How to bruteforce CMSs and e-commerce apps with Hydra and the Password Auditor
This guide provides real-world testing methodologies for WordPress, Drupal, Joomla, PrestaShop, and Magento, helping you correctly identify weak login endpoints, analyze error messages, and work around security mechanisms for efficient pentests and security assessments.
You’ll find detailed Hydra commands for precise, high-efficiency bruteforcing, along with insights on using our Password Auditor to automate credential testing. This comparison makes it easier to choose which tool can help you brute-forcing faster and more effectively by capturing screenshots of logged-in sessions and generating detailed proof of valid credentials.
Bruteforce commands and settings for Hydra and the Password Auditor
Since every CMS and e-commerce platform handles authentication differently, with varying levels of protection like rate limiting, CAPTCHAs, and account lockouts, you need a tool as flexible and capable as your workflows.
Whether you’re testing a single admin account or running large-scale credential audits, this guide gives you the practical techniques and automation strategies to improve your credential auditing workflow while avoiding unnecessary detection.
How to check Wordpress for weak credentials
Deployment method: Vultr marketplace
1. Find the Wordpress web app login endpoint
The WordPress administrator login usually sits on the /wp-login.php endpoint.
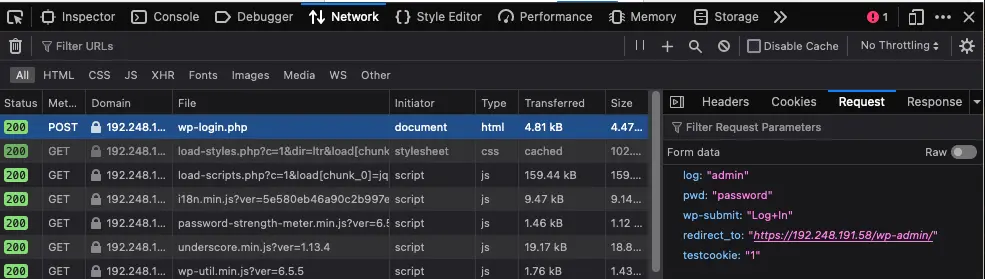
2. Discover the Wordpress login parameters
Use the Network tab in the browser’s Web Developer Tools to find the login parameters.
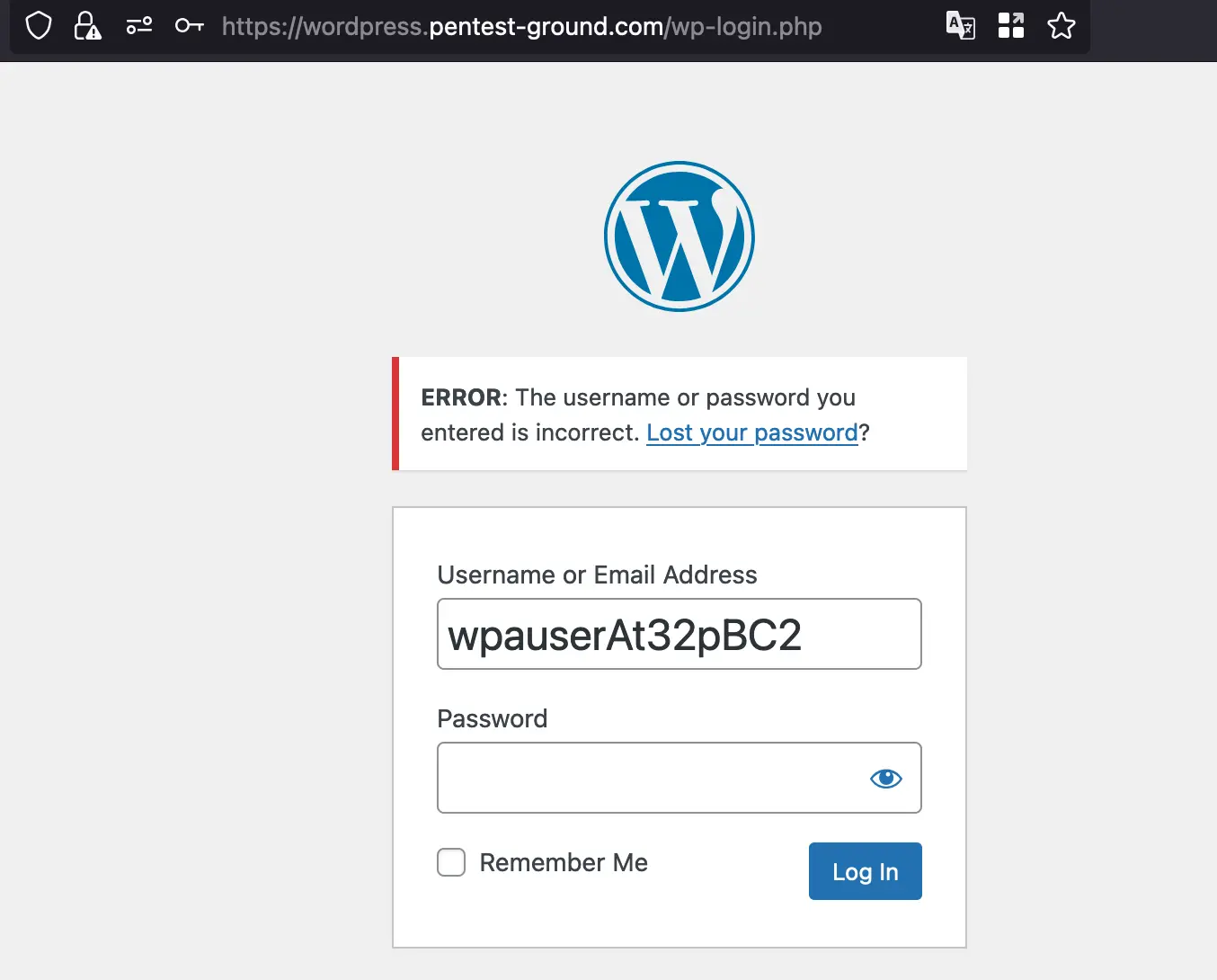
3. Identify error messages and protection mechanisms
After one invalid attempt, the WordPress app returns the following message:
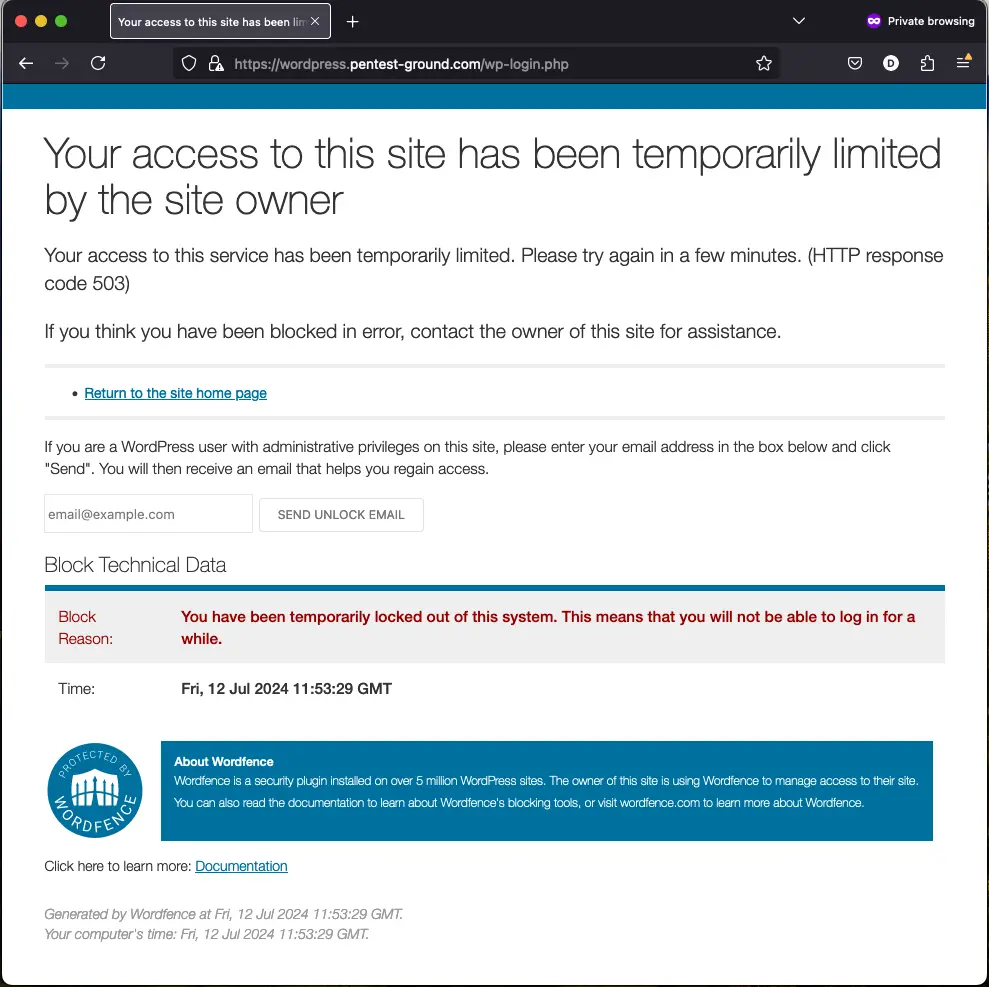
After 10 invalid attempts, the Wordfence plugin (pre-installed in the deployed environment) gets triggered. Note that the block only works for active accounts.
Hydra commands and output
For bruteforcing Wordpress with 1 valid and 1 invalid pairs of credentials, we used the following commands:
hydra -l wpauserAt32pBC2 -p bad-password wordpress.pentest-ground.com -V https-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:The username or password you entered is invalid.'hydra -l wpauserAt32pBC2 -p D5nZ9UzELriBpENkATlgWR7jqeamvr7j wordpress.pentest-ground.com -V https-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:The username or password you entered is invalid.'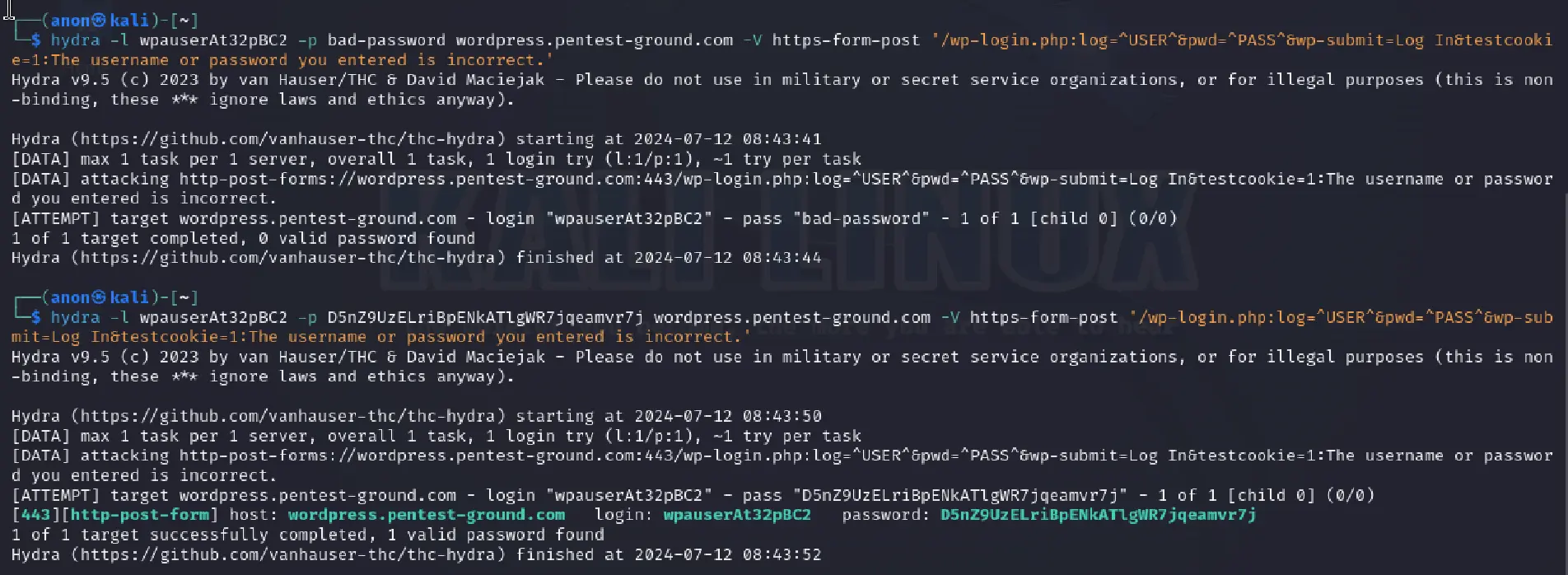
As shown in the output, Hydra successfully distinguished between invalid and valid credentials.
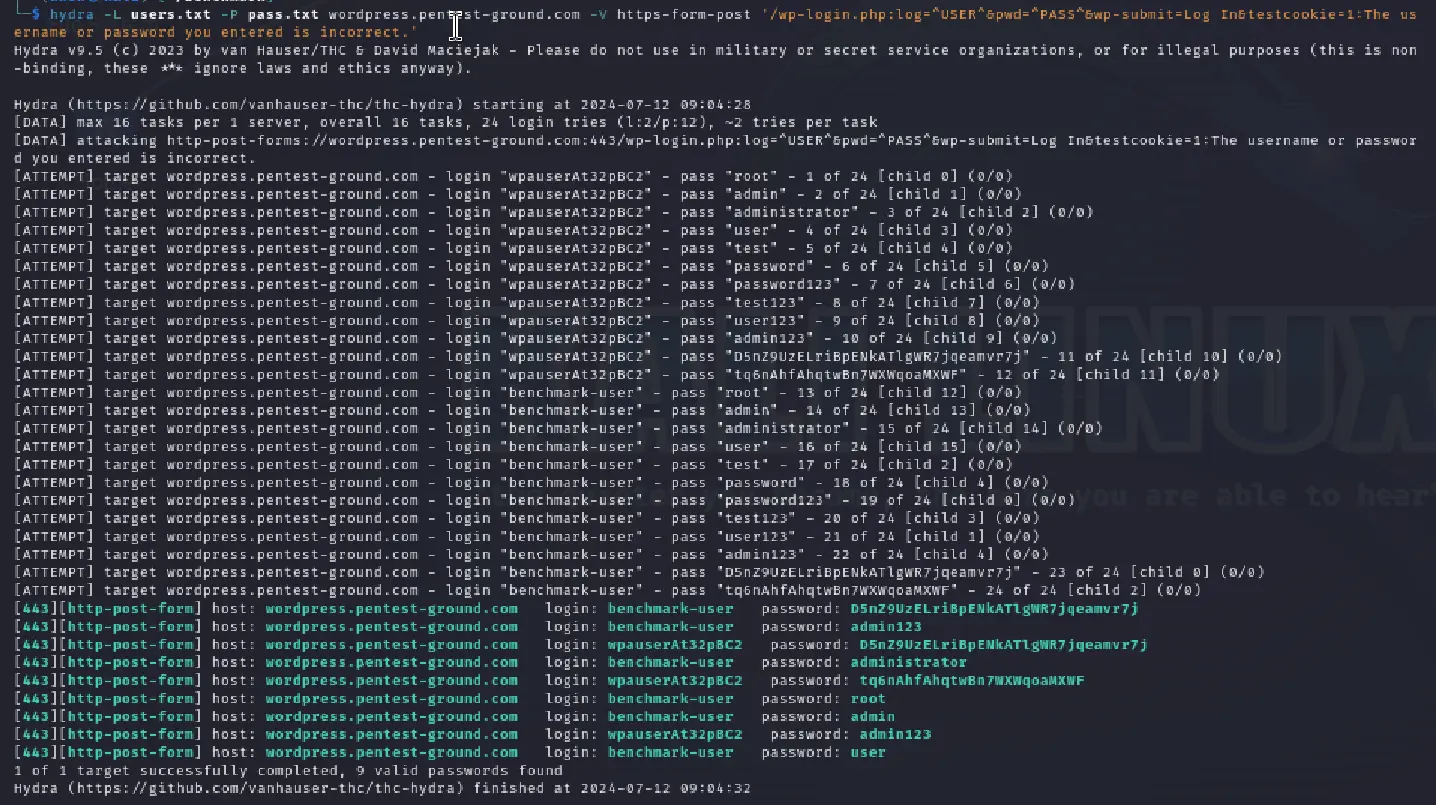
For the second scenario that used multiple sets of credentials, we used the following Hydra command:
hydra -L users.txt -P pass.txt wordpress.pentest-ground.com -V https-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:The username or password you entered is invalid.'Wordfence was activated after multiple failed attempts, and Hydra generated numerous incorrect credentials.
