Hydra or the Password Auditor: the best tool for brute-force attacks
When it comes to credential auditing, choosing the right tool can make all the difference.
This comparison puts Hydra and the Password Auditor to the test across 26 web applications - including Microsoft Exchange, WordPress, and Joomla - to evaluate how effectively they identify weak credentials, navigate complex login forms, and detect security defenses like CAPTCHAs and IP blocking.
Find out which tool gets you in faster, smarter, and with less hassle.
Overview of this bruteforce tools comparison
Necessary
Why compare these credential scanning tools?
This comparison dives into how Hydra and the Password Auditor actually perform in real-world scenarios to find weak credentials.
By testing both tools across different web apps, it shows how well they handle various login forms, error messages, and security defenses like CAPTCHA or IP blocking.
This isn't just about raw data; it's about helping you pick the right tool that’s effective, easy to use, and fits your specific needs when you're on a job, trying to efficiently audit targets for weak credentials.
Transparent
What kind of findings does this comparison include?
The findings cover the tool’s detection rates of valid credentials, how they detect defensive measures like CAPTCHA and IP blocking, and how accurately they identify login endpoints and parameters in 26 different web applications.
The key findings and full list of results include all the Hydra commands and Password Auditor parameters used, as well as proof for each tested web app.
Realistic and relevant
How does this comparison evaluate the tested bruteforce tools?
The comparison measures each tool's success rate by testing both Hydra and the Pentest-Tools.com Password Auditor across 26 HTTP applications, using two scenarios: a controlled lab environment with a mix of valid and invalid credentials, and a real-life setup with multiple invalid credentials.
It assesses each tool's ability to identify login endpoints, detect error messages, detect defenses like IP blocking and CAPTCHA, and accurately report results.
Methodology for this bruteforce tools comparison
Testing period: July-August 2024
Evaluated on the ability to identify:
login endpoints
login parameters
error messages & protection mechanisms
26
HTTP applications tested
2
replicable test scenarios
2
wordlists with valid + invalid usernames & passwords
7
defensive measures tested
Criteria for evaluating bruteforce tools
For a fair, objective evaluation of both Hydra (open-source) and our Password Auditor (proprietary), we chose transparent criteria and a replicable setup to open this analysis up to independent testing and validation.
This comparison test how each credential scanning tool interacts with the application login in two situations:
Lab scenario: when sending 1 valid and 1 invalid pairs of credentials
Realistic scenario: when sending 1 valid and 10+ invalid pairs of credentials.
Successful detection means the tool identified the credentials or provided a server error finding with a screenshot, along with bypass recommendations on how to override protections.
Testing bruteforce software in a lab scenario
Simulating a lab environment, we evaluated the tools’ ability to detect login parameters and validate two sets of credentials to confirm a successful login.
Testing bruteforce software in a realistic scenario
Replicating a real-life scenario, we tested the tools' ability to handle multiple sets of credentials and observe the application's defensive measures against brute force attacks - and how effectively the tools reported these defenses.
Defensive measures included: 2FA, IP whitelisting and IP blacklisting, CAPTCHA, account lockout, source IP blocking, rate-limiting, context-based authentication, and login attempt delay.
Watch the bruteforce tool comparison breakdown
Watch David Bors, Security Research Engineer, break down the results of this comparison and see how each credential scanning tool did against the 26 HTTP applications.
