Cloud Vulnerability Scanner
Discover and report cloud security vulnerabilities, misconfigurations, bucket owners and users, weak access controls, and interesting files with our custom Cloud Vulnerability Scanner.
Assess targets across multi-cloud environments – AWS, GCP, Azure – both from the outside and from within. Monitor cloud-based systems, networks, and applications for security vulnerabilities with regular scans and notifications tuned to your severity criteria.
Paid plans give you access to its full capabilities, plus other 20+ security testing tools and features.
Unlock full capabilities
There's so much you can do with this tool!
Plus, access to it means full access to all 20+ tools on the platform.
Discover and report cloud security vulnerabilities, misconfigurations, bucket owners and users, weak access controls, and interesting files with our custom Cloud Vulnerability Scanner.
Assess targets across multi-cloud environments – AWS, GCP, Azure – both from the outside and from within. Monitor cloud-based systems, networks, and applications for security vulnerabilities with regular scans and notifications tuned to your severity criteria.
Paid plans give you access to its full capabilities, plus other 20+ security testing tools and features.
Reporting
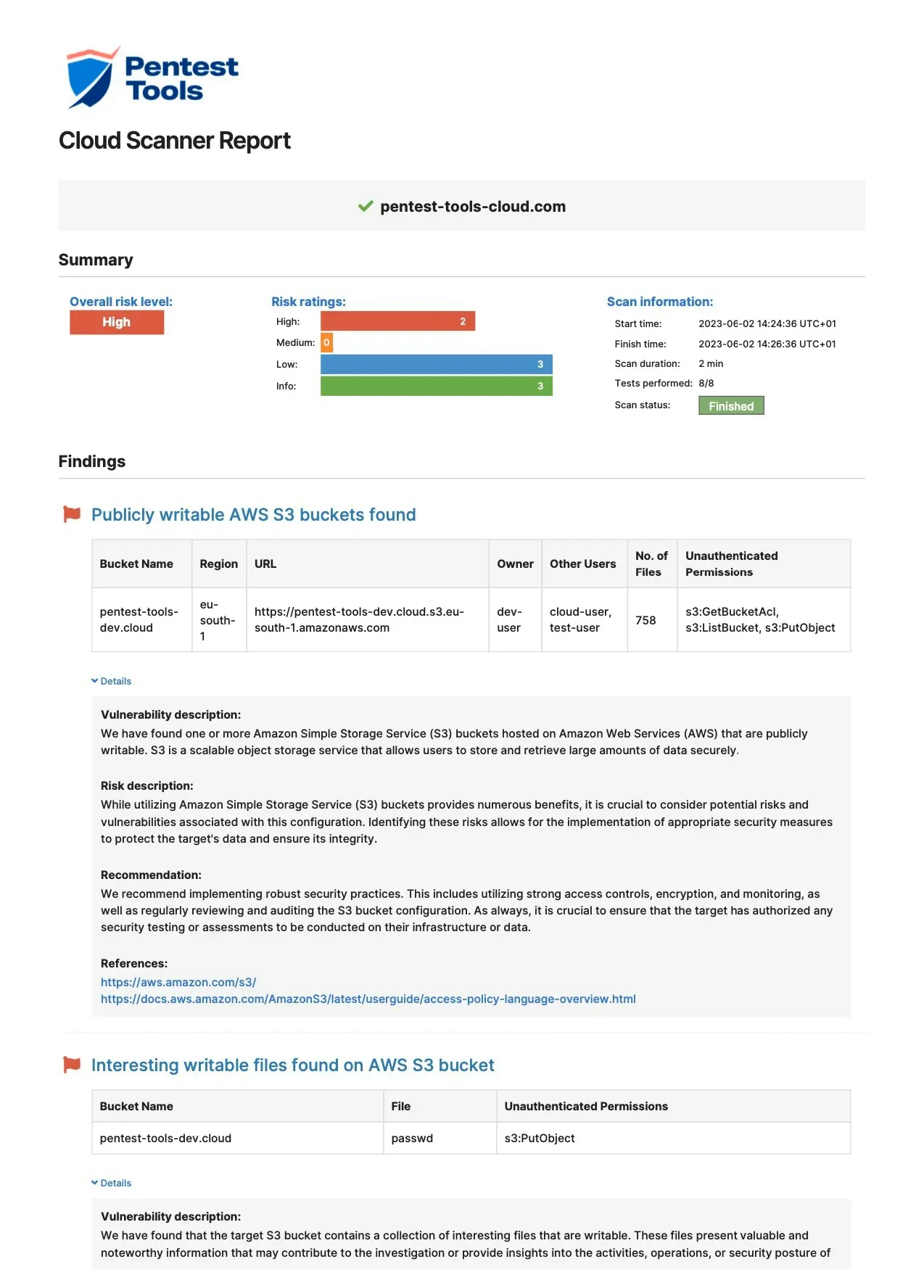
Sample Cloud Vulnerability Scanner report
Each cloud security scan generates detailed findings which are easy to export in PDF, HTML, CSV, XLSX, or editable DOCX reports, based on your subscription. Each report includes:
Vulnerability summary categorized by risk level
Comprehensive vulnerability evidence
Ready-to-use remediation advice
Advanced pentest reporting options available
Better vulnerability discovery.Faster pentest reporting.
Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.

Scanning capabilities
How our Cloud Vulnerability Scanner runs deep, accurate scans
- 1
Proprietary, up-to-date detectors developed in-house
The Cloud Vulnerability Scanner has a strong set of detectors to help you discover your target’s:
- Cloud provider (AWS, GCP, Azure)
- AWS S3 buckets
- AWS S3 ACLs
- Overly permissive configurations
- Interesting files inside AWS S3 buckets (wp-config, backup, keys, etc.)
- 2
Constantly updated cloud security testing capabilities
The engineering team behind our Cloud Vulnerability Scanner is constantly working to upgrade its capabilities. The next big improvement coming to this tool is authentication support for AWS targets so you can run internal scans.
- 3
Built-in mechanism for reducing scan errors
If your target has multiple redirects, enabling the Follow redirects option can help you automatically avoid scanning errors.
- 4
Scan S3 buckets by known URL
If you want to scan an AWS S3 bucket directly, just drop the URL (e.g
http(s)://{bucket_name}.s3.amazonaws.com) in the target field and get going! - 5
Functionality battle-tested by penetration testers
We also build and run Pentest-Tools.com in the cloud, so we use our own experience with maintaining strong cloud security to make this tool even more powerful for you.
Use cases
What you can do with the Cloud Vulnerability Scanner
Validate cloud asset security before deployment
Demonstrate and maintain compliance
Balance scan depth and time limitations
Discover exploitable misconfigurations and risks
Keep a documented trail of evidence for audits
Use clear risk evidence to get more resources for cloud security projects
Or check out 20+ more included tools
