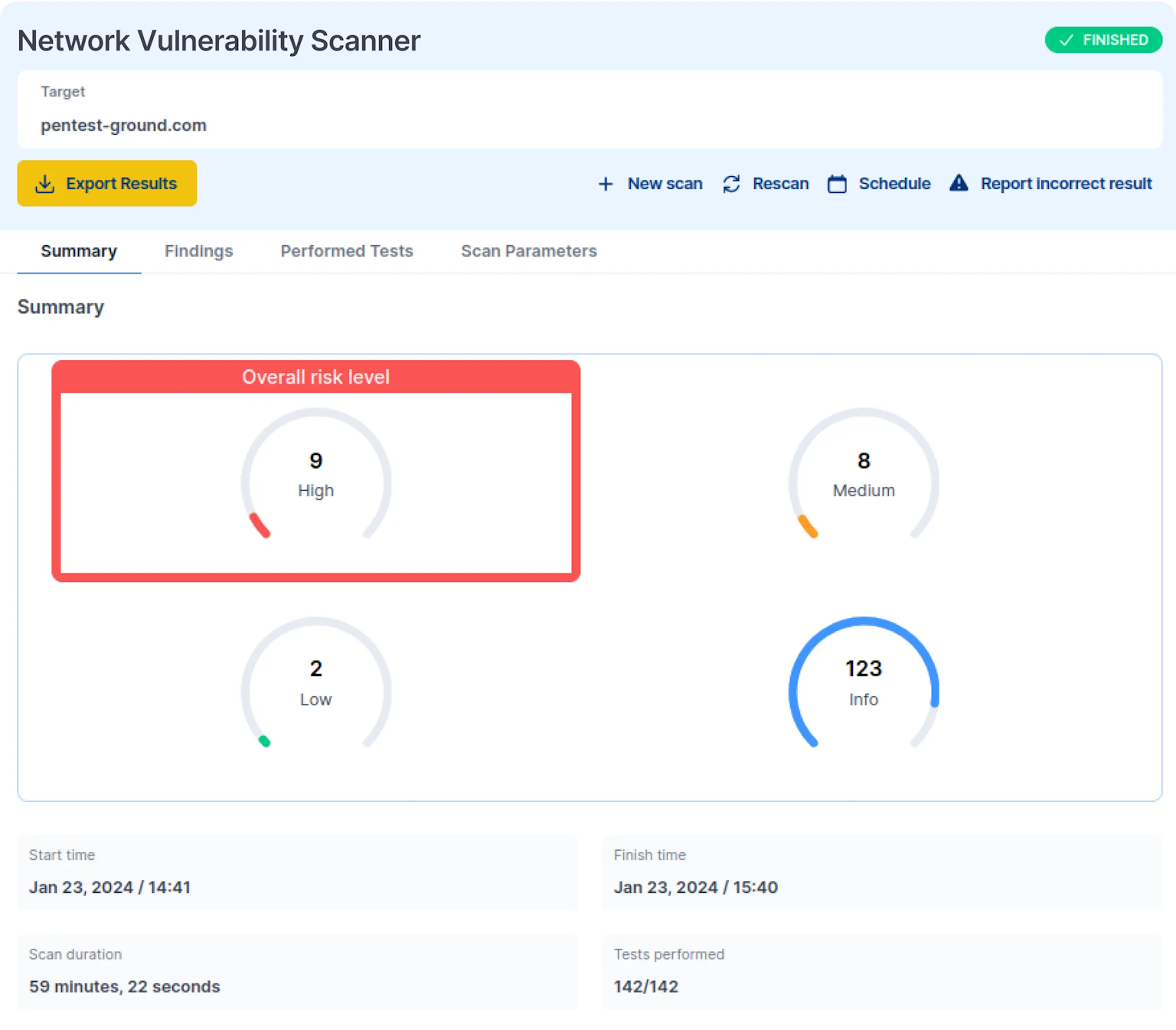
Network Vulnerability Scanner
The Network Vulnerability Scanner is a highly accurate tool that detects 16.725 CVEs in extensively used software products and technologies.
With daily vulnerability updates and a very low rate of false positives, the scanner provides reliable results for your next move.
- Scan type
Light scan
The Network Vulnerability Scanner on Pentest-Tools.com is designed to identify and assess weak configurations, vulnerabilities, and other security flaws within a computer network. Its primary purpose is to proactively detect potential entry points or weaknesses that attackers could exploit to gain unauthorized access, compromise, or disrupt the network.
The Network Vulnerability Scanner is a highly accurate tool that detects 16.725 CVEs in extensively used software products and technologies.
With daily vulnerability updates and a very low rate of false positives, the scanner provides reliable results for your next move.
A supercharged Network Scanner for your Infrastructure
Our Network Vulnerability Scanner is a well-rounded tool for all your network security assessments.