Password Auditor commands and results
For the first scenario, we adjusted the following parameters in the interface to run a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, the Password Auditor will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
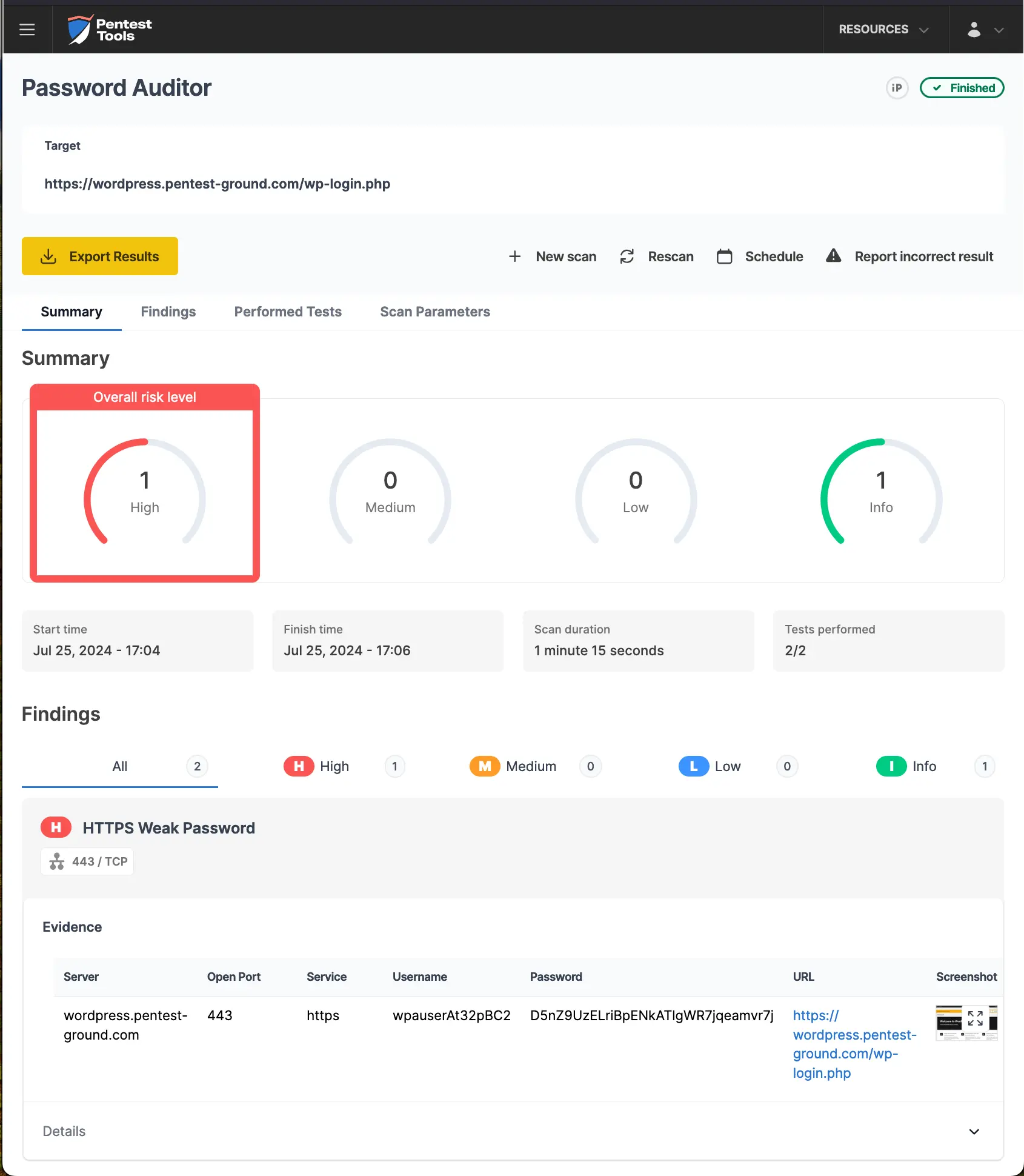
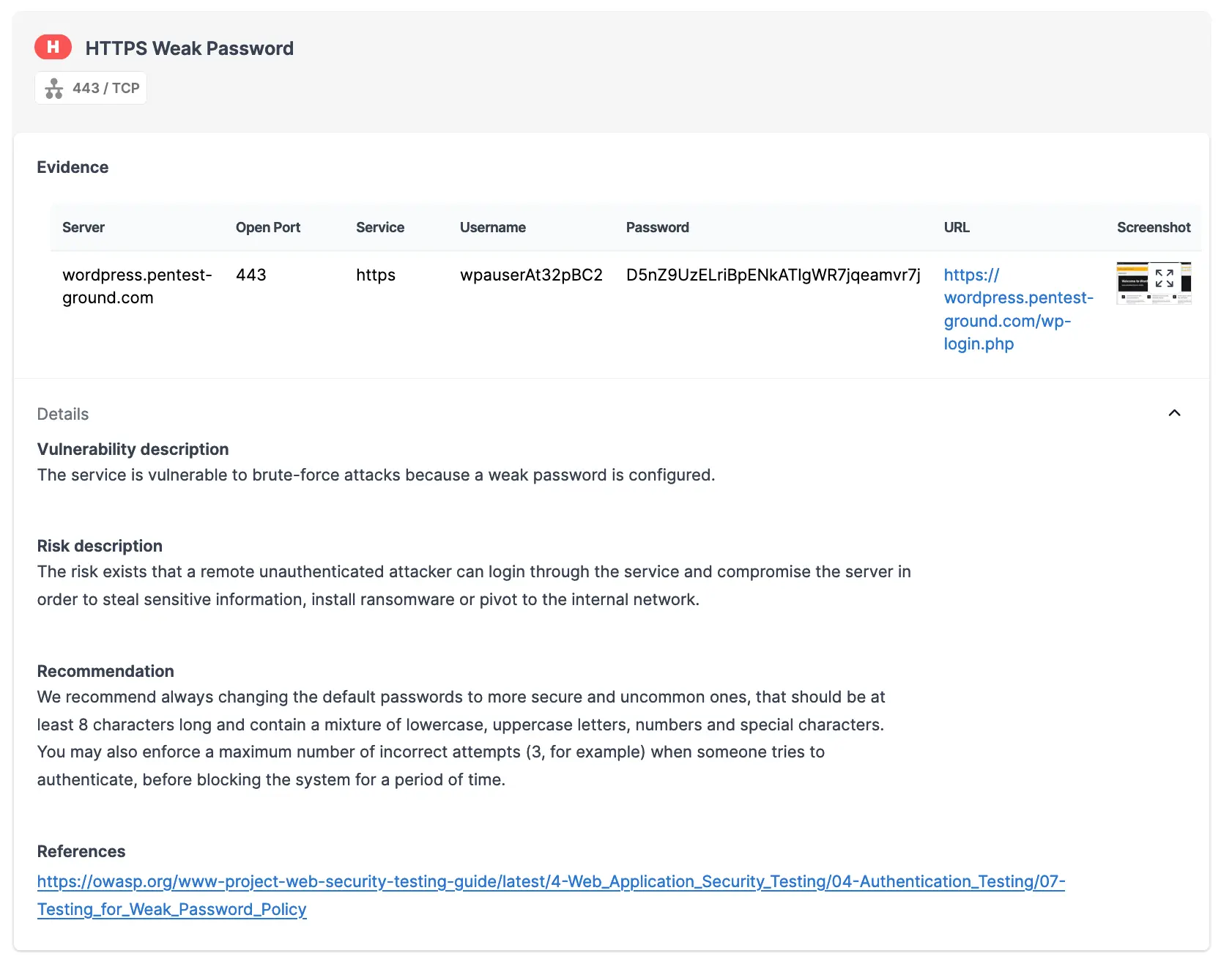
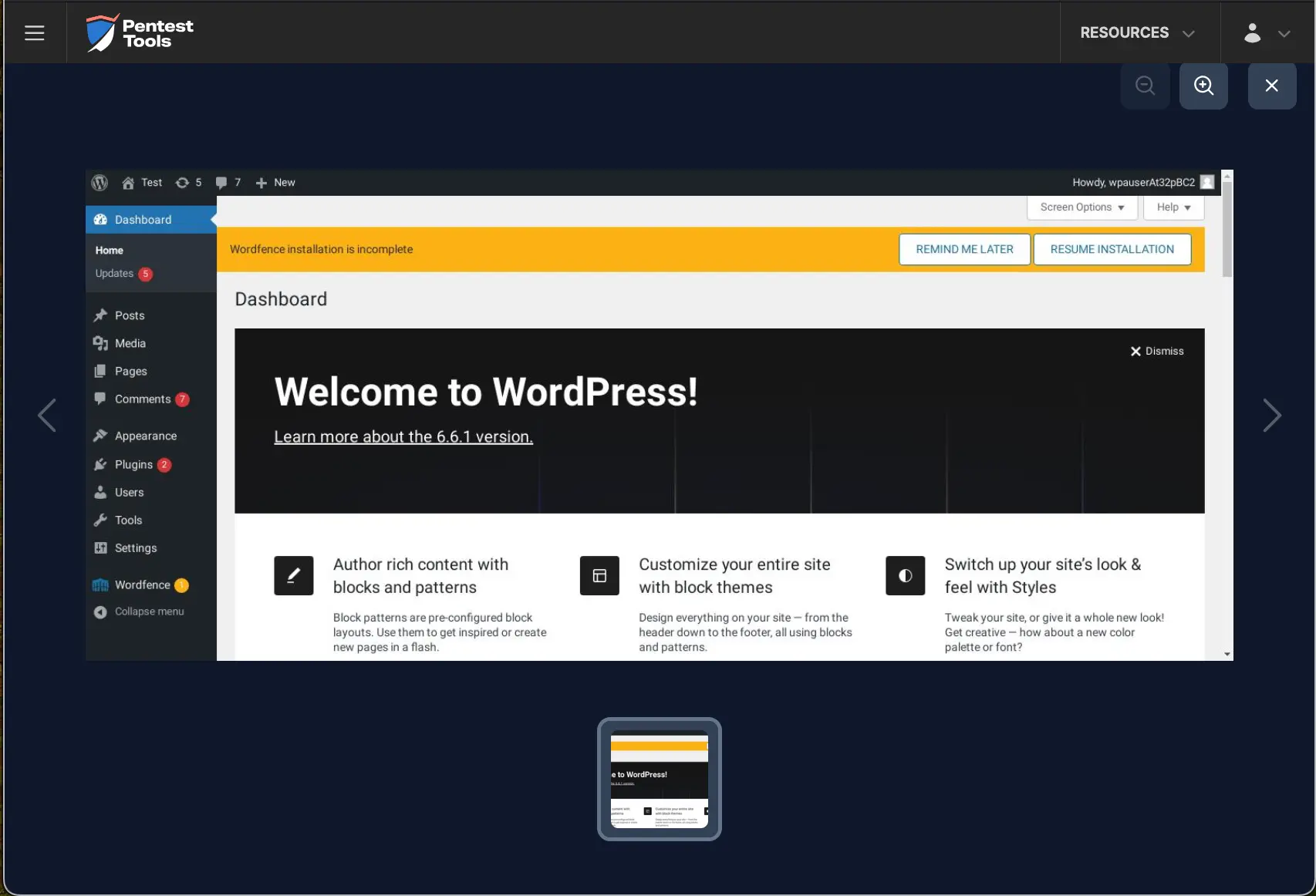
The Pentest-Tools.com Password Auditor also includes a screenshot of the logged-in session to confirm the provided credentials are valid.
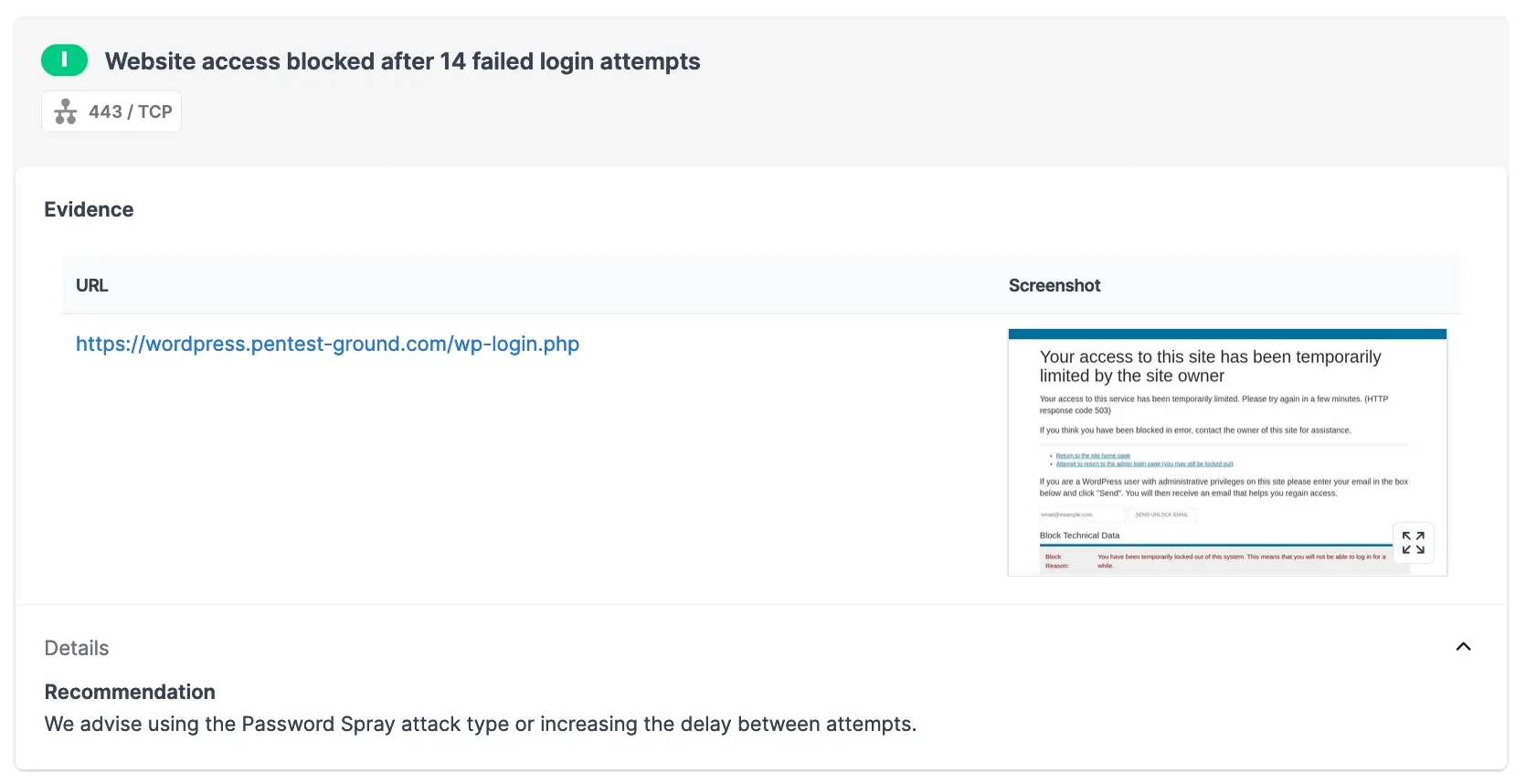
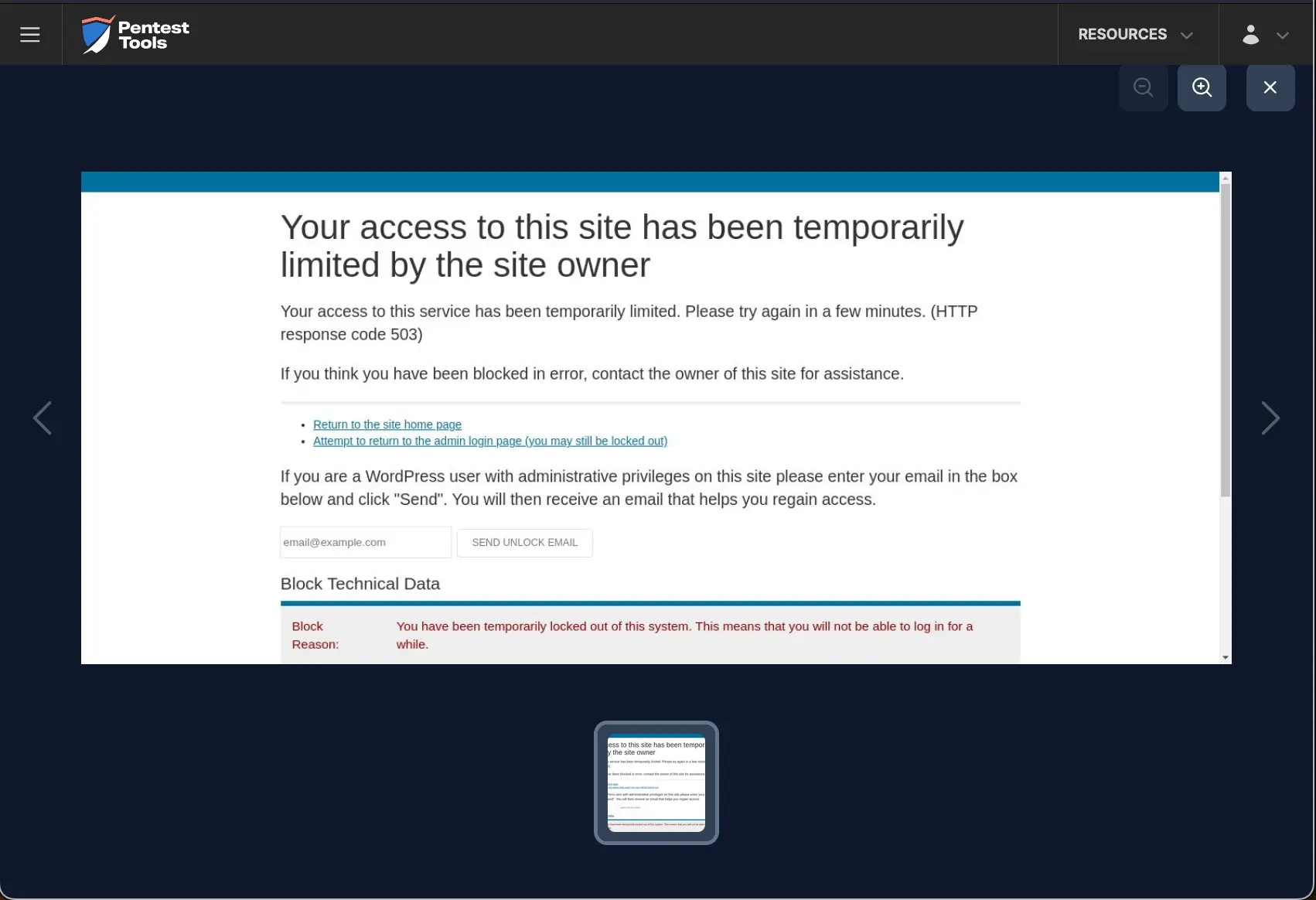
For the scenario with multiple credentials, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid). The Password Auditor reports the IP address was temporarily blocked.
To automatically avoid IP blocking, you can use the “Delay between attempts” option in the Password Auditor to set a custom delay duration and ensure your attacks are effective and get you the results you need.
How to check Drupal for weak credentials
Deployment method: Vultr marketplace
1. Find the Drupal web app login endpoint
You can usually find the Drupal login at the /user/login endpoint.
2. Discover the Drupal login parameters
Use the Network tab in the browser’s Web Developer Tools to identify the login parameters.
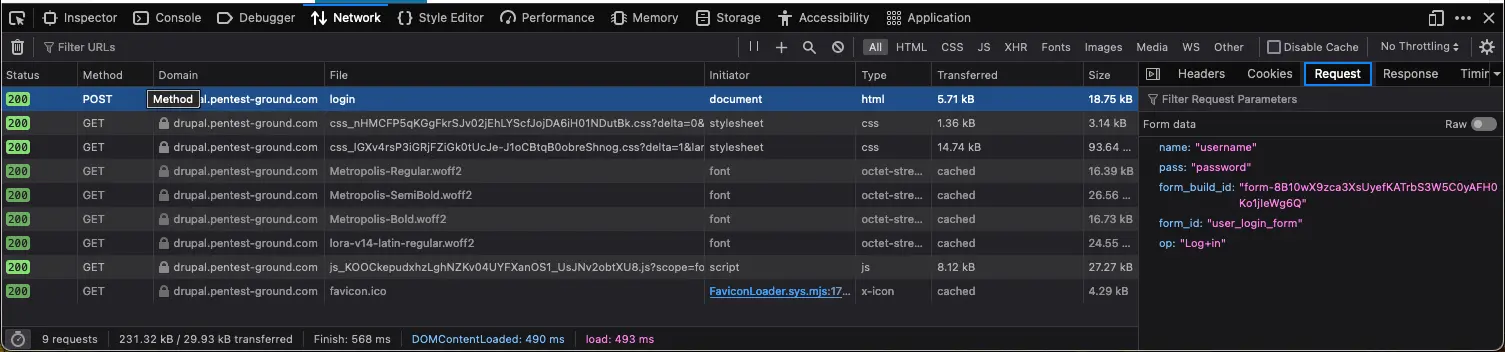
3. Identify error messages and protection mechanisms
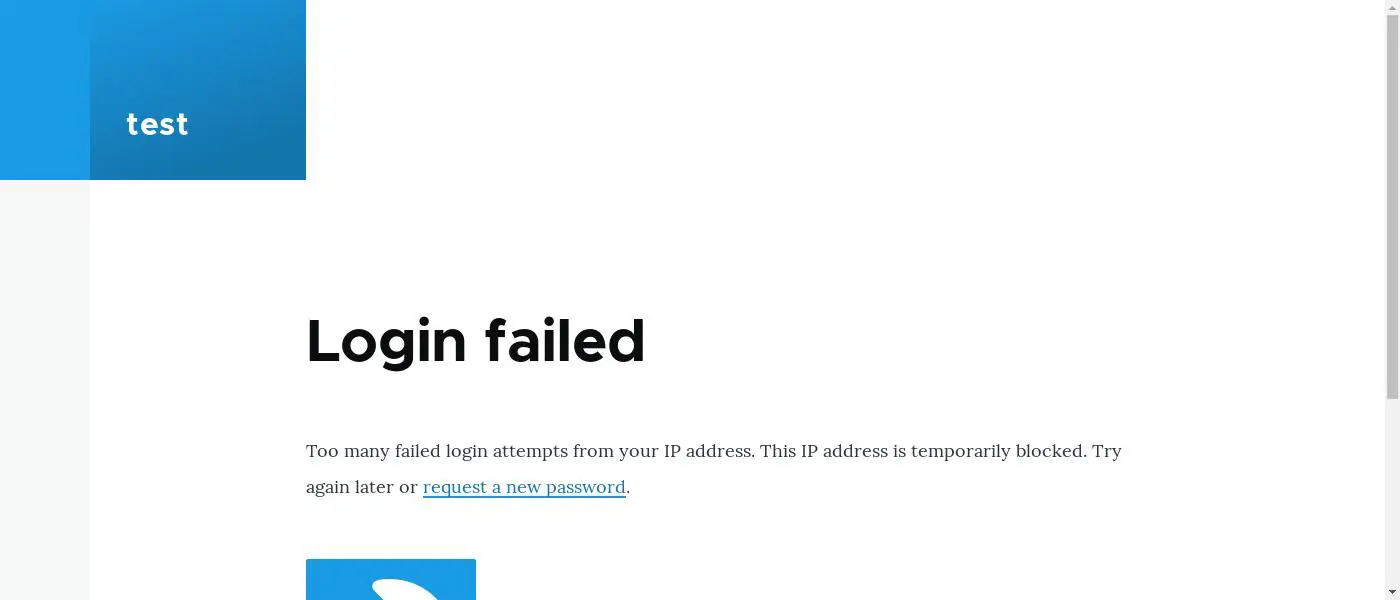
After one invalid attempt, the following message is returned:
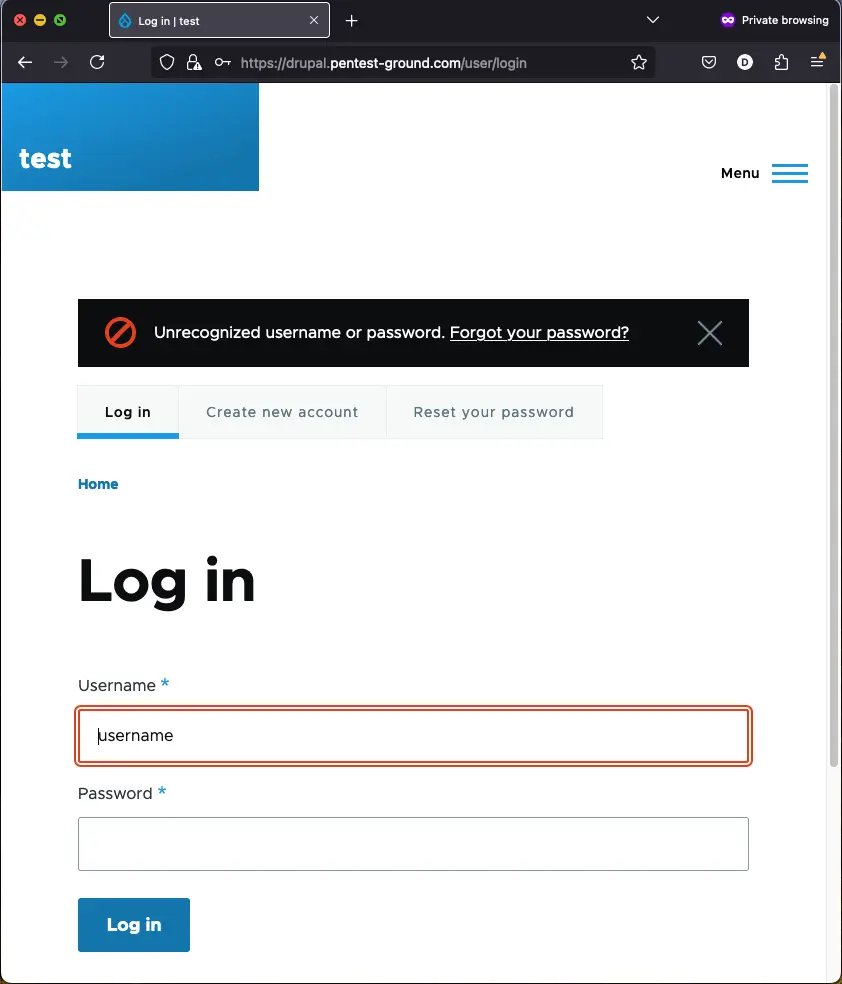
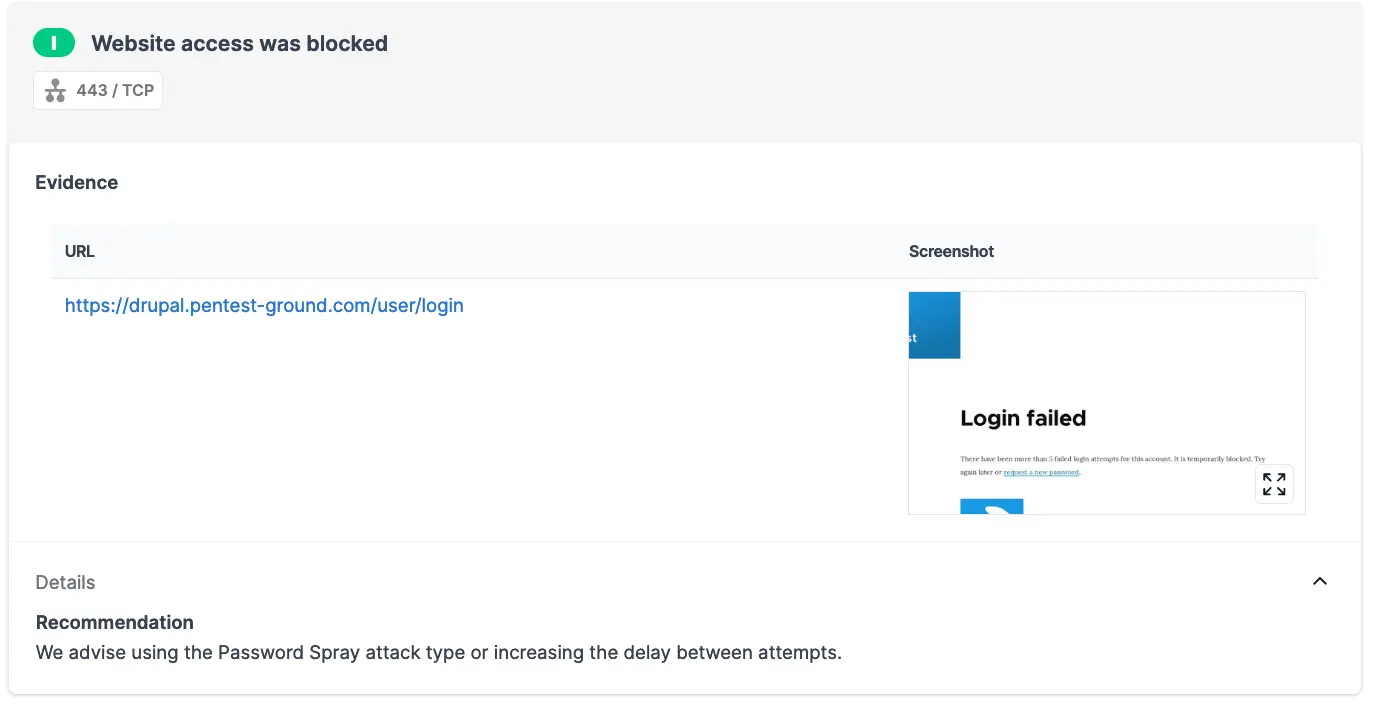
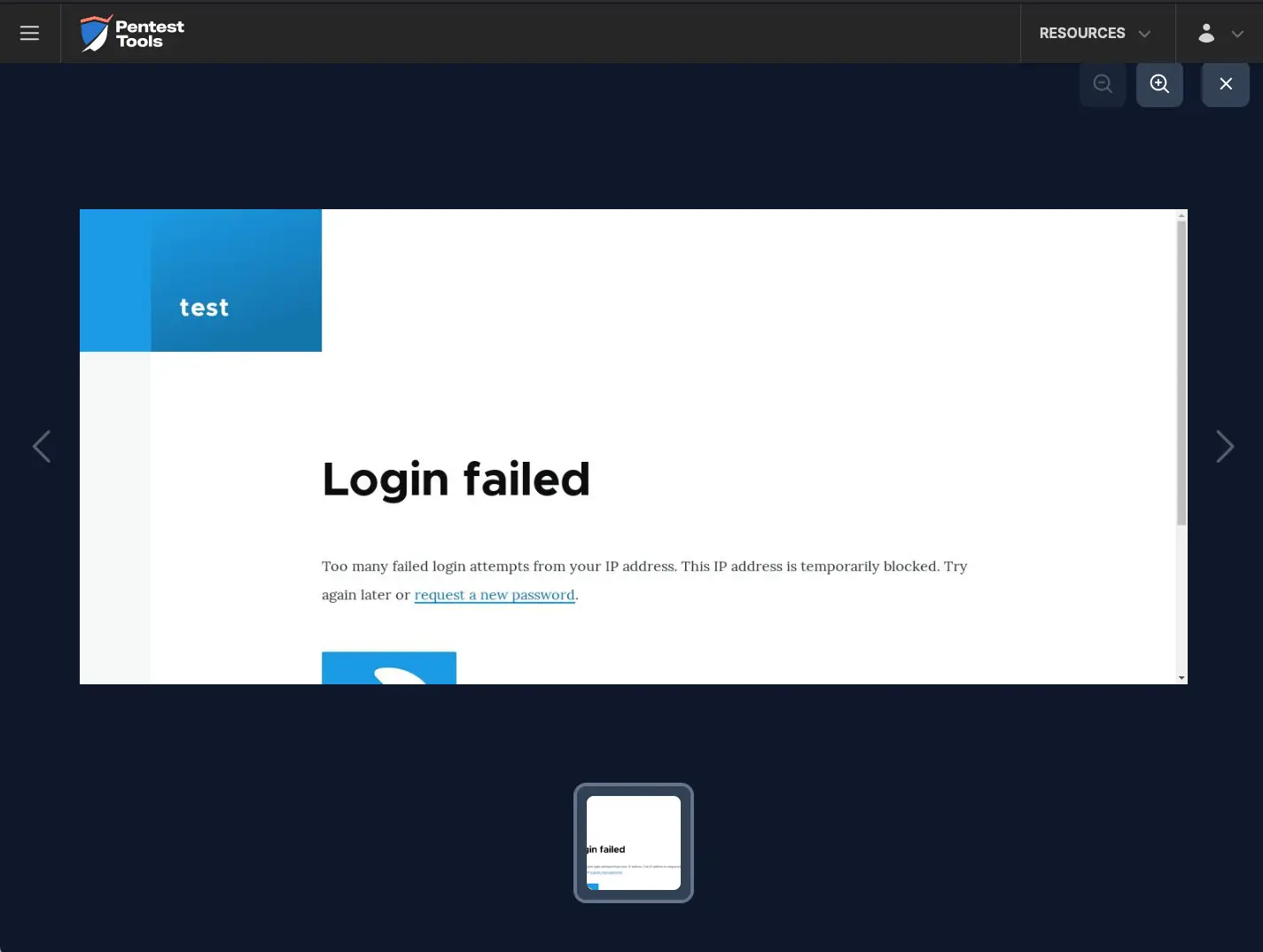
After 5 invalid login attempts, the protection mechanism is activated, and the account is temporarily blocked.
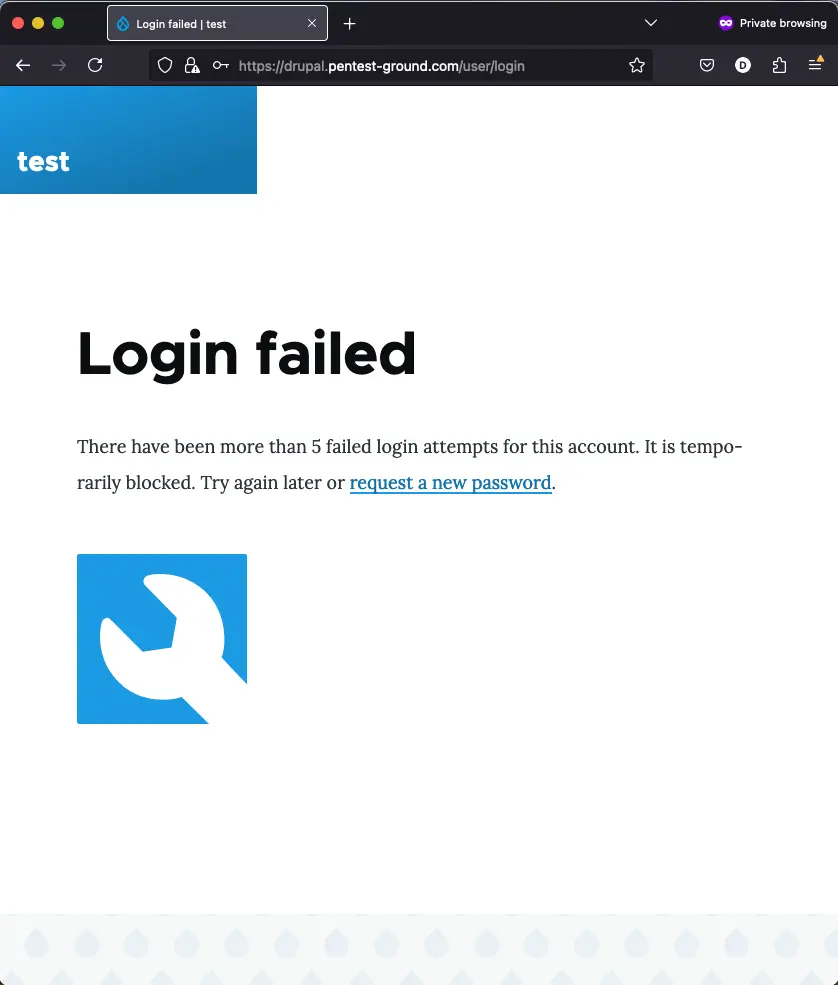