Comparison results: the most accurate brute forcing tool
Find out which bruteforce tool cracks faster and better
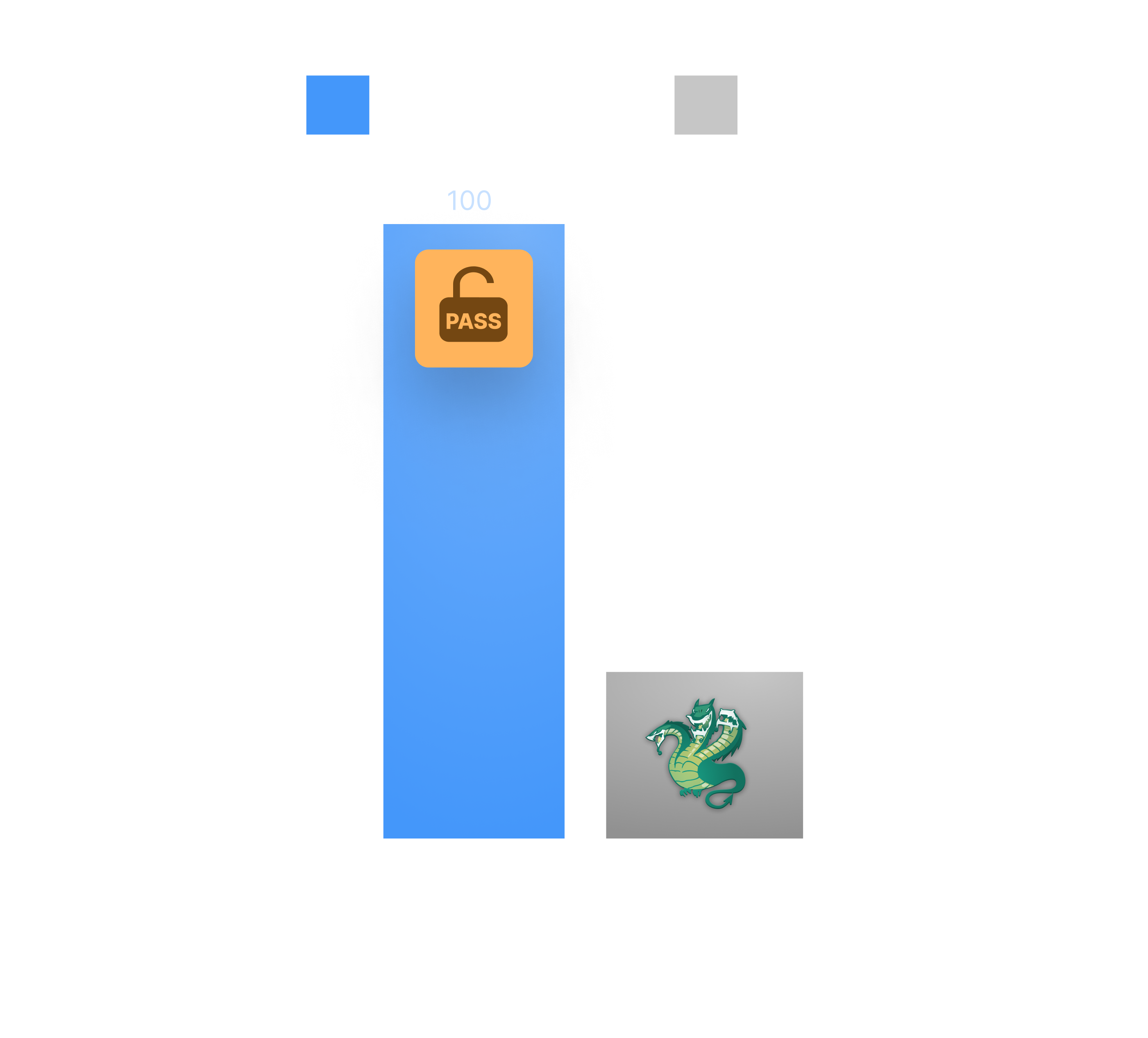
Identifying valid credentials in a lab scenario
The Password Auditor on Pentest-Tools.com consistently demonstrated superior accuracy in identifying valid credentials across all 26 web applications. It achieved a 100% success rate when tested with one valid and one invalid credential set.
Hydra, in contrast, identified only 7 valid credentials with a 27% success rate for the single credential test scenario.