It combines multiple engines and fine-tuned (customizable) scan settings which surface critical vulnerabilities, misconfigurations, and outdated services. Each scan automatically updates your attack surface and provides an up-to-date map for planning targeted attacks or strategic lateral movements.
Comprehensive technology coverage
The Network Vulnerability Scanner accurately identifies 10.000+ CVEs including the famous CitrixBleed, Log4Shell, ProxyShell, and BlueKeep bugs, plus many more. Through the database of detection modules, the tool addresses critical vulnerabilities in software applications of well-known vendors such as Microsoft, Cisco, Citrix, Juniper, Attlassian, and others.
Self-updating detection
Our team integrates new detection modules each day and develops custom ones, keeping the tool relevant in a constantly evolving threatscape. Automated updates keep the Network Vulnerability Scanner consistently effective in uncovering emerging security issues. No need to update plugins and databases manually!
Findings confirmed by solid evidence
The Network Vulnerability Scanner delivers robust evidence for findings, such as targeted endpoints, specific ports, and more. The intuitive interface lets you easily integrate findings into professional reports, making it easier to understand potential security risks and speed up the remediation process.
Automatically validated findings
The Network Vulnerability Scanner uses an automatic system to validate findings, which minimizes false positives and improves accuracy. It assigns a "Confirmed" tag to the vulnerabilities it investigates after interpreting sent requests and received responses, and it also provides evidence of how it discovered the validated issues.
Developed by offensive security pros
Built for what experienced pentesters need, the tool automates security checks such as examining services and software versions and scanning multiple protocols on network hosts. This robust analysis of network hosts delivers results that help security and IT pros to prioritize their work.
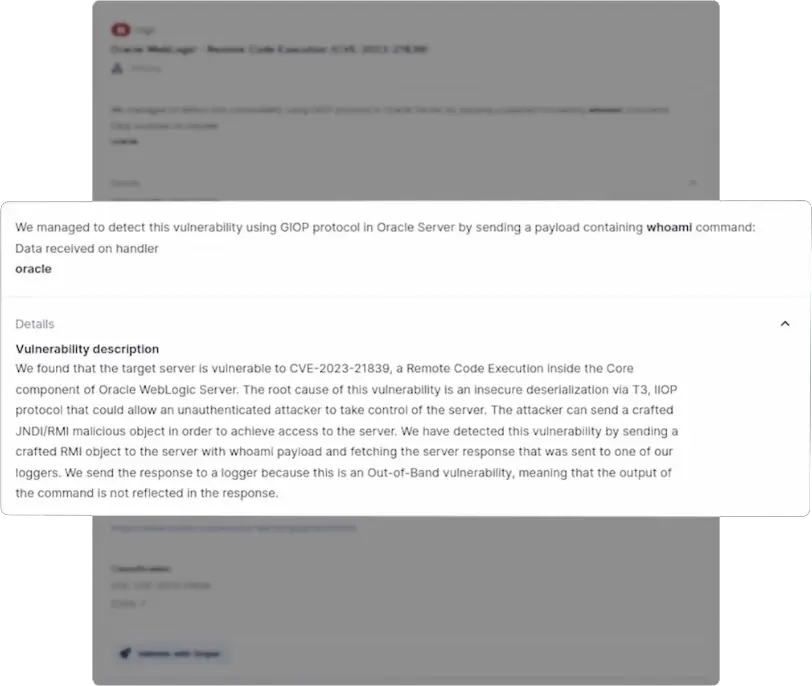
Sample Network Vulnerability Scanner report
Explore a real-life network assessment report. Browse through key sections, examine risk rating graphs, and review in-depth technical findings to get an accurate preview of the report's structure and content.
Provides a quick and complete look at the included security issues, showing their potential impact and urgency. This helps prioritize and address critical vulnerabilities.
Scanned your network? Now go deeper.

How does the Network Vulnerability Scanner work?
The Network Vulnerability Scanner confirms if the target host is alive, pinpoints open ports and associated services, then runs the vulnerability detection routines.
Featuring four complementary scanning engines, it checks software versions against a regularly updated CVE database, uses OpenVAS to target network services, runs custom Sniper modules for critical vulnerability detection, and automates network security checks through Nuclei templates.
Want more details? Check out the full technical documentation and see how it stacks against top industry competitors.
Port discovery
Each network scan starts with a host discovery phase that uses an optional “Check if host is alive before scanning” feature alongside port discovery functionalities.
Upon confirming the target, the port discovery phase identifies open ports and gathers data on running services. The scan then moves forward based on these results and the selected scan type, making for a thorough assessment.
Sniper detection
The Sniper Auto-Exploiter engine uses custom vulnerability checks and modules to pinpoint critical vulnerabilities in widely used software. Bridging the gap between common scanners and real-world attack methods, Sniper focuses on powerful and targeted intrusion techniques.