After multiple failed attempts, the source IP address will be blocked.
Hydra commands and output
In the first scenario, we used the following Hydra commands:
hydra -l benchmark-user -p bad-password drupal.pentest-ground.com -V https-form-post "/user/login/:name=^USER^&pass=^PASS^&form_build_id=form-8B10wX9zca3XsUyefKATrbS3W5C0yAFH0Ko1jIeWg6Q&form_id=user_login_form&op=Log+in:Unrecognized username or password"hydra -l benchmark-user -p tq6nAhfAhqtwBn7WXWqoaMXWF drupal.pentest-ground.com -V https-form-post "/user/login/:name=^USER^&pass=^PASS^&form_build_id=form-8B10wX9zca3XsUyefKATrbS3W5C0yAFH0Ko1jIeWg6Q&form_id=user_login_form&op=Log+in:Unrecognized username or password"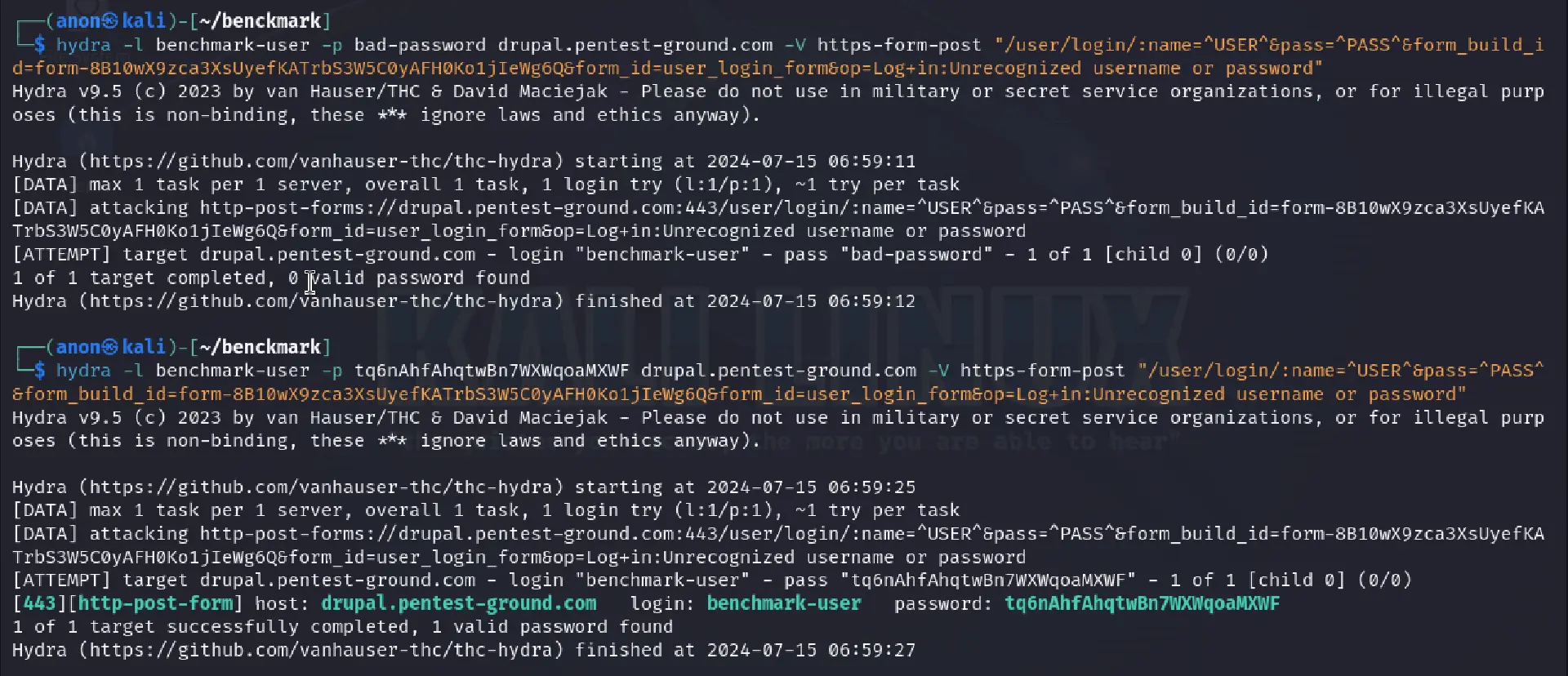
As shown in the output, Hydra accurately identified the invalid and valid credentials.
For the second, more complex scenario, we used the following command:
hydra -L users.txt -P pass.txt drupal.pentest-ground.com -V https-form-post "/user/login/:name=^USER^&pass=^PASS^&form_build_id=form-8B10wX9zca3XsUyefKATrbS3W5C0yAFH0Ko1jIeWg6Q&form_id=user_login_form&op=Log+in:Unrecognized username or password"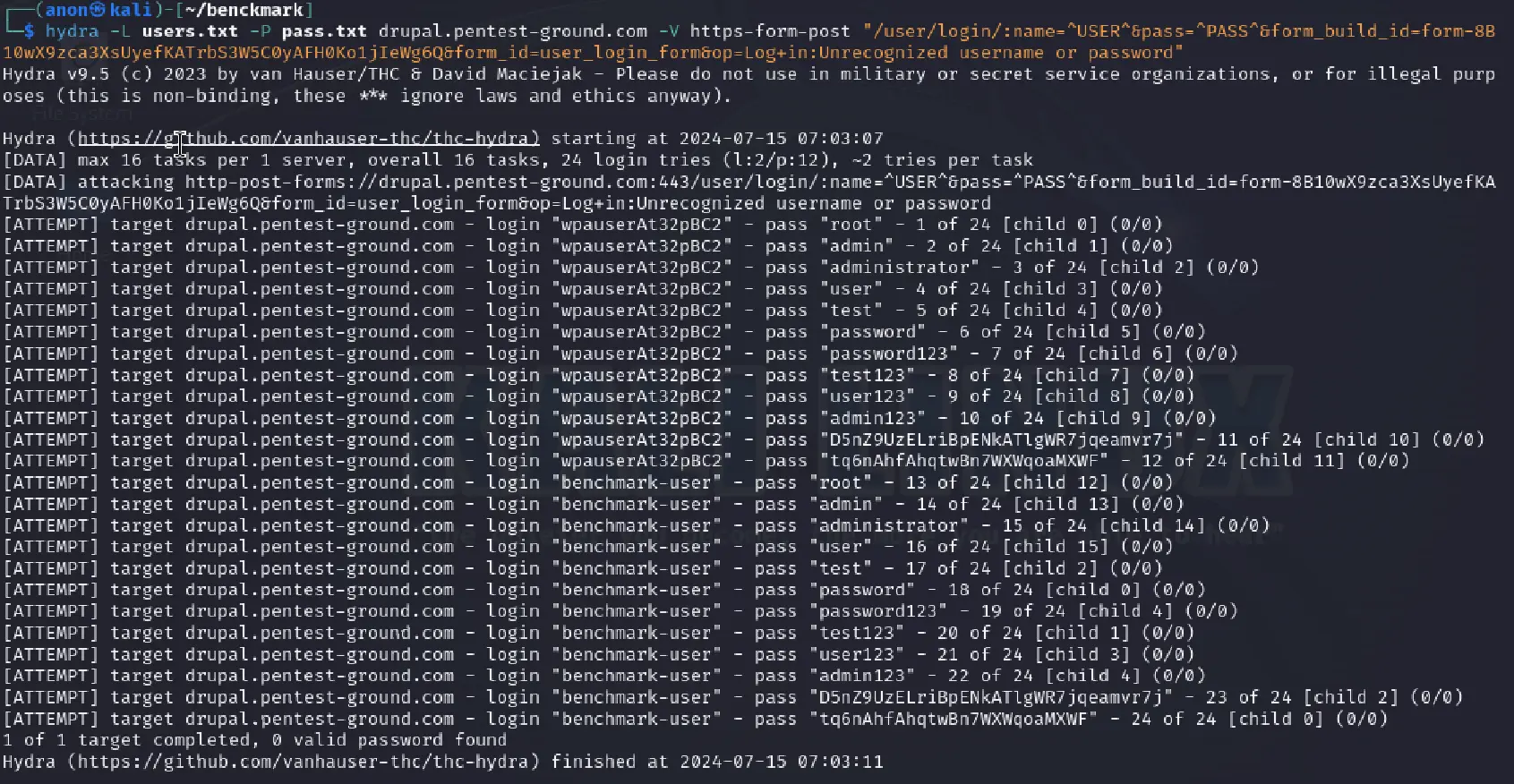
Drupal activated its protection mechanism after multiple failed attempts, and Hydra was unable to find the valid credentials.
Password Auditor commands and results
To run a quicker, more focused scan in the first scenario, we adjusted the following parameters:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As shown in the screenshots below, the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
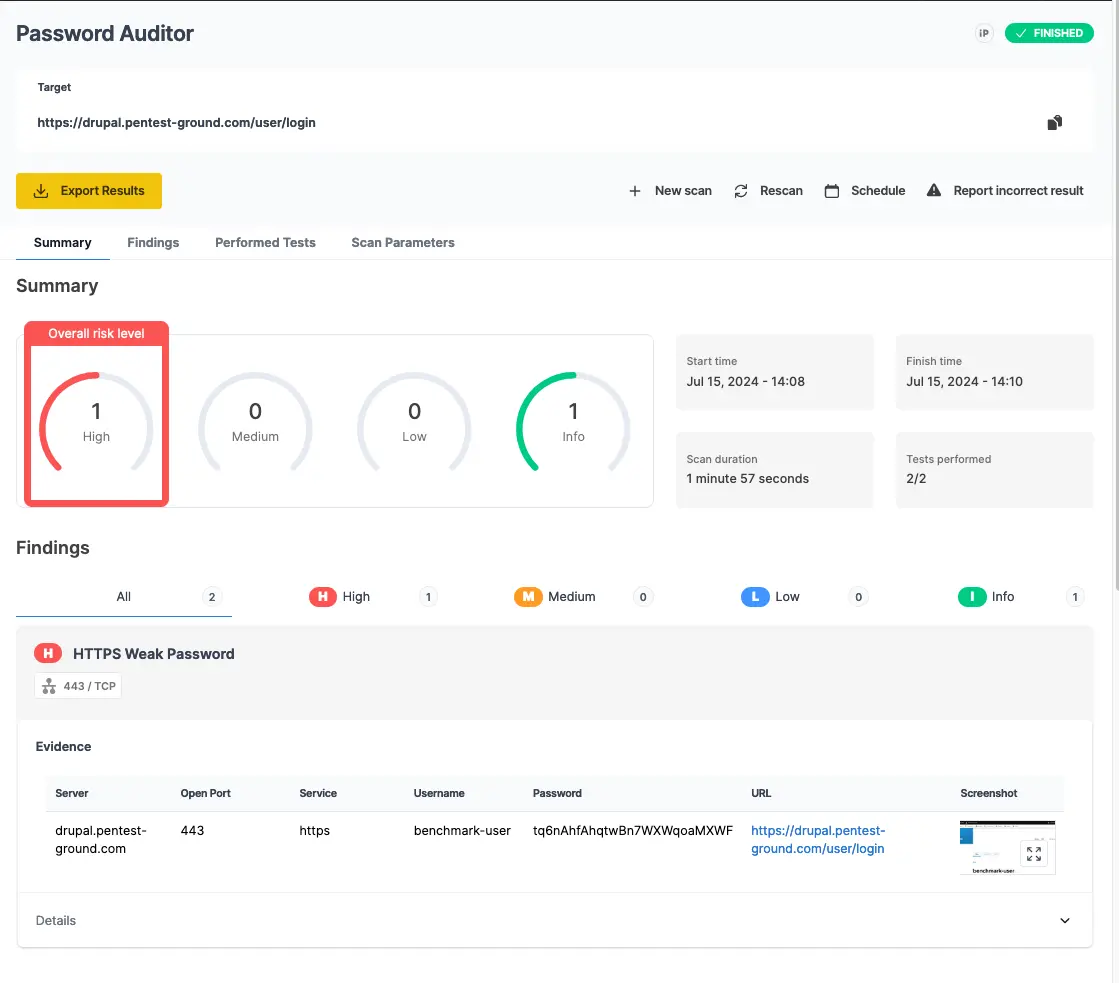
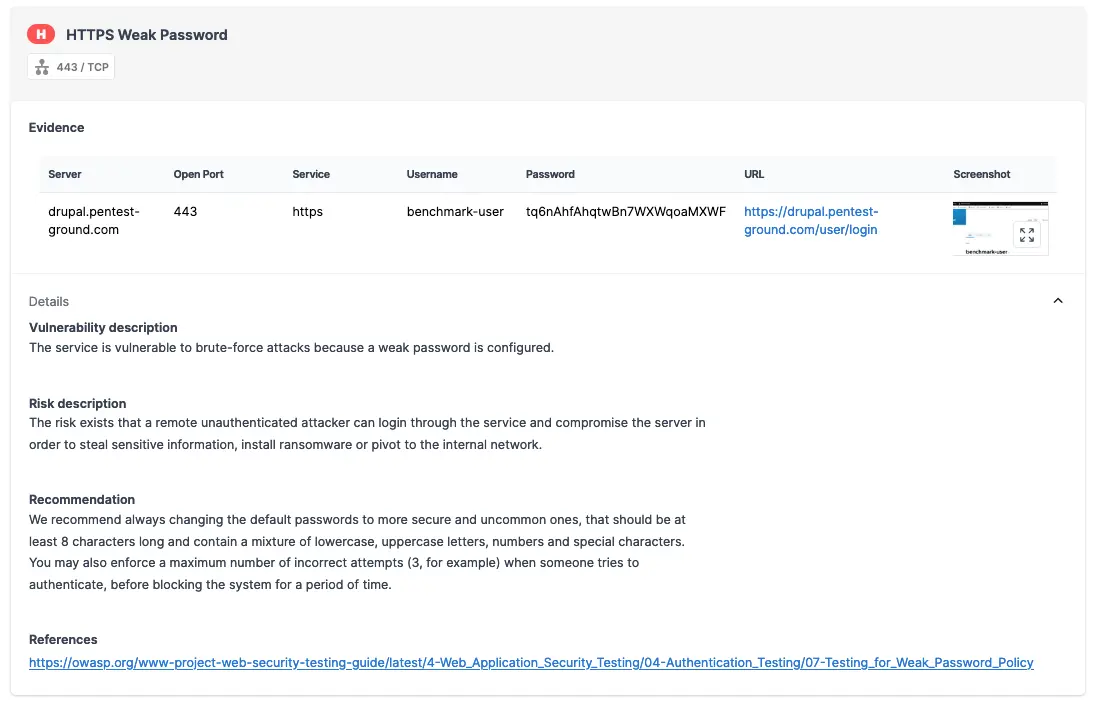
The Password Auditor also includes a screenshot of the logged-in session to confirm that the provided credentials are valid.
