Comparison
The expansive Invicti
(formerly Netsparker) alternative
Pentest-Tools.com - defense-piercing tool stack for vigilant pentesters on the hunt
Built from the ground up with the singular perspective of a meticulous pentester
Exceptional tool stack with a surpassing breadth of quality tools from reconnaissance to vulnerability scanning to exploitation
Expansive Invicti alternative that offers flexible automation by chaining tools using pentest robots
A full pentesting arsenal
Does Pentest-Tools.com cut itas an Invicti alternative?
Watch this 3 minute video and learn how to use the platform for penetration testing and vulnerability assessment.

Start your journey here.
I can highly recommend Pentest-Tools
The scope of tests provided is pervasive and covers a lot of potential system vulnerabilities. I was surprised by how many indicators are analyzed by (the) platform. I can highly recommend Pentest-Tools.

Wojciech D.
Head of Acceleration, G2 Review
At a glance
Pentest-Tools.com vs Invicti (formerly Netsparker)
Are you working with SaaS clients as a security consultant or with security teams as an in-house pentester? Then you’ll be delighted with our chained detection and automatic exploitation tools, as well as our transparent and customizable reports for feeding back your findings. Pentest-Tools.com excels with its battery of aggressive vulnerability-seeking tools for online security professionals.
But, since you’ve landed on this page, you may be asking: How good is Pentest-Tools.com? How does it stand up in a side-by-side comparison with Invicti?
Explore the distinctives of each toolset so you can make an informed choice about your next pentesting investment.
Comparison

Pentest-Tools.com

Invicti
Use cases
Range of available tools
Specialized tools
Connected tools
Why security and IT pros prefer Pentest-Tools.com as an Invicti alternative
Pentest-Tools.com helped me scan my home servers to identify security concerns with my deployments. Their continued development and growth have been great to watch. Pen test tools gave me an idea of what issues or security vulnerabilities I was open to. They have an entire suite of tools to test my home environment. Some of my most used features were their website and network scanners, sniper: auto exploiter, various login page tests, and their subdomain finder to help me with subdomains I had forgotten about.
Start using the platform today
Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.

Designed with the pentesting environment in mind
Your role as a security sentinel is complex. You maintain the security posture across multiple attack points across your client’s territory. This involves many website applications, CMSes, firewalls, and networks. To do this, you must venture across the multiple attack surfaces of each target to find its boundaries, then burrow into its center to find its exposed underbelly. You value precision tools and adaptability.
First, you’ll run some of our Reconnaissance tools to determine the scope of your organization’s risk. Depending on the results, you can select the relevant web, CMS or network scanners and exploiters to expose and illustrate the security flaws. During scanning, our Attack Surface view is instantly automatically populated with reconnaissance findings, giving you an overview of the current security posture.
Your next step is to jump straight to our automatically compiled Findings lists, and expand them with manual findings from external sources, if required. Findings windows offer the functionality to filter, interpret, and recategorize, before fixing and rescanning. Then, you can rapidly generate and customize a report, and configure it to be automatically delivered directly to your colleagues or clients. Our reports include pre-filled findings templates listing the risk, its level and recommendation for each detected vulnerability, bundled together with evidence of the finding (including screenshots).
The limitation of Invicti, in contrast, is that it is designed solely for the context of the web application SDLC. The typical user is a web developer whose attention is needed in multiple directions. They are not necessarily familiar with the pentesting environment and its varying concerns. As a result, this places an over-reliance on automated features – such as pre-configured scan policy templates and scan profiles – to close the gap caused by the lack of expertise among some of its users.
Pentest-Tools.com offers a powerful security arsenal with tools you can select, adapt for purpose and wield to great effect in your discerning hands.
Superior, dedicated reconnaissance tools
Though you can conduct a crawl and wait option in Invicti Standard edition, it is simply impossible – without resorting to cumbersome configuration that limits the advanced scan scope settings of a scan policy – to run a reconnaissance scan that zeroes in on one area.
If precisely crafted weapons are what you want to eliminate exploitable weaknesses, then Pentest-Tools.com has several options.
Our Google Hacking tool works well as a launching strategy. It collates target website or domain data from freely available Google dorks sources. You’re bound to uncover a few alarming details to get your adrenaline running.