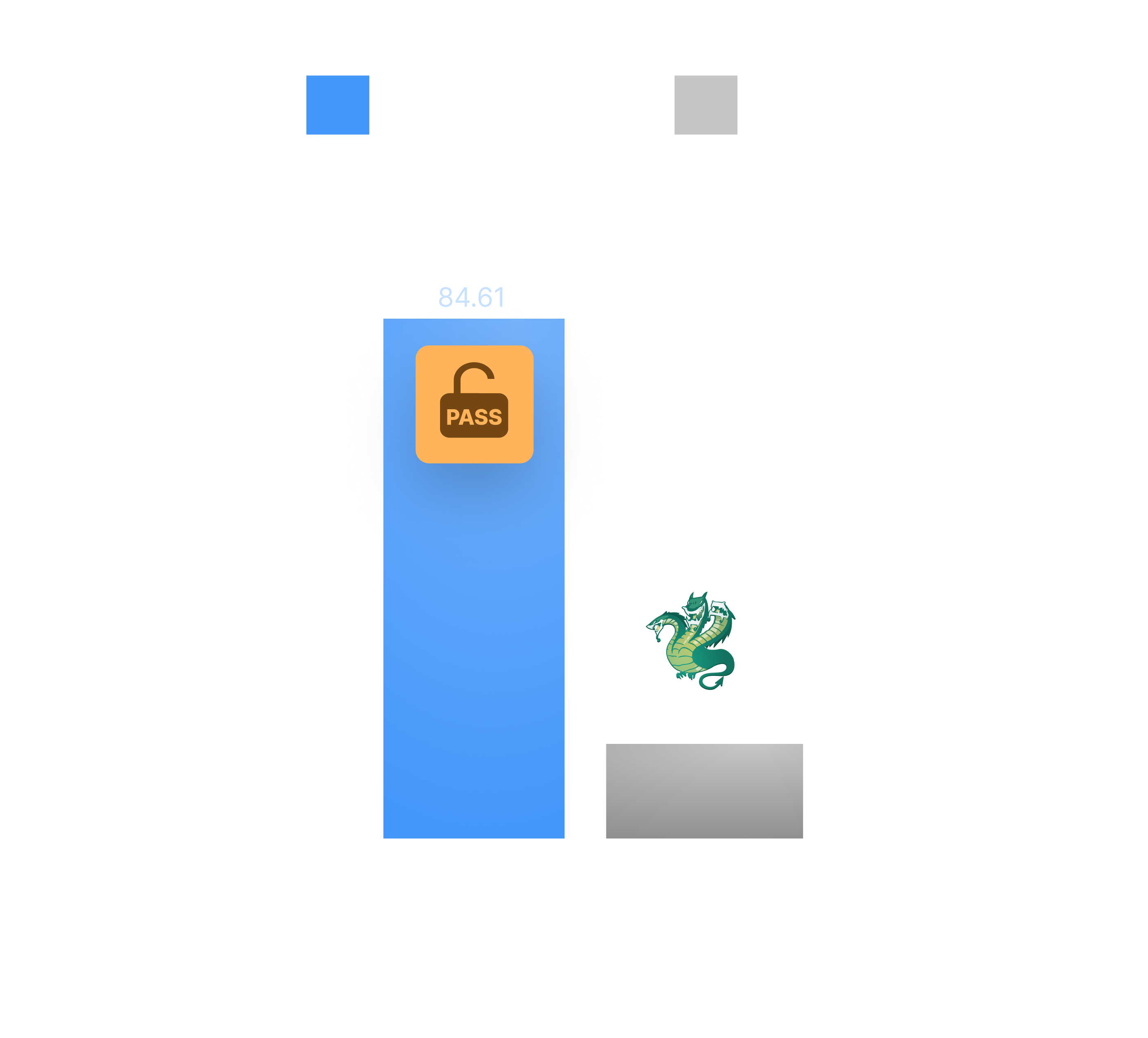
Identifying valid credentials in a realistic scenario
When testing the 26 target apps with multiple credentials (one valid and 10+ invalid ones), the Password Auditor on Pentest-Tools.com maintained a high success rate of 84% in identifying credentials or detecting defensive measures.
In this more complex scenario, Hydra's success rate dropped to 15%, correctly identifying only 4 valid credentials. This suggests Hydra struggles more with identifying valid credentials under varying conditions.
Handling application-specific defensive mechanisms
The Password Auditor on Pentest-Tools.com was notably effective in recognizing various defensive mechanisms like IP blacklisting, CAPTCHA, account lockout, and rate limiting. It provided specific feedback and recommendations to bypass or handle these defenses, which is crucial for real-life penetration testing where such measures are common.
Hydra faced challenges with certain applications that use web CSRF tokens or dynamic form protections. Because of its inability to handle client-side JavaScript token generation or CSRF token rotation, Hydra often marked valid and invalid attempts similarly, reducing its effectiveness. Workarounds exist, but they require several tools and do not fit the scope of this benchmark.
Ease of use and setup
The Password Auditor on Pentest-Tools.com is more user-friendly with a pre-configured interface that simplifies the setup process. Security practitioners just need to specify the target, select the attack type, choose ports, and enable desired services. The tool also allows scheduling regular scans, enhancing its usability.
Hydra requires a more manual setup process, including crafting specific commands to find login endpoints and parameters, which is time-consuming. This setup complexity is a disadvantage in fast-paced testing environments where time efficiency is critical.
Ability to work around encryption and token mechanisms
The Password Auditor effectively managed to bypass client-side encoding and token mechanisms by using its pre-built configurations. This capability is particularly valuable for auditing web apps that implement client-side protections.