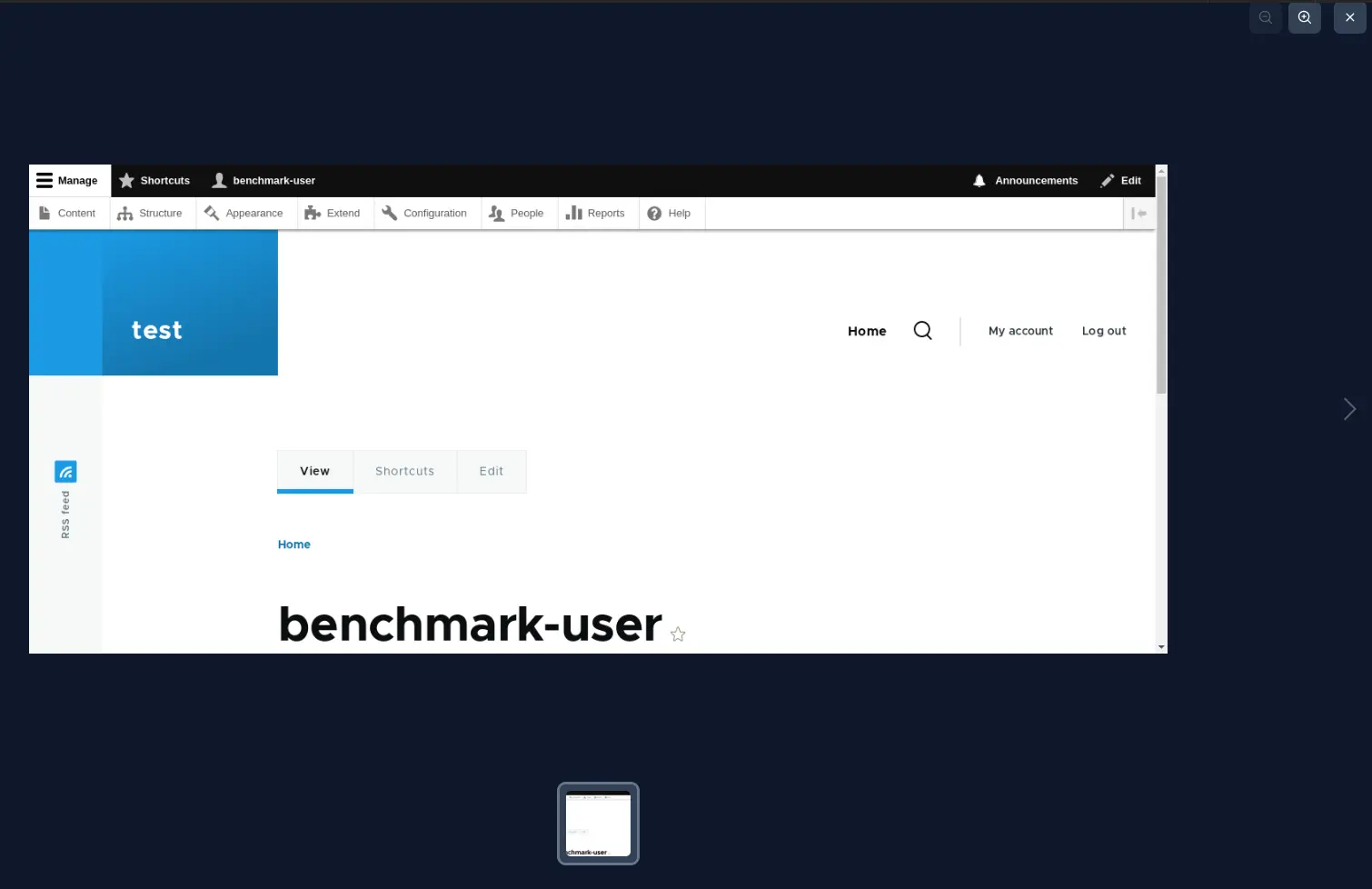
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
The Password Auditor reported both a temporary account lockout and an IP address block error.
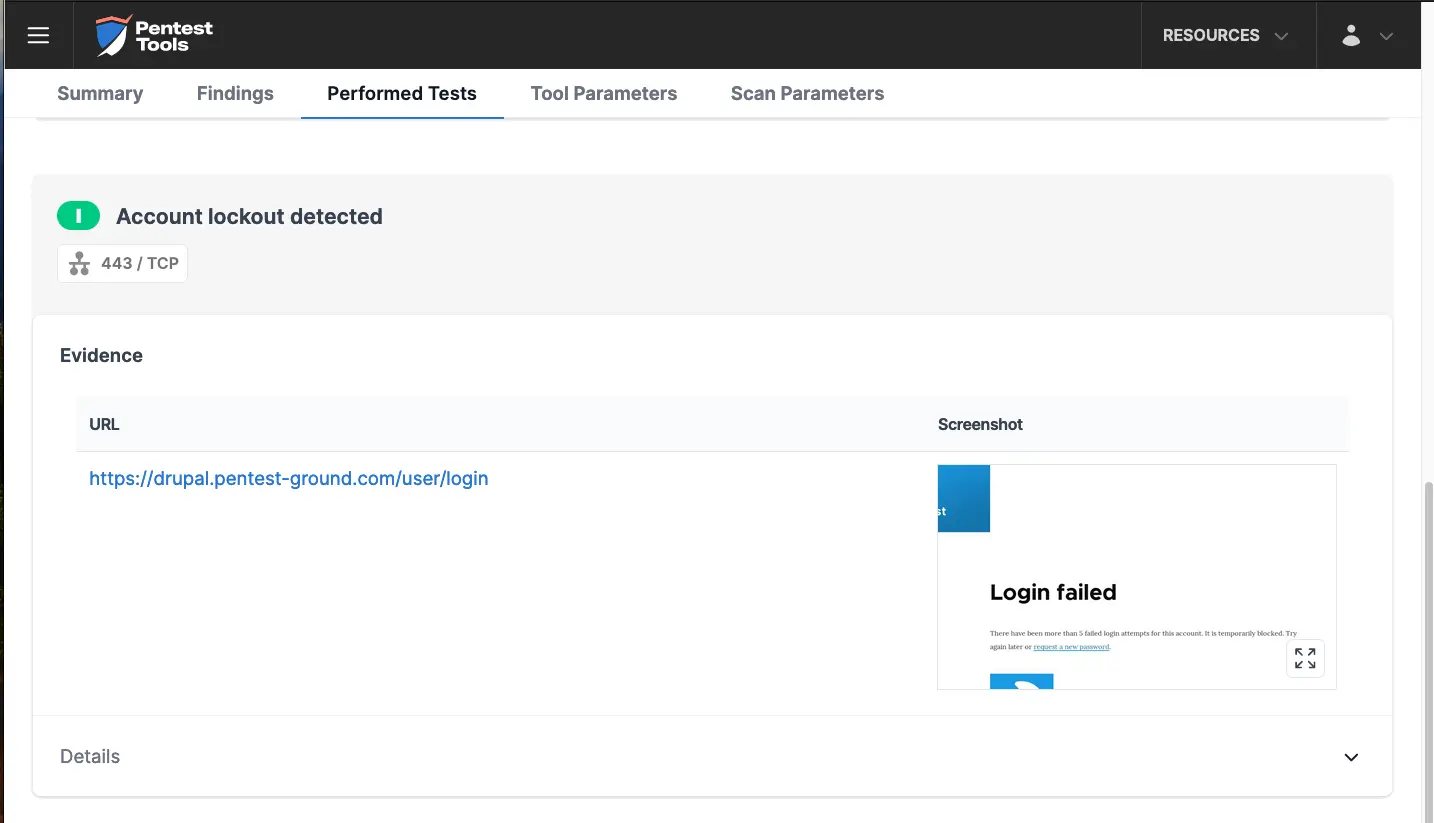
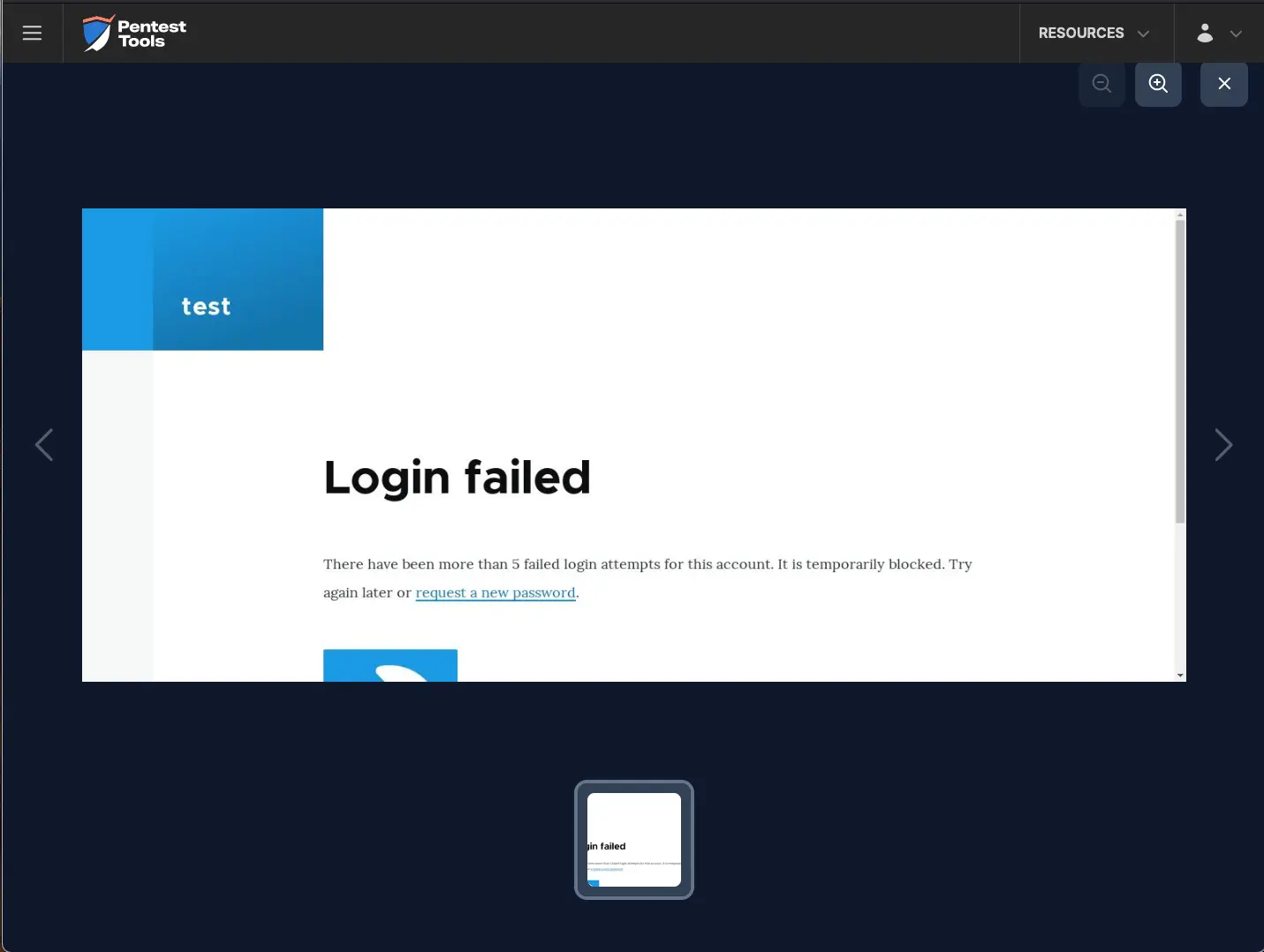
How to check Joomla login for weak credentials
Deployment method: Vultr marketplace
1. Find the Joomla web app login endpoint
Usually, the Joomla login form is found on the / or on the /index.php/component/users/login endpoints.
2. Discover the Joomla login parameters
Use the Network tab in your browser’s Web Developer Tools to identify the parameters.
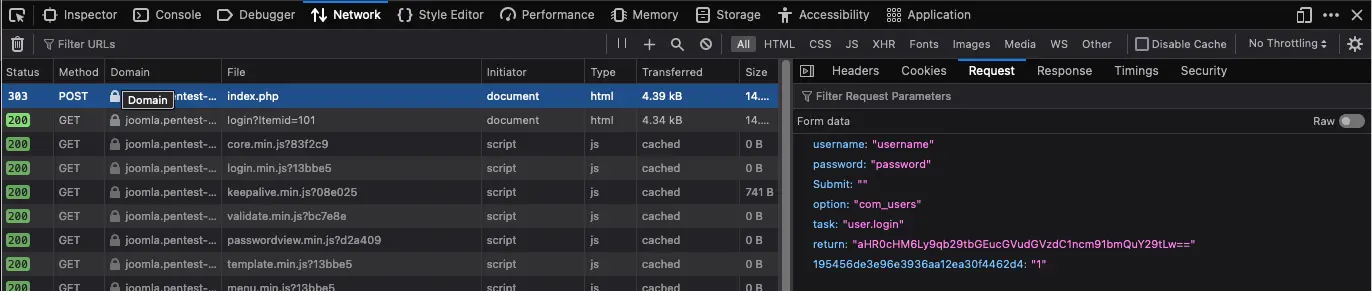
The "return" parameter is a base64-encoded URL to which the user will be redirected after a successful login. Decoding this base64 string would reveal the actual URL.
3. Identify error messages and protection mechanisms
After one invalid attempt, the following message is returned:
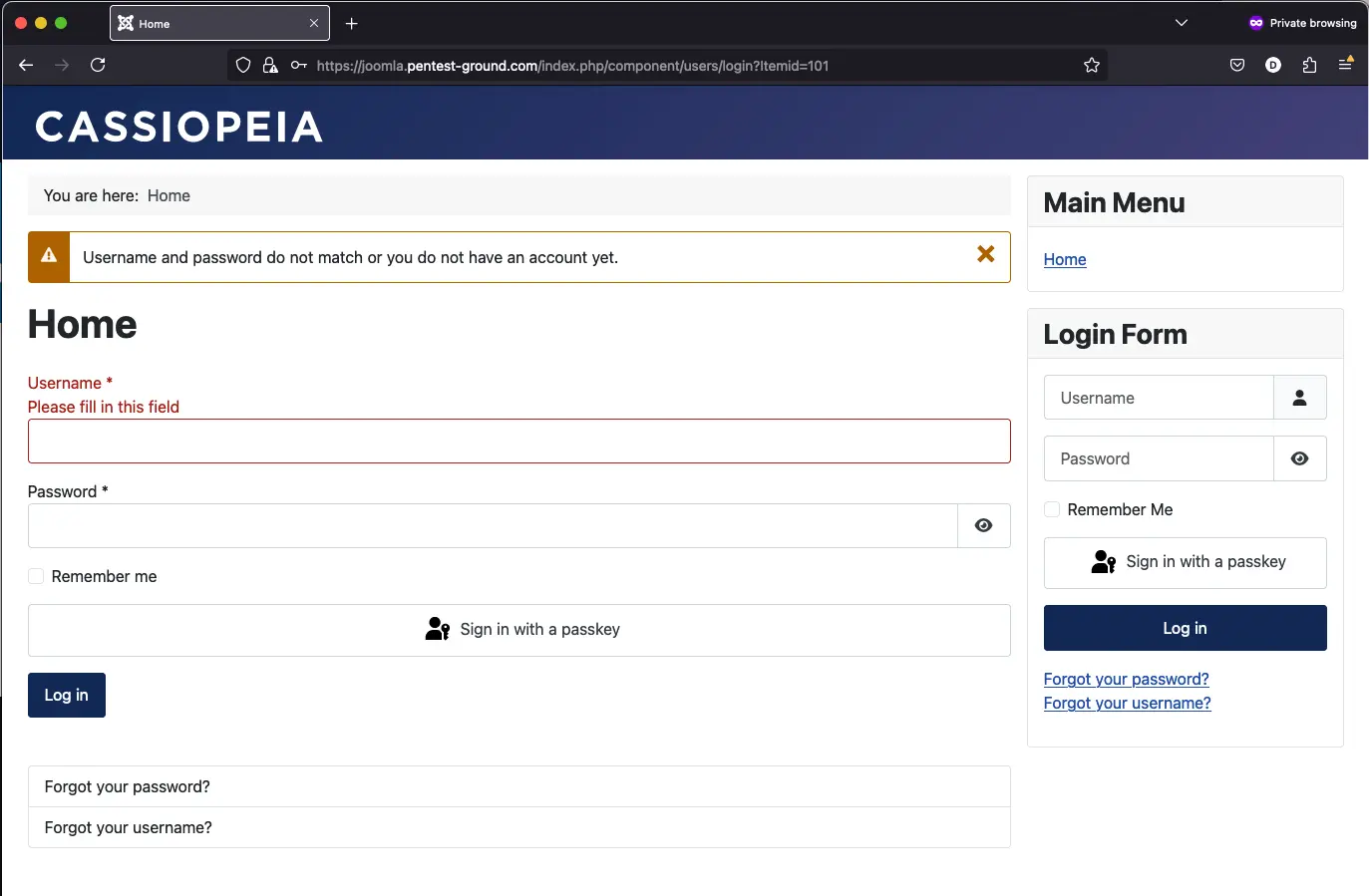
After multiple failed attempts, no protection mechanism came up.
Hydra commands and output
In the first scenario, we used the following Hydra commands to bruteforce the Joomla app:
hydra -l benchmark-user -p bad-password joomla.pentest-ground.com -V https-form-post "/index.php:username=^USER^&passwd=^PASS^&option=com_users&task=user.login&&return=aHR0cHM6Ly9qb29tbGEucGVudGVzdC1ncm91bmQuY29tLw%3D%3D&195456de3e96e3936aa12ea30f4462d4=1:Username and password do not match or you do not have an account yet."hydra -l benchmark-user -p tq6nAhfAhqtwBn7WXWqoaMXWF joomla.pentest-ground.com -V https-form-post "/index.php:username=^USER^&passwd=^PASS^&option=com_users&task=user.login&&return=aHR0cHM6Ly9qb29tbGEucGVudGVzdC1ncm91bmQuY29tLw%3D%3D&195456de3e96e3936aa12ea30f4462d4=1:Username and password do not match or you do not have an account yet."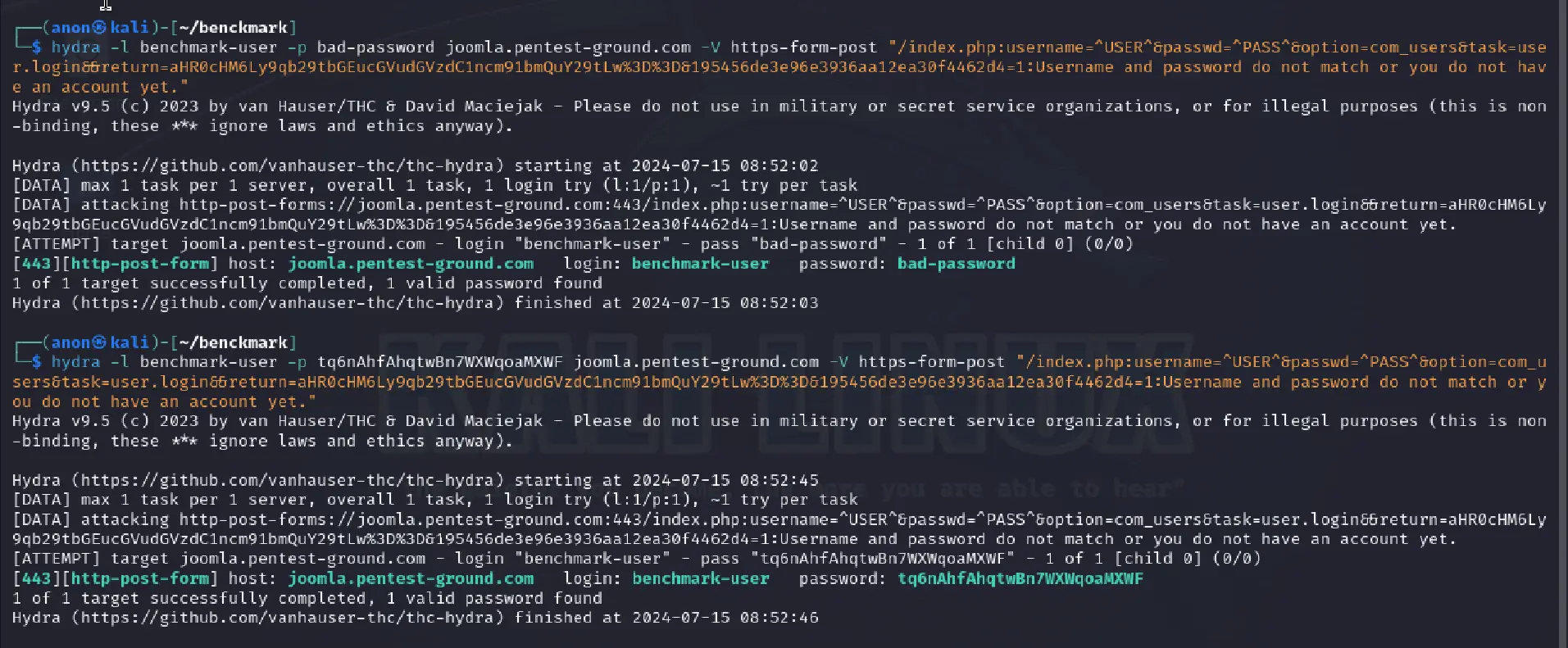
As visible in the output, Hydra failed to distinguish between invalid and valid credentials, marking both as valid.