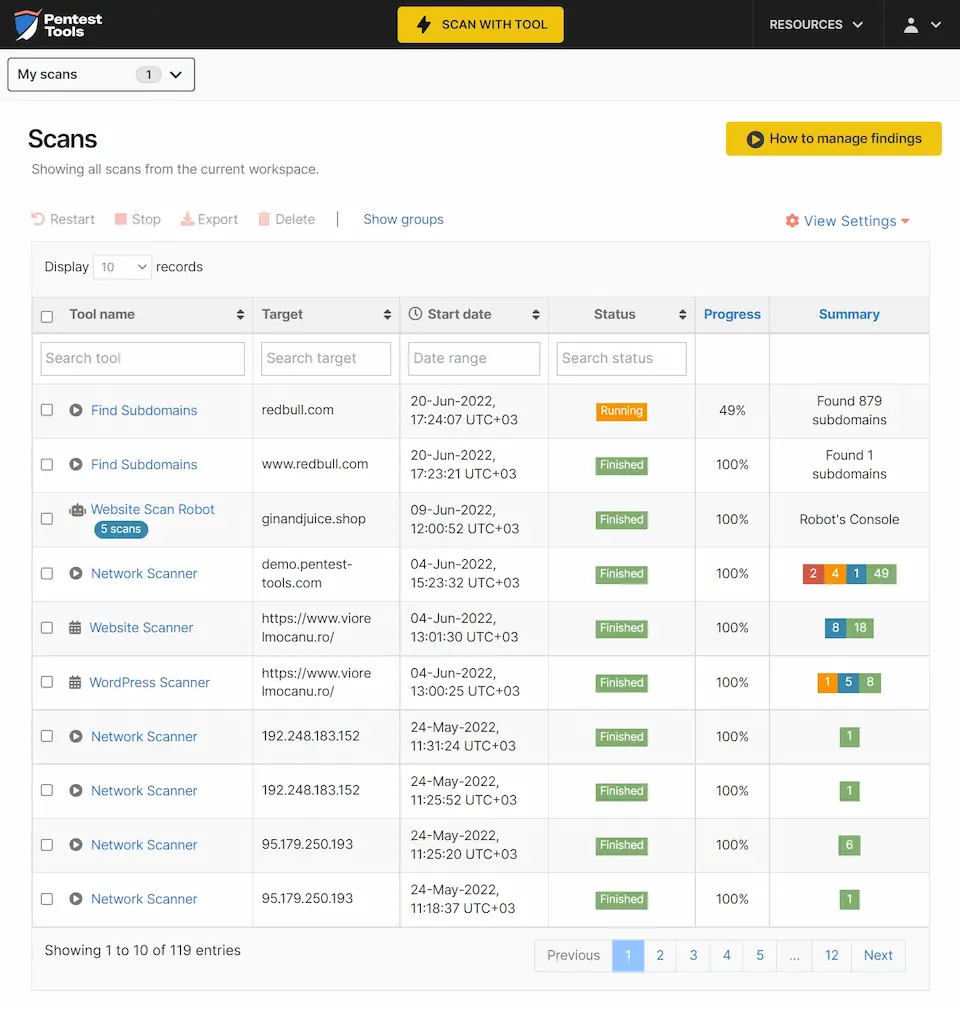
You can then launch pinpoint Reconnaissance tools for each type of discovery. For example, you can scan for new discoveries on one or more targets using Find Domains, Find Subdomains or Find Virtual Hosts. Alternatively, you can opt to use our Asset Discovery template to uncover subdomains, virtual hosts and associated domain names at once.
The next item on the checklist is to tackle open, outdated or misconfigured ports that can offer an attractive entry point for lazy, casual pillagers. Run a Port Scanner with Nmap on a list or range of target IP addresses and hostnames to first discover hosts and operating systems, then open ports and web services. Follow up with a UDP Port Scan. Grasp the easy wins and make sure the access points are nailed shut on your services.
Finally, our Website Recon scan will compile a list of backend and frontend technologies used by your target, such as its CMS, server, OS technology and versions. This helps you discover which attacks to run in order to determine remaining security vulnerabilities across the target. Results may include out-of-date, unpatched and misconfigured technologies that could result in system compromises and access or data breaches.
Our top 3 scanners by usage volume are:
Scan for more than just web applications
What is Invicti (formerly Netsparker) used for? Invicti is promoted and used as a web application scanner. Their software incorporates an extensive list of industry recognised web application security testing standards and benchmarks into their scans and reports. For example, you can run scans for the following: HIPAA, ISO27001, DISA STIG, NIST SP 800-53, OWASP Top 10, ASVS 4.0, PCI DSS, Sans Top 25, and WASC Threat.
You can tackle these most well-known and persistent attack vectors – and many others – by employing Pentest-Tools.com as the library of pentests and tools that supports your workflows as they change and evolve.
- First, deploy our Website Scanner, to detect the latest high risk vulnerabilities and CVEs, such as the Spring4Shell (CVE-2022-22965) Remote Code Execution (RCE) that can enable bad actors to gain unauthorized access.
