Website Recon
Technical details
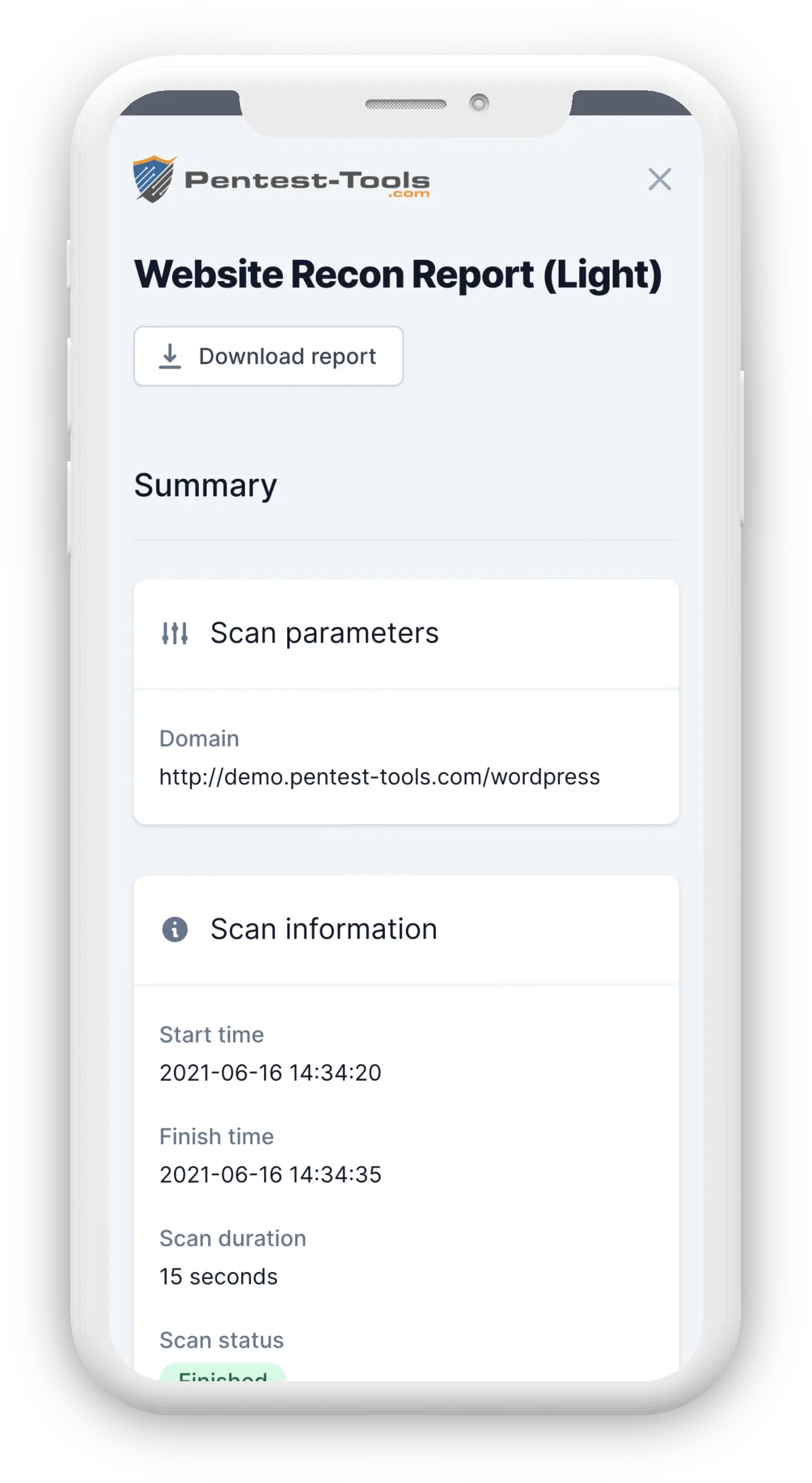
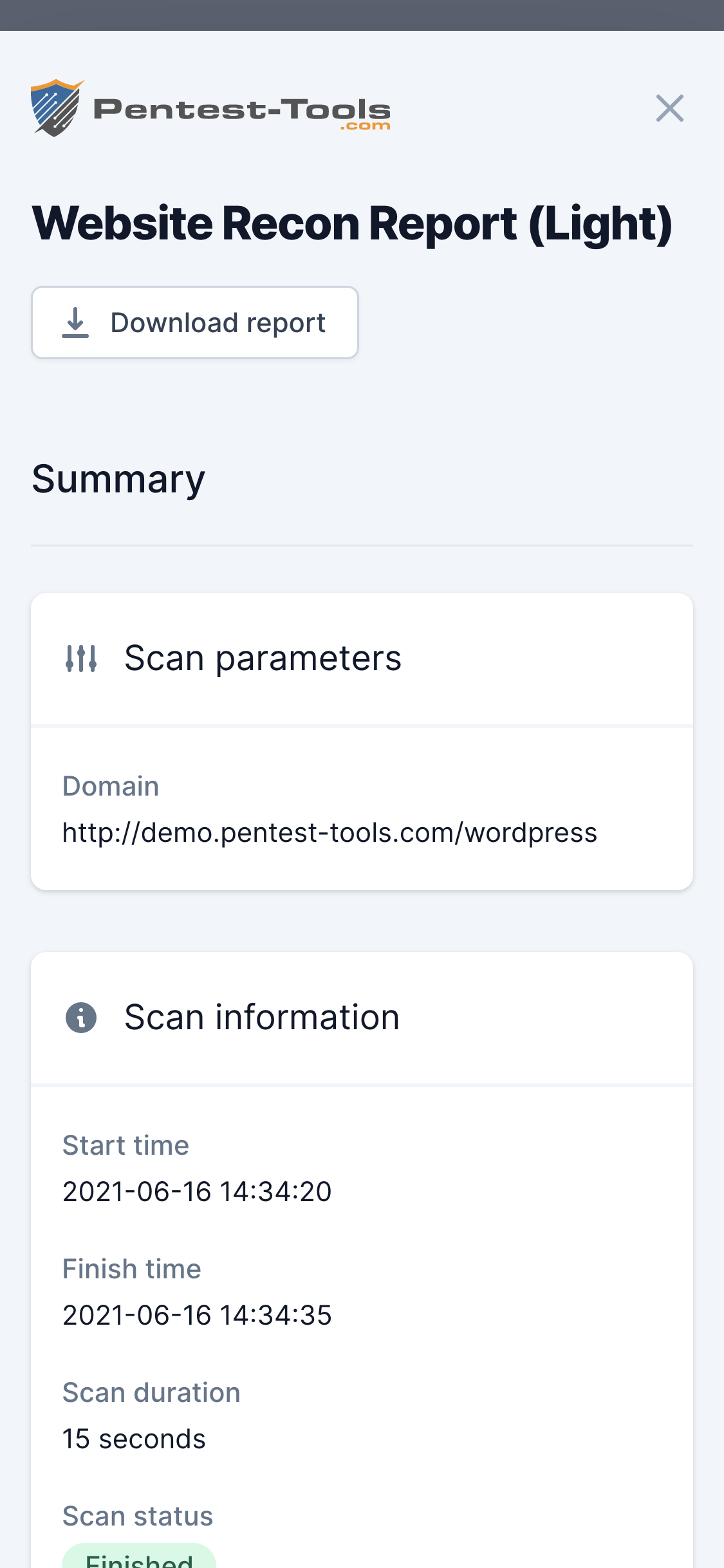
Reconnaissance is the first phase of a penetration test, in which the pentester finds as much information as possible about the target website.
The backend and frontend technologies used by the website can lead to constructing dedicated attack vectors in which the penetration tester exploits specific vulnerabilities of the identified software type and version.
For instance, if the Website Recon tool finds the following information about the target website:
CMS: WordPress 4.1Server: Apache 2.2Operating system: Linux
the next step would be to investigate if the specific version of the software is affected by known vulnerabilities (ex. version 4.1 of WordPress). If such vulnerability is found, the penetration tester can proceed to exploit the vulnerability. The operating system and the server information are also important to select the appropriate exploit to successfully compromise the system.
Parameters
| Parameter | Description |
|---|---|
| Target URL | Is the address of the website which will be searched for known technologies |
| Scan single website | The tool accesses a single URL and detects existing technologies (default option) |
| Scan IP address | The tool first determines the open web ports on the target IP (80, 81, 8080, 443, 8443), then finds the DNS names (virtual hosts) associated with the IP, and lastly it initiates HTTP(S) connections to each port by using hostname previously discovered. For each of these combinations, the tool reports the web technologies identified |
How it works
Website Recon uses Wappalyzer as a scanning engine. It has a consistent database of web application signatures which allows it to correctly identify over 900 web technologies from more than 50 categories.
The tool looks at multiple website elements to determine its technologies:
- Server HTTP response headers
- HTML Meta Generator tags
- Embedded JavaScript files
- HTML specific content
- HTML specific comments
- Website's favicon