For the second scenario, we’ve used the following command:
hydra -L users.txt -P pass.txt joomla.pentest-ground.com https-form-post "/index.php:username=^USER^&passwd=^PASS^&option=com_users&task=user.login&&return=aHR0cHM6Ly9qb29tbGEucGVudGVzdC1ncm91bmQuY29tLw%3D%3D&195456de3e96e3936aa12ea30f4462d4=1:Username and password do not match or you do not have an account yet."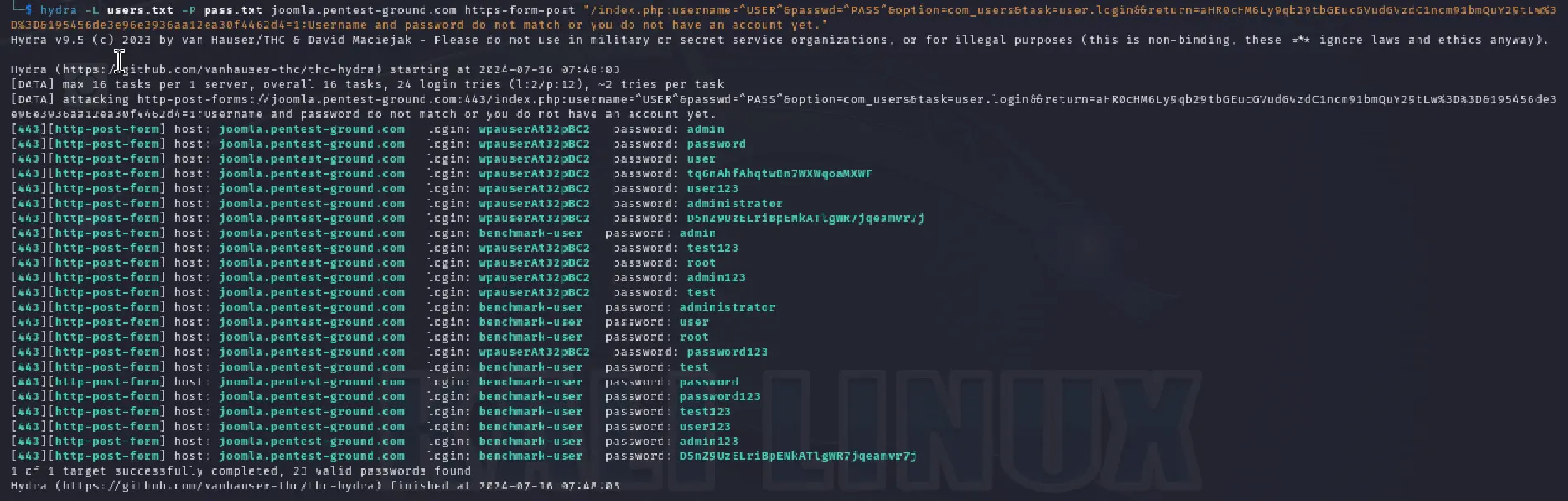
As you can see, Hydra failed to identify any valid credentials, marking all attempts as valid.
Password Auditor commands and results
For the first scenario, we adjusted the following parameters in the interface to conduct a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As shown in the screenshots below, Password Auditor successfully identified the valid credentials.
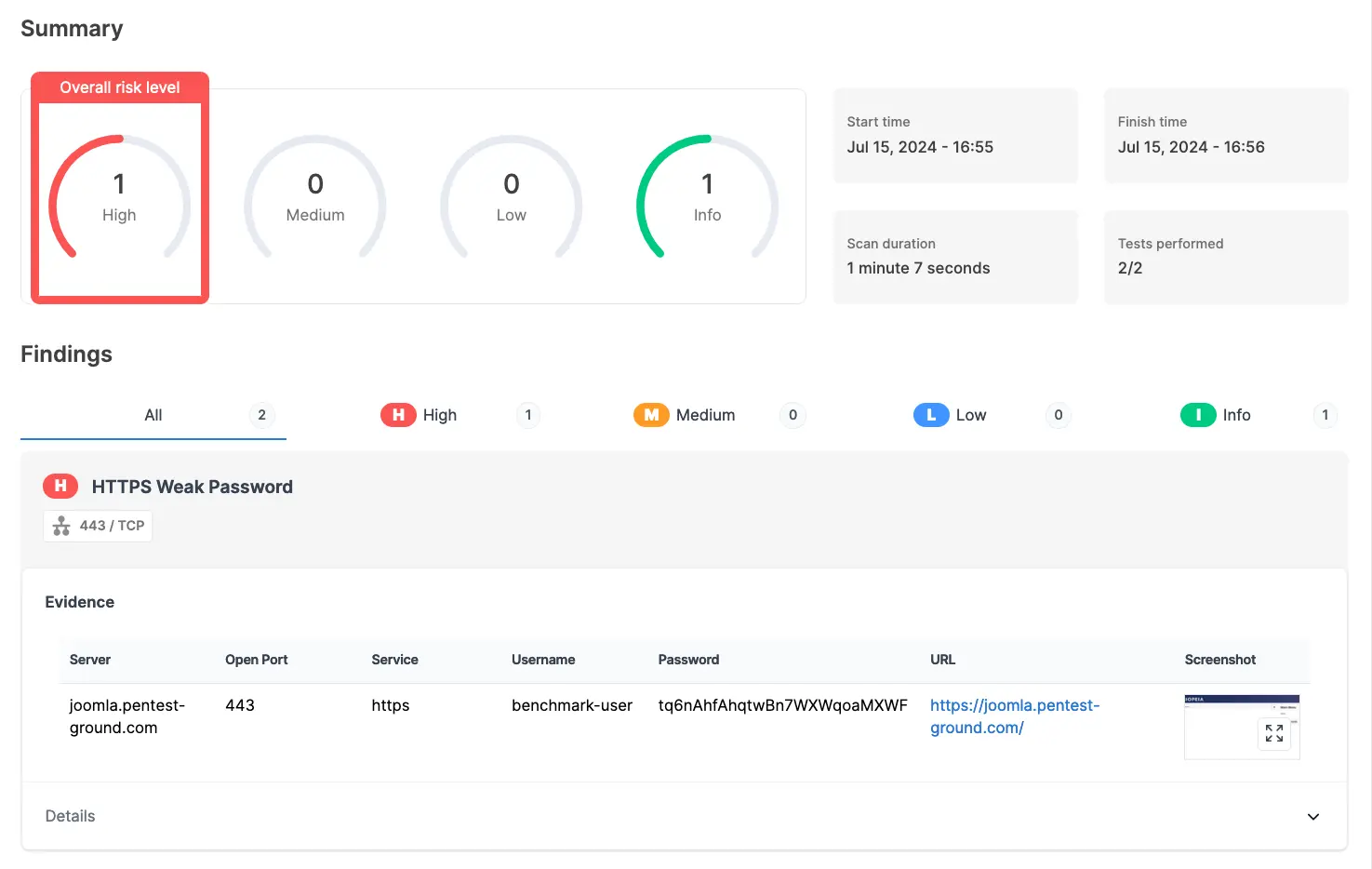
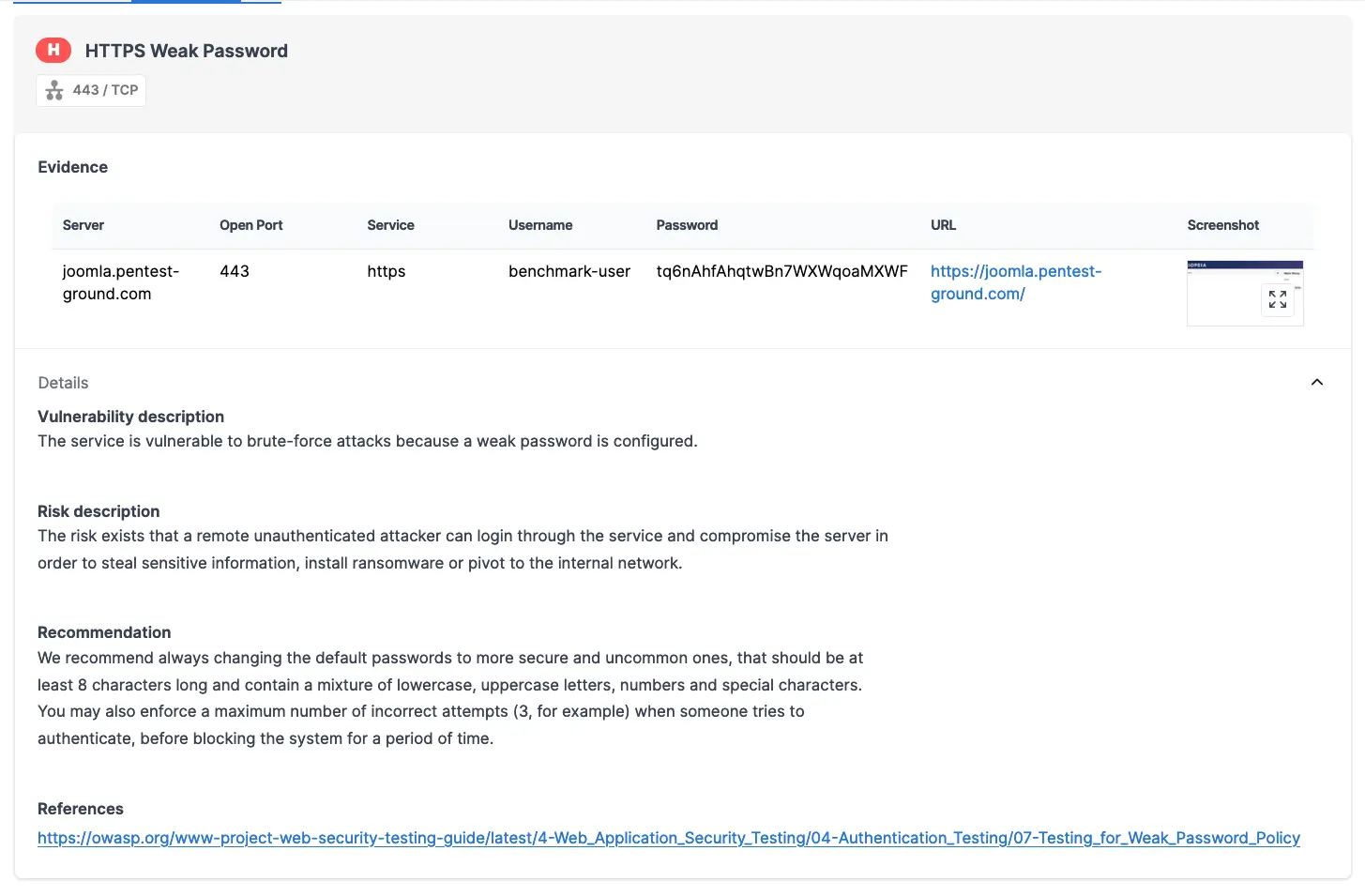
The Password Auditor on Pentest-Tools.com also includes a screenshot of the logged-in session to confirm the provided credentials are valid.
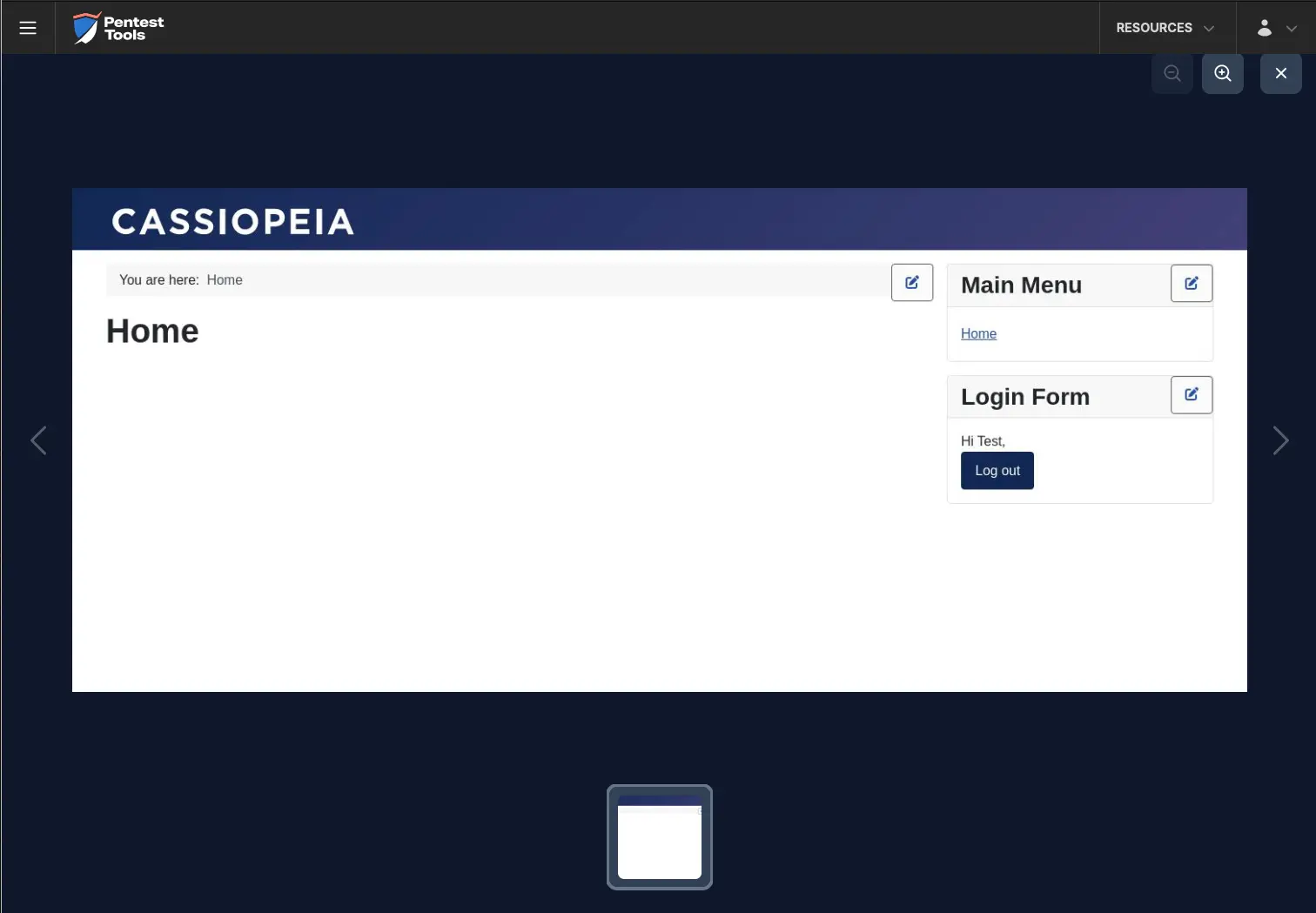
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
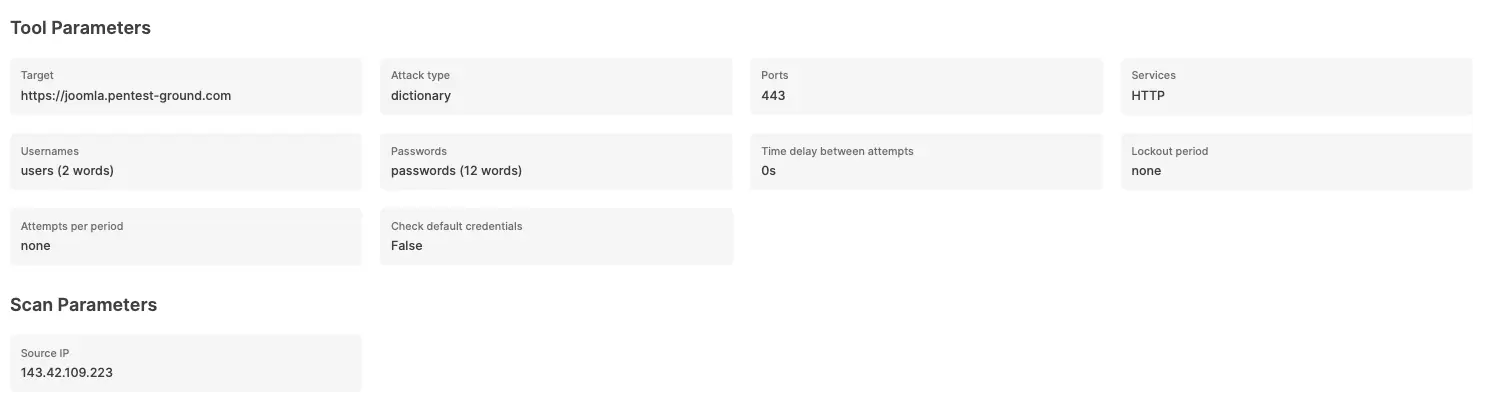
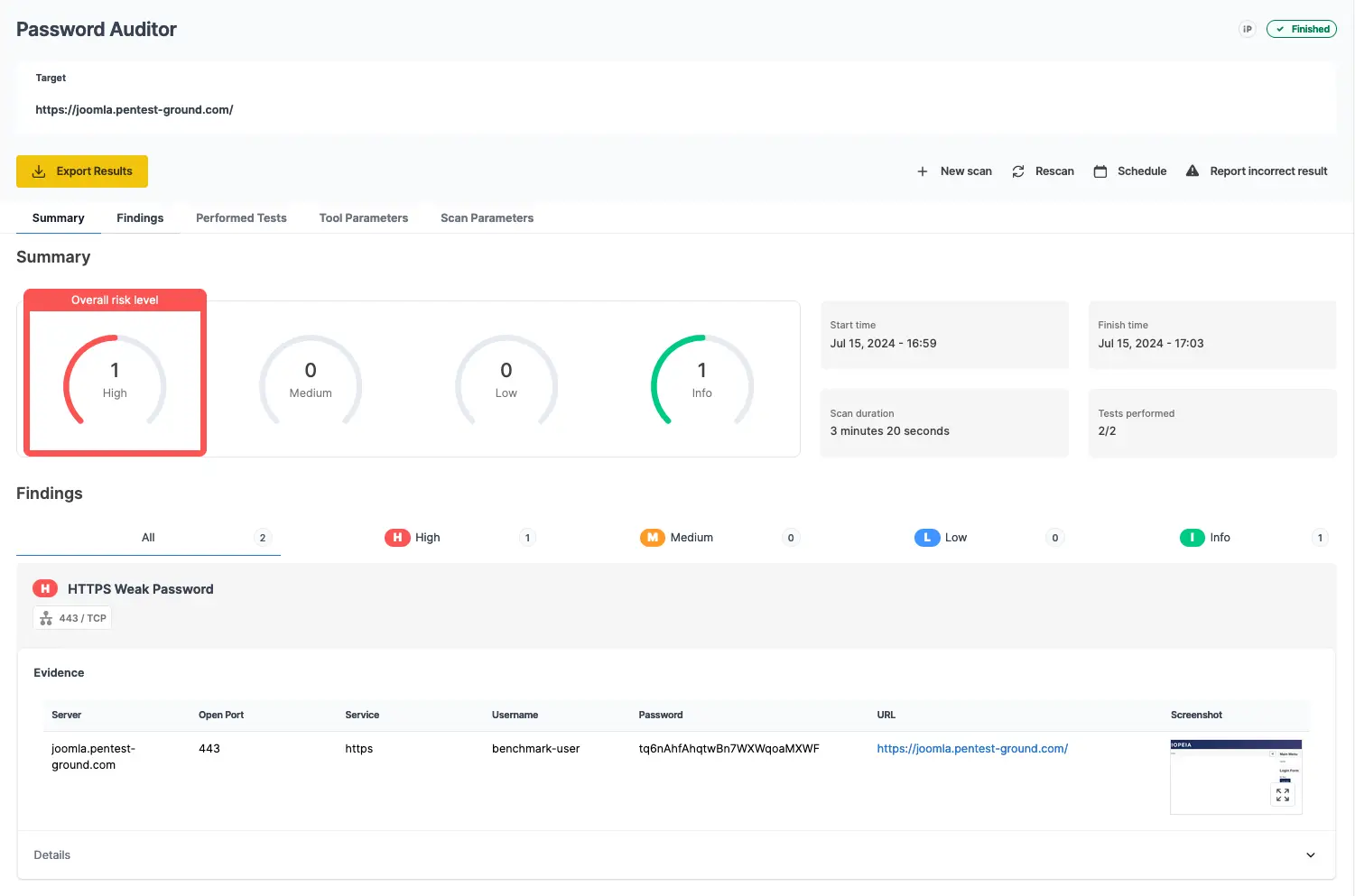
The Password Auditor identified the valid credentials when testing 2 users and 12 passwords.