- For your next maneuver, dig in and detect any malicious scripts using the XSS Scanner. Speed things up even more with the SQLi Scanner, which reveals insecure access points that permit behavior modification through specific SQL statements and queries.
In addition to our Website Scanner, we offer two further lines of defense: CMS Scanners and Network Vulnerability Scanners:
- For web applications built in a specific CMS, pick from our WordPress, Drupal, Joomla or SharePoint scanners. These domain specific scanners will examine known vulnerabilities for the core, components and modules; weak credentials and configurations; plugins and themes; versions; and more. Or, you can opt to scan using one of our templates instead, either the Passive Website Vulnerability Scan or WordPress Scan.
- When it comes to networks, we offer Network Vulnerability Scanning, SSL/TLS, and DNS Server scanning. You can also launch our Internal Vulnerability Scanner to reveal threats from within.
Once you’ve compiled this intelligence on the current security posture of your website applications, CMSes and networks, it’s time to choose your weapon. It’s time for a targeted assault on your digital collateral using our Offensive Tools. The latest piece of precision kit is our Sniper – Automatic Exploiter. Operate like an intruder, with silence and focus. Model any number of real-life exploitations by safely extracting some persuasive, evidential artefacts.
Great compliment to my toolbox! Easy to use.
Being cloud-based, you can get to the tools from anywhere without lugging around a dedicated device.

Dr. Patrick Johnson
True North Consulting Group, G2 Review
Zero onsite configuration or maintenance
What kind of companies use Invicti (formerly Netsparker)? Pentesting experts conducting an Invicti review will be directed to their desktop edition, Invicti Standard. Following download, there are a few additional, manual tasks required to set up and maintain. If you use both Standard and Enterprise products, and want to share scans and findings, you’ll have to manually import scan sessions between them. And, if you get a new laptop, you have to backup and move your settings – not a big deal, but a little pesky!
Enterprises convinced of the advantages of the Invicti web application security scanner who opt for Invicti Enterprise’s on-premises edition face considerable configuration to set it up on-site. Further, if you need to scan internal web applications, you’ll first have to download and install internal agents and authentication verifier agents, which also need updates. And, this is before we get to the issue of managing and maintaining sufficient licenses. These tasks could prove onerous for less technical members of the team.
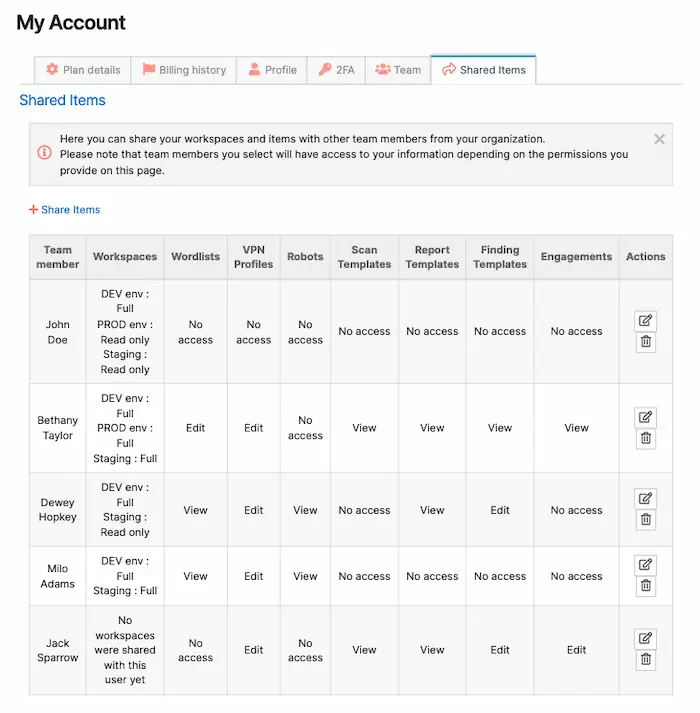
Pentest-Tools.com in contrast is a fully cloud-based, on-demand platform. We facilitate hassle-free asset sharing for larger teams using our Shared Workspaces and Items features, with access to engagements, templates, pentest robots, scans, findings, and reports. Software updates are automated with both vulnerability libraries and new tools expanded regularly. And, there are no on-site downloads, configurations or manual settings required for internal network scanning or any other type of scan.
Automation reserved for minimizing technical debt
Automation is only one item on the shelf. We don’t make it the central aspect of our offering because we believe that a good pentester can never be replaced. We’ve reserved it to allow you to automate 80% of those dull, repetitive tasks like Attack Surface Mapping. For example, with scan templates, you can group several tools and options and launch them together at target. Or, you can schedule periodic scans.
