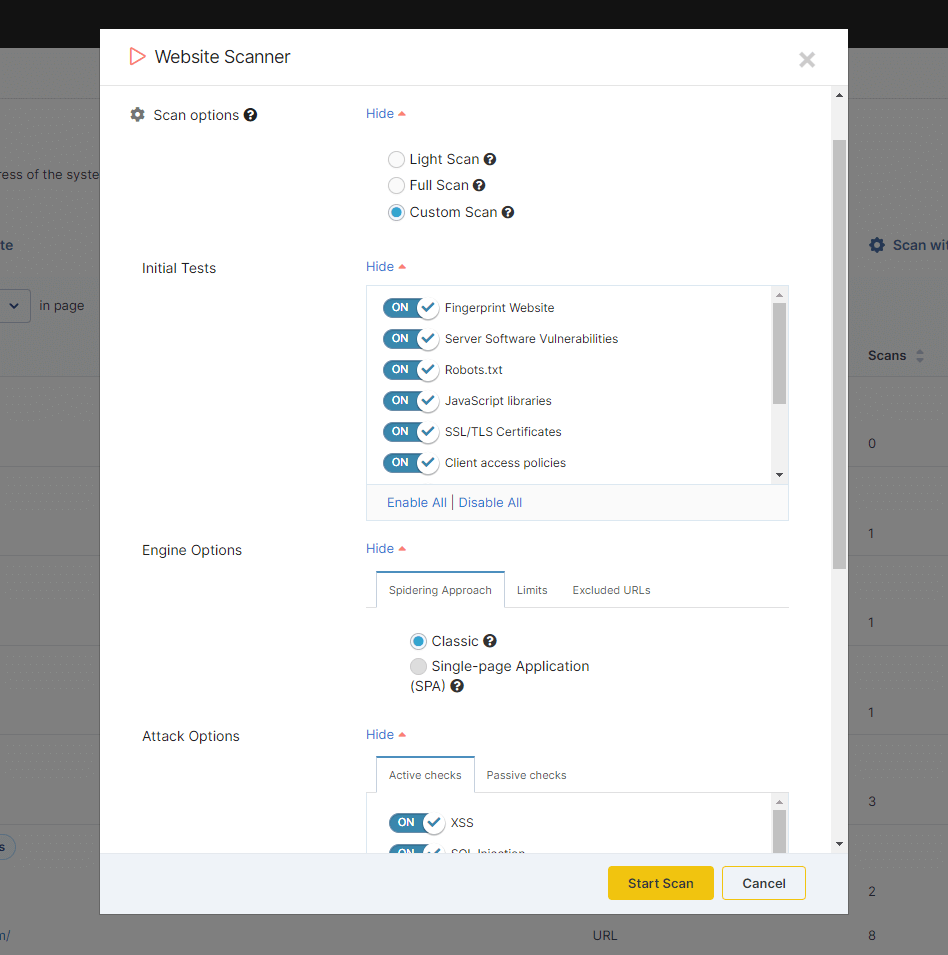
With Pentest-Test.com you can easily reconfigure your scan settings to specific requirements or run more targeted checks.
This flexibility is particularly useful for your scheduled scans. You have complete control over when the scan runs and the timezones involved. You can also control how frequently you receive notifications, and modify the email addresses for those who receive them, saving hours of manual work.
- 3
Authenticated scanning for web apps and networks
An authenticated scanning option is vital for any reliable online vulnerability scanner. The capability to scan web apps as an authenticated user means you can scan websites that require authentication as a logged-in user. You also may need an internal scanning network option so you can scan targets from a private network over VPN.
All Pentest-Tools.com pricing plans include two-factor authentication. When you choose higher tiers, you can scan behind logged-in websites as an authenticated user. You can also scan internal networks by employing the ready-to-use VPN networks to reach internal hosts.
- 4
Full transparency for test lists and other items
The Pentest-Tools.com website vulnerability scanner gives you full transparency over all its technical details. This includes a list of all the tests performed by the Website Scanner for both the light and deep scans. Our report also provides details on the approach and methodology used in the scan.
Transparency is also a feature of our platform's Attack Surface view . This includes a centralized overview of all IP addresses, hostnames, operating systems, services, technologies, and their versions from all your targets. This includes, for example, open ports. Each workspace generates an Attack Surface.
Finally, in the Team tab, under Shared Items, our platform provides a view of the complete list of team members, granted permissions, wordlists, and other shared resources. This gives you a transparent overview of your entire team setup and makes collaboration a lot more effective.
- 5
Predictable and professional online scanning reports
Reports play a major part in the overall scanning service because they incorporate details about the vulnerability details and remediation. It's a major problem when you're researching for an online vulnerability scanner if potential scanners give you no idea what your eventual reports might look like.
Pentest-Tools.com provides a report preview for all online vulnerability scanners. You can also watch a video that shows you how our advanced reporting options work. Pentest-Tools.com reports are fast, accurate, and exportable. An advanced edit option allows you to generate advanced pentest reports in editable format, enabling you to produce a customized 'white label' report for your clients with custom logos, heading, and other elements.

There is a tool for everything, starting from the analysis of the attack surface, to network scanning, and in-depth scans of web application security. We use it as an automatic tool for automatic scans every week to avoid problems and regressions. There are dozen different scanning solutions, they cover all the possible network architectures, technology and scheduling to produce professional reports. The price is excellent and it is almost impossible to have the same quality at the same price.