How to check Joomla administrator for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for Joomla administrator
Usually, Joomla administrator login form is found at /administrator endpoint.
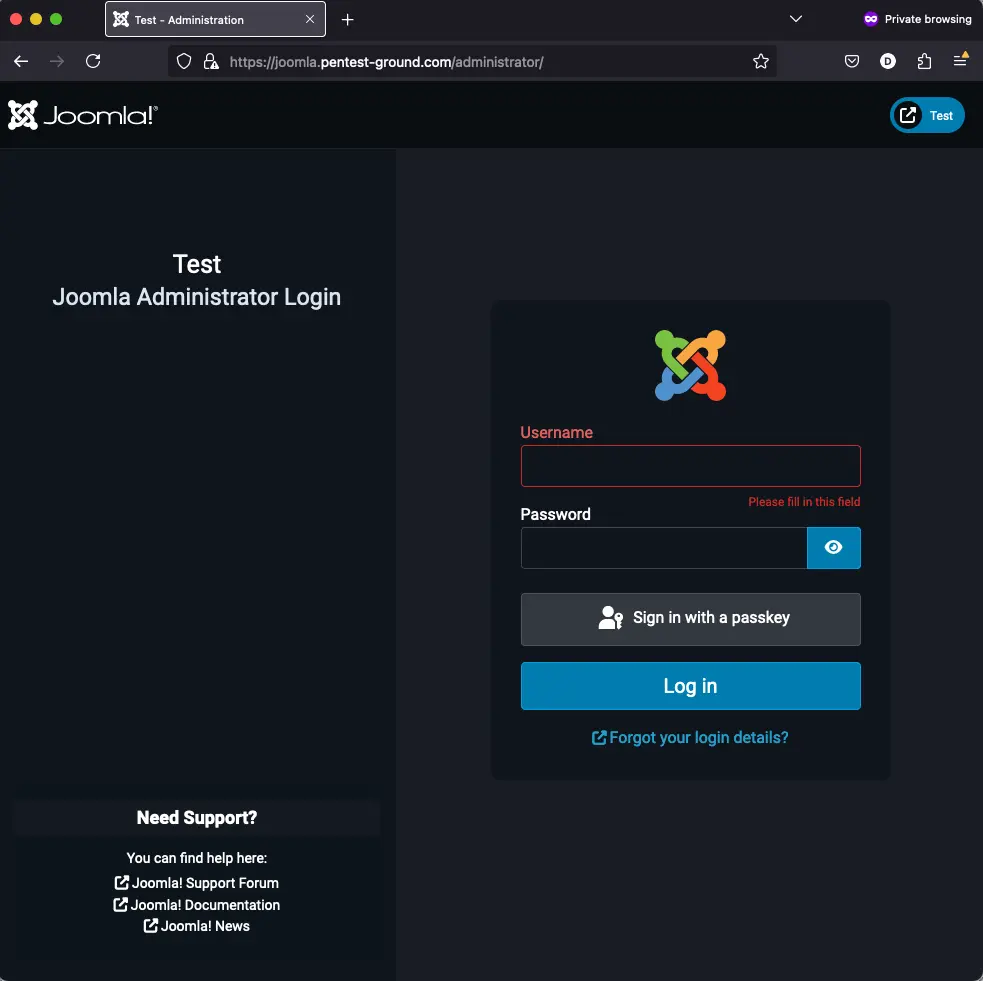
2. Discover the Joomla administrator login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
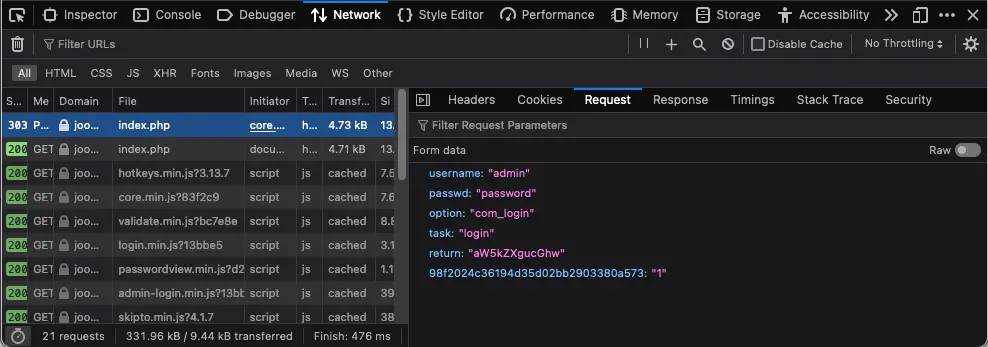
The "return" parameter is a base64-encoded URL to which the user will be redirected after a successful login. Decoding this base64 string reveals the actual URL.
3. Identify error messages and protection mechanisms
After one invalid attempt, the following message is returned:
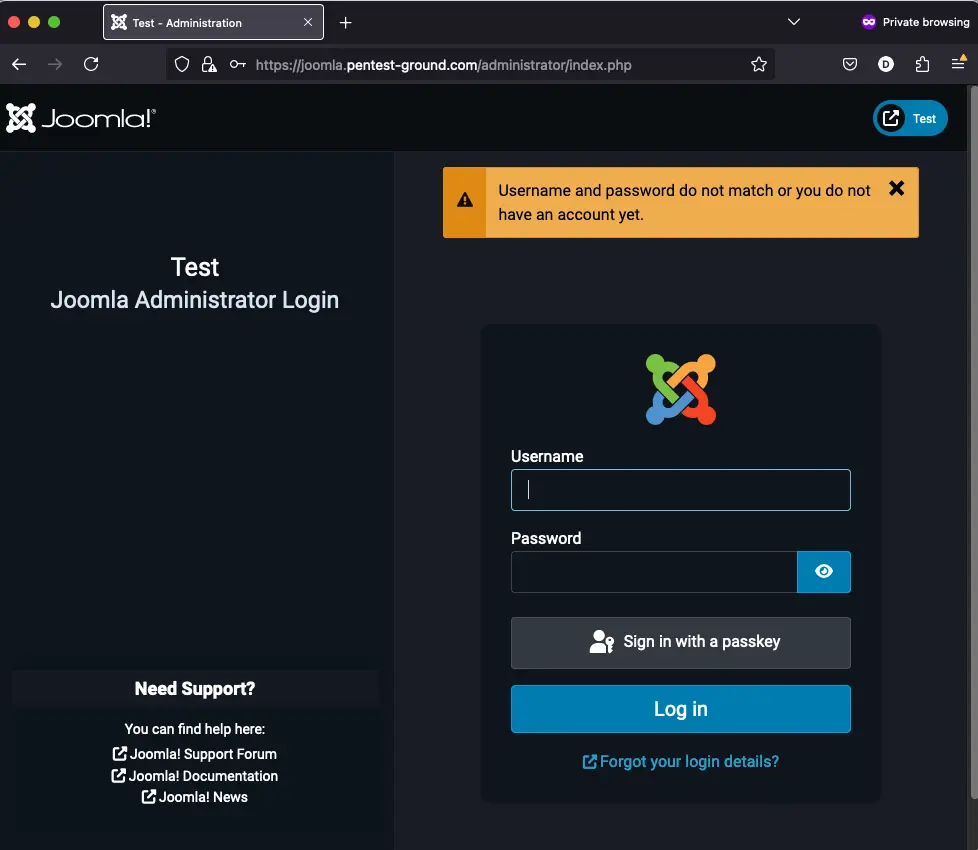
After multiple failed attempts, we didn’t find any protection mechanism.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -l benchmark-user -p bad-password joomla.pentest-ground.com -V https-form-post "/index.php:username=^USER^&passwd=^PASS^&option=com_login&task=login&return=aW5kZXgucGhw&98f2024c36194d35d02bb2903380a573=1:Username and password do not match or you do not have an account yet."hydra -l benchmark-user -p tq6nAhfAhqtwBn7WXWqoaMXWF joomla.pentest-ground.com -V https-form-post "/index.php:username=^USER^&passwd=^PASS^&option=com_login&task=login&return=aW5kZXgucGhw&98f2024c36194d35d02bb2903380a573=1:Username and password do not match or you do not have an account yet."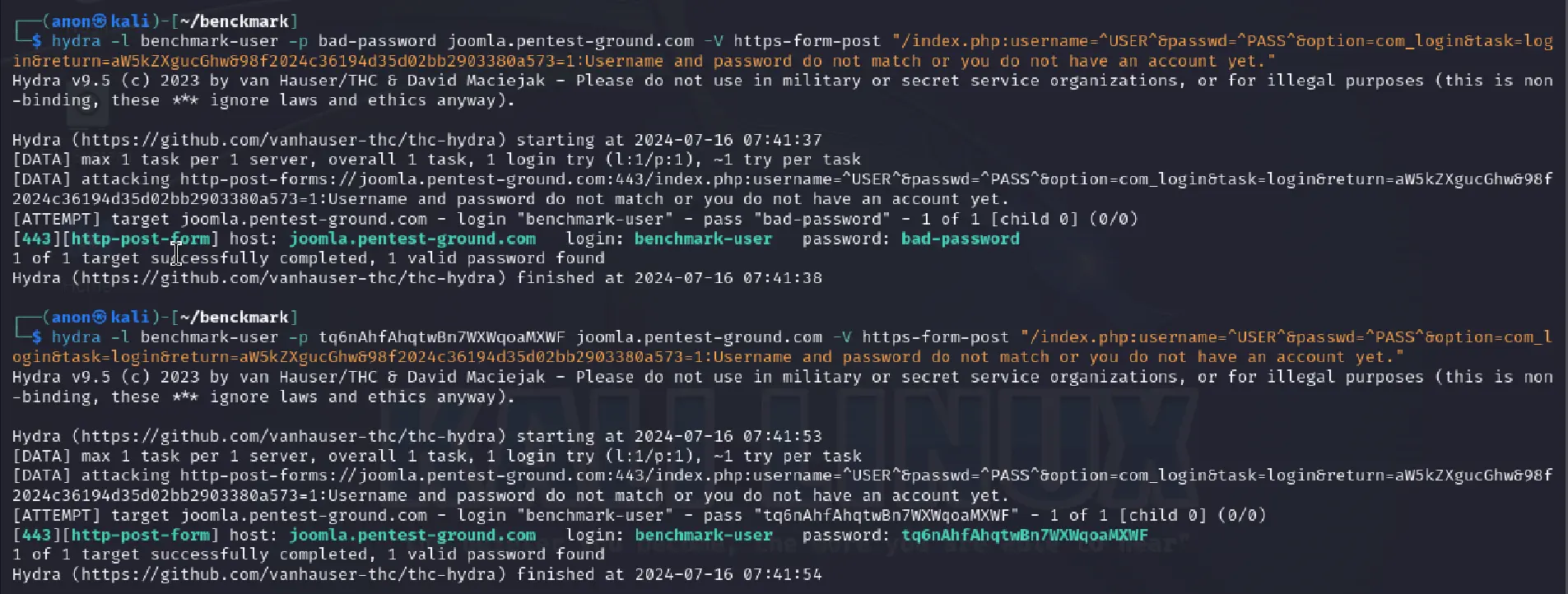
As shown in the output, Hydra failed to distinguish between invalid and valid credentials, marking both as valid.
For the second, more realistic scenario, we used the following command:
hydra -L users.txt -P pass.txt joomla.pentest-ground.com -V https-form-post "/index.php:username=^USER^&passwd=^PASS^&option=com_login&task=login&return=aW5kZXgucGhw&98f2024c36194d35d02bb2903380a573=1:Username and password do not match or you do not have an account yet."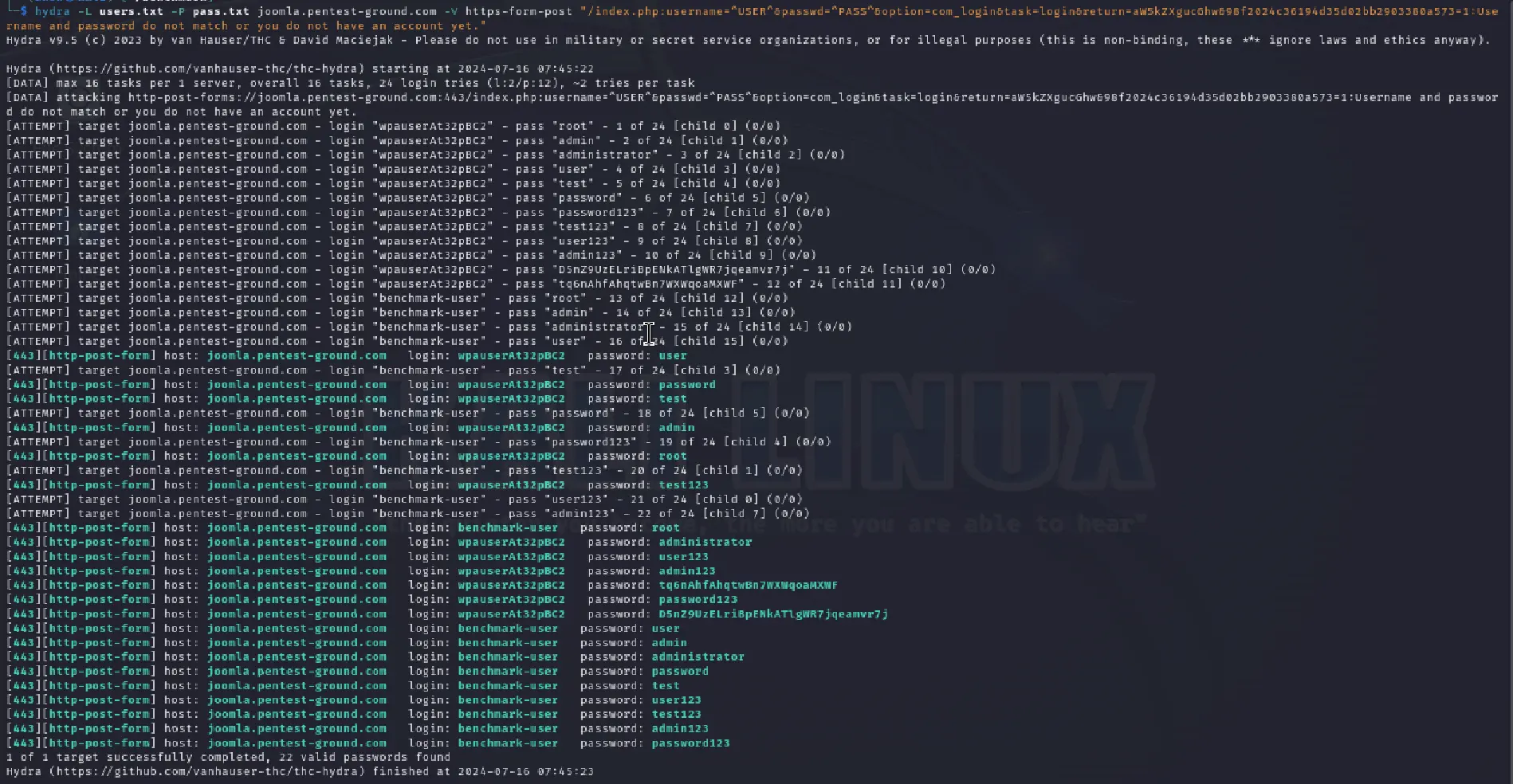
As you can see, Hydra failed to identify any valid credentials.
Password Auditor commands and results
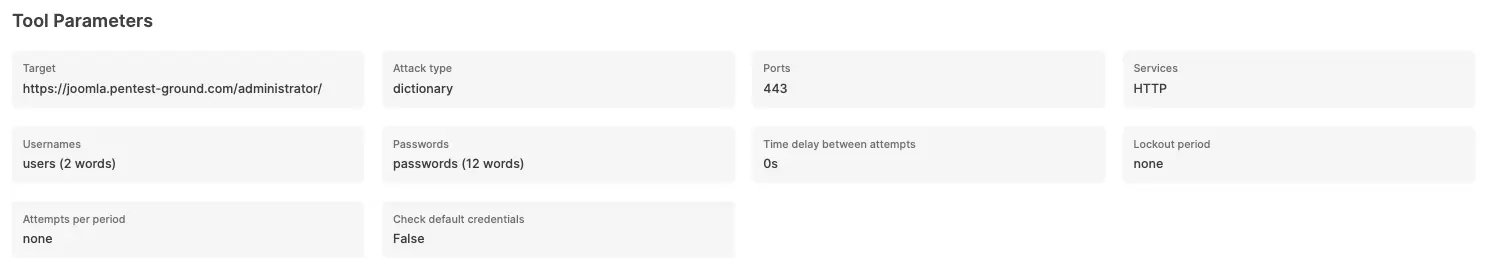
For the first scenario, we adjusted the following parameters in the interface to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As shown in the screenshots below, the Password Auditor successfully identified the valid credentials.
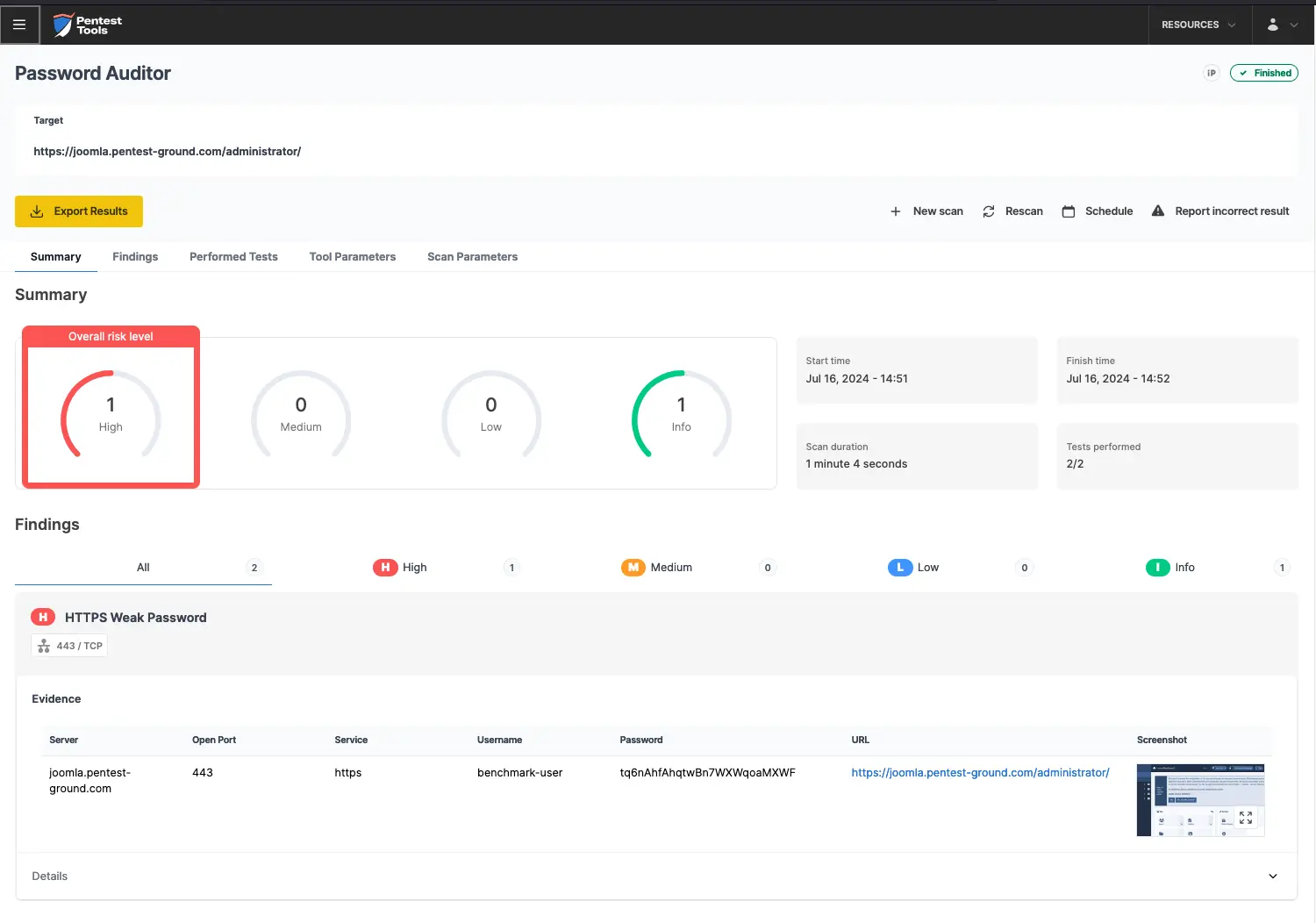
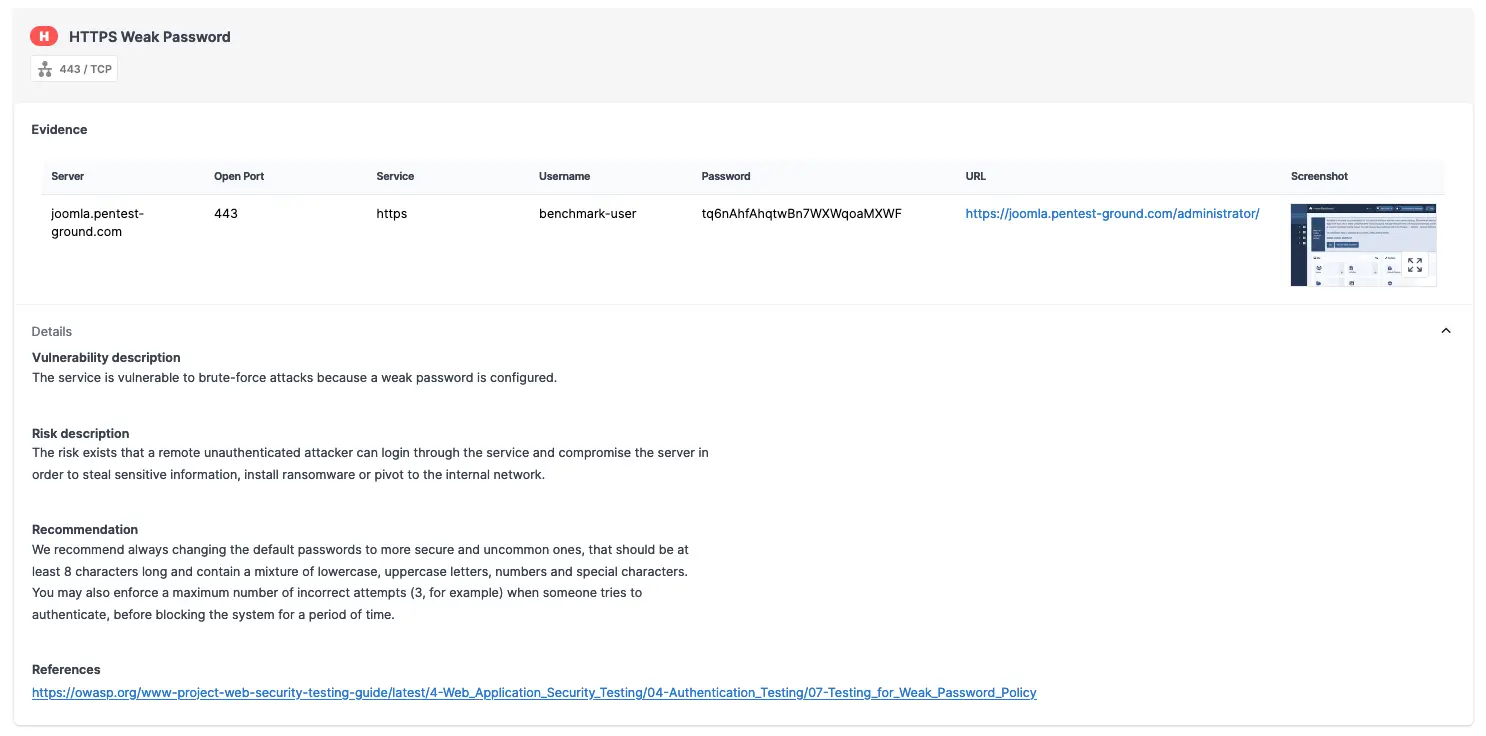
The Pentest-Tools.com Password Auditor also provides a screenshot of the logged-in session to confirm that the provided credentials are valid.