Hydra’s performance dropped significantly on platforms that used client-side hashing or encryption. Since Hydra doesn’t operate within a browser environment, it couldn’t replicate JavaScript-based hashing, limiting its effectiveness against applications like Adobe ColdFusion and JetBrains TeamCity, which use advanced encryption or client-side hashing.
Overall performance
For security specialists looking for a robust, easy-to-use tool with high accuracy in detecting weak credentials and handling modern web application defenses, the Password Auditor on Pentest-Tools.com is a recommended choice. Its high success rates, user-friendly interface, and ability to navigate advanced security mechanisms make it a more reliable option for comprehensive web app auditing.
Hydra remains a powerful tool, especially for scenarios where a more manual, command-line approach is suitable, or when dealing with simpler authentication mechanisms without complex client-side protections. However, for advanced, automated credential auditing across diverse environments, the Password Auditor offers more value and reliability.
Setup and specs for bruteforcing with Hydra and the Password Auditor
Tinkering with security tools is fun, but it can quickly become frustrating if it takes too long.
The most demanding part of this comparison was setting up Hydra correctly. Crafting the right command is time-consuming, so we're sharing the detailed steps for identifying parameters and configuring Hydra to test all 26 web apps.
Alongside it you’ll see how to use our Password Auditor - and what results it gets you.

Hydra
To determine the Hydra command, follow these steps:
1. Find the login endpoint
Find the application's login endpoint by either exploring the application in a browser or by fuzzing to discover login paths.
2. Discover the login parameters
Use Firefox's Web Developer Tools, specifically the Network tab, to find the parameters required for logging into the application.
3. Identify error messages and protection mechanisms
Input invalid credentials to identify possible error messages and observe how many invalid attempts trigger a protection mechanism.

The Password Auditor on Pentest-Tools.com
The Password Auditor on Pentest-Tools.com is pre-configured and ready to use.
Add your target.
Choose the attack type (dictionary or password spray).
Select the port range.
Enable the services you want to test.
Use the default wordlists or create/add your own.
Set a delay between attempts to avoid lockouts.
[Optional] Enable default credentials check.
[Optional] Set a custom scan time.
[Optional] Choose a “follow redirects” policy.
And scan - or schedule a regular scan.
How to bruteforce web apps with Hydra and the Password Auditor
9 things you can do with this comparison of bruteforcing tools
1. Choose the most effective bruteforcing tool for your target
Based on the results from this comparison, you can select the right tool for bruteforcing credentials based on the type of system or web application you’re targeting (e.g., WordPress, Drupal, Joomla).
Case in point, the Password Auditor demonstrated superior performance across more complex login scenarios (e.g., dynamic forms, CAPTCHA, IP blocking), while Hydra was more limited in handling client-side security mechanisms like JavaScript hashing.
2. Confidently automate credential auditing - at scale
If you need an automated tool for auditing web apps with a focus on ease of use and minimal configuration, the Password Auditor is a reliable choice. You can simply select the attack type (dictionary or password spray), enable services, and configure the port range to launch scans quickly.
The tool’s ability to schedule regular scans and automate credential auditing across multiple targets makes it a valuable tool for large-scale projects. You can automate routine checks for weak credentials and have reports generated without manual intervention. This helps manage multiple clients or a large number of assets efficiently.
3. Adapt attacks to application-specific configurations
Many web applications, such as Jira, Bitbucket, or Microsoft Exchange, use unique login forms and parameters. The comparison outlines specific commands and configurations for each tool, allowing you to adapt your brute-force attacks to each application’s setup.
For instance, Hydra requires manual setup but allows for deep configuration of attacks, making it suitable when you need fine-tuned control over the process, especially in simpler environments that don’t implement client-side security mechanisms.
4. Detect CAPTCHA and IP blocking
The comparison reveals that the Password Auditor is more effective at recognizing defensive mechanisms like CAPTCHA and IP blocking and providing bypass recommendations. You can use this capability to audit web apps that deploy such protections.
5. Adjust attack speed and avoid detection
Both the Password Auditor and Hydra can set delays between attempts to avoid triggering account lockouts or rate-limiting mechanisms. This feature is useful for flying under the radar while performing brute-force attacks, reducing the risk of detection.
6. Validate web app login endpoints and error messages
This comparison shows how both Hydra and the Password Auditor detect login endpoints and error messages, a critical first step in assessing web applications for brute-force vulnerabilities. You can compare their effectiveness and accuracy to choose the most reliable tool for simulating attacks against your targets.
7. Handle client-side hashing mechanisms
The comparison shows how the Password Auditor was able to bypass complex security mechanisms like client-side encryption and token generation. This makes it ideal for environments like Adobe ColdFusion where Hydra failed because it was unable to replicate client-side security processes.
