Wordpress Scanner
Detect vulnerable plugins and themes, exposed database dumps, config issues and plenty more in core Wordpress software. Paid plans unlock deep, scheduled scans and notifications for more high risk security issues.
- Scan type
Light scan
Detect vulnerable plugins and themes, exposed database dumps, config issues and plenty more in core Wordpress software. Paid plans unlock deep, scheduled scans and notifications for more high risk security issues.
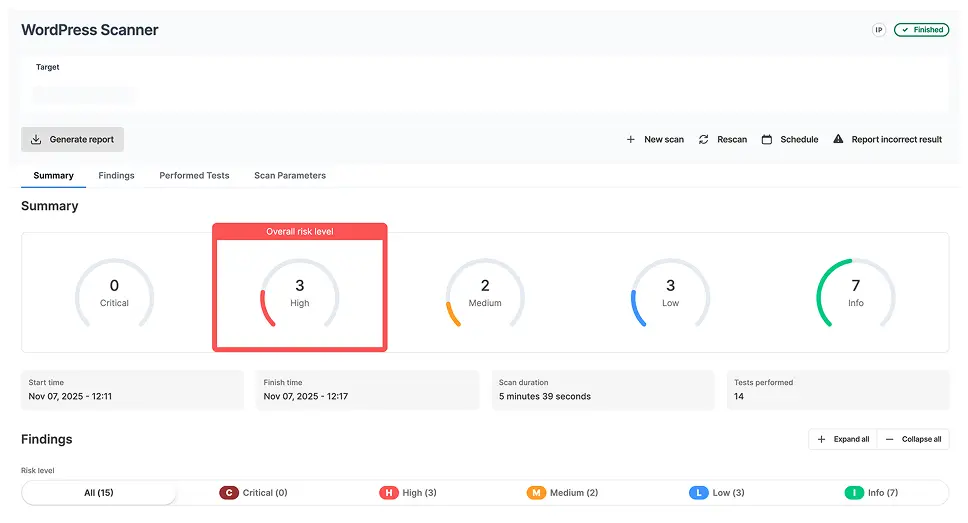
Sample Wordpress Scanner report
Here is a sample report from our Wordpress Scanner that gives you a taste of how our tools save you time and reduce repetitive manual work.
Includes all discovered plugins, themes and their versions
Shows vulnerabilities and exploits which affect each component
Reports WordPress configuration issues (directory listing, backup files, etc.)
Incorporates WordPress fingerprinting information
Your CMS is only as strong as its weakest plugin

Use Cases for Wordpress Scanner
WordPress Penetration Testing
You can speed-up your penetration test using this scanner since it is already installed, configured and ready-to-go. Quickly discover vulnerable plugins, themes and other configuration issues.
Security Self-Assessment
Check if your installation of WordPress is up to date and properly configured. Do an inventory of existing plugins and check if you’re using their latest version.
Third-Party Website Audit
If you are a web development company, you can use this report to prove to your clients that you have implemented proper security measures in their Wordpress-based website.
Better vulnerability discovery. Faster pentest reporting.
Get instant access to custom Vulnerability Scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.

Technical details
List of tests performed
Fingerprint the installed WordPress version
Show the vulnerabilities for the running WordPress version
Enumerate the installed plugins and their versions
Show the vulnerabilities for the identified plugins
Enumerate the installed themes and their versions
Show the vulnerabilities for the identified themes
Enumerate the WordPress users
Search for config backups
Search for database exports
Search for vulnerable timthumbs
Parameters
Target URL
This is the URL of the WordPress website that will be scanned. All URLs must start with http or https. Don't forget to specify the complete path to the base directory of the WordPress installation. e.g. http://targetwp.com/blog/.
Detection Mode - Passive
Runs a non-intrusive detection i.e it sends a few requests to the server. It commonly scans the home page for any vulnerability. The passive mode is less likely to be detected by IDS/IPS solutions
Detection Mode - Aggressive
Performs a more intrusive scan as it sends numerous requests to the server. This approach has a greater chance to find the correct WordPress version, enumerate users and better find the plugins.
Enumerate
Search for: usernames, vulnerable themes, vulnerable plugins, config backups, database dumps, timthumbs.
How it works
The scanner connects to the target WordPress website and does a series of passive checks to identify the WordPress version, plugins, themes, users, config backups, database dumps and timthumbs.
By analyzing the HTML source code and the HTTP headers, WPScan manages to extract all the necessary information to perform the assessment. The vulnerabilities presented are determined based on the specific versions of WordPress or plugins/themes that have been identified.
The tool also incorporates a database of WordPress vulnerabilities that gets periodic updates and maintenance.

How do WordPress sites get hacked?
Since WordPress is a widely used platform, it often becomes a target for hackers. Their attacks are facilitated by the high number of outdated WordPress installations and outdated plugins and themes. These old versions of WordPress components contain vulnerabilities and security weaknesses that can be exploited.
A WordPress hack often starts by identifying which version of WordPress is running and what are the installed plugins and themes. The next step is to fingerprint the running versions of those components and to search for public vulnerabilities affecting them. A lot of public exploits are also available online.
For instance, a well-known WordPress plugin called Revolution Slider is affected by multiple high-risk vulnerabilities in some of its older versions.
- Versions <= 4.1.4 of this plugin are affected by an Arbitrary File Download vulnerability which allows an attacker to download any file from the server (including PHP configuration files, database files, etc.) by accessing a link such as
http://vulnerable_wordpress.xx/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php - Versions <= 3.0.95 of this plugin allow hackers to upload arbitrary files on the server including PHP shell files. The result of such an action is taking total control of the webserver.
These hacks can be prevented by periodically scanning the WordPress installation using a tool such as our WordPress vulnerability scanner and identifying vulnerable components. These must be updated and the WordPress installation becomes secure and trustworthy.