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
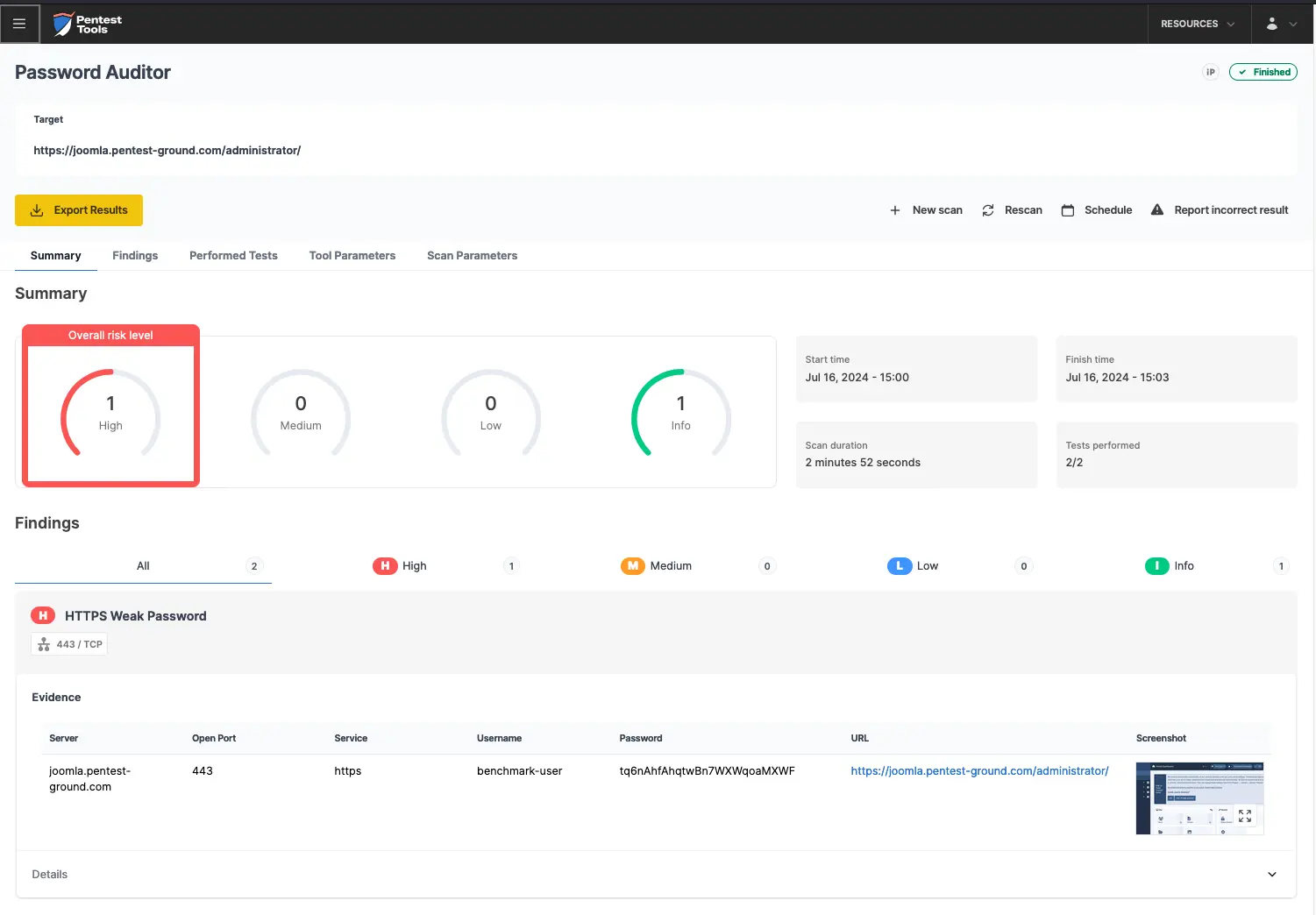
The Password Auditor identified the valid credentials when testing 2 users and 12 passwords.
How to check PrestaShop for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for PrestaShop
The default admin login page for PrestaShop is typically located at /admin. However, during installation, PrestaShop prompts you to rename the /admin directory for security reasons.
The renamed endpoint would look something like /admin123, where admin123 is a randomly generated or manually chosen name.
Vultr has created the /admin_area/ link as a convenient static URL.
2. Discover the PrestaShop login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
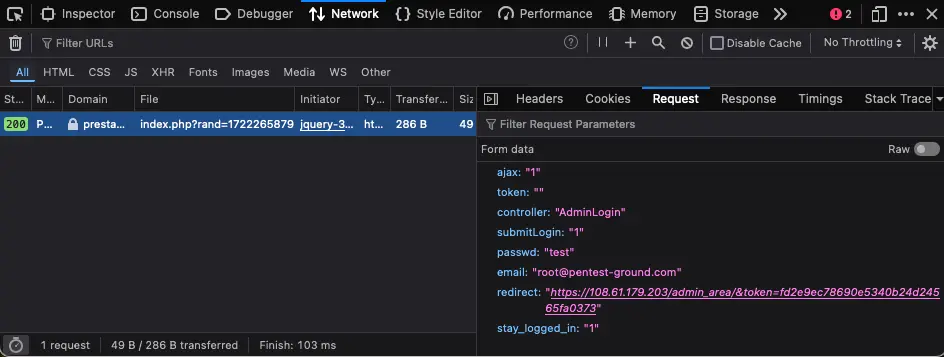
In PrestaShop, the redirect parameter often contains a CSRF (Cross-Site Request Forgery) token. This is used to ensure the security of redirect actions by verifying they are legitimate and come from a trusted source.
3. Identify error messages and protection mechanisms
After one invalid attempt, PrestaShop returns the following message:
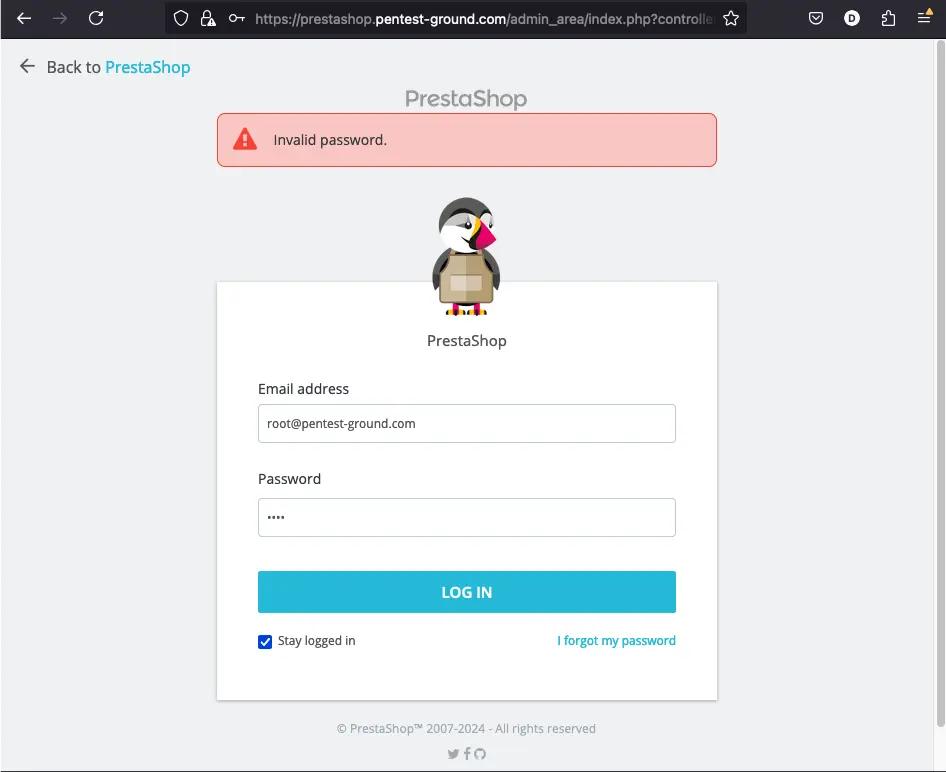
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -l "root@pentest-ground.com" -p bad-password prestashop.pentest-ground.com https-post-form "/admin_area/index.php:ajax=1&token=&controller=AdminLogin&submitLogin=1&passwd=^PASS^&email=^USER^&redirect=https%3A%2F%2F108.61.179.203%2Fadmin_area%2F%26token%3Dfd2e9ec78690e5340b24d24565fa0373&stay_logged_in=1:Invalid password." -Vhydra -l "root@pentest-ground.com" -p iY5Na7ZIa3WPgrh3zrVgYdQmF6rnNCtb prestashop.pentest-ground.com https-post-form "/admin_area/index.php:ajax=1&token=&controller=AdminLogin&submitLogin=1&passwd=^PASS^&email=^USER^&redirect=https%3A%2F%2F108.61.179.203%2Fadmin_area%2F%26token%3Dfd2e9ec78690e5340b24d24565fa0373&stay_logged_in=1:Invalid password." -V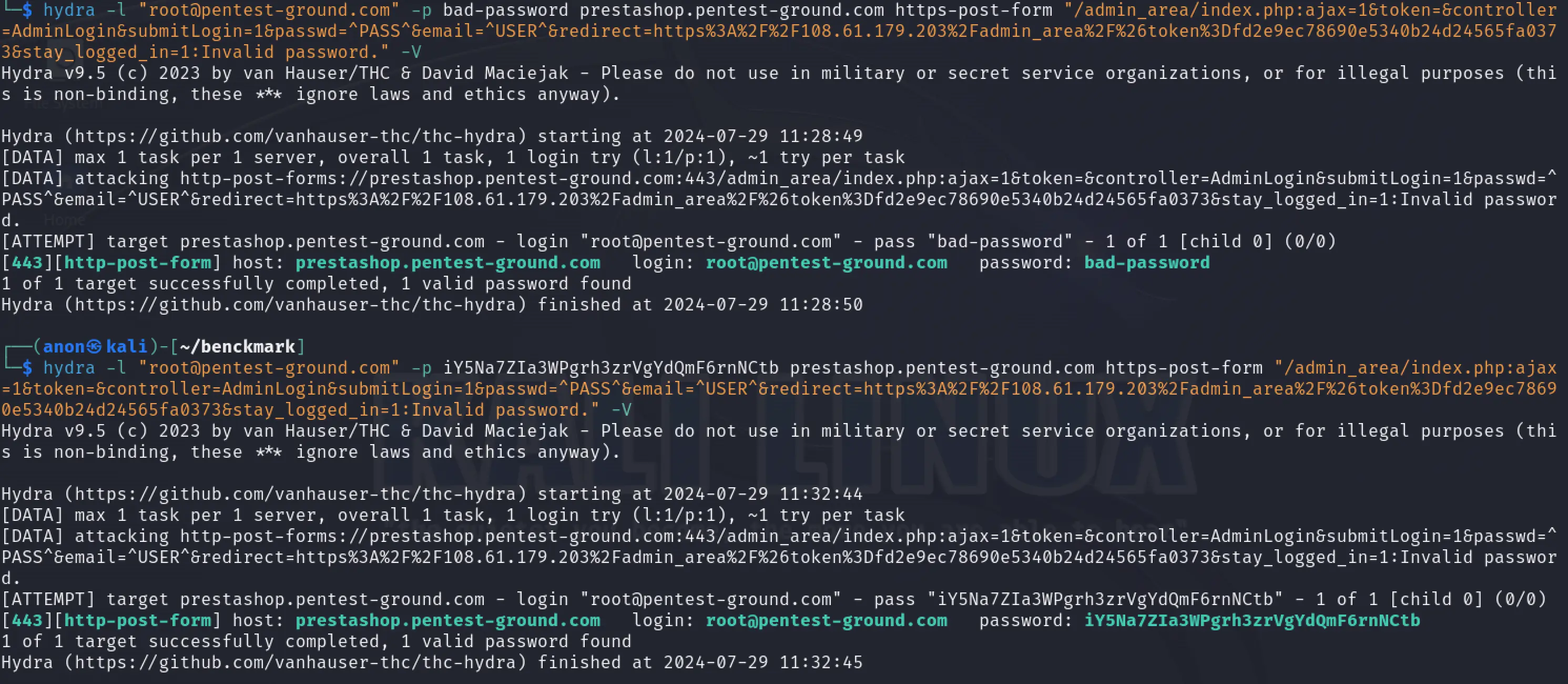
PrestaShop uses the redirect parameter as a CSRF token, which changes with each request. Since Hydra requires this parameter to be configured as static, it cannot generate these tokens. Consequently, Hydra marked both attempts as valid credentials.
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Target: https://prestashop.pentest-ground.com/admin_area/index.php
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
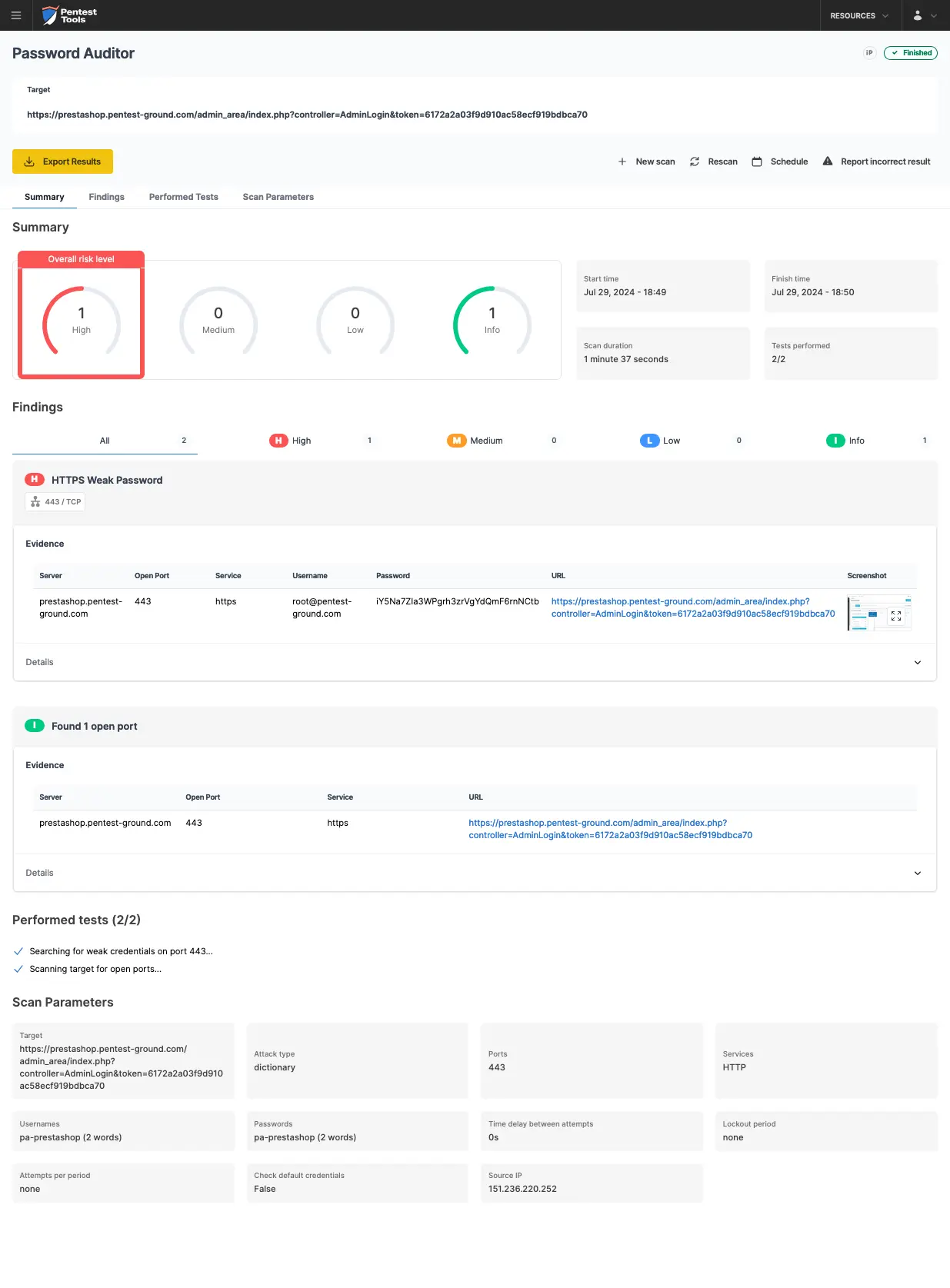
The Pentest-Tools.com Password Auditor also includes a screenshot of the logged-in session to confirm the provided credentials are valid.
For the second scenario, we only changed the wordlist to include 2 users (1 invalid and 1 valid) and 13 passwords (12 invalid and 1 valid).
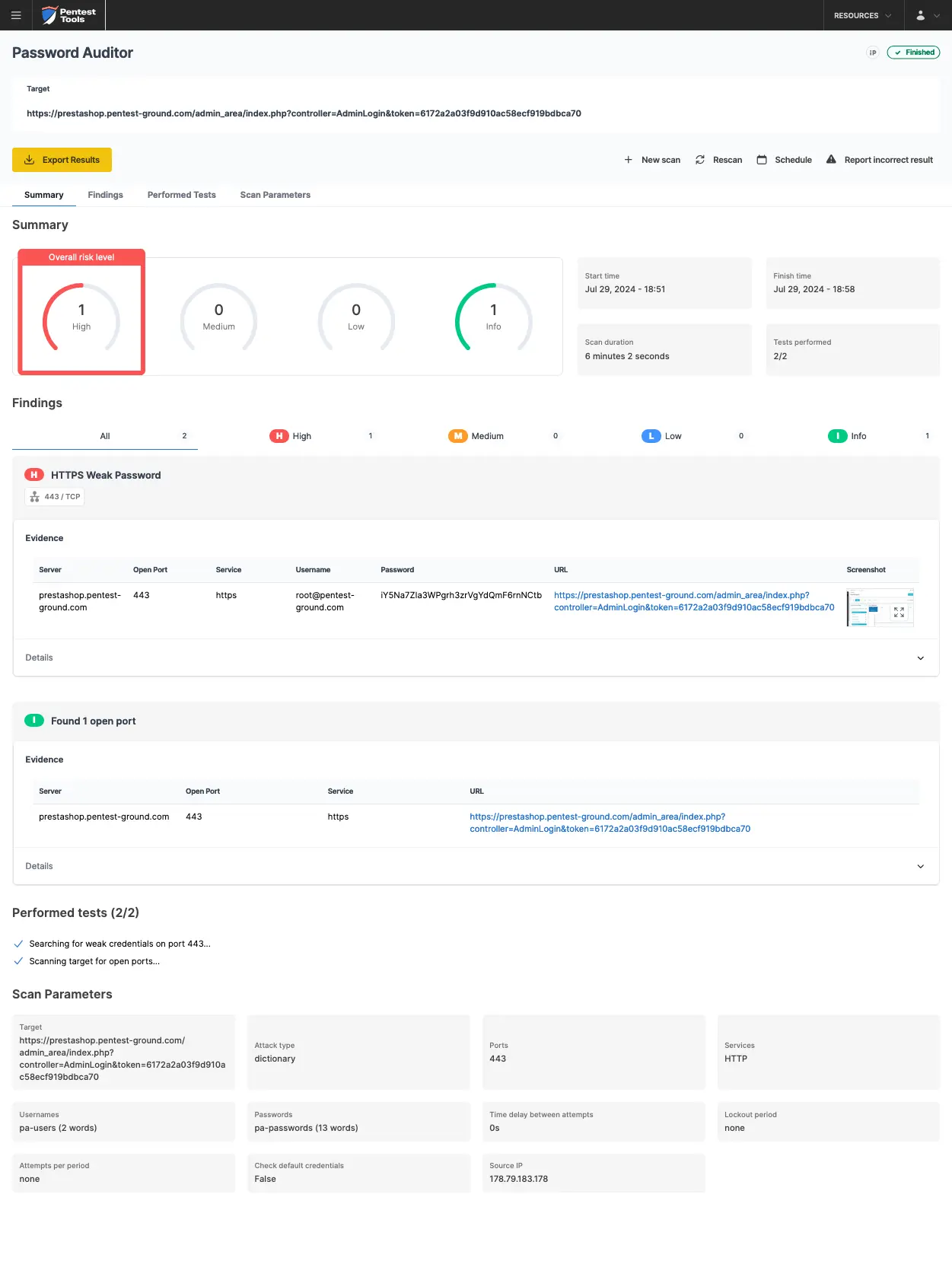
In the second scenario, the Password Auditor on Pentest-Tools.com identified the valid credentials.