We’ve also built in pentest robots to support your creative investigations. The Pentest-Tools.com platform allows you to chain multiple tools and logic blocks using built-in, drag and drop, automated testing sequences. This helps you create your own testing flow against any target. This visual flow is translated into a script that lets you monitor the progress and results. No coding or maintenance is required, and the RPA-like, non-invasive approach ensures targets remain intact.
Another area in which we adopt automation to save you time on mundane tasks is in internal network scanning. Our Network Vulnerability Scanner is pre-configured to pass your targets through our VPN Agent to uncover any internal network vulnerabilities. Unmask the risks from within such as out-of-date network services, missing security patches, weak credentials and other unexpected attack vectors to cover all the bases.
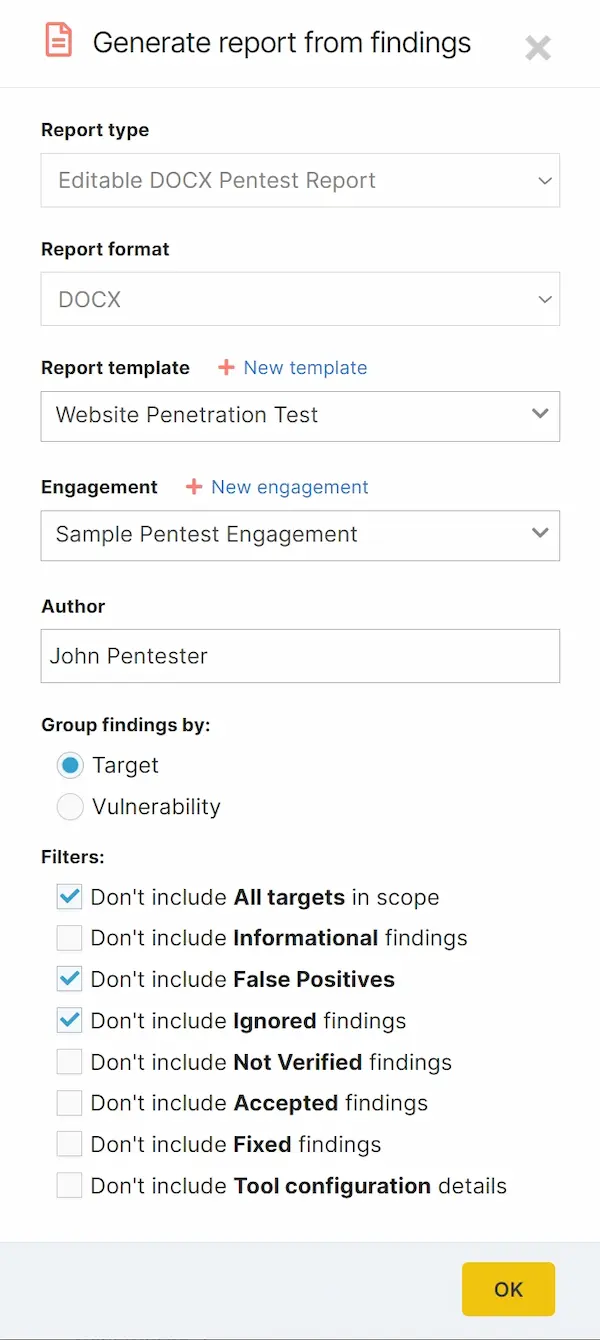
Ultimately, you will deploy our professionally written pentest reports to distill your expertise and blend it with our pre-filled findings templates. The automated report generator tool rapidly aggregates, categorizes and displays findings, their exploits and recommendations from across your scans. You need only choose the report type, format, template, engagement, and filters from dropdowns to produce reports within minutes.
These useful automations allow you to redeploy resources into the edge cases, such as the recurring and least explored risks. Enjoy more time to enhance your reports with atypical, manual findings and demonstrate a higher ROI. Claw back your time for exploring without agendas.
Common Questions
FAQs: Pentest-Tools as the Invicti (formerly Netsparker) alternative
So, is Pentest-Tools.com a better choice than the Invicti security scanner?
The answer is that it depends on what you want. It’s true that Invicti provides web application scanning. But, we assume you’ve landed on this page because you’re interested in researching technical pentesting solutions. If so, Pentest-Tools.com combines its proprietary and open-source tools to help you:
Make offense your best asset for strengthening defense.
Our customers rave about the sheer scope of tools from which they can select. You can deploy each independently for rapid identification, documentation and remediation of known weaknesses. But, you can also link and chain tools together for enhanced detection capability. And, if you work in a team environment, you can employ our cloud-based Shared Items and Workspaces to share your engagements, templates, robots, scans, findings, and reports.
What else is there?