The Network Vulnerability Scanner uses Sniper only for detecting vulnerabilities, but you can use its findings with the standalones Sniper Auto-Exploiter tool for exploitation. Explore the Sniper extensive modules list here.
OpenVAS detection
OpenVAS, an advanced open-source vulnerability scanner, actively identifies a multitude of vulnerabilities across network services, including SMTP, DNS, SSH, RDP, VNC, HTTP, and more. It establishes connections and dispatches specifically generated packets, determining service vulnerability based on responses.
Boasting more than 57,000 active plugins, the OpenVAS engine in the PentestTools.com Network Vulnerability Scanner is not only a powerful vulnerability detector for various network environments but also comes preconfigured, ready-to-use, and is constantly up-to-date.
Nuclei detection
Nuclei, a powerful open-source project the offensive community relies on, serves as a robust tool for security testing and reconnaissance.
It identifies common vulnerabilities, such as RCEs, XSS, SQL injection, SSRF, open redirect, and many others, providing support for various protocols.
The Network Vulnerability Scanner actively uses 5000+ network-related Nuclei templates, categorized under tags like CVE, DNS, network, SSL, and WAF, ensuring comprehensive security assessments.

Version-based detection
After completing the port-scanning phase, the Network Scanner actively cross-references the results with a comprehensive vulnerability database.
It then checks the identified service versions for any known vulnerabilities or issues.This meticulous process actively tests your network's resilience against potential attackers through the very tactics they use.
Scanning through VPN
Our VPN agent provides secure, encrypted connections and saves time on travel and setup.
Use it for remote internal penetration tests to get a global view of your target's attack surface. Identify missing patches, outdated services, open ports, and default credentials through your Pentest-Tools.com dashboard.
With reliable information about your target's internal network environment, you can test more attack vectors, chain vulnerabilities, and develop exploits that demonstrate critical business risks.
It's really easy to scan your network for vulnerabilities
No setup required. No processing power limits
Operating as a cloud-based scanner, the Network Vulnerability Scanner works out of the box. No need to install anything on your end to scan public-facing or internal network hosts.
Scheduling & running parallel scans
Automatically execute recurring and routine scans for your network hosts. Combine scheduling with the option to run multiple scans in parallel for a productivity boost, and get notifications for specific findings.
API access for easy integration
Initiate scans programmatically with our REST API. Integrate findings into your internal processes - CI/CD workflows, data sources, or custom applications - for an efficient and automated way to use our Network Scanner.
Internal scanning
Detect vulnerabilities, misconfigurations, and other security issues in hosts from internal networks, intranets, private clouds, or restricted-access systems. Quick and easy to set up, our VPN agent directs traffic from our servers to your target’s internal network.
Integrations
The Network Vulnerability Scanner integrates seamlessly with your preferred office and productivity tools: Jira, Slack, email, and Webhooks. Simplify your and your team’s workflow with notifications for scan results for findings truly worth your time.
Customer reviews
Pentest-Tools.com allows for rapid deployment and automation of many industry-standard security tools, then organizes the results into an easy-to-view 'attack surface'. This allows our penetration testers more time to focus on vulnerability analysis and exploitation.
An added benefit that has been fantastic is that the ease of use allows new employees to add value to an engagement on their first day.
Travis DeForge
Security Engineering Manager at Gotham Security
United States of America 🇺🇸


Common questions about network vulnerability scanning
How can I start using your Network Vulnerability Scanner?
Check out our quick setup guide to quickly familiarize yourself with the tool and launch your network scan. We designed it to help you make the most of Pentest-Tools.com effortlessly.
Get your network vulnerability assessment rolling in just a few easy steps!
How do I scan for network vulnerabilities?
Take your pick: go for a free scan or level up with one of our premium plans for the full power of our Network Vulnerability Scanner, plus 20+ tools and a range of features to supercharge your pentesting process.
For a hands-on walkthrough, explore our guide on conducting a thorough network vulnerability assessment using Pentest-Tools.com.
How do I know if my network is vulnerable?
Run a thorough scan and receive a detailed report that unveils potential vulnerabilities—key insights into the entry points attackers hackers might exploit for infiltrating a network, exfiltrating confidential data, and delivering other types of threats.
Need expert guidance in evaluating your attack surface, identifying vulnerabilities, and fixing misconfigurations? Our certified penetration testing service team is here to lend a hand.
How long will the scan take?
This varies based on the scanning engines used, ranging from minutes to a few hours. While running, the scan may seem inactive, but you can always check the progress by clicking on the target name for a tooltip with a progress bar.
Keep in mind that scan speed depends on server response time and network latency. Despite any delays, the scan will ultimately complete.
If it exceeds the expected duration, hitting our 24-hour limit, your scan will time out. In such cases, consider dividing the scan into two parts, focusing on smaller port ranges, especially if it initially detects numerous open ports.
Ready for your next step? Try these tools
Web
Network & Cloud
Try the light version for free