How to check Magento for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for Magento
The default admin login page for Magento is typically located on the /admin endpoint on port 443.

2. Discover the Magento login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
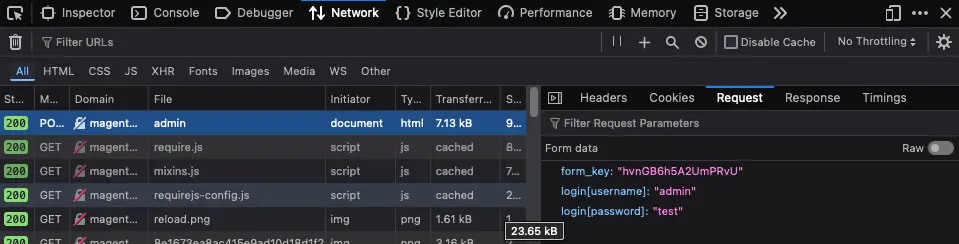
In Magento, the form_key parameter is a critical security feature used to prevent Cross-Site Request Forgery (CSRF) attacks. It ensures the form submission is coming from the same site and session, protecting the website and its users from malicious actions.
3. Identify error messages and protection mechanisms
After one invalid attempt, Magento returns the following message:
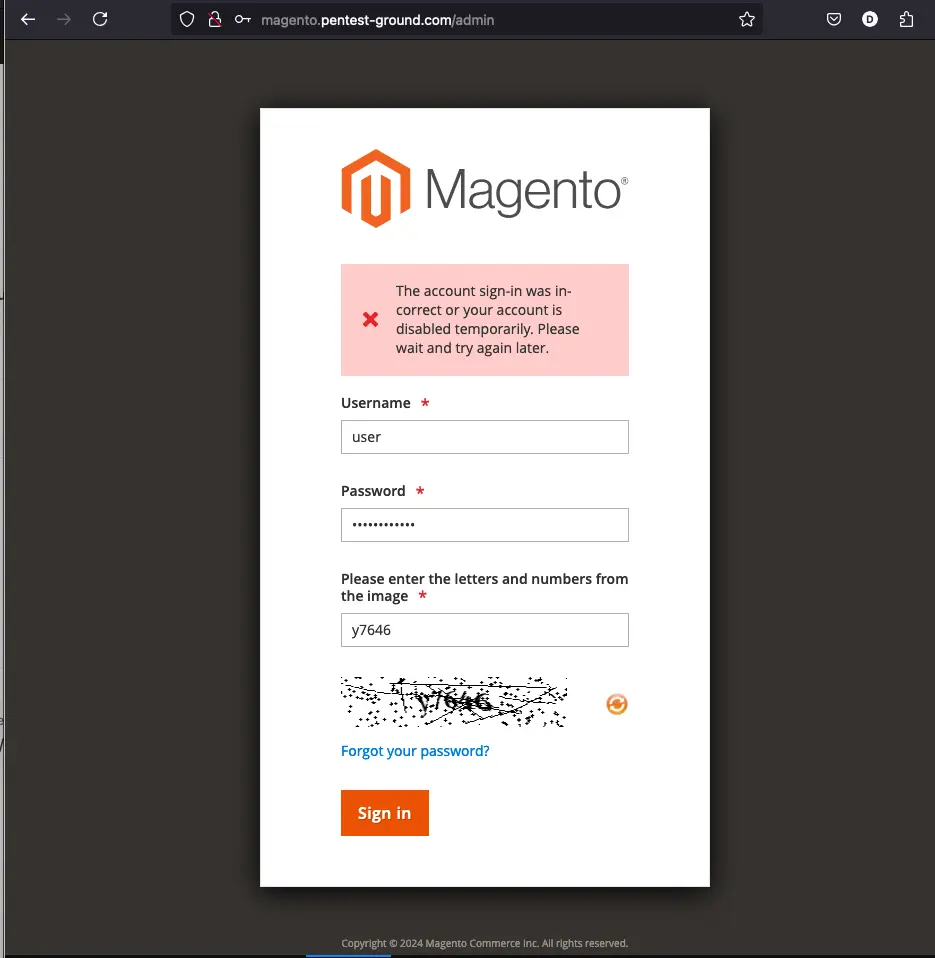
The application has a basic anti-brute-force mechanism: the CAPTCHA gets activated after several failed login attempts, and the account can be temporarily disabled.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands to bruteforce Magento:
hydra -l user -p bad-password magento.pentest-ground.com http-post-form "/admin/:form_key=7sqshgljTsjOGZtB&login%5Busername%5D=^USER^&login%5Bpassword%5D=^PASS^:The account sign-in was incorrect" -Vhydra -l user -p 5CIaEBMqlcwN magento.pentest-ground.com http-post-form "/admin/:form_key=7sqshgljTsjOGZtB&login%5Busername%5D=^USER^&login%5Bpassword%5D=^PASS^:The account sign-in was incorrect" -V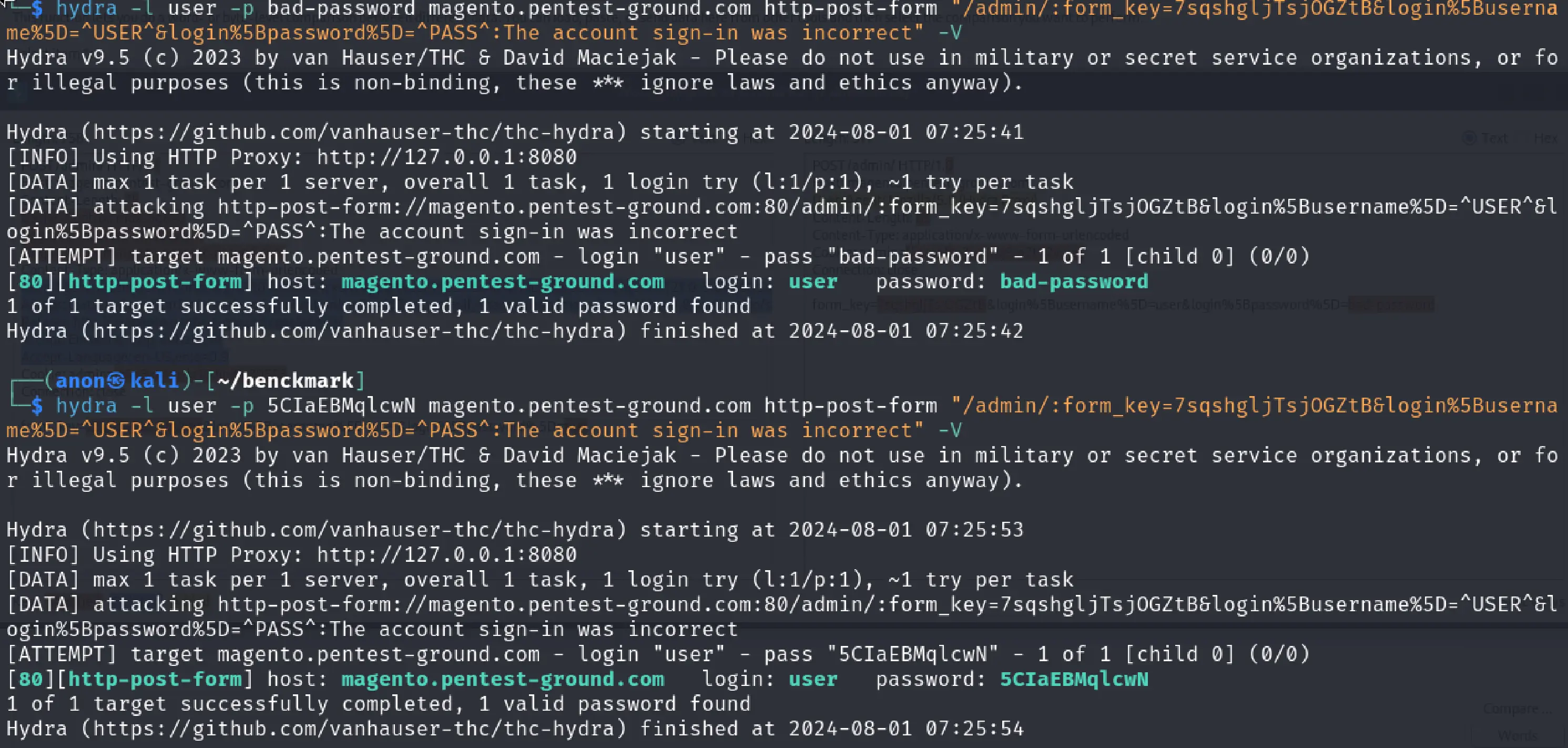
As explained in the section about discovering Magento parameters, the `form_key` is used as a CSRF token and is dynamically set. Hydra cannot use a session to automatically set this parameter, so it incorrectly marks both invalid and valid credentials as valid.
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
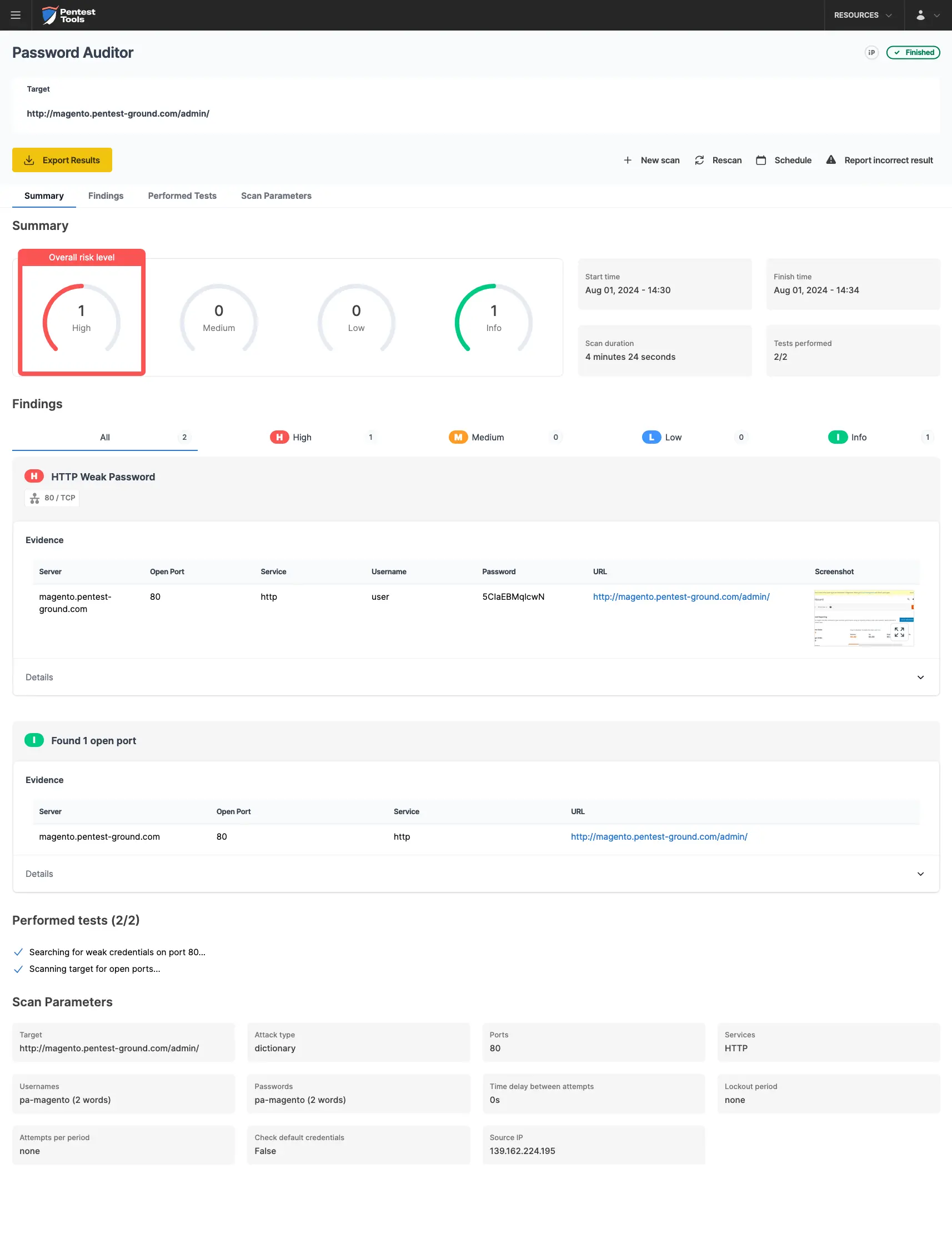
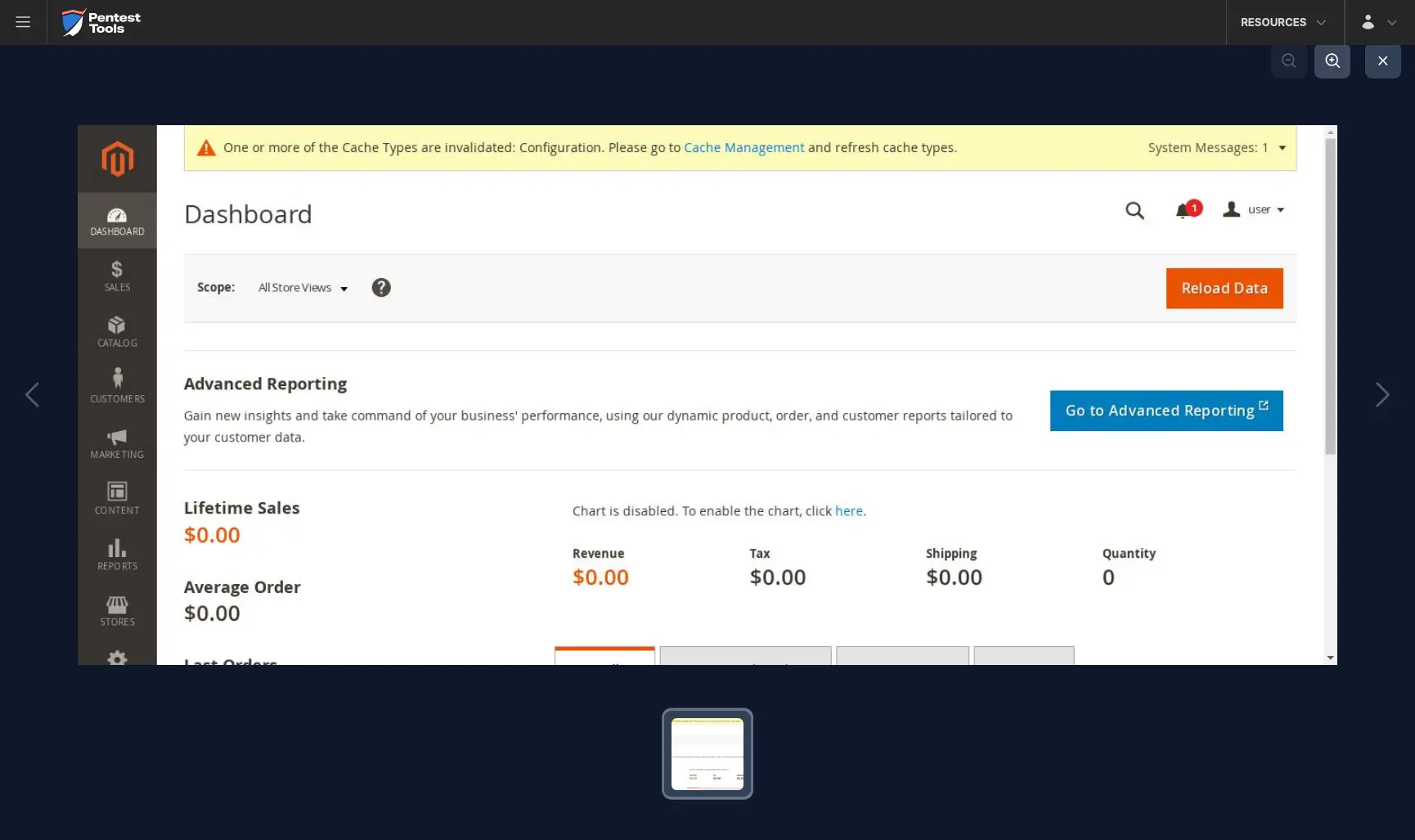
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we adjusted the wordlist to include 2 users (1 invalid and 1 valid) and 13 passwords (12 invalid and 1 valid).
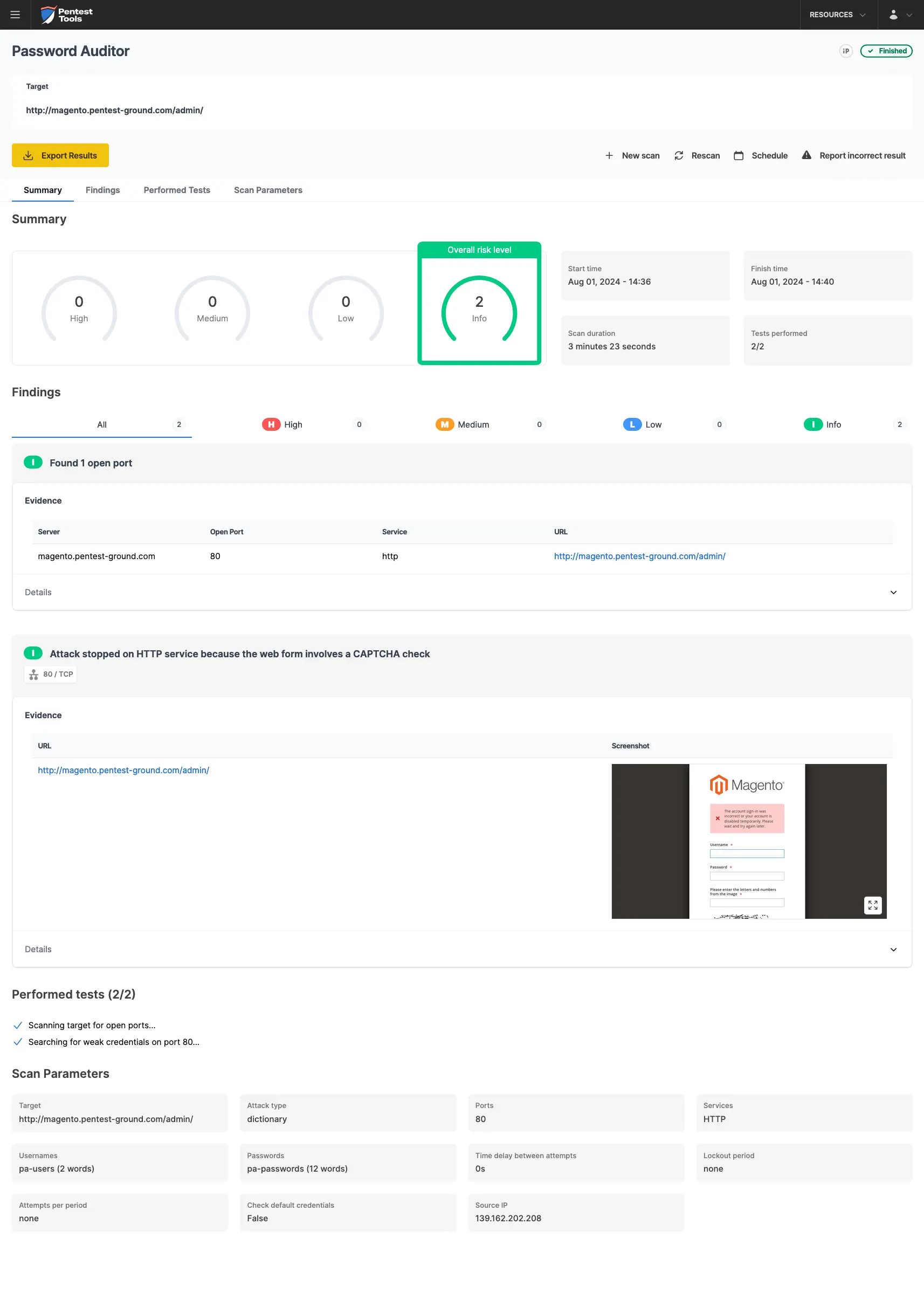
Because Magento activated the CAPTCHA mechanism, the Password Auditor on Pentest-Tools.com reported with an informational finding that the bruteforce stopped because of this.




