URL Fuzzer
Technical details
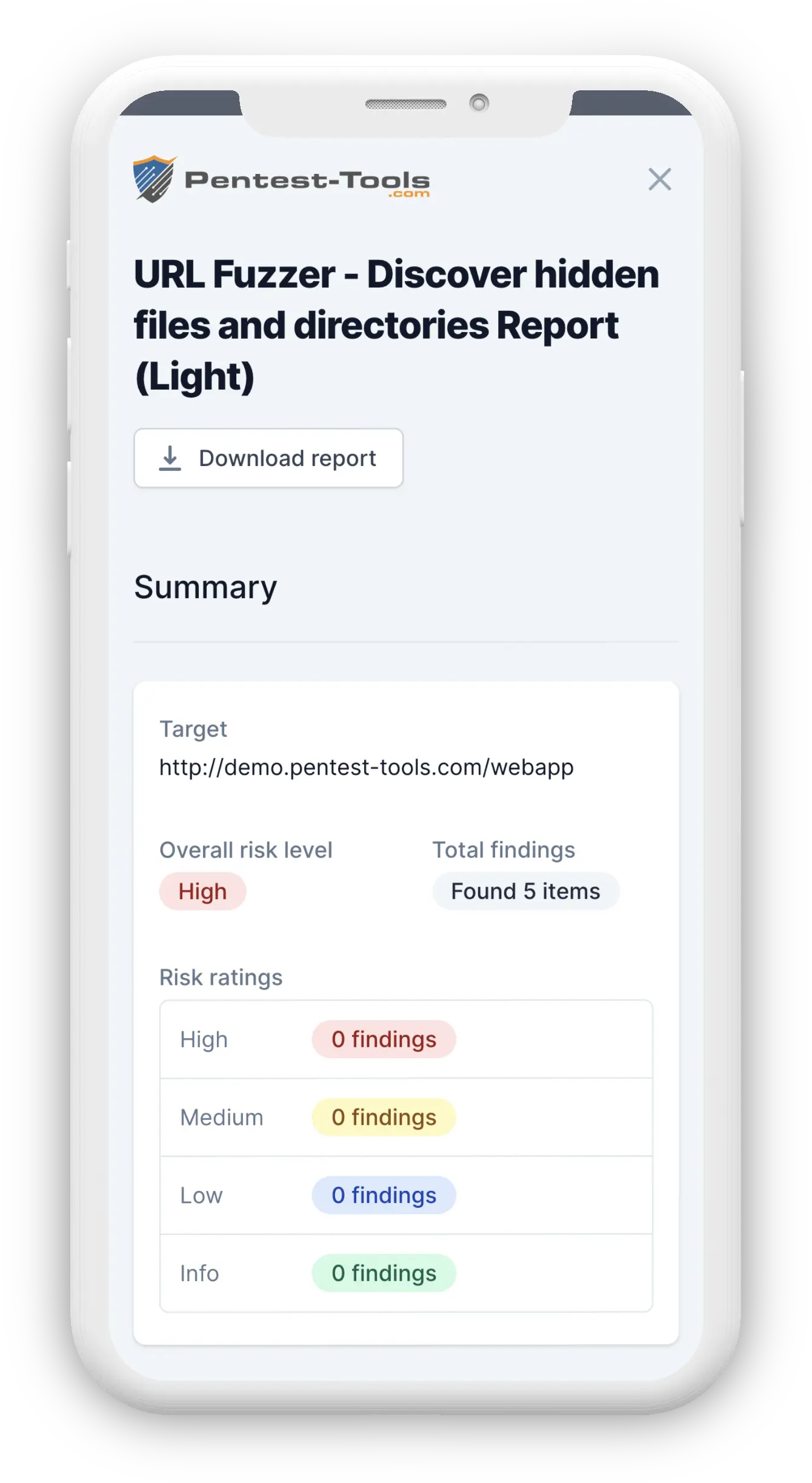
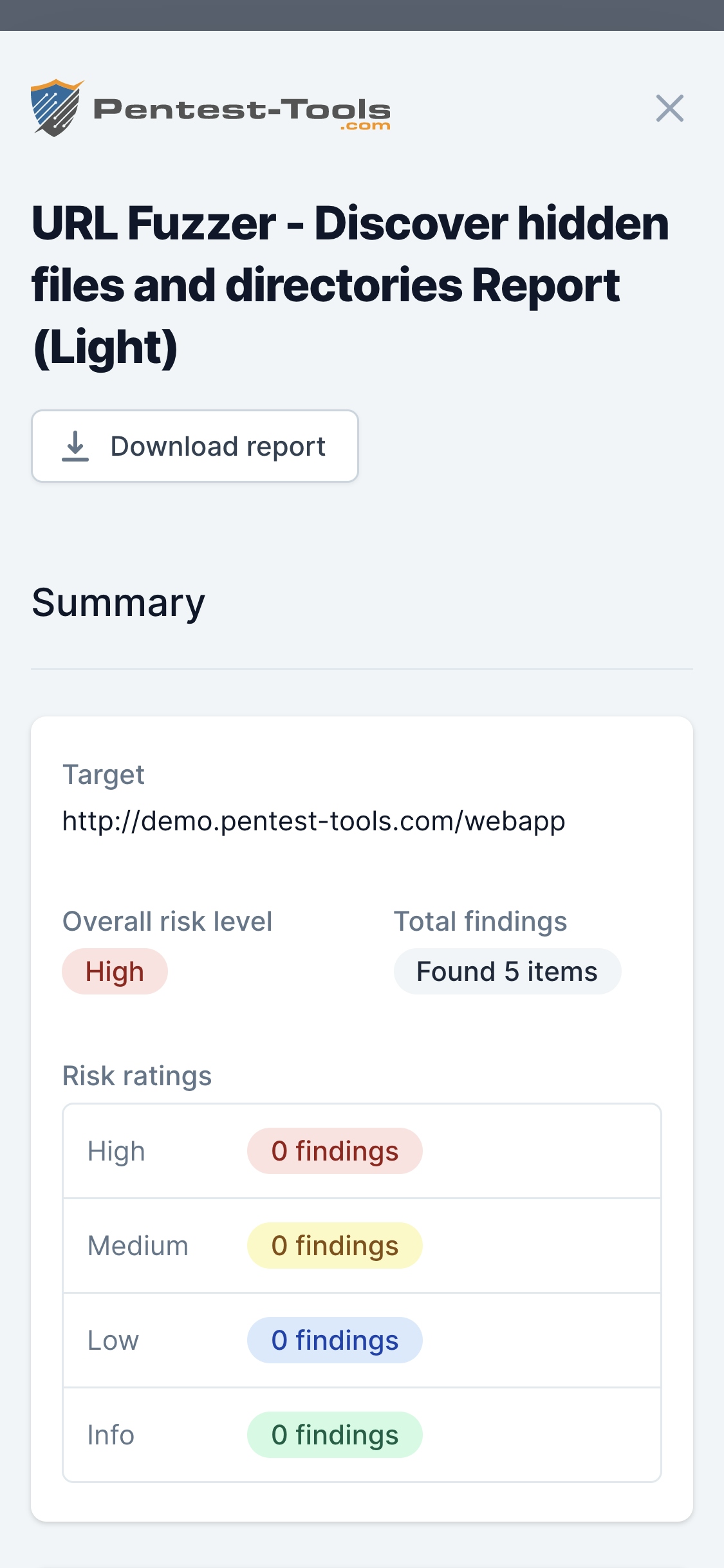
You can use the URL Fuzzer to find hidden files and directories on a web server by fuzzing.
This is a discovery activity which allows you to discover resources that were not meant to be publicly accessible (e.g. /backups, /index.php.old, /archive.tgz, /source_code.zip etc.).
Since "security by obscurity" is not a good practice, you can often find sensitive information in the hidden locations the URL Fuzzer identifies.
Parameters
| Parameter | Description |
|---|---|
| Template URL | This is the template URL on the target server that will be fuzzed. You can (optionally) insert your payload in a custom location specified by a 'FUZZ' marker. You can place it in the path or in the query strings, but NOT in the domain or subdomain. The default location is at the end of the URL. Examples: - http://example.com/dirs/FUZZ/index.php?id=3 - http://example.com/dirs/profiles/user.php?name=FUZZ - http://example.com/ |
| Request options | |
| Method | Specify the HTTP requests method (GET or POST) and POST data. |
| Custom headers | Specify the headers to be sent with every request |
| Retry - Max retries for a request | Maximum number of retries in case of connection error for a HTTP request. Default: 3 |
| Retry - Retry delays exponent | The delay between retries increases exponentially. The exponent can be a float between 0 and 120. If the exponent is 1 (default), the first retry is sent immediately (after 0s), the second one after 1s, then 2s, 4s... If the exponent is 0.1, the sleeps between the retries are: 0s, 0.1s, 0.2s, 0.4s... |
| Retry - Force retry on HTTP codes | By default, the retry policy is only applied on connection errors. With this option, you can enforce retrying on responses with these status codes. They can be integers between 100 and 599 |
| Timing - Number of parallel requests (threads) | Number of threads for this scan. Default: 7 |
| Timing - Delay between requests | Thread count must be 1 in order for this to work properly. It represents the delay between the requests (in seconds) Default: 0 |