8. Generate detailed attack reports
The Password Auditor provides detailed feedback on defenses it encounters during an attack, including IP blacklisting, CAPTCHA, and login attempt delays. This level of detail allows you to generate comprehensive reports for clients or colleagues, outlining the strength of their authentication defenses and the bypasses that can override them.
9. Benchmark bruteforce tool performance for future tests
These detailed comparison results offer a benchmark for future bruteforce testing. By understanding how each tool performed across the 26 tested applications, you can set realistic expectations for similar tools or when using Hydra or the Password Auditor in your environment.
Bruteforce tools comparison FAQs
What is the main difference between Hydra and the Password Auditor?
The Password Auditor is more user-friendly and effective at handling modern web application defenses, while Hydra requires manual setup and is better for simpler authentication scenarios.
Which tool is better for detecting CAPTCHA and IP blocking?
The Password Auditor is more effective at recognizing CAPTCHA and IP blocking mechanisms, offering detailed feedback, screenshots, and ready to use reports.
Can Hydra handle client-side security mechanisms?
No, Hydra struggles with client-side security mechanisms like JavaScript-based hashing and token generation, making it less effective against web apps using advanced encryption.
Which tool is easier to set up and use?
The Password Auditor is easier to use because it provides a pre-configured interface and built-in reporting, while Hydra requires manual command-line configuration, which is more time-consuming.
How does each tool detect defensive measures like IP blocking?
The Password Auditor can detect and report various defensive measures, including IP blocking and CAPTCHA, while Hydra often fails detecting such protections.
Which tool works best for large-scale credential auditing?
The Password Auditor is more suited for large-scale credential auditing, as it allows for automated scans and scheduling, making it more efficient for managing multiple targets.
Does Hydra perform well in realistic brute-force scenarios?
Hydra performs poorly in realistic scenarios with multiple invalid credentials, while the Password Auditor maintains a higher success rate in such conditions due to its capabilities.
Is it possible to use custom wordlists with both tools?
Yes, both Hydra and the Password Auditor allow you to use custom wordlists, giving you flexibility in brute-forcing with tailored credential lists.
Does the Password Auditor require installation or setup?
No, the Password Auditor is a web-based tool on Pentest-Tools.com, requiring no installation. It is pre-configured and ready to use after setting the parameters you need.
Which tool is more effective for auditing web applications with client-side security mechanisms?
The Password Auditor is more effective because it can navigate JavaScript-based hashing and dynamic tokens, which Hydra cannot handle because of its limitations in replicating client-side processes.
Is the Password Auditor user-friendly for beginners?
Yes, the Password Auditor offers a user-friendly interface with minimal configuration required, making it accessible for beginners and efficient for professionals needing quick setup.
How can I choose the right tool for my penetration testing needs?
Consider the complexity of the target application's security mechanisms. Use the Password Auditor for applications with advanced defenses and when ease of use is a priority. Choose Hydra for simpler scenarios where manual configuration is acceptable.
Does the Password Auditor provide detailed reports and screenshots?
Yes, the Password Auditor provides detailed findings, including screenshots of successful logins, and offers recommendations for bypassing security defenses encountered during testing.
Are there any scenarios where Hydra performs better than the Password Auditor?
Hydra may perform adequately in simple authentication scenarios without advanced client-side security mechanisms, but overall, the Password Auditor showed superior performance in the comparison.
Is it possible to replicate the testing scenarios from the comparison?
Yes, the document provides transparent methodology and detailed steps, allowing you to replicate the testing scenarios to validate the results in your own environment.
How do the tools handle account lockouts and rate limiting?
The Password Auditor can detect account lockouts and rate limiting, providing recommendations to avoid triggering these defenses and even an option to set custom delays between attack attempts. Hydra lacks the capability to detect account lockouts and rate limiting, often failing to recognize when these mechanisms are activated.
Can Hydra be used to test applications with dynamic CSRF tokens?
Hydra struggles with applications that use dynamic CSRF tokens because it cannot replicate the dynamic generation of tokens required for each request.
How important is ease of use when choosing a credential auditing tool?
Ease of use is crucial, especially when time efficiency is important. A tool like the Password Auditor minimizes setup time and complexity, allowing you to focus on the testing itself.
Are there any legal considerations when using these tools?
Yes, it's important to use these tools ethically and legally, only on systems for which you have explicit permission to perform security testing, to comply with laws and regulations.