| Timing - Request Timeout | Set the timeout for a HTTP request, measured in seconds. Default: 4 |
| Payload type | |
| Wordlist | Specify a custom wordlist for the payloads that will replace the FUZZ marker |
| Sequence of numbers | Generate a sequence of numbers with a given start, end and step to be used as payload that will replace the FUZZ marker |
| Add words from HTML | This option extends the default wordlist with words from the HTML page located at the base URL (including existing links). Not supported with Sequence of numbers payload type |
| Extensions | This option allows you to find files with custom extensions. You can specify multiple extensions that you want to search for (up to 10 extensions per scan), including double extensions (e.g. .php.old, .jsp.bak, .tgz etc.) |
| Mutate words found | Apply various mutations to the identified files to find other resources (e.g. config.php, config2.php, config_old.php, config-dev.php etc.) |
| Filter results | |
| Auto | Discard responses with the 404 status code and (only for the GET method) auto-detect soft 404 pages: non-existing resources, error pages, redirects (false positives) |
| Manual | Results will be filtered according to the Match/Ignore conditions that you specify |
| Match/Ignore HTTP Codes | Match/Ignore responses with the specified status codes. They should be integers between 100 and 599 |
| Match/Ignore Response Size | Match/Ignore responses with the size matching the specified condition. The size used for comparing should be an integer between 0 and 10240 and is measured in KB |
| Match/Ignore HTML contains string | Match/Ignore responses that contain the specified string in the HTML content |
How it works
The URL Fuzzer uses a custom-built wordlist for discovering hidden files and directories. The wordlist contains more than 1000 common names of known files and directories. For each WORD in the wordlist, it makes an HTTP request to: Base_URL/WORD/ or to Base_URL/WORD.EXT in case you chose to fuzz a certain EXTension.
The files and directories the tool finds are returned along with their HTTP response code and the page size